CentOS Linux 安装IPSec+L2TP
第二层隧道协议L2TP(Layer 2 Tunneling Protocol)是一种工业标准的Internet隧道协议,它使用UDP的1701端口进行通信。L2TP本身并没有任何加密,但是我们可以使用IPSec对L2TP包进行加密。L2TP VPN比PPTP VPN搭建复杂一些。
环境说明:
[root@l2tp_server ~]# cat /etc/redhat-release CentOS release 6.9 (Final) [root@l2tp_server ~]# uname -r 2.6.32-696.10.1.el6.x86_64
1、需要先添加epel源:
rpm -ivh https://mirrors.aliyun.com/epel/epel-release-latest-6.noarch.rpm
yum -y install openswan ppp xl2tpd ##openswan是Linux系统上IPsec的一个实现 官网:http://www.openswan.org/
安装一些依赖包:
yum -y install make gcc gmp-devel bison flex lsof
2、配置IPsec
编辑配置文件/etc/ipsec.conf,只需要将最下面的"YOUR_SERVER_IP"改成你的公网IP即可:
[root@l2tp_server ~]# vim /etc/ipsec.conf
# /etc/ipsec.conf - Libreswan IPsec configuration file # This file: /etc/ipsec.conf # # Enable when using this configuration file with openswan instead of libreswan #version 2 # # Manual: ipsec.conf.5 # basic configuration config setup # which IPsec stack to use, "netkey" (the default), "klips" or "mast". # For MacOSX use "bsd" protostack=netkey # # Normally, pluto logs via syslog. If you want to log to a file, # specify below or to disable logging, eg for embedded systems, use # the file name /dev/null # Note: SElinux policies might prevent pluto writing to a log file at # an unusual location. logfile=/var/log/pluto.log # # The interfaces= line is only required for the klips/mast stack #interfaces="%defaultroute" #interfaces="ipsec0=eth0 ipsec1=ppp0" # # If you want to limit listening on a single IP - not required for # normal operation #listen=127.0.0.1 # # Do not set debug options to debug configuration issues! # # plutodebug / klipsdebug = "all", "none" or a combation from below: # "raw crypt parsing emitting control kernel pfkey natt x509 dpd # private". # Note: "crypt" is not included with "all", as it can show confidential # information. It must be specifically specified # examples: # plutodebug="control parsing" # plutodebug="all crypt" # Again: only enable plutodebug or klipsdebug when asked by a developer #plutodebug=none #klipsdebug=none # # Enable core dumps (might require system changes, like ulimit -C) # This is required for abrtd to work properly # Note: SElinux policies might prevent pluto writing the core at # unusual locations dumpdir=/var/run/pluto/ # # NAT-TRAVERSAL support # exclude networks used on server side by adding %v4:!a.b.c.0/24 # It seems that T-Mobile in the US and Rogers/Fido in Canada are # using 25/8 as "private" address space on their wireless networks. # This range has never been announced via BGP (at least upto 2015) virtual_private=%v4:10.0.0.0/8,%v4:192.168.1.0/24,%v4:172.16.0.0/12,%v6:fd00::/8,%v6:fe80::/10 # For example connections, see your distribution's documentation directory, # or https://libreswan.org/wiki/ # # There is also a lot of information in the manual page, "man ipsec.conf" # # It is best to add your IPsec connections as separate files in /etc/ipsec.d/ include /etc/ipsec.d/*.conf conn L2TP-PSK-NAT rightsubnet=vhost:%priv also=L2TP-PSK-noNAT conn L2TP-PSK-noNAT authby=secret pfs=no auto=add keyingtries=5 rekey=no ikelifetime=8h keylife=1h type=transport left=YOUR_SERVER_IP leftprotoport=17/1701 right=%any rightprotoport=17/%any
3、设置预共享密钥PSK
[root@l2tp_server ~]# vim /etc/ipsec.secrets
YOUR_SERVER_IP.ADDRESS %any: PSK "YourSharedSecret"
4、修改包转发设置
[root@l2tp_server ~]# for each in /proc/sys/net/ipv4/conf/*; do echo 0 > $each/accept_redirects; echo 0 > $each/send_redirects; done
[root@l2tp_server ~]# echo 1 >/proc/sys/net/core/xfrm_larval_drop
修改内核设置,使其支持转发,编辑/etc/sysctl.conf文件:
[root@l2tp_server ~]# sed -i 's/net.ipv4.ip_forward = 0/net.ipv4.ip_forward = 1/' /etc/sysctl.conf
[root@l2tp_server ~]# sysctl -p
5、启动IPsec
/etc/init.d/ipsec start
查看系统IPSec安装和启动的正确性:
[root@l2tp_server ~]# ipsec verify
Verifying installed system and configuration files
Version check and ipsec on-path [OK]
Libreswan 3.15 (netkey) on 2.6.32-696.10.1.el6.x86_64
Checking for IPsec support in kernel [OK]
NETKEY: Testing XFRM related proc values
ICMP default/send_redirects [OK]
ICMP default/accept_redirects [OK]
XFRM larval drop [OK]
Pluto ipsec.conf syntax [OK]
Hardware random device [N/A]
Two or more interfaces found, checking IP forwarding [OK]
Checking rp_filter [ENABLED]
/proc/sys/net/ipv4/conf/default/rp_filter [ENABLED]
/proc/sys/net/ipv4/conf/lo/rp_filter [ENABLED]
/proc/sys/net/ipv4/conf/eth0/rp_filter [ENABLED]
/proc/sys/net/ipv4/conf/ppp0/rp_filter [ENABLED]
rp_filter is not fully aware of IPsec and should be disabled
Checking that pluto is running [OK]
Pluto listening for IKE on udp 500 [OK]
Pluto listening for IKE/NAT-T on udp 4500 [OK]
Pluto ipsec.secret syntax [OK]
Checking 'ip' command [OK]
Checking 'iptables' command [OK]
Checking 'prelink' command does not interfere with FIPSChecking for obsolete ipsec.conf options [OK]
Opportunistic Encryption [DISABLED]
没有FAILD报错就可以/
6、安装L2TP(xl2tpd和rp-l2tp) xl2tpd是由Xelerance Corporation维护的l2tpd应用。但是xl2tpd没有l2tp-control,需要从rp-l2tp这个里面提取。所以要装这两个软件包。
yum -y install libpcap-devel ppp policycoreutils #依赖软件
安装xl2tpd和rp-l2tp:
[root@localhost ~]# cd /usr/local/src/
[root@localhost src]# wget http://sourceforge.net/projects/rp-l2tp/files/rp-l2tp/0.4/rp-l2tp-0.4.tar.gz
[root@localhost src]# tar -zxvf rp-l2tp-0.4.tar.gz
[root@localhost src]# cd rp-l2tp-0.4
[root@localhost rp-l2tp-0.4]# ./configure && make
[root@localhost rp-l2tp-0.4]# cp handlers/l2tp-control /usr/local/sbin/
[root@localhost rp-l2tp-0.4]# mkdir /var/run/xl2tpd/
[root@localhost rp-l2tp-0.4]# ln -s /usr/local/sbin/l2tp-control /var/run/xl2tpd/l2tp-control
##安装xl2tpd
[root@localhost ~]# cd /usr/local/src
[root@localhost src]# wget https://github.com/xelerance/xl2tpd/archive/v1.3.10.1.tar.gz
[root@localhost src]# tar xf v1.3.10.1.tar.gz && cd xl2tpd-1.3.10.1 && make && make install
7、编辑xl2tpd配置文件
[root@localhost ~]# mkdir /etc/xl2tpd/
[root@localhost ~]# vim /etc/xl2tpd/xl2tpd.conf
; ; This is a minimal sample xl2tpd configuration file for use ; with L2TP over IPsec. ; ; The idea is to provide an L2TP daemon to which remote Windows L2TP/IPsec ; clients connect. In this example, the internal (protected) network ; is 192.168.1.0/24. A special IP range within this network is reserved ; for the remote clients: 192.168.1.128/25 ; (i.e. 192.168.1.128 ... 192.168.1.254) ; ; The listen-addr parameter can be used if you want to bind the L2TP daemon ; to a specific IP address instead of to all interfaces. For instance, ; you could bind it to the interface of the internal LAN (e.g. 192.168.1.98 ; in the example below). Yet another IP address (local ip, e.g. 192.168.1.99) ; will be used by xl2tpd as its address on pppX interfaces. [global]
ipsec saref = yes ; listen-addr = 192.168.1.98 ; ; requires openswan-2.5.18 or higher - Also does not yet work in combination ; with kernel mode l2tp as present in linux 2.6.23+ ; ipsec saref = yes ; Use refinfo of 22 if using an SAref kernel patch based on openswan 2.6.35 or ; when using any of the SAref kernel patches for kernels up to 2.6.35. ; saref refinfo = 30 ; ; force userspace = yes ; ; debug tunnel = yes [lns default] ip range = 192.168.20.2-192.168.20.220 local ip = 192.168.20.1 require chap = yes refuse pap = yes require authentication = yes name = LinuxVPNserver ppp debug = yes pppoptfile = /etc/ppp/options.xl2tpd length bit = yes
8、配置PPP
[root@localhost ~]# vim /etc/ppp/options.xl2tpd
require-mschap-v2 ms-dns 8.8.8.8
auth mtu 1200 mru 1000 crtscts hide-password modem
lock name l2tpd proxyarp lcp-echo-interval 30 lcp-echo-failure 4
9、设置拨号用户名和密码
[root@localhost ~]# vim /etc/ppp/chap-secrets
1 # Secrets for authentication using CHAP 2 # client server secret IP addresses 3 test l2tpd 123456 *
10、以debug方式启动l2tp,查看有无错误:
[root@localhost ~]# xl2tpd -D xl2tpd[30734]: Enabling IPsec SAref processing for L2TP transport mode SAs xl2tpd[30734]: IPsec SAref does not work with L2TP kernel mode yet, enabling force userspace=yes xl2tpd[30734]: setsockopt recvref[30]: Protocol not available xl2tpd[30734]: Not looking for kernel support. xl2tpd[30734]: xl2tpd version xl2tpd-1.3.10.1 started on localhost.localdomain PID:30734 xl2tpd[30734]: Written by Mark Spencer, Copyright (C) 1998, Adtran, Inc. xl2tpd[30734]: Forked by Scott Balmos and David Stipp, (C) 2001 xl2tpd[30734]: Inherited by Jeff McAdams, (C) 2002 xl2tpd[30734]: Forked again by Xelerance (www.xelerance.com) (C) 2006-2016 xl2tpd[30734]: Listening on IP address 0.0.0.0, port 1701
11、加入开机自启动
[root@localhost ~]# echo -e "/usr/local/sbin/xl2tpd\n/etc/init.d/ipsec restart\necho 1 >/proc/sys/net/core/xfrm_larval_drop" >> /etc/rc.local
[root@localhost ~]# echo "for each in /proc/sys/net/ipv4/conf/*; do echo 0 > $each/accept_redirects; echo 0 > $each/send_redirects; done" >> /etc/rc.local
12、添加iptables转发规则,如果服务端是在内网的话,需要在路由器上做1701端口的映射,以及添加到对应VPN网段的路由
iptables --table nat --append POSTROUTING --jump MASQUERADE
/etc/init.d/iptables save
/etc/init.d/iptables restart
13、Windows端连接配置:
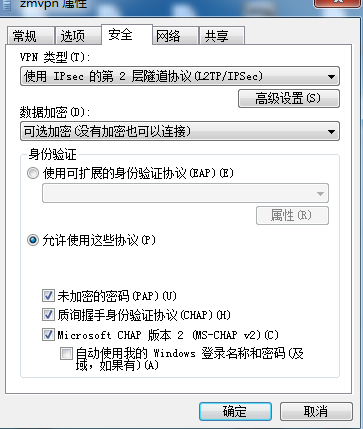
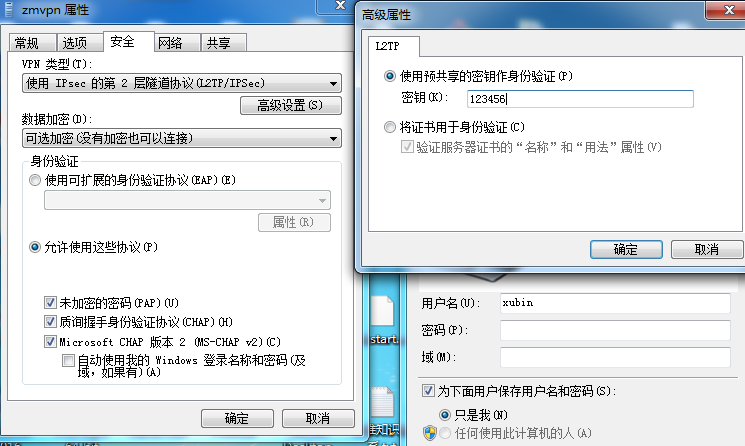
14、Win 10 连接vpn 输入用户名密码后没有反应的解决办法
单击开始—>运行,键入regedit,点击确定找到下面的注册表项 HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters
在编辑菜单上,单击新建DWORD值
在名称框中键入“ProhibitIpSec”
在数值数据框中,键入1、然后确定’
继续找到下面的注册表项
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent
新建一个DWORD类型的键AssumeUDPEncapsulationContextOnSendRule值为2
然后重启计算机。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号