Otter CTF (取证专项赛)WP兼volatility取证工具运用技巧
Otter CTF (取证专项赛)WP兼volatility取证工具运用技巧
前言:是很基础的vol工具使用的取证题目,练练相关的命令以及插件挺不错的
复现赛链接:NSSCTF - OtterCTF 2018(复现赛) (ctfer.vip)
附件链接:OtterCTF.7z
1、What the password?
you got a sample of rick's PC's memory. can you get his user password?
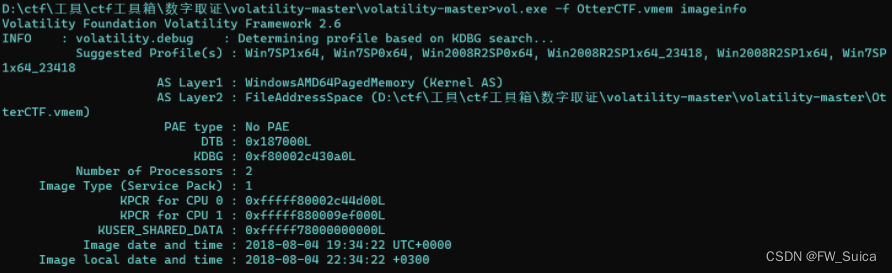
惯例,拿到附件以后先分析一下映像的信息
vol.exe -f OtterCTF.vmem imageinfo
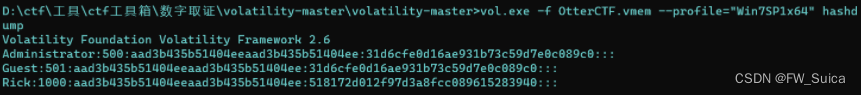
使用hashdump来获取用户hash
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" hashdump
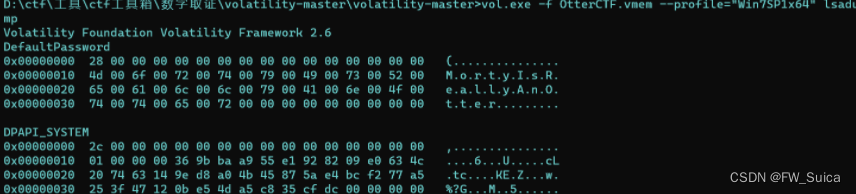
使用lsadump从注册表中提取LSA秘钥信息(mimikatz也可以)
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" lsadump
NSSCTF
2、General Info
Let's start easy - whats the PC's name and IP address?
使用hivelist命令列出注册表
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" hivelist
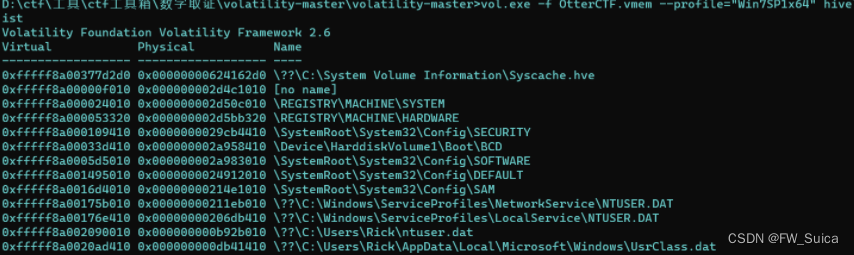
注册表位置0xfffff8a000024010 主机名在注册表的ControlSet001\Control\ComputerName\ComputerName位置
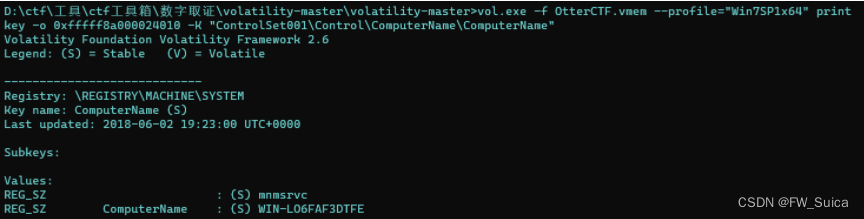
所以
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" printkey -o 0xfffff8a000024010 -K "ControlSet001\Control\ComputerName\ComputerName"
netscan查看网络连接状况
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" netscan
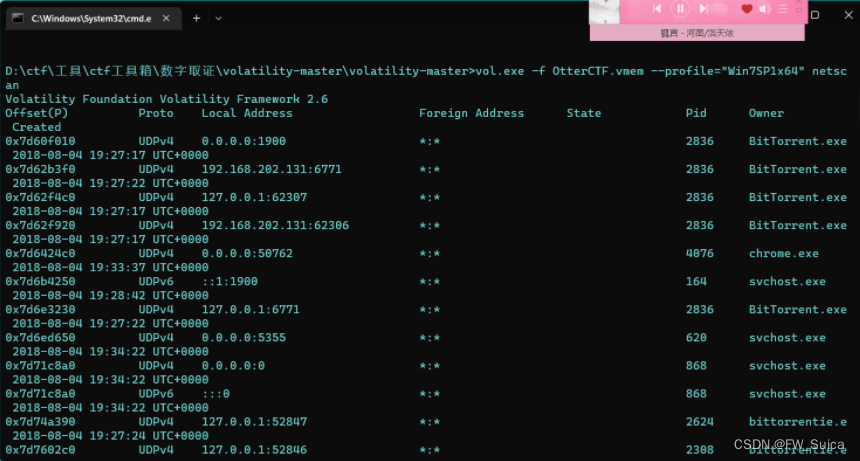
排除0.0.0.0与127.0.0.1 剩下
NSSCTF{WIN-LO6FAF3DTFE-192.168.202.131}
3、Play Time
Rick just loves to play some good old videogames. can you tell which game is he playing? whats the IP address of the server?
使用pstree命令以树的形式来列出正在进行的进程
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" pstree

lunarMS是个游戏

netscan命令查看网络连接状况,同时使用grep命令过滤LunarMS
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" netscan | grep "LunarMS"
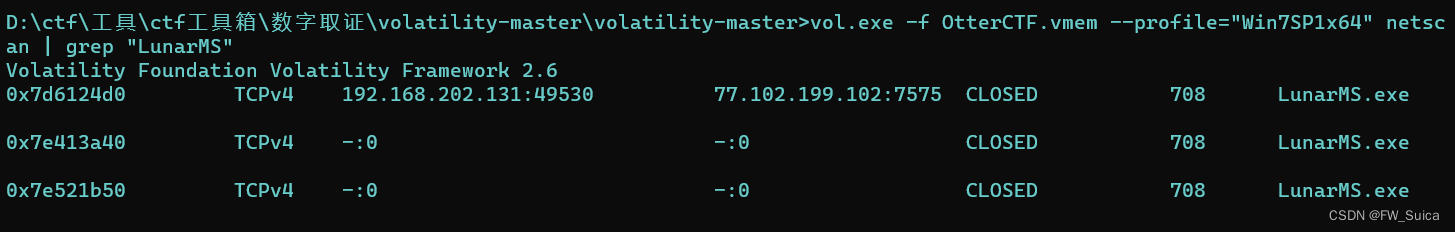
NSSCTF{LunarMS-77.102.199.102}
4、Name Game
We know that the account was logged in to a channel called Lunar-3. what is the account name?
从上一步可以知道 LunarMS的PID是708 使用memdump插件将进程转存出来
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" memdump -p 708 -D .
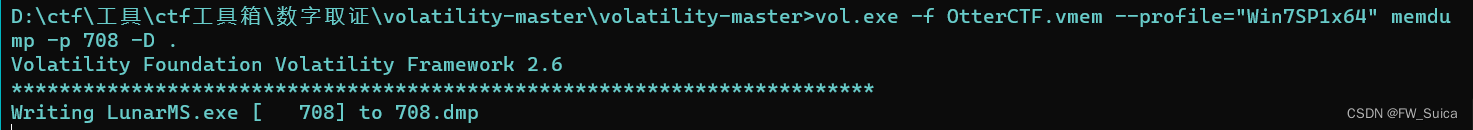
strings 708.dmp > 708.dmp.strings
grep -C 10 "Lunar-3" 708.dmp.strings
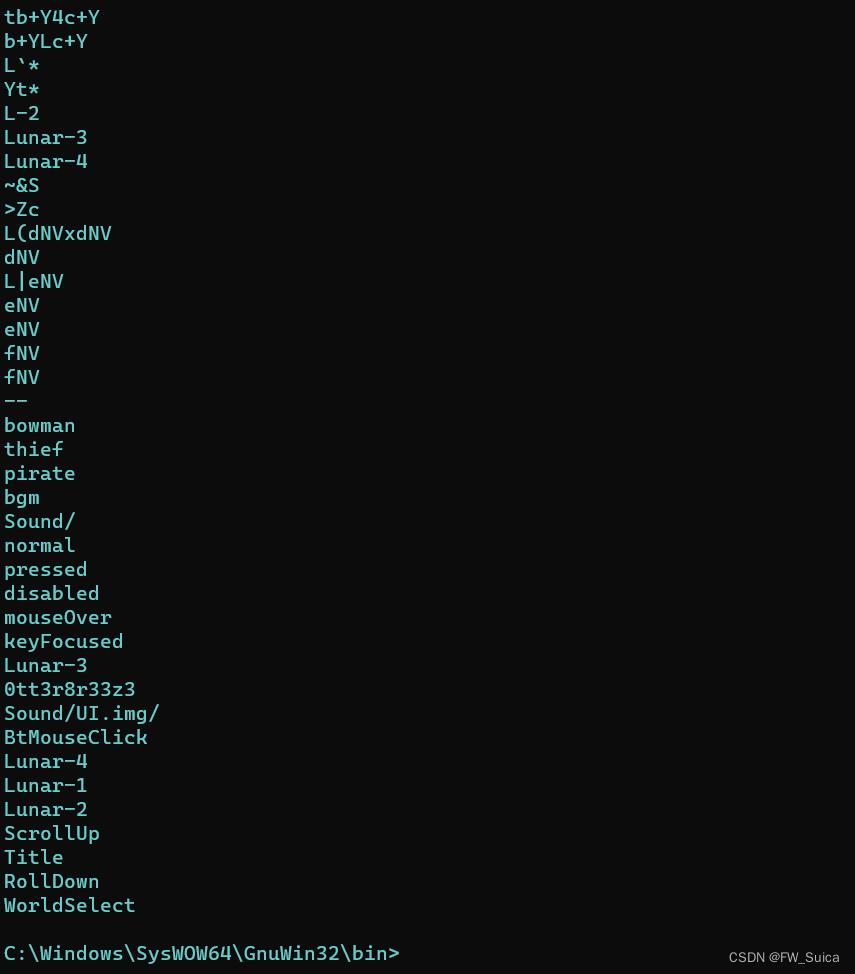
NSSCTF
5、Name Game 2
From a little research we found that the username of the logged on character is always after this signature: 0x64 0x??{6-8} 0x40 0x06 0x??{18} 0x5a 0x0c 0x00{2} What's rick's character's name?
全局搜索
xxd 708.dmp | grep "5a0c 0000"
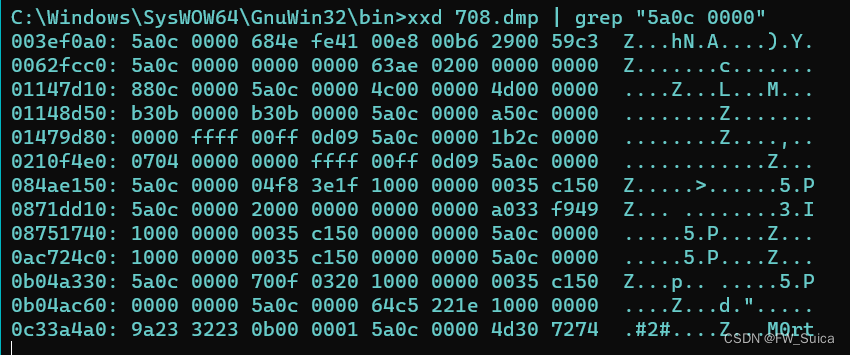
0c33a4ac位置有一个M0rt 尝试xxd出来
xxd -s 0x0c33a4ac -l 16 708.dmp
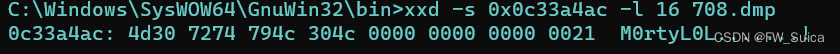
NSSCTF
6、Silly Rick
Silly rick always forgets his email's password, so he uses a Stored Password Services online to store his password. He always copy and paste the password so he will not get it wrong. whats rick's email password?
clipboard直接查看剪贴板
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" memdump -p 708 -D .
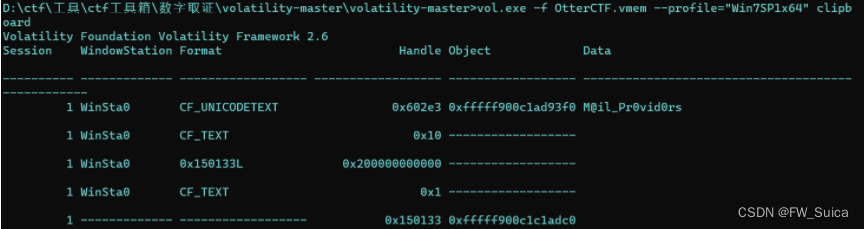
NSSCTF
7、Hide And Seek
The reason that we took rick's PC memory dump is because there was a malware infection. Please find the malware process name (including the extension)
pstree列出进程
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" pstree
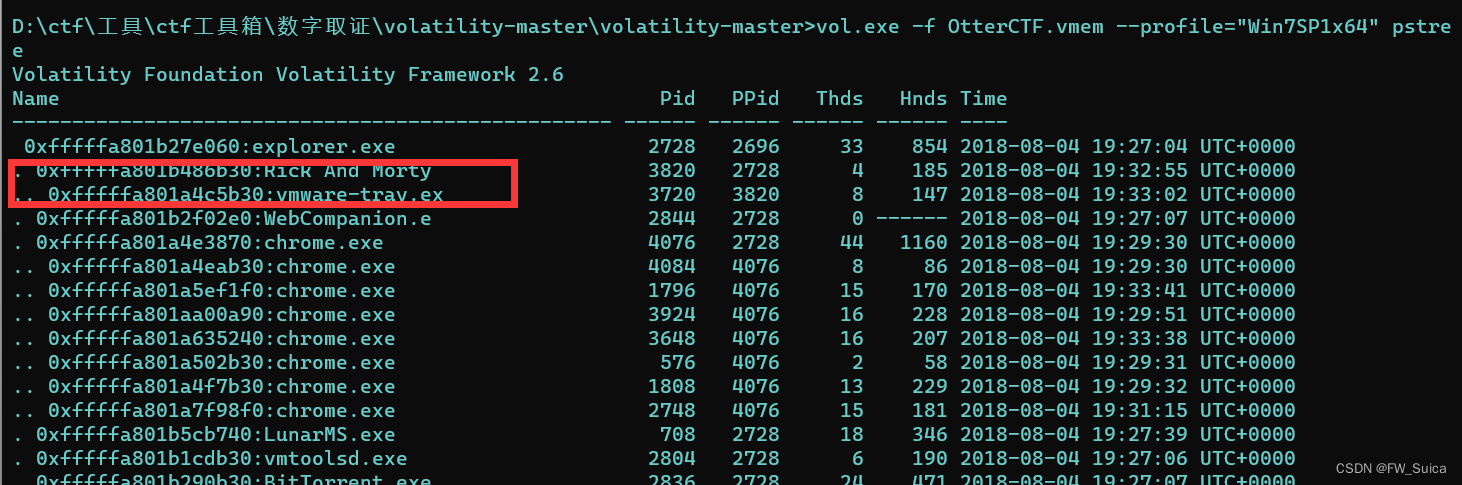
列出此进程下命令行运行的程序
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" cmdline -p 3820,3720
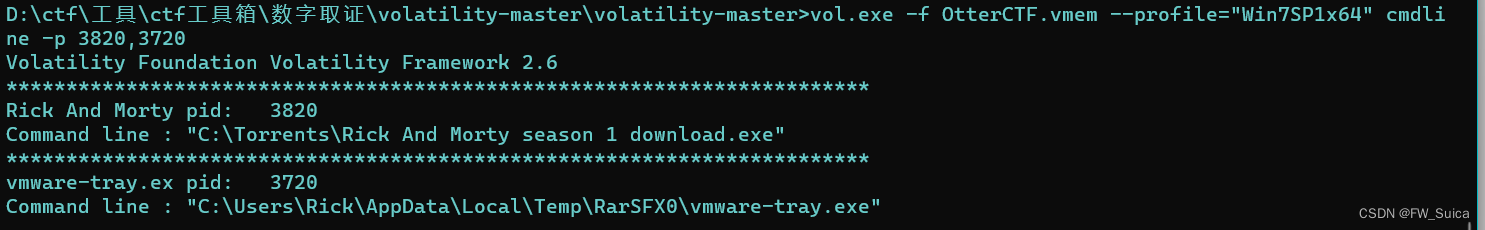
NSSCTF
8、Path To Glory
How did the malware got to rick's PC? It must be one of rick old illegal habits..
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" filescan | grep -i "rick and morty"
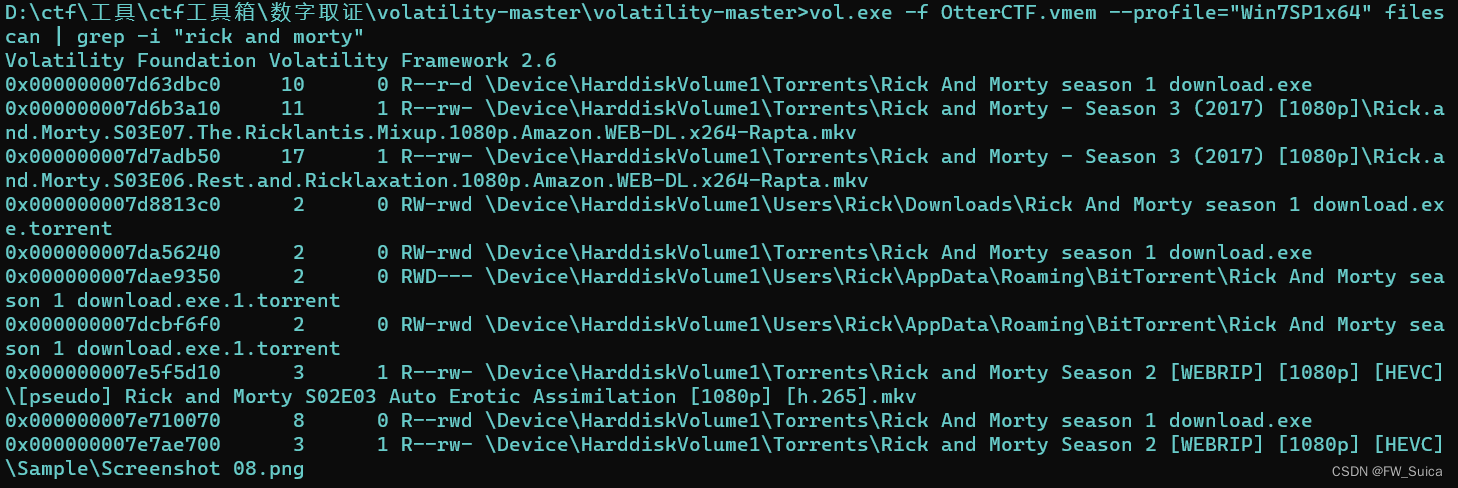
提取文件
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" dumpfiles -Q 0x000000007d8813c0 -D .
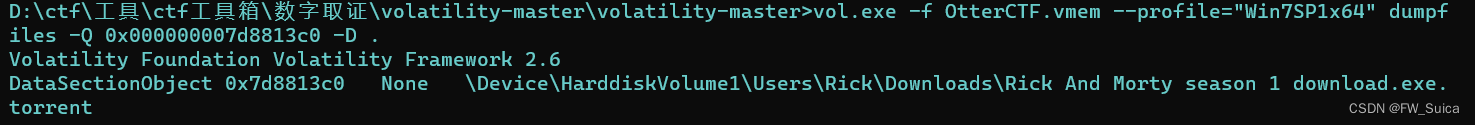
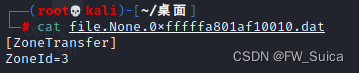
cat file.None.0xfffffa801af10010.dat
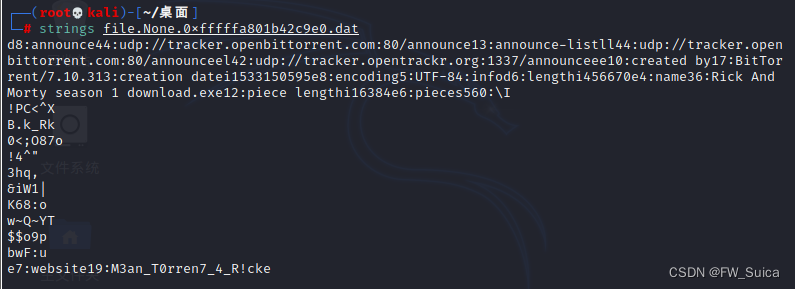
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" dumpfiles -Q 0x000000007dae9350 -D .
strings file.None.0xfffffa801b42c9e0.dat
NSSCTF
9、Path To Glory 2
Continue the search after the way that malware got in.
查找浏览器的历史记录 -i e搜索history
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" filescan | grep -ie "history$"
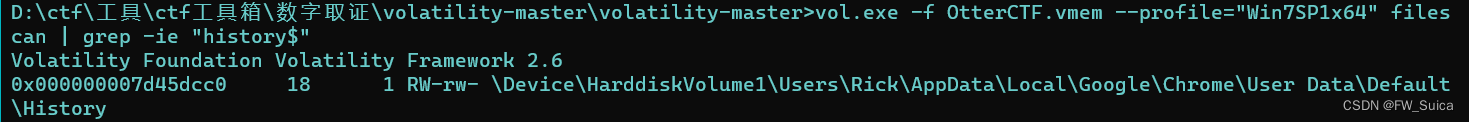
提取数据库文件
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" dumpfiles -Q 0x000000007d45dcc0 -D .
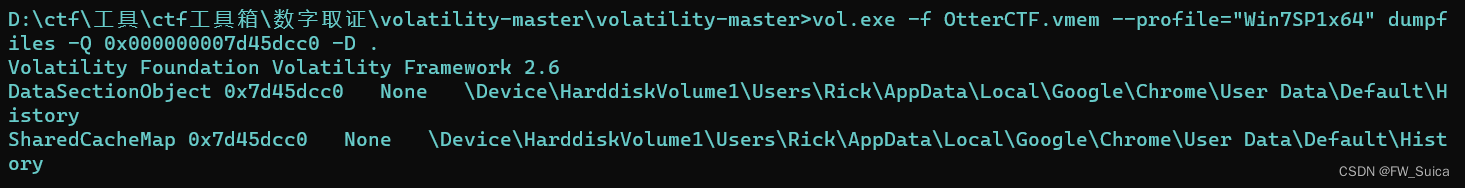
将转存文件重命名后使用sqlite3访问并执行sql查询语句
select current_path, site_url from downloads;
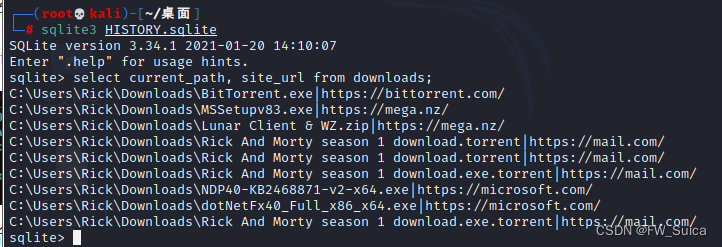
可以看到种子文件的下载来源是https://mail.com/
重定向至文本后进行全局搜索
strings OtterCTF.vmem > OtterCTF.vmem.strings
grep "@mail.com" OtterCTF.vmem.strings
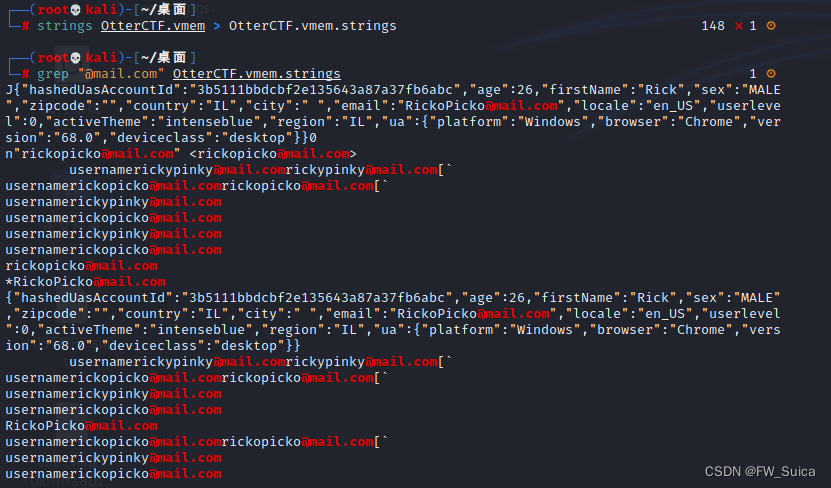
显示电子邮件地址后的20行
grep -A 20 "rickopicko@mail.com" OtterCTF.vmem.strings
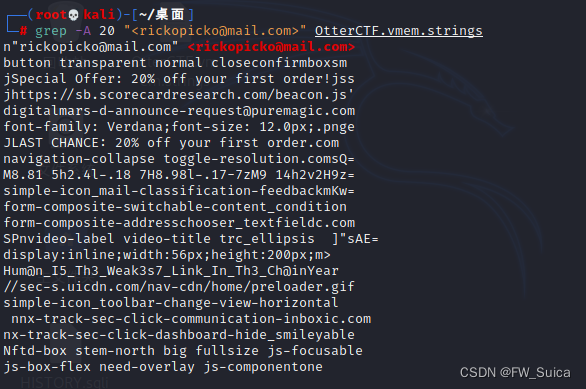
NSSCTF
10、Bit 4 Bit
We've found out that the malware is a ransomware. Find the attacker's bitcoin address.
勒索软件总喜欢把勒索标志丢在显眼的地方,所以搜索桌面的记录
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" filescan | grep "Desktop"
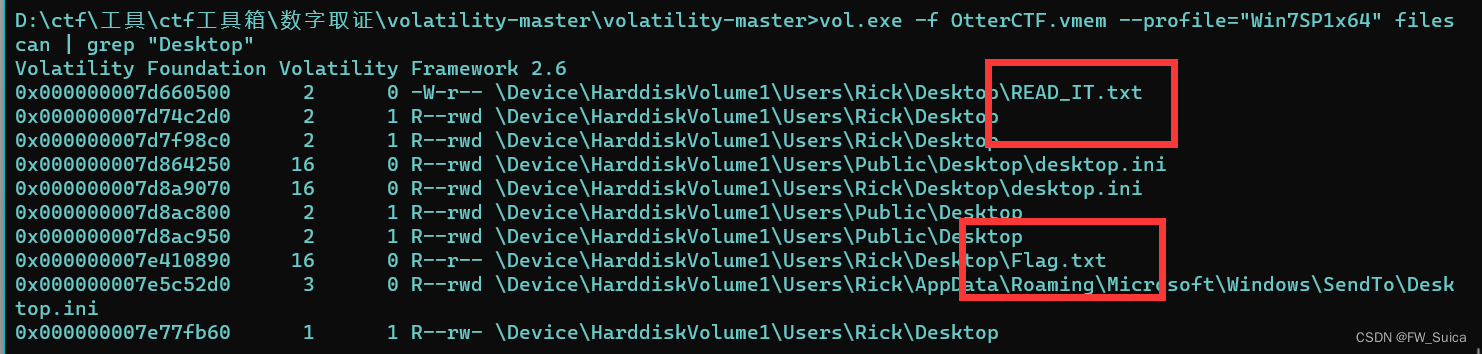
提取read_it
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" dumpfiles -Q 0x000000007d660500 -D .
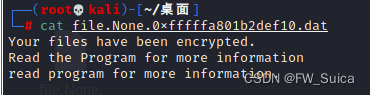
提示我们查看程序获得更多信息(就是上面的VMware-tray.exe)
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" memdump -p 3720 -D .
提取后 根据题目提示 ransomware 搜索赎金相关内容
strings -e l 3720.dmp | grep -i -A 5 "ransomware"
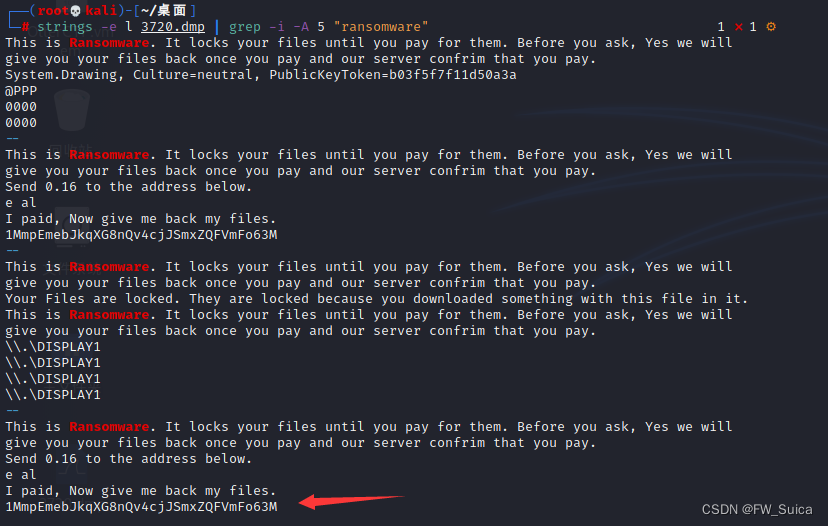
NSSCTF
11、Graphic's For The Weak
There's something fishy in the malware's graphics.
使用procdump转存进程的可执行文件
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" procdump -p 3720 -D .
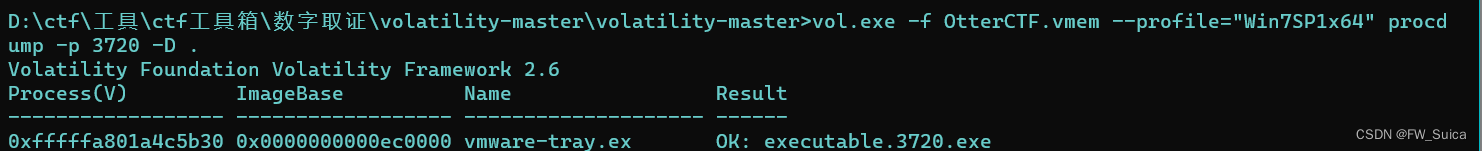
binwalk分析文件
binwalk executable.3720.exe
foremost分离出图片

NSSCTF
12、Recovery
Rick got to have his files recovered! What is the random password used to encrypt the files?
重定向文本
strings -e l 3720.dmp > 3720.dmp.strings
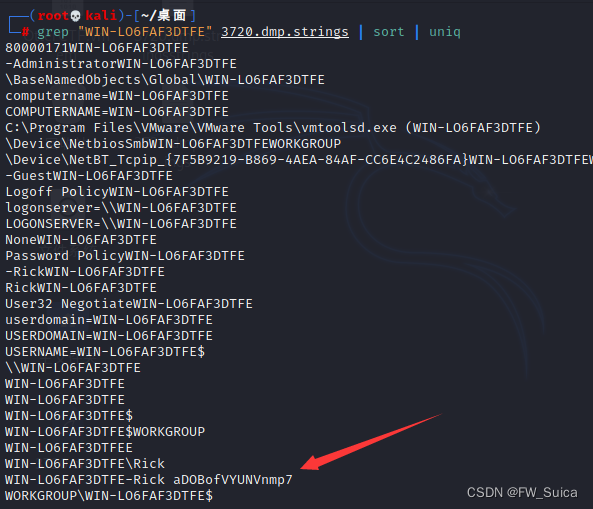
全局搜索主机名相关
grep "WIN-LO6FAF3DTFE" 3720.dmp.strings | sort | uniq
grep -C 5 "aDOBofVYUNVnmp7" 3720.dmp.strings
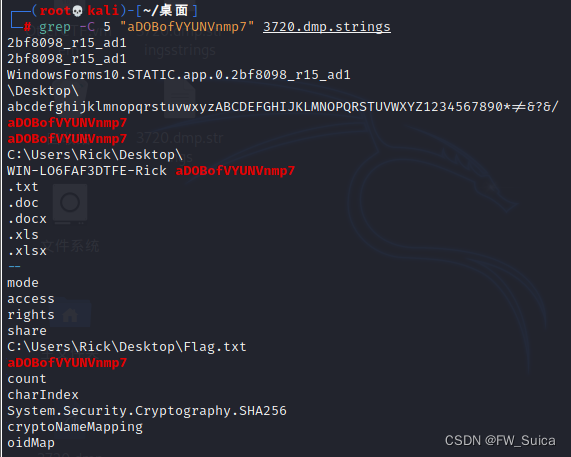
NSSCTF
13、Closure
Now that you extracted the password from the memory, could you decrypt rick's files?
已知这是个勒索软件,考虑沙箱上搜搜)
先检查勒索软件的hash值
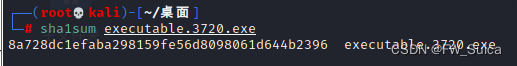
搜搜
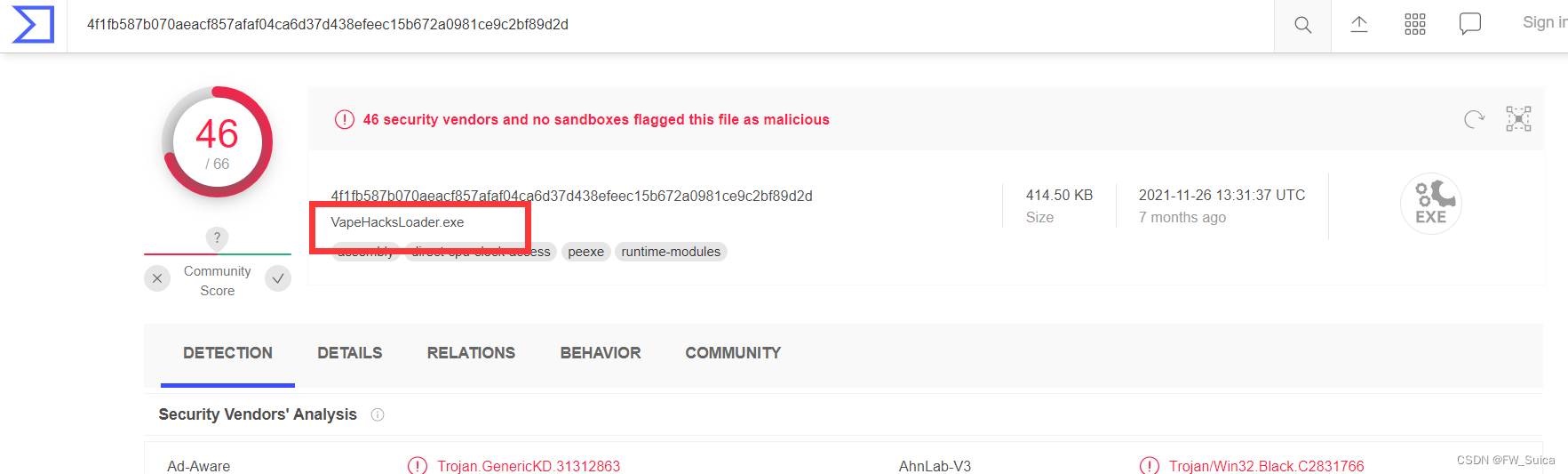
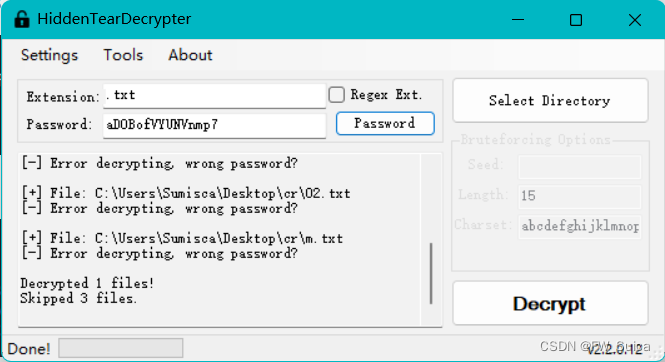
结合前面分离出来的图片中的 $ ucyLocker 搜索可知$ucyLocker是开源Hidden Tear勒索软件的变体,搜索找到解密器:Download Hidden Tear Decrypter (bleepingcomputer.com)
提取之间看到的flag.txt文件
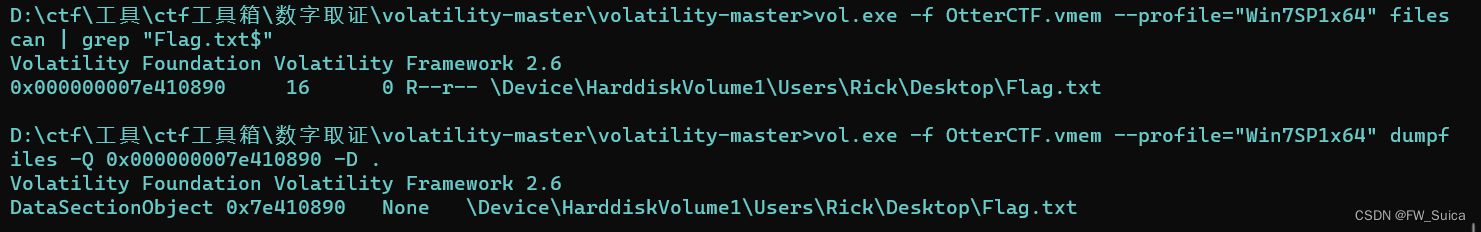
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" filescan | grep "Flag.txt$"
vol.exe -f OtterCTF.vmem --profile="Win7SP1x64" dumpfiles -Q 0x000000007e410890 -D .
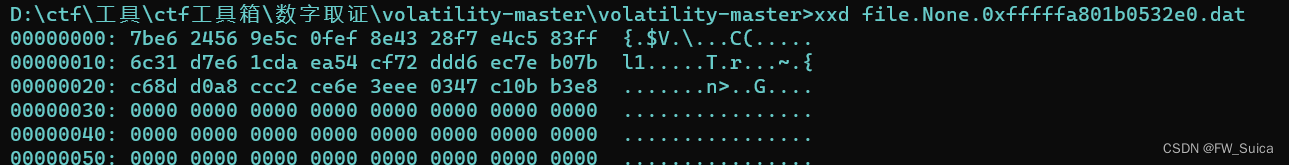
瞅一眼文件
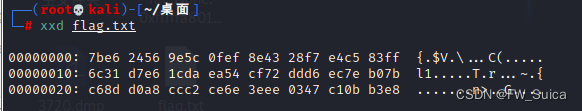
xxd file.None.0xfffffa801b0532e0.dat
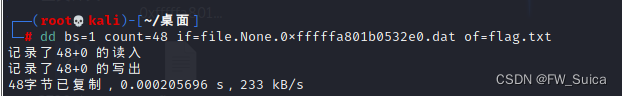
把前面几个字节提取出来并且重命名文件
dd bs=1 count=48 if=file.None.0xfffffa801b0532e0.dat of=flag.txt
xxd flag.txt
运行解密器
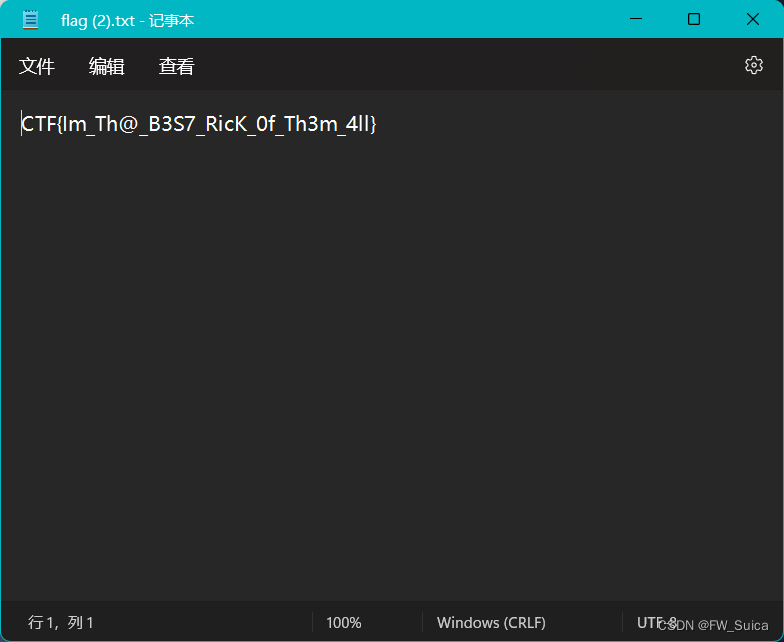
NSSCTF


