k8s 图形化生成yaml,告别手写
安装说明
参数解析: serverName: 集群别名 serverAddress: Kubernetes APIServer地址 serverAdminUser: Kubernetes管理员账号(需要配置basic auth) serverAdminPassword: Kubernetes管理员密码 serverAdminToken: Kubernetes管理员Token // 暂不支持 serverDashboardUrl: Kubernetes官方dashboard地址,1.x版本需要添加/#!,2.x需要添加/# kubeConfigPath: Kubernetes kube.config路径(绝对路径,这个路径不是宿主机的本地路径,而是1.2小节secret的挂载路径,一般可以不改/mnt) harborConfig: 对于多集群管理的情况下,可能会存在不同的harbor仓库,配置此参数可以在拷贝资源的时候自动替换harbor配置 kubeConfigPath 通过secret挂载到容器的/mnt目录或者其他目录
创建secret
[root@master01 ratel]# vi servers.yaml
- serverName: 'test1' serverAddress: 'https://127.0.0.1:8443' #serverAdminUser: 'xxx' #serverAdminPassword: 'xxx#' # serverAdminToken: 'null' serverDashboardUrl: "https://172.16.1.11:30001/#" production: 'false' kubeConfigPath: "/mnt/test1.config" harborConfig: "HarborUrl, HarborUsername, HarborPassword, HarborEmail"
[root@master01 ratel]# kubectl create secret generic ratel-config --from-file=test1.config --from-file=servers.yaml -n kube-system && kubectl create ns kube-users
创建RBAC
创建权限管理namespace [root@master01 ratel]# kubectl create ns kube-users 然后添加如下的ClusterroleBinding [root@master01 ratel]# vim ratel-rbac.yaml apiVersion: v1 items: - apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: annotations: rbac.authorization.kubernetes.io/autoupdate: "true" labels: kubernetes.io/bootstrapping: rbac-defaults rbac.authorization.k8s.io/aggregate-to-edit: "true" name: ratel-namespace-readonly rules: - apiGroups: - "" resources: - namespaces verbs: - get - list - watch - apiGroups: - metrics.k8s.io resources: - pods verbs: - get - list - watch - apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: ratel-pod-delete rules: - apiGroups: - "" resources: - pods verbs: - get - list - delete - apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: ratel-pod-exec rules: - apiGroups: - "" resources: - pods - pods/log verbs: - get - list - apiGroups: - "" resources: - pods/exec verbs: - create - apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: annotations: rbac.authorization.kubernetes.io/autoupdate: "true" name: ratel-resource-edit rules: - apiGroups: - "" resources: - configmaps - persistentvolumeclaims - services - services/proxy verbs: - patch - update - apiGroups: - apps resources: - daemonsets - deployments - deployments/rollback - deployments/scale - statefulsets - statefulsets/scale verbs: - patch - update - apiGroups: - autoscaling resources: - horizontalpodautoscalers verbs: - patch - update - apiGroups: - batch resources: - cronjobs - jobs verbs: - patch - update - apiGroups: - extensions resources: - daemonsets - deployments - deployments/rollback - deployments/scale - ingresses - networkpolicies verbs: - patch - update - apiGroups: - networking.k8s.io resources: - ingresses - networkpolicies verbs: - patch - update - apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: ratel-resource-readonly rules: - apiGroups: - "" resources: - configmaps - endpoints - persistentvolumeclaims - pods - replicationcontrollers - replicationcontrollers/scale - serviceaccounts - services verbs: - get - list - watch - apiGroups: - "" resources: - bindings - events - limitranges - namespaces/status - pods/log - pods/status - replicationcontrollers/status - resourcequotas - resourcequotas/status verbs: - get - list - watch - apiGroups: - "" resources: - namespaces verbs: - get - list - watch - apiGroups: - apps resources: - controllerrevisions - daemonsets - deployments - deployments/scale - replicasets - replicasets/scale - statefulsets - statefulsets/scale verbs: - get - list - watch - apiGroups: - autoscaling resources: - horizontalpodautoscalers verbs: - get - list - watch - apiGroups: - batch resources: - cronjobs - jobs verbs: - get - list - watch - apiGroups: - extensions resources: - daemonsets - deployments - deployments/scale - ingresses - networkpolicies - replicasets - replicasets/scale - replicationcontrollers/scale verbs: - get - list - watch - apiGroups: - policy resources: - poddisruptionbudgets verbs: - get - list - watch - apiGroups: - networking.k8s.io resources: - networkpolicies - ingresses verbs: - get - list - watch - apiGroups: - metrics.k8s.io resources: - pods verbs: - get - list - watch kind: List metadata: resourceVersion: "" selfLink: "" [root@master01 ratel]# kubectl create -f ratel-rbac.yaml vim ratel-rbac-binding.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: ratel-namespace-readonly-sa roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: ratel-namespace-readonly subjects: - apiGroup: rbac.authorization.k8s.io kind: Group name: system:serviceaccounts:kube-users [root@master01 ratel]# kubectl create -f ratel-rbac-binding.yaml
部署ratel
[root@master01 ratel]# vi ratel.yaml apiVersion: apps/v1 kind: Deployment metadata: labels: app: ratel name: ratel namespace: kube-system spec: replicas: 1 selector: matchLabels: app: ratel strategy: rollingUpdate: maxSurge: 1 maxUnavailable: 0 type: RollingUpdate template: metadata: creationTimestamp: null labels: app: ratel spec: containers: - command: - sh - -c - ./ratel -c /mnt/servers.yaml env: - name: TZ value: Asia/Shanghai - name: LANG value: C.UTF-8 - name: ProRunMode value: prod - name: ADMIN_USERNAME value: admin # 登录用户 - name: ADMIN_PASSWORD value: password #登录密码 image: registry.cn-beijing.aliyuncs.com/dotbalo/ratel:latest imagePullPolicy: Always livenessProbe: failureThreshold: 2 initialDelaySeconds: 10 periodSeconds: 60 successThreshold: 1 tcpSocket: port: 8888 timeoutSeconds: 2 name: ratel ports: - containerPort: 8888 name: web protocol: TCP readinessProbe: failureThreshold: 2 initialDelaySeconds: 10 periodSeconds: 60 successThreshold: 1 tcpSocket: port: 8888 timeoutSeconds: 2 resources: limits: cpu: 500m memory: 512Mi requests: cpu: 500m memory: 512Mi volumeMounts: - mountPath: /mnt name: ratel-config dnsPolicy: ClusterFirst imagePullSecrets: - name: myregistrykey restartPolicy: Always schedulerName: default-scheduler securityContext: {} terminationGracePeriodSeconds: 30 volumes: - name: ratel-config secret: defaultMode: 420 secretName: ratel-config
需要更改的内容如下:
ProRunMode: 区别在于dev模式打印的是debug日志, 其他模式是info级别的日志, 实际使用时应该配置为非dev
ADMIN_USERNAME: ratel自己的管理员账号
ADMIN_PASSWORD: ratel自己的管理员密码
实际使用时账号密码应满足复杂性要求,因为ratel可以直接操作所有配置的资源。
其他无需配置, 端口配置暂不支持。[root@master01 ratel]# kubectl apply -f ratel.yaml
创建service
[root@master01 ratel]# vi ratel-service.yaml 创建ratel Service的文件如下: apiVersion: v1 kind: Service metadata: labels: app: ratel name: ratel namespace: kube-system spec: ports: - name: container-1-web-1 port: 8888 protocol: TCP targetPort: 8888 selector: app: ratel type: NodePort [root@master01 ratel]# kubectl apply -f ratel-service.yaml
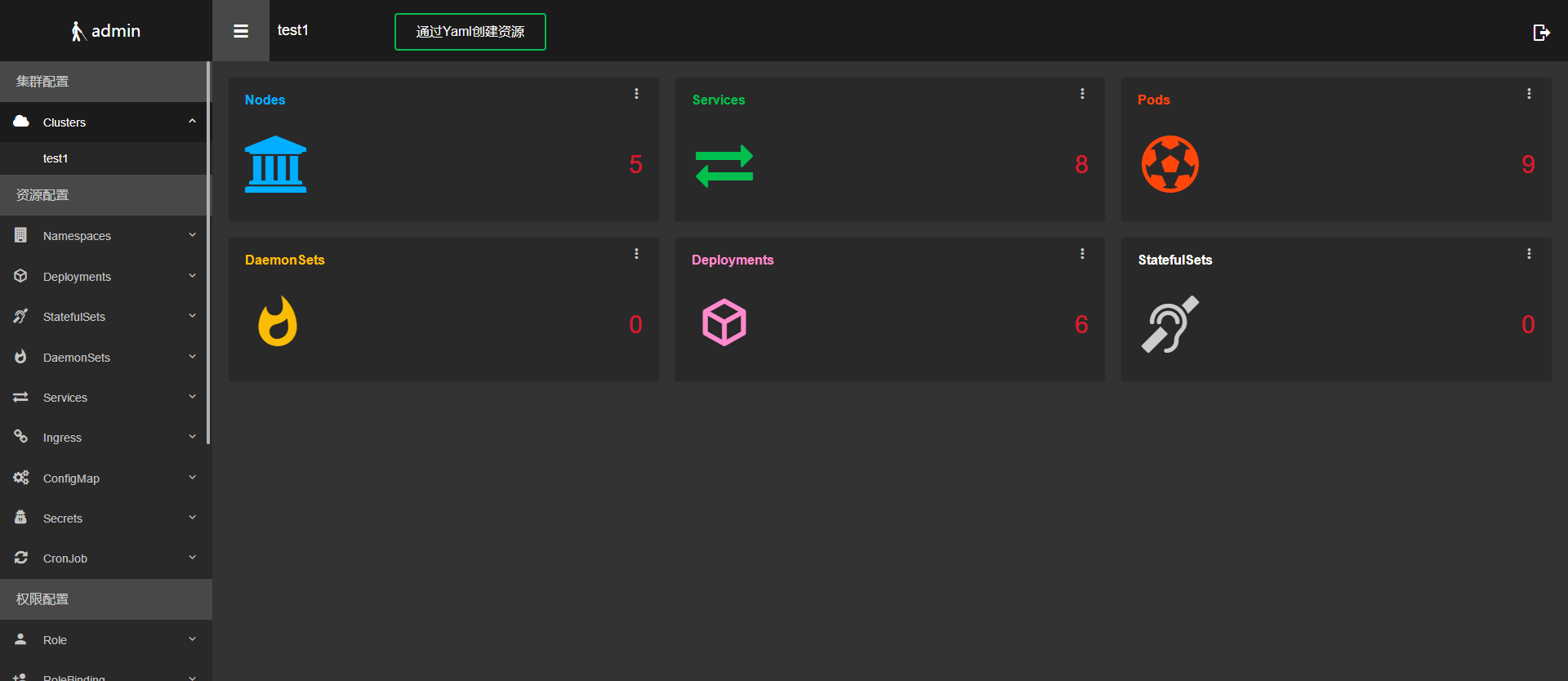
#参考链接:https://www.cnblogs.com/dukuan/p/13524622.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号