Exp5 信息搜集与漏洞扫描
非非非非常抱歉!
本人是课题负责人,但是由于前两天在openvas上卡了一段时间,博客做的拖沓了,给各位道歉!🤐

我看其他负责人和组长写的都很清晰了,我的博客写了一些我的体会,主要放在前面,还希望刚开始做的同学可以看一看。操作部分我以代码段为主,方便大家查看。
实验概述
本次实验的难度不大,就是掌握信息搜集的最基础技能与常用工具的使用方法,命令都很简单,大家在做的时候知道自己在做什么就好,不要单纯的输入命令,我在操作部分也尽我所能地解释了一部分操作,引入了一些知识点详解。
重点提示
metasploit模块使用的一般步骤
什么是metasploit?
Metasploit是一款开源的安全漏洞检测工具……Metasploit是一个免费的、可下载的框架,通过它可以很容易地获取、开发并对计算机软件漏洞实施攻击……它本身附带数百个已知软件漏洞的专业级漏洞攻击工具。
百度百科的索引官网是(http://www.metasploit.cn),但这个直接是打不开的,如果直接把后缀的“cn”改成“com”,就可以导向(https://www.metasploit.com),倒是可以打开的,内有metasploit的详细介绍,metasploit也有Windows版本,大家也可以试试。
本实验中的metasploit
我们可以把metasploit简单的理解成一个工具箱,它统一了应用于计算机系统与网络设备安全所需的各类工具的“规格”,我们需要什么,就使用什么。
本实验中大量使用到metasploit,基本步骤可以归纳如下:
use [模块名称]
set [参数]
……
set [参数]
show options
run/exploit
理解起来也很容易,使用什么工具,设定何种参数,比如RHOST、THREADS等,检视一下工具的参数,开始探测(运行)。
有以上的理解,那么本次实验中使用metasploit就有了直观的认识。
metasploit支持多行一起输入,可以先编辑好几行的命令,使用ctrl+shift+c和ctrl+shift+v直接输入命令。
metasploit的更详细用法
https://www.fujieace.com/metasploit/
以上网站有metasploit各类模块的使用方法,我在实验中也测试了一些,博文比较具有实践性,大家有兴趣可以试试。
Openvas的安装提示
什么是Openvas?
OpenVAS is a full-featured vulnerability scanner. Its capabilities include unauthenticated testing, authenticated testing, various high level and low level Internet and industrial protocols, performance tuning for large-scale scans and a powerful internal programming language to implement any type of vulnerability test.
The scanner is accompanied by a vulnerability tests feed with a long history and daily updates. This Greenbone Community Feed includes more than 50,000 vulnerability tests.
简单来说,OpenVAS (Open Vulnerability Assessment System)是开放式漏洞评估系统,其核心部件是一个服务器,包括一套望楼漏洞测试程序,可以检测远程系统和应用程序中的安全问题。
名词扫盲
| 名称 | 功能 |
|---|---|
| gvmd | GVM10自带的守护进程 |
| openvasmd | GVM9及之前的守护进程的叫法 |
| openvassd | GVM的扫描器进程,作用就是进行漏洞扫描,并将结果反馈给管理模块。 |
| OSPd | 多个扫描器之间使用OSP协议进行通信,而OSPd就是通信进程。 |
| GOS | 全称Greenbone Operating System。GSM设备的操作系统。提供商业版本,具有企业支持功能的GVM框架。 |
| GSM | 全称Greenbone Security Manager,绿骨公司系列产品之一,常以应用程序或虚拟机形式出现。 |
| GMP | 全称Greenbone Management Protocol,听名字就知道是管理协议,gvmd和openvasmd使用该协议、基于XML与其他模块进行通信,以前叫OMP。 |
| OSP | 全称Open Scanner Protocol,多种绿骨公司产品之间用于通信的协议 |
| GVM | 全称Greenbone Vulnerability Manager,这是许多服务的一个框架,作为一个商业产品也是组成GSM的一部分,以前直接叫openvas。 |
| GVM9 | GVM9代版本,也叫OpenVas9,用在GOS 4代系列。 |
| GVM10 | GVM10代版本,用在GOS 5代系列。 |
| GSE | 全称Greenbone Source Edition,绿骨应用栈,支撑漏洞扫描,漏洞管理,GVM等,用以支持第三方调用,比如Linux的某个分支提供GVM,但它是以GSE为基础构建的。 |
本文作者:LittleT1ger,来自FreeBuf.COM
地址:https://www.freebuf.com/sectool/226016.html
官方参考文档:https://readthedocs.org/projects/gvm-tools/downloads/pdf/latest/
怎么安装Openvas?
Openvas的安装花了我很长时间,我首先和大家说我最后的解决办法:
重装Kali

我听说不少朋友已经这么做了23333
我回想我的安装过程最大的问题可能是——硬盘不足
如果按照kali的硬盘推荐大小20G,在经过几次实验过后,硬盘可能已经有些满了(如果大家不像我电脑内存256G,财大气粗给kali50G,这话当我没说=。=),这时候安装openvas,很可能遇到安装不完全的问题。
这个时候可能有朋友就要问了,如果安装不了,系统为什么会允许开始安装呢?

如果大家细致理解老师知道手册里安装逐条命令的意义,其实能够猜到一些,除了openvas本体,还有许多的数据需要安装,与软件相匹配的环境未完成,软件虽然已经下载,但永远无法运行。
之所以写在前面,就是希望大家切不要走我的老路,以下几个建议可能不全对,但是大家心里留个底,也好。
- 首先使用“df -lh ”查看一下硬盘大小,最好留在2G左右,我的新虚拟机安装完成之后占用了1.1G。如果更新过程中有缺项是会有提示的,但是命令行比较长,大家可能不太会注意到。
- “apt-get update”和“apt-get dist-upgrade”是类似“更新系统”的操作,这两个操作与“apt-get install openvas”乃至后面的“openvas-check-setup”顺序一定不要颠倒。
- 一定要记得使用虚拟机快照功能(我不会是最后一个开始用这个的吧呜呜),如果发现自己做的不对,可以随时回头,相比较重装系统,占用一些硬盘空间不能好的太多。
- 如果你的安装没有问题,那么你的安装一定顺风顺水!如果遇到些奇奇怪怪的、上网都查不出来的问题,本人诚恳地建议您回头是岸,可以稍作研究,能解决更好,切勿执迷不悟=。=
实验步骤
各种搜索技巧的应用
metasploit提供的msf-dir_scanner网页目录结构扫描辅助模块
dir_scanner是Metasploit当中的一个辅助模块,参数设置完成后使用exploit或者run命令发起攻击。
开始攻击前的参数设置:
THREADS 攻击使用的线程数,数值越大力度越大,数值小不容易被发现
RHOSTS 目标网址或IP地址,url或IP前后http://和具体路径
以本人的博客为例,使用命令:
use auxiliary/scanner/http/dir_scanner
set rhosts https://www.cnblogs.com/PeterDon-WorkHardPlayHard/
set threads 30
exploit
结果:
msf5 auxiliary(scanner/http/dir_scanner) > exploit
[*] Detecting error code
[*] Detecting error code
[*] Detecting error code
[*] Using code '502' as not found for 101.37.113.127
[*] Using code '502' as not found for 114.55.187.58
[*] Using code '502' as not found for 114.55.205.139
[*] Scanned 3 of 3 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/http/dir_scanner) > traceroute www.cnblogs.com
[*] exec: traceroute www.cnblogs.com
IP路由侦查工具traceroute
这个大家都比较熟悉了
命令
traceroute www.cnblogs.com
结果:
traceroute to www.cnblogs.com (114.55.205.139), 30 hops max, 60 byte packets
1 _gateway (192.168.233.2) 0.349 ms 0.271 ms 0.224 ms
2 * * *
3 * * *
4 * * *
5 * * *
搜索特定类型的文件
这个操作老师上课已经讲过,直接使用百度也可以使用图形化界面调整一些参数
命令:
site:edu.cn filetype:xls
图示:
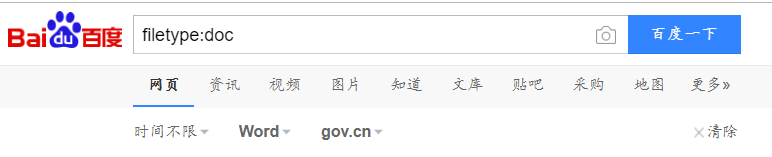

DNS IP注册信息的查询(以www.baidu.com为例)
whois、nslookup、dig的使用方式基本一致。
whois
直接在metasploit终端输入
whois [目标网站]
通过whois我们即可找到所谓的“3R”信息,这里不赘述了。
附录里有我查看百度的命令行结果。
nslookup
msf5 auxiliary(scanner/http/dir_scanner) > nslookup baidu.com
[*] exec: nslookup baidu.com
Server: 192.168.233.2
Address: 192.168.233.2#53
Non-authoritative answer:
Name: baidu.com
Address: 39.156.69.79
Name: baidu.com
Address: 220.181.38.148
dig
msf5 auxiliary(scanner/http/dir_scanner) > dig baidu.com
[*] exec: dig baidu.com
; <<>> DiG 9.11.5-P1-1-Debian <<>> baidu.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 12558
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 5, ADDITIONAL: 5
;; QUESTION SECTION:
;baidu.com. IN A
;; ANSWER SECTION:
baidu.com. 5 IN A 39.156.69.79
baidu.com. 5 IN A 220.181.38.148
;; AUTHORITY SECTION:
baidu.com. 5 IN NS ns4.baidu.com.
baidu.com. 5 IN NS ns1.baidu.com.
baidu.com. 5 IN NS ns2.baidu.com.
baidu.com. 5 IN NS ns7.baidu.com.
baidu.com. 5 IN NS ns3.baidu.com.
;; ADDITIONAL SECTION:
ns2.baidu.com. 5 IN A 220.181.33.31
ns3.baidu.com. 5 IN A 112.80.248.64
ns4.baidu.com. 5 IN A 14.215.178.80
ns1.baidu.com. 5 IN A 202.108.22.220
ns7.baidu.com. 5 IN A 180.76.76.92
;; Query time: 10 msec
;; SERVER: 192.168.233.2#53(192.168.233.2)
;; WHEN: 二 4月 21 09:24:30 CST 2020
;; MSG SIZE rcvd: 229
IP-address
还可使用IP-address网站,使用上述方法查到的IP进行搜索即可。
基本的扫描技术(以自己主机为目标)
主机发现
做这一部分实验的时候可以再打开一个虚拟机,便于探查,不过要注意虚拟机的网络设置,可以使用ip add和ping查看网络状态。
ping
这个大家都相当熟悉了,在Windows即可实现。
win+R
cmd
ping www.baidu.com
ping命令 发送ICMP报文的方法检测活跃主机
namp
kali其实也自带了nmap(我经常手滑达成namp,然后报错找不到命令=。=)
root@kali-2-20174306:~# nmap -sn 192.168.124.121
Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-22 00:32 CST
Nmap scan report for 192.168.124.121
Host is up.
Nmap done: 1 IP address (1 host up) scanned in 0.08 seconds
metasploit
位于modules/auxiliary/scanner/discovery 主要有
- arp_sweep
- ipv6_multicast_ping
- ipv6_neighbor
- ipv6_neighbor_router_advertise
- ment, udp_probe,udp_sweep
arp_sweep一看就知道使用arp扫描本地局域网的活跃主机,metasploit模块的一般思路这里就不再赘述了,如果使用其他模块,操作基本一致,可以提前使用show命令,查看有哪些参数。
命令:
use auxiliary/scanner/discovery/arp_sweep
show options
set RHOSTS 192.168.233.135/24
set THREADS 30
exploit
结果:
msf5 auxiliary(scanner/discovery/arp_sweep) > exploit
[+] 192.168.233.1 appears to be up (VMware, Inc.).
[+] 192.168.233.2 appears to be up (VMware, Inc.).
[+] 192.168.233.254 appears to be up (VMware, Inc.).
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
端口扫描
metasploit提供的auxiliary/scanner/portscan/tcp
命令:
use auxiliary/scanner/portscan/tcp
show options
set RHOSTS 192.168.233.135/24
set THREADS 30
exploit
这里能导出很长的报表,可能需要花些时间,这里列举一部分:
msf5 auxiliary(scanner/portscan/tcp) > exploit
[+] 192.168.233.1: - 192.168.233.1:7 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:9 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:13 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:19 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:17 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:135 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:139 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:443 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:445 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:902 - TCP OPEN
[+] 192.168.233.1: - 192.168.233.1:912 - TCP OPEN
……
nmap
使用nmap可以探测开放的TCP服务
命令:
nmap -sS [IP]
如果要探测本机Windows的话,需要关闭防火墙和防护软件。
Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-22 00:44 CST
Nmap scan report for 192.168.43.1
Host is up (0.00011s latency).
Not shown: 988 closed ports
PORT STATE SERVICE
7/tcp open echo
9/tcp open discard
13/tcp open daytime
17/tcp open qotd
19/tcp open chargen
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
902/tcp open iss-realsecure
912/tcp open apex-mesh
1688/tcp open nsjtp-data
nmap详解:https://www.cnblogs.com/LyShark/p/10637507.html
| 参数 | 功能 |
|---|---|
| -sS/sT/sA/sW/sM | 使用TCP SYN方式扫描TCP端口 |
| -sU | 指定使用UDP扫描方式确定目标主机的UDP端口状况 |
| -sN/sF/sX | 指定使用TCP Null, FIN, and Xmas scans秘密扫描方式来协助探测对方的TCP端口状态 |
| -sO | 使用IP protocol 扫描确定目标机支持的协议类型 |
OS及服务版本探测
命令:
nmap -sV [IP]
本机结果:
msf5 > nmap -sV 192.168.43.1
[*] exec: nmap -sV 192.168.43.1
Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-21 16:45 CST
Nmap scan report for 192.168.43.1
Host is up (0.00051s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
7/tcp open echo
9/tcp open discard?
13/tcp open daytime
17/tcp open qotd Windows qotd (English)
19/tcp open chargen
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/https
445/tcp open microsoft-ds?
902/tcp open ssl/vmware-auth VMware Authentication Daemon 1.10 (Uses VNC, SOAP)
912/tcp open vmware-auth VMware Authentication Daemon 1.0 (Uses VNC, SOAP)
1688/tcp open msrpc Microsoft Windows RPC
这里举例分析一下:
Remote Procedure Call (RPC)调用是WINDOWS使用的一个协议,提供进程间交互通信,允许程序在远程机器上运行任意程序
NetBiOS 即Network Basic Input Output System(网络基本输入输出系统),是一种应用程序接口(API),
具体服务的查点
这里的服务就是指主机的一些服务,操作步骤基本一致。
telnet
=。=大二的时候学Java用过telnet,其实win10上的telnet已经是阉割版了,telnet里的“tel”就已经显现出它的历史悠久。
use auxiliary/scanner/telnet/telnet_version
set RHOSTS 192.168.43.1
set THREADS 30
run
msf5 auxiliary(scanner/telnet/telnet_version) > run
[-] 192.168.43.1:23 - A network issue has occurred: The connection was refused by the remote host (192.168.43.1:23).
[*] 192.168.43.1:23 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
SSH
SSH 为 Secure Shell 的缩写……SSH 为建立在应用层基础上的安全协议。SSH 是较可靠,专为远程登录会话和其他网络服务提供安全性的协议。
use auxiliary/scanner/ssh/ssh_version
set RHOSTS 192.168.43.1
set THREADS 30
run
msf5 auxiliary(scanner/ssh/ssh_version) > run
[*] 192.168.43.1:22 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Oracle数据库服务查点
use auxiliary/scanner/oracle/tnslsnr_version
set RHOSTS 192.168.43.1
set THREADS 30
run
msf5 auxiliary(scanner/oracle/tnslsnr_version) > run
[*] 192.168.43.1:1521 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
开放代理探测
开放代理指一个能被所有互联网用户访问的代理服务器。
use auxiliary/scanner/http/open_proxy
set RHOSTS 192.168.43.1
run
msf5 auxiliary(scanner/http/open_proxy) > run
[*] Scanned 1 of 1 hosts (100% complete)
漏洞扫描(以自己主机为目标)
Openvas的安装
这里再次提醒大家前述的几条建议:
提前安装、硬盘大小、保证顺序、虚拟机快照、回头是岸
建议大家阅读老师的指导文档:https://gitee.com/wildlinux/NetSec/blob/master/ExpGuides/0x52_漏洞扫描-OpenVAS.md
其实如果安装操作正确,openvas的安装花费的只是时间,大家完全可以睡前执行set-up,早上起来看到“It seems like your OpenVAS-9 installation is OK.”就可以心满意足地开始实验了。
如果openvas成功安装的命令行结果我放在附录,大家可以看一下自己的报错卡在哪一个step。
这里我就粘贴老师的指导文档了,具体方法如下所示:
(1)更新软件包列表。
# apt-get update
执行以上命令后,获取最近的软件包列表。
(2)获取到最新的软件包。
# apt-get dist-upgrade
执行以上命令后,对有更新的包进行下载并安装。
(3)重新安装OpenVAS工具。
# apt-get install openvas
完成以上就代表你的openvas本体基本搞定,but!这事儿没结束
执行检查
openvas-check-setup
根据报错进行运行,这里举个栗子
Step 1: Checking OpenVAS Scanner ...
OK: OpenVAS Scanner is present in version 5.1.3.
OK: redis-server is present in version v=5.0.7.
OK: scanner (kb_location setting) is configured properly using the redis-server socket: /var/run/redis-openvas/redis-server.sock
OK: redis-server is running and listening on socket: /var/run/redis-openvas/redis-server.sock.
OK: redis-server configuration is OK and redis-server is running.
ERROR: The NVT collection is very small.
FIX: Run a synchronization script like greenbone-nvt-sync.
我们可以直接关注 ERROR 和 FIX ,一般FIX的最后一句即为解决办法,这里的解决办法就是
greenbone-nvt-sync
这一步可能要花较长的时间,建议睡觉时运行
举例2:
ERROR: No users found. You need to create at least one user to log in.
It is recommended to have at least one user with role Admin.
FIX: create a user by running 'openvasmd --create-user=<name> --role=Admin && openvasmd --user=<name> --new-password=<password>'
这里的解决办法就是创建用户
create-user=<name> --role=Admin && openvasmd --user=<name> --new-password=<password>'
以下是回头是岸式报错:
真的不是没有办法,只是相较起来重装更直接,因为当你遇到这些问题,就说明可能后续问题更多。
ERROR: No OpenVAS Scanner (openvassd) found.
/usr/bin/openvas-check-setup: 142: cannot create /tmp/openvas-check-setup.log: Permission denied
FIX: Please install OpenVAS Scanner.
/usr/bin/openvas-check-setup: 142: cannot create /tmp/openvas-check-setup.log: Permission denied
翻译:文件创建没有权限,就算已经是root也不行,用chmod改也不行,而且网上基本没有这个报错的解决

ERROR: redis-server is not running or not listening on socket: /var/run/redis/redis-server.sock
FIX: You should start the redis-server or configure it to listen on socket: /var/run/redis/redis-server.sock
翻译:redis的socket有问题,有没有解决办法,有!很详细,但是不一定能成功。
Openvas的使用
做到这里就要恭喜大家,实验快结束了

启动Openvas:
openvas-start
看到运行成功之后就可以直接打开主页:https://127.0.0.1:9392
这里直接点开浏览器可能拦截,莫怕,莫乱点,我们能看懂。
如果发现自己忘了之前敲得是啥用户和密码,回命令行再加一个用户也行
openvasmd --user=admin --new-password=admin
登录之后,点击顺序:
- 绿色图标下的Scans一栏里的Tasks
- Dashboard下方的紫色小魔棒
- 输入本机IP
- 开始扫描
- 扫描完成,点击任务,点击Full and fast,可以看到具体的漏洞报告。
扫描需要花一定时间,建议关闭Windows防护墙和防护软件,不建议扫描的时候乱点,可能报错。
图示:
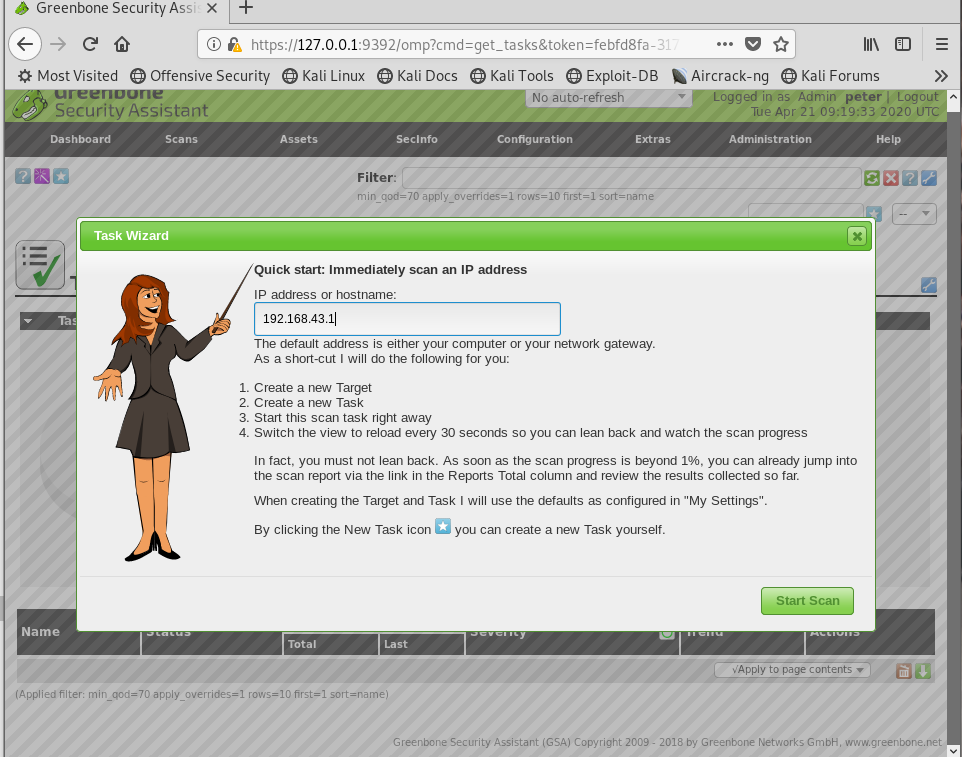
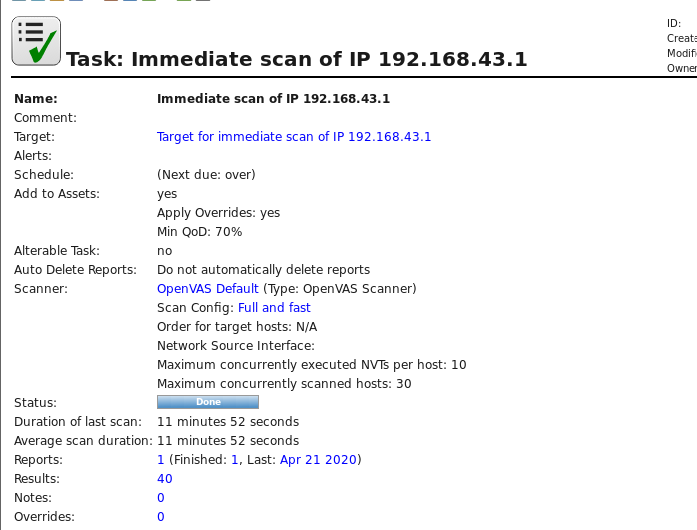
查看漏洞及后续操作
这里我查看了两个漏洞,一个是华为的,另一个是其他同学也试过的FTP,大家可以自行选择。
24 huawei-sa-20180425-02-buffer
点击Full and fast里的家族,就可以看到各个族系的漏洞,下图是华为的漏洞家族:
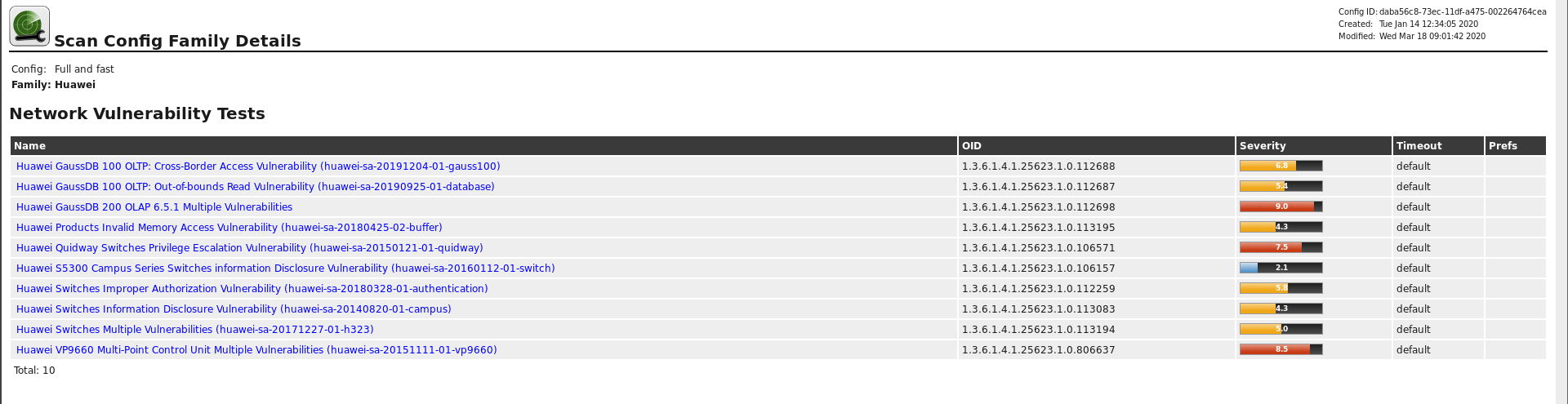
具体到24 huawei-sa-20180425-02-buffer,我查了一下华为官方,找到了这个漏洞报告(https://www.huawei.com/cn/psirt/security-advisories/huawei-sa-20180425-02-buffer-cn)
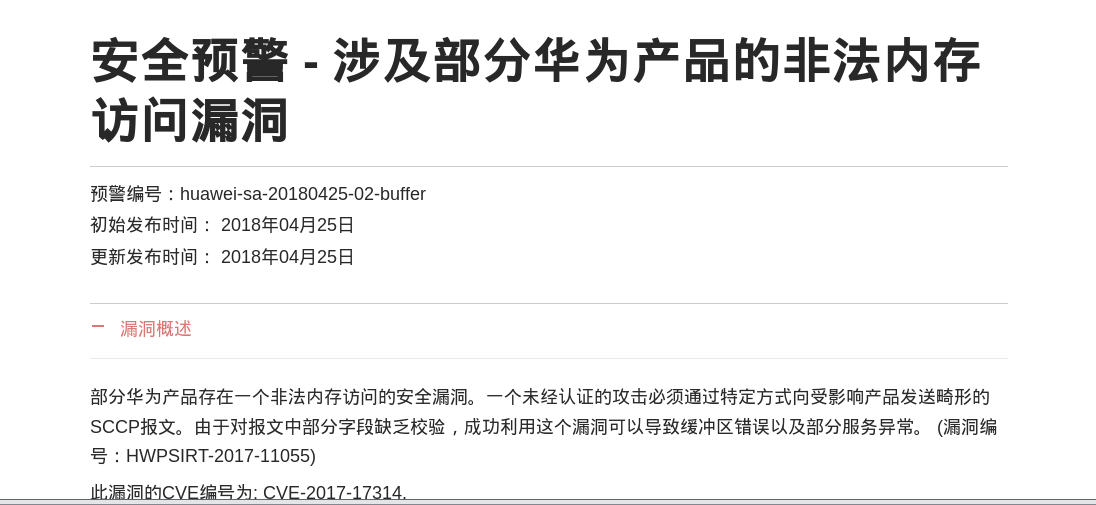
表述是这样的:
部分华为产品存在一个非法内存访问的安全漏洞。一个未经认证的攻击必须通过特定方式向受影响产品发送畸形的SCCP报文。由于对报文中部分字段缺乏校验,成功利用这个漏洞可以导致缓冲区错误以及部分服务异常。 (漏洞编号:HWPSIRT-2017-11055)
此漏洞的CVE编号为: CVE-2017-17314.
华为已发布版本修复该漏洞。
所以解决这个漏洞,及时更新版本即可。
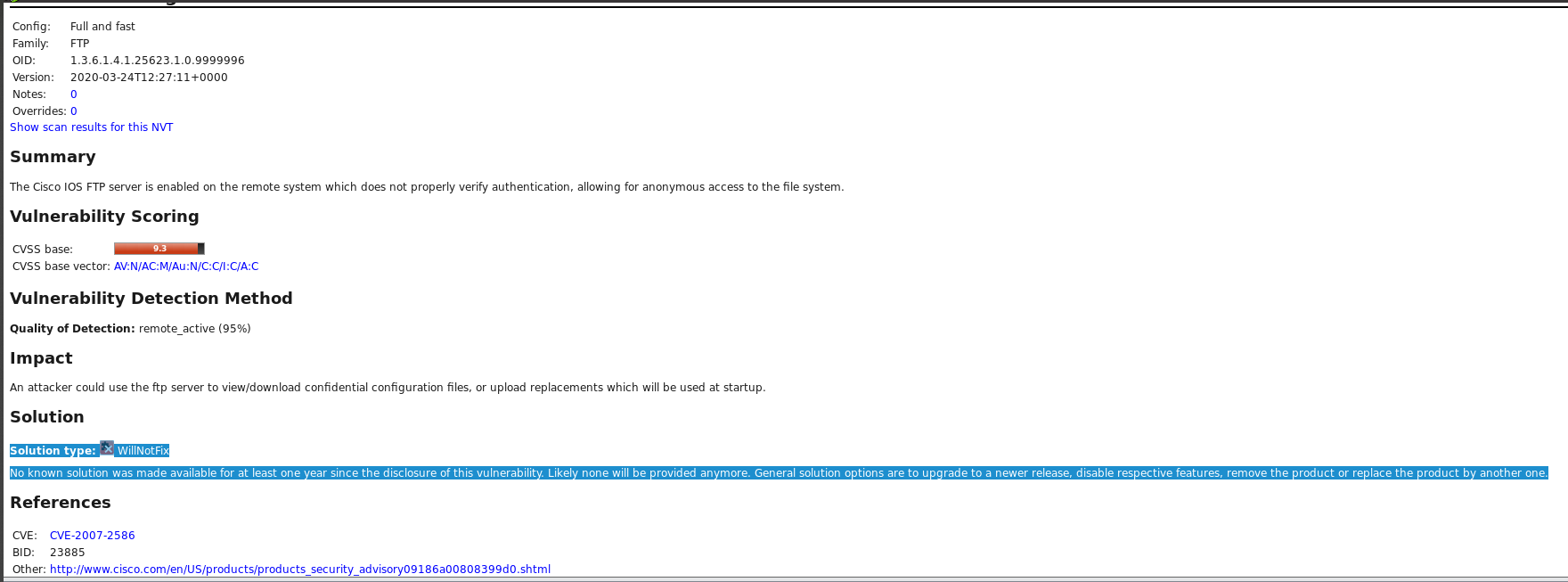
FTP
这里我查看了两个漏洞,都是评分较高的。
第一个可以通过更新解决。
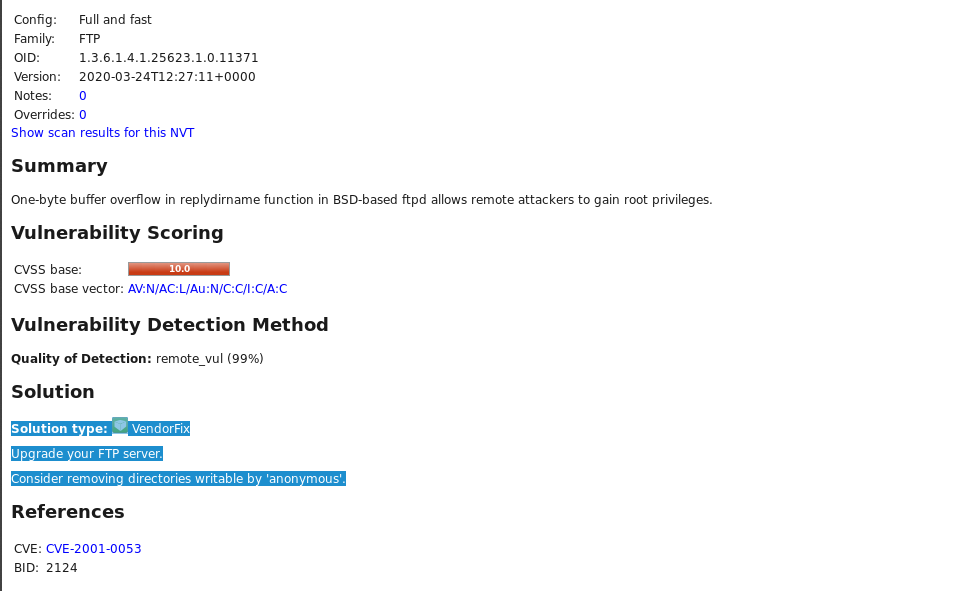
第二个居然还没有解决办法
实验后续问题
哪些组织负责DNS,IP的管理。
Internet 域名与地址管理机构(ICANN)负责全球的域名根服务器、DNS和IP地址管理。
ICANN是为承担域名系统管理IP地址分配,协议参数配置,以及主服务器系统管理等职能而设立的非盈利机构。
它设立三个支持组织:地址支持组织(ASO)负责IP地址系统的管理;域名支持组织(DNSO)负责互联网上的域名系统(DNS)的管理;协议支持组织(PSO)负责涉及Internet协议的唯一参数的分配。
什么是3R信息。
- 注册人(Registrant)
- 注册商(Registrar)
- 官方注册局(Registry)
使用whois命令可以查看到该部分的信息
Domain Name: BAIDU.COM
Registry Domain ID: 11181110_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.markmonitor.com
Registrar URL: http://www.markmonitor.com
Updated Date: 2019-05-09T04:30:46Z
Creation Date: 1999-10-11T11:05:17Z
Registry Expiry Date: 2026-10-11T11:05:17Z
Registrar: MarkMonitor Inc.
Registrar IANA ID: 292
Registrar Abuse Contact Email: abusecomplaints@markmonitor.com
Registrar Abuse Contact Phone: +1.2083895740
评价下扫描结果的准确性。
我觉得还是比较准确的吧,我们目前使用的软件也都是最新的,网站也可以看到实时的漏洞报告等内容。
实验补充内容
whios baidu.com
msf5 auxiliary(scanner/http/dir_scanner) > whois baidu.com
[*] exec: whois baidu.com
Domain Name: BAIDU.COM
Registry Domain ID: 11181110_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.markmonitor.com
Registrar URL: http://www.markmonitor.com
Updated Date: 2019-05-09T04:30:46Z
Creation Date: 1999-10-11T11:05:17Z
Registry Expiry Date: 2026-10-11T11:05:17Z
Registrar: MarkMonitor Inc.
Registrar IANA ID: 292
Registrar Abuse Contact Email: abusecomplaints@markmonitor.com
Registrar Abuse Contact Phone: +1.2083895740
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Domain Status: serverDeleteProhibited https://icann.org/epp#serverDeleteProhibited
Domain Status: serverTransferProhibited https://icann.org/epp#serverTransferProhibited
Domain Status: serverUpdateProhibited https://icann.org/epp#serverUpdateProhibited
Name Server: NS1.BAIDU.COM
Name Server: NS2.BAIDU.COM
Name Server: NS3.BAIDU.COM
Name Server: NS4.BAIDU.COM
Name Server: NS7.BAIDU.COM
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2020-04-21T01:16:01Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
Domain Name: baidu.com
Registry Domain ID: 11181110_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.markmonitor.com
Registrar URL: http://www.markmonitor.com
Updated Date: 2019-05-08T20:59:33-0700
Creation Date: 1999-10-11T04:05:17-0700
Registrar Registration Expiration Date: 2026-10-11T00:00:00-0700
Registrar: MarkMonitor, Inc.
Registrar IANA ID: 292
Registrar Abuse Contact Email: abusecomplaints@markmonitor.com
Registrar Abuse Contact Phone: +1.2083895770
Domain Status: clientUpdateProhibited (https://www.icann.org/epp#clientUpdateProhibited)
Domain Status: clientTransferProhibited (https://www.icann.org/epp#clientTransferProhibited)
Domain Status: clientDeleteProhibited (https://www.icann.org/epp#clientDeleteProhibited)
Domain Status: serverUpdateProhibited (https://www.icann.org/epp#serverUpdateProhibited)
Domain Status: serverTransferProhibited (https://www.icann.org/epp#serverTransferProhibited)
Domain Status: serverDeleteProhibited (https://www.icann.org/epp#serverDeleteProhibited)
Registrant Organization: Beijing Baidu Netcom Science Technology Co., Ltd.
Registrant State/Province: Beijing
Registrant Country: CN
Registrant Email: Select Request Email Form at https://domains.markmonitor.com/whois/baidu.com
Admin Organization: Beijing Baidu Netcom Science Technology Co., Ltd.
Admin State/Province: Beijing
Admin Country: CN
Admin Email: Select Request Email Form at https://domains.markmonitor.com/whois/baidu.com
Tech Organization: Beijing Baidu Netcom Science Technology Co., Ltd.
Tech State/Province: Beijing
Tech Country: CN
Tech Email: Select Request Email Form at https://domains.markmonitor.com/whois/baidu.com
Name Server: ns3.baidu.com
Name Server: ns4.baidu.com
Name Server: ns7.baidu.com
Name Server: ns1.baidu.com
Name Server: ns2.baidu.com
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2020-04-20T18:16:17-0700 <<<
For more information on WHOIS status codes, please visit:
https://www.icann.org/resources/pages/epp-status-codes
If you wish to contact this domain’s Registrant, Administrative, or Technical
contact, and such email address is not visible above, you may do so via our web
form, pursuant to ICANN’s Temporary Specification. To verify that you are not a
robot, please enter your email address to receive a link to a page that
facilitates email communication with the relevant contact(s).
Web-based WHOIS:
https://domains.markmonitor.com/whois
If you have a legitimate interest in viewing the non-public WHOIS details, send
your request and the reasons for your request to whoisrequest@markmonitor.com
and specify the domain name in the subject line. We will review that request and
may ask for supporting documentation and explanation.
The data in MarkMonitor’s WHOIS database is provided for information purposes,
and to assist persons in obtaining information about or related to a domain
name’s registration record. While MarkMonitor believes the data to be accurate,
the data is provided "as is" with no guarantee or warranties regarding its
accuracy.
By submitting a WHOIS query, you agree that you will use this data only for
lawful purposes and that, under no circumstances will you use this data to:
(1) allow, enable, or otherwise support the transmission by email, telephone,
or facsimile of mass, unsolicited, commercial advertising, or spam; or
(2) enable high volume, automated, or electronic processes that send queries,
data, or email to MarkMonitor (or its systems) or the domain name contacts (or
its systems).
MarkMonitor reserves the right to modify these terms at any time.
By submitting this query, you agree to abide by this policy.
MarkMonitor Domain Management(TM)
Protecting companies and consumers in a digital world.
Visit MarkMonitor at https://www.markmonitor.com
Contact us at +1.8007459229
In Europe, at +44.02032062220
Openvas成功安装
root@kali-2-20174306:~# openvas-check-setup
openvas-check-setup 2.3.7
Test completeness and readiness of OpenVAS-9
(add '--v6' or '--v7' or '--v8'
if you want to check for another OpenVAS version)
Please report us any non-detected problems and
help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Send us the log-file (/tmp/openvas-check-setup.log) to help analyze the problem.
Use the parameter --server to skip checks for client tools
like GSD and OpenVAS-CLI.
Step 1: Checking OpenVAS Scanner ...
OK: OpenVAS Scanner is present in version 5.1.3.
OK: redis-server is present in version v=5.0.7.
OK: scanner (kb_location setting) is configured properly using the redis-server socket: /var/run/redis-openvas/redis-server.sock
OK: redis-server is running and listening on socket: /var/run/redis-openvas/redis-server.sock.
OK: redis-server configuration is OK and redis-server is running.
OK: NVT collection in /var/lib/openvas/plugins contains 58924 NVTs.
WARNING: Signature checking of NVTs is not enabled in OpenVAS Scanner.
SUGGEST: Enable signature checking (see http://www.openvas.org/trusted-nvts.html).
WARNING: The initial NVT cache has not yet been generated.
SUGGEST: Start OpenVAS Scanner for the first time to generate the cache.
Step 2: Checking OpenVAS Manager ...
OK: OpenVAS Manager is present in version 7.0.3.
OK: OpenVAS Manager database found in /var/lib/openvas/mgr/tasks.db.
OK: Access rights for the OpenVAS Manager database are correct.
OK: sqlite3 found, extended checks of the OpenVAS Manager installation enabled.
OK: OpenVAS Manager database is at revision 184.
OK: OpenVAS Manager expects database at revision 184.
OK: Database schema is up to date.
OK: OpenVAS Manager database contains information about 58924 NVTs.
OK: At least one user exists.
OK: OpenVAS SCAP database found in /var/lib/openvas/scap-data/scap.db.
OK: OpenVAS CERT database found in /var/lib/openvas/cert-data/cert.db.
OK: xsltproc found.
Step 3: Checking user configuration ...
WARNING: Your password policy is empty.
SUGGEST: Edit the /etc/openvas/pwpolicy.conf file to set a password policy.
Step 4: Checking Greenbone Security Assistant (GSA) ...
OK: Greenbone Security Assistant is present in version 7.0.3.
OK: Your OpenVAS certificate infrastructure passed validation.
Step 5: Checking OpenVAS CLI ...
OK: OpenVAS CLI version 1.4.5.
Step 6: Checking Greenbone Security Desktop (GSD) ...
SKIP: Skipping check for Greenbone Security Desktop.
Step 7: Checking if OpenVAS services are up and running ...
OK: netstat found, extended checks of the OpenVAS services enabled.
OK: OpenVAS Scanner is running and listening on a Unix domain socket.
WARNING: OpenVAS Manager is running and listening only on the local interface.
This means that you will not be able to access the OpenVAS Manager from the
outside using GSD or OpenVAS CLI.
SUGGEST: Ensure that OpenVAS Manager listens on all interfaces unless you want
a local service only.
OK: Greenbone Security Assistant is listening on port 80, which is the default port.
Step 8: Checking nmap installation ...
WARNING: Your version of nmap is not fully supported: 7.70
SUGGEST: You should install nmap 5.51 if you plan to use the nmap NSE NVTs.
Step 10: Checking presence of optional tools ...
OK: pdflatex found.
OK: PDF generation successful. The PDF report format is likely to work.
OK: ssh-keygen found, LSC credential generation for GNU/Linux targets is likely to work.
WARNING: Could not find rpm binary, LSC credential package generation for RPM and DEB based targets will not work.
SUGGEST: Install rpm.
WARNING: Could not find makensis binary, LSC credential package generation for Microsoft Windows targets will not work.
SUGGEST: Install nsis.
It seems like your OpenVAS-9 installation is OK.
If you think it is not OK, please report your observation
and help us to improve this check routine:
http://lists.wald.intevation.org/mailman/listinfo/openvas-discuss
Please attach the log-file (/tmp/openvas-check-setup.log) to help us analyze the problem.
Metapsloit 端口扫描
来源:https://www.fujieace.com/metasploit/port-scanning-2.html
Nmap 和 db_nmap
使用通常从命令行使用的选项运行Nmap。如果我们希望我们的扫描被保存到我们的数据库中,我们将省略输出标志并使用db_nmap。
msf5 > db_nmap -v -sV 192.168.233.255 -oA subnet_2
[*] Nmap: Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-21 08:10 CST
[*] Nmap: NSE: Loaded 43 scripts for scanning.
[*] Nmap: Initiating ARP Ping Scan at 08:10
[*] Nmap: Scanning 192.168.233.255 [1 port]
[*] Nmap: Completed ARP Ping Scan at 08:10, 0.47s elapsed (1 total hosts)
[*] Nmap: Nmap scan report for 192.168.233.255 [host down]
[*] Nmap: Read data files from: /usr/bin/../share/nmap
[*] Nmap: Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
[*] Nmap: Nmap done: 1 IP address (0 hosts up) scanned in 0.94 seconds
[*] Nmap: Raw packets sent: 2 (56B) | Rcvd: 0 (0B)
Metasploit 漏洞扫描
默认情况下,所有扫描仪模块都将THREADS值设置为'1'。THREADS值设置并发线程的数量,同时扫描使用。将此值设置为较高的数字以加快扫描速度或降低扫描速度以减少网络流量,但一定要遵守以下准则:
- 原生Win32系统上的THREADS值保持在16以下
- 在Cygwin下运行MSF时,请将THREADS保持在200以下
- 在类Unix操作系统上,THREADS可以设置为256。
SMB登录检查
用smb_login扫描访问
发现自己的一种常见情况是拥有一个有效的用户名和密码组合,并且想知道你可以在哪里使用它。这是SMB登录检查扫描程序非常有用的地方,因为它将连接到一系列主机并确定用户名/密码组合是否可以访问目标。
https://www.fujieace.com/metasploit/smb-login-check.html
VNC认证
VNC验证无扫描仪 是用于Metasploit的一个辅助模块。
msf5 auxiliary(scanner/smb/smb_login) > use auxiliary/scanner/vnc/vnc_none_auth
msf5 auxiliary(scanner/vnc/vnc_none_auth) > show options
Module options (auxiliary/scanner/vnc/vnc_none_auth):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 5900 yes The target port (TCP)
THREADS 1 yes The number of concurrent threads
msf5 auxiliary(scanner/vnc/vnc_none_auth) > set RHOSTS 192.168.233.255/24
RHOSTS => 192.168.233.255/24
msf5 auxiliary(scanner/vnc/vnc_none_auth) > set THREADS 50
THREADS => 50
msf5 auxiliary(scanner/vnc/vnc_none_auth) > run
[*] 192.168.233.255/24:5900 - Scanned 46 of 256 hosts (17% complete)
[*] 192.168.233.255/24:5900 - Scanned 53 of 256 hosts (20% complete)
[*] 192.168.233.255/24:5900 - Scanned 99 of 256 hosts (38% complete)
[*] 192.168.233.255/24:5900 - Scanned 103 of 256 hosts (40% complete)
[*] 192.168.233.255/24:5900 - Scanned 130 of 256 hosts (50% complete)
[*] 192.168.233.255/24:5900 - Scanned 168 of 256 hosts (65% complete)
[*] 192.168.233.255/24:5900 - Scanned 184 of 256 hosts (71% complete)
[*] 192.168.233.255/24:5900 - Scanned 206 of 256 hosts (80% complete)
[*] 192.168.233.255/24:5900 - Scanned 232 of 256 hosts (90% complete)
[*] 192.168.233.255/24:5900 - Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed

 来!给我康康!
来!给我康康!