9.14 BUUCTF RSA 2
We have n,e,dp,c.
Assume that it is quite difficult to factorize n, but it can be easily divided in fact.
What can we do with dp leak?
dp ≡ d mod (p-1)
=> dp*e ≡ d*e mod (p-1)
we have d*e ≡ 1 mod ((p-1)*(q-1))
=> dp*e ≡ d*e ≡ 1 mod (p-1)
d*e = k*(p-1)+1
dp*e = k'*(p-1)+1
So we can use another k1 to combine d and dp to fully take use of condition.
d*e = k1*(p-1)+dp*e
Notice that we have
d*e ≡ 1 mod ((p-1)*(q-1))
k1*(p-1)+dp*e = k2*(p-1)*(q-1)+1
i.e
dp*e = (p-1)*(k2*(q-1)-k1)+1
Let x=k2*(q-1)-k1
We have
dp*e = (p-1)*x+1
Because dp<p-1, we can conclude x<e.
As e is small(65537), we can enumerate x to check if (dp*e-1) % x == 0. Once we find x, it is just a simple RSA problem, using x to calculate p, q, φ...
Here we code(Be aware of that we must use 'n//p' not 'n/p'!):
from Crypto.Util.number import *
import primefac
import gmpy2
def modinv(a,n):
return primefac.modinv(a,n) % n
e = 65537
n = 248254007851526241177721526698901802985832766176221609612258877371620580060433101538328030305219918697643619814200930679612109885533801335348445023751670478437073055544724280684733298051599167660303645183146161497485358633681492129668802402065797789905550489547645118787266601929429724133167768465309665906113
dp = 905074498052346904643025132879518330691925174573054004621877253318682675055421970943552016695528560364834446303196939207056642927148093290374440210503657
c = 140423670976252696807533673586209400575664282100684119784203527124521188996403826597436883766041879067494280957410201958935737360380801845453829293997433414188838725751796261702622028587211560353362847191060306578510511380965162133472698713063592621028959167072781482562673683090590521214218071160287665180751
for x in range(1,e):
dpe1 = dp*e-1
if dpe1%x == 0:
if(primefac.isprime((dpe1//x)+1)):
p = dpe1//x + 1
q = n//p
phi = (p-1)*(q-1)
d = modinv(e,phi)
m = pow(c,d,n)
print(m)
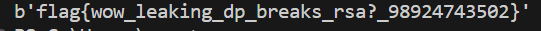
print(long_to_bytes(m))
Finally, we get the flag.