Block ciphers
Block Ciphers
notes from the open course provided by Stanford University: https://www.coursera.org/learn/crypto/home/module/2
What is block ciphers
A block cipher is made up of two algorithms, E and D. These are encryption and decryption algorithms. Both of these algorithms take N-bit plaintext as input and output the same number of bits as output.
So it maps N bits of inputs to N bits of outputs.
Block ciphers are typically built by iteration.
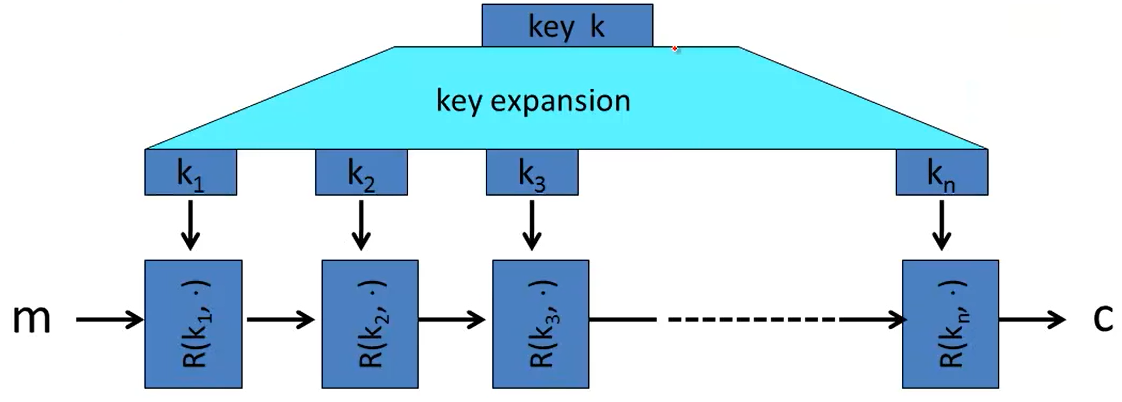
where the R(k, m) is called a round function.
Block ciphers are slower than stream ciphers, but we’ll see that we can do many things with block cipher that we couldn’t do very efficiently with constructions like RC4.
PRFs and PRPs
PRF is a pseudorandom function, which is defined over a key space, an input space, and an output space. It can be written as follows:
And the only requirement is that there’s an efficient way to evaluate the function.
For a pseudorandom function, we’re not requiring that they be invertible. We just need them to be evaluatable.
A related concept that more accurately captures what a block cipher is is pseudorandom permutation, PRP. So a PRP is defined over a key space and then just a set X. And what it does is it takes an element in the key space, an element of X, and outputs one element in X. It can be written as follows:
The function E should be easy to evaluate, so there should be an algorithm to evaluate the function E.
Once we fix the key K, this function E will be one-to-one.
A PRP is also a PRF where X=Y and is efficiently invertible.
Let be a PRF, Funs[X, Y] be the set of all functions from X to Y, Funs[X, Y], be the set of all functions that function F traverse all keys from the key space.
Obviously, the size of Funs[X, Y] is and the size of is |K|.
Def.: A PRF F is secure if a randomly selected function in Funs[X, Y] is indistinguishable from a random function in .
let:
f Funs[X, Y] in a uniform distribution,
k K in a uniform distribution
the adversary is capable of querying the challenger with a sequence of inputs, and the challenger will return the output from either random function f or PRF F(k, ).
If F is a secure PRF, then the adversary can't tell the difference.
: even if you have a secure PRF, it's enough that on just one known input the output is not random, the output is fixed, and already the PRF is broken, even though you realize that everywhere else the PRF is perfectly indistinguishable from random.
Theorem.: If F: is a secure PRF, then the following G: is a secure PRG:
-
Proof(Roughly).
Since F is a secure PRF, it's indistinguishable from a truly random function f
is indistinguishable fromf is a truly random function
f(0) is random, and f(1) is also independently random, and so on.
is a random string.Therefore, is indistinguishable from a random string.
Such construction is sometimes called "counter mode". The key property of such construction is parallel, which means it could reach a faster speed in a multi-processor system than the sequential PRG, such as RC4.
Data Encryption Standard
The core idea behind DES is the Feistel network.
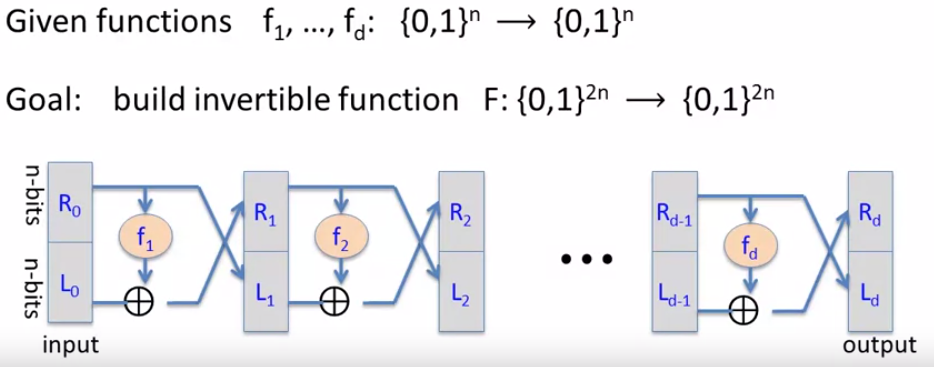
for all , the Feistel network is invertible.
Proof. construct inverse
Theorem.: let be a secure PRF, then 3-round Feistel is a secure PRP
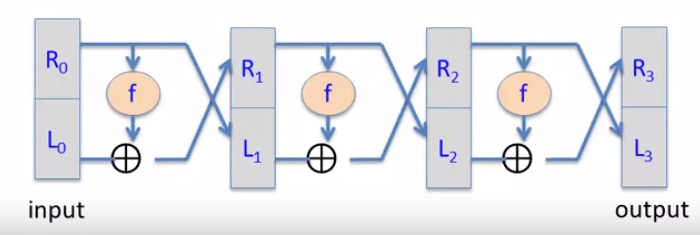
where the means three independent keys.
DES: a 16 round Feistel Network,

the structure of DES round function(i.e., the SPN(Substitution-Permutation) structure):
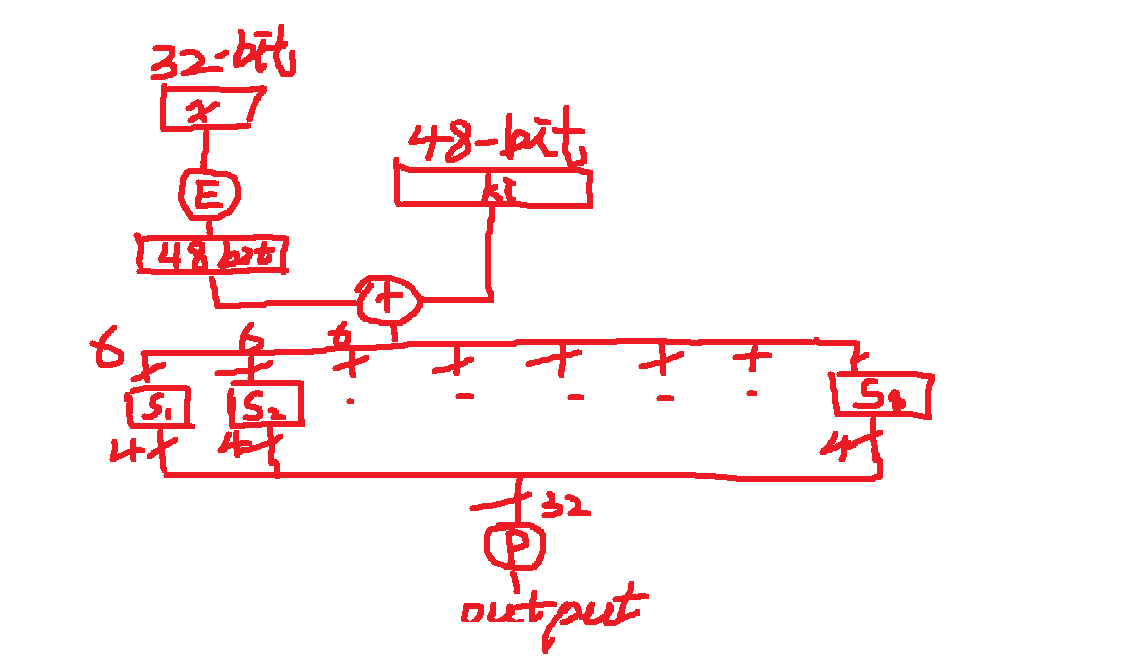
the key component of the round function is S boxes, a non-linear function implemented as a look-up table.
: The S box should never be a liner function.
Suppose we have a bad S-box, implemented as:
or written equivalently:
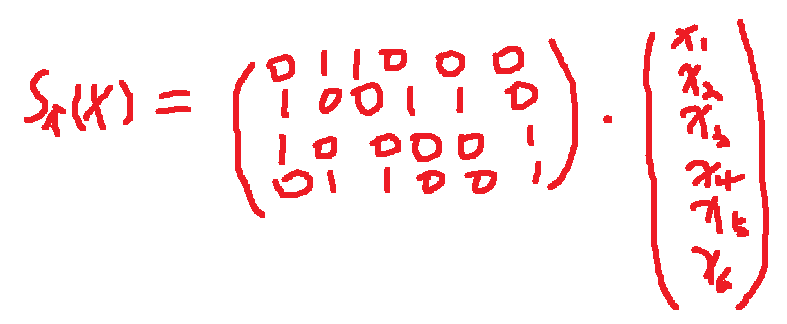 we say that is a linear function.
we say that is a linear function.
since the permutation is also a linear function, suppose a 4-bit permutation , then such permutation can be written as:
*Then, the DES would be entirely linear, exists a matrix B, satisfy :

If the DES is function, then,
thus, DES is not a random function, since a random function will never satisfy this equality.
In fact, you just need 832 input-output pairs to recover the entire secret keys under a linear S-box construction. The DES is insecure even if the S-box is close to linear(i.e., linear at most of the time) (linear analysis attacks, or linear cryptanalysis).
Exhaustive Search Attacks
Goal: Given a few input-output pairs find the certain key K.
how many input-output pairs required to find the key that does this map?
the answer is just one pair is enough to find the key.
Lemma: Suppose DES is an cipher(which means we're going to pretend the DES is made up of random invertible functions), then for every key K, DES implements a random invertible function.
Proof.
Since the size of key space is , we pretend the DES is a collection of random invertible functions:
then , to find key k mapping the m to c, s.t., , then the key is unique with probability
get the probability that the key k is NOT unique:
therefore, the probability that the key k is unique
For two plain-cipher pairs, the key k mapping is unique with probability .
DES-challenge: given two or three pairs of plaintext-ciphertext, find key s.t. , i = 1, 2, 3.
this challenge can be solved by essentially trying all possible keys.
- in 1997, the internet search, takes 3 months
- in 1998, the EFF machine(deep crack), takes 3 days
- in 1999, the combined search, takes 22 hours
- in 2006, the COPACABANA(120 FPGA), 7 days
therefore, 56-bit ciphers should not be used!
Strengthening the DES
#1.
Why not double DES?
because it is vulnerable for meet in the middle attack
Meet in the Middle attack
given a brunch of input-output pairs and ,
to find the s.t.
obviously the key also satisfy
1st, build a table with entries, mapping the key to the corresponding ciphertext,
2nd, for all do: if the D(k, C) is found in that table, then
then we can get the key
the time complexity is approximately
even 3DES has an attack that basically explores on possible keys. but it is still secure enough to be standardized by the NIST.
#2. DESX
let be a block cipher
Define EX as
the size of key space |K| = 2^{64 + 56 +64} = 2^{184}
however, the DESX can be cracked in 2^{120} computes.
Proof.
homework
Note that, the implementation of or does NOTHING for the security against exhaustive search attacks.
Proof.
homework
More attacks on block ciphers
#1. Side-channel attacks:
- measure the time to do enc/dec, or measure the power of enc/dec.
even use mask to mitigate the side-channel attacks, there still exists a differential analysis attack to extract the secret information. - cache side-channel attacks:
#2. Fault attacks:
computing errors in the last round exposed the secret key k
: do not even implement the crypto primitives by yourself.
because 1) you have to make sure there are no side-channel attacks on your implementation, 2) you have to make sure that the implementation is secure against fault attacks.
instead, you just use the standard library like the ones available in OpenSSL.
Linear and differential attacks
Goal: given many inp/out pairs, can recover the secret key k in less times computes.(better than the exhaustive search)
lesson: A tiny bit of linearly in lead to a time attack. do not design cipher by yourself.
Quantum attacks:
Generic search problem: let be a function, the goal is find s.t.
the best you can do is just try all possible input, so this takes time which is linear in the size of the domain, i.e. O(|X|)
if you can build a computer on the quantum physics, then you can solve this problem faster. [Grover'96] In fact you can solve this search problem not in but . Therefore the quantum computer has a great impact on the modern cryptography.
Advanced Encryption Standard
Since the DES and 3DES are simply not designed for modern hardware and are too slow, the NIST publishers request for proposal called Advanced Encryption Standard, and them finally adopt the Rijndael as AES.
The AES block cipher
the AES is constructed by the Substitution-Permutation Network(SPN) instead of Feistel network.
Remember that there are half of bits unchanged round to round in Feistel network. While in SPN all the bits are changed every round.
the workflow of SPN:
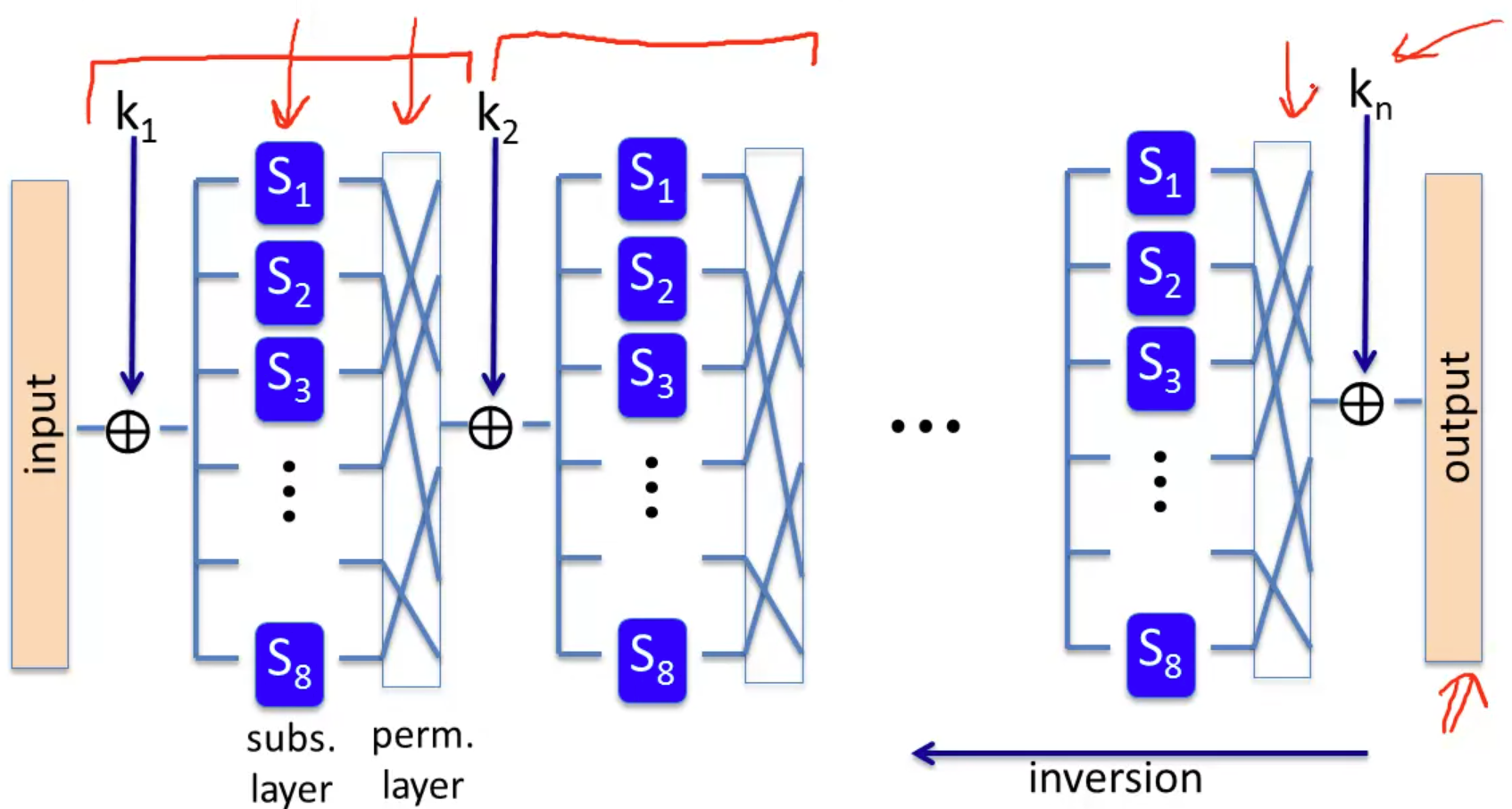
the inversion of SPN is simply done by applying all of the steps in the reverse order.
the AES works on 128-bit block, so the message block is handled in a 4 4 bytes matrix.
the specific work flow of AES:
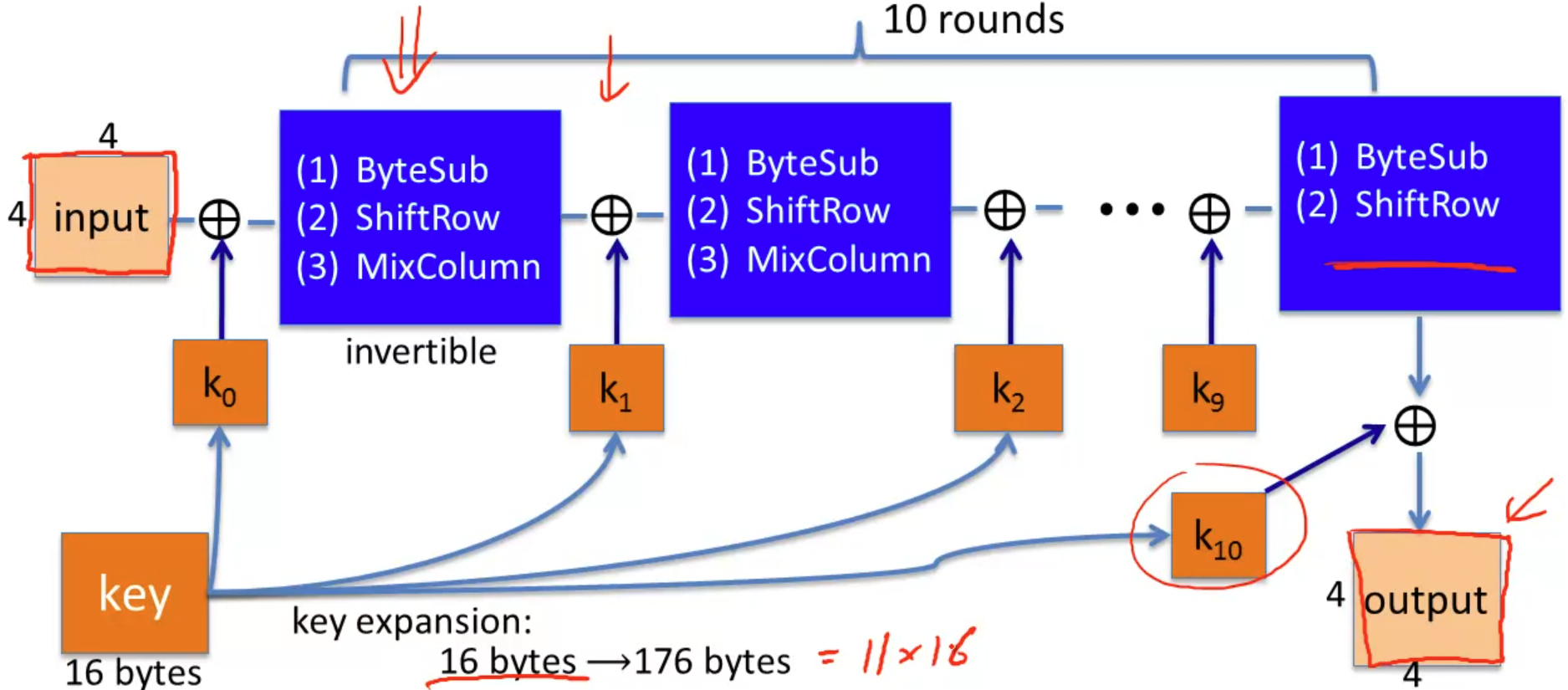
#1. byte substitution:
the way byte substitution works is literally based on S-box containing 256(16 16) bytes, and essentially what it does is applying the S-box to every byte in the current states matrix.
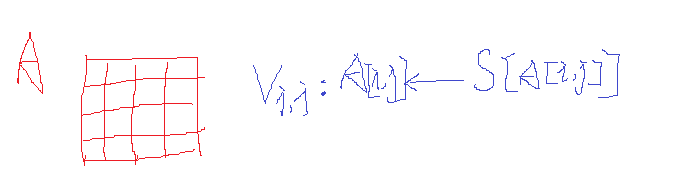
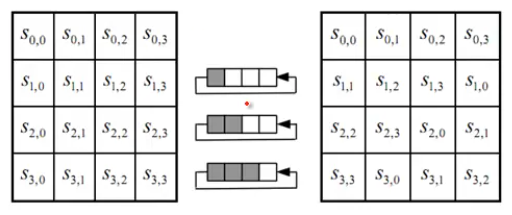
#2. shift rows:
just shift the rows of state matrix:
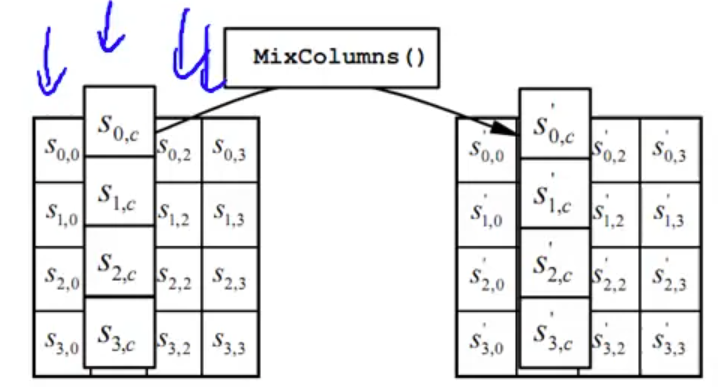
#3. mix columns:
literally apply a linear transformation to each one of these columns.
it should point out that shift rows and mixed columns are very easy to implement in code, and the byte substitution itself is also easily computable. Therefore, you can simply shrink the description of AES by literally storing code that computes the table rather than hardwiring the table into the implementation.
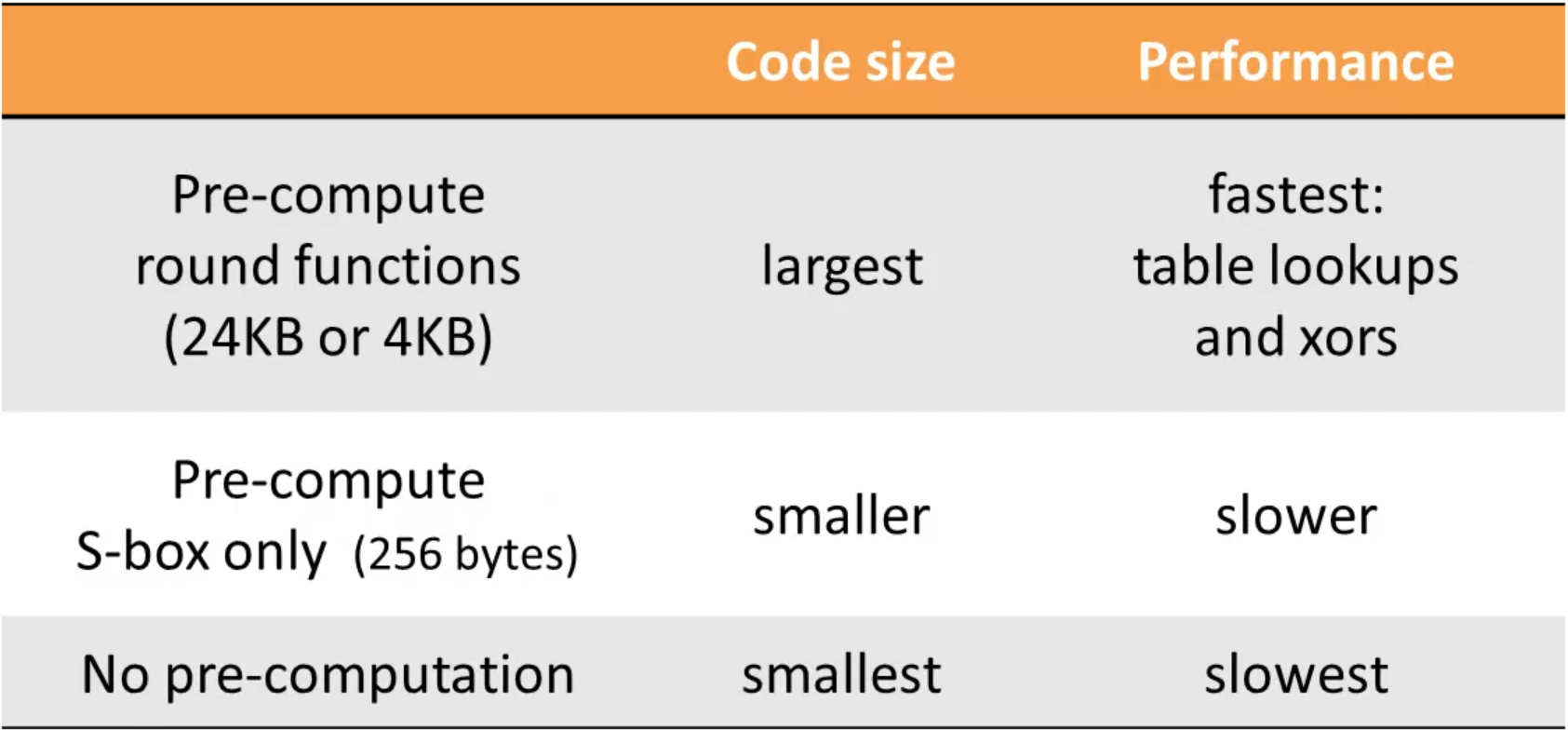
Code size & Performance tradeoff
a popular performance optimization of AES is precompute some of the transformation and then look-up the table:
Example: Javascript AES.
it send the AES library to the browser with no pre-computation (6.4 KB in size) to lower the network transmission overhead. the laptop will compute the lookup table on the AES library arrival to reach the best performance.
AES in hardware
AES instructions in Intel Westmere:
- aesenc, aesenclast: do one round function of AES and the last round function of AES
128-bit registers: xmm1<-state, xmm2<-round key
aesenc xmm1, xmm2; puts round function result in xmm1 - aeskeygenassist: perform AES key expansion
Claim 14x speedup over OpenSSL on the same hardware.
Similar instructions on AMD Bulldozer.





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 上周热点回顾(3.3-3.9)