2018铁三测评WP
1
根据提示拿到password.txt
前端有输入限制,用burpsuite爆破

newpage字段 base64解码
之后留言时再改包 修改islogin=1 和 userlevel=root 即可
2
burp抓包改UA字段为
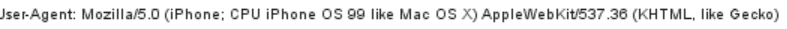
3
burpsuite抓包发现cookie字段base64+md5解密后为2699:2699,用1234567890:1234567890再加密发送即可
4
gpg john.tar.gz.gpg 输入公钥
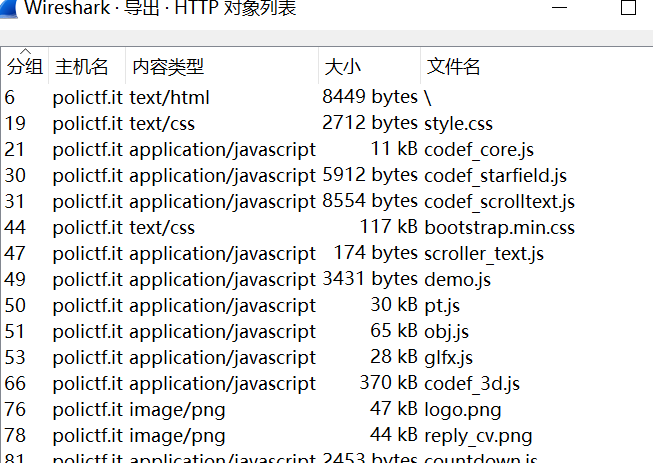
tar -xzvf john.tar.gz.gpg 解出一个pcap包 wireshark导出http对象 内有一张logo.png stegsolve即可
5
文本打开后发现提示
data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAARgAAAEYCAIAAAAI7H7bAAAFRElEQVR4nO3dUW4bOxAAQSt497+ycwMi4GuNZ62q3yDyeq0GPwYkX9/f31/A//Pnpx8AfgMhQUBIEBASBIQEASFBQEgQEBIE/jv82+v1GnuO3GHQfPi98vH03Tu8e/j8A5e8jSXOb8OKBAEhQUBIEBASBIQEASFBQEgQEBIETgPZgyX7aicHfEt+1t2bzx8+f8Knf6OsSBAQEgSEBAEhQUBIEBASBIQEASFB4HIge5DP/paM6iYf4/AO7yah+ZbbSY/4RlmRICAkCAgJAkKCgJAgICQICAkCQoJAP5Ddb8mEd9LdGHf/rHYPKxIEhAQBIUFASBAQEgSEBAEhQUBIEPjEgWxu8hrWnKlrwooEASFBQEgQEBIEhAQBIUFASBAQEgT6gewHjiAnN5nmP2vJpbQH+79RX1YkSAgJAkKCgJAgICQICAkCQoKAkCBwOZD9rdsqHz1azX/WkmtzH8GKBAEhQUBIEBASBIQEASFBQEgQEBIEXo/YftjaP4Jccq/rB343rlmRICAkCAgJAkKCgJAgICQICAkCQoJAP5Ddv7szP9p3yYR30v658OT38MuKBAkhQUBIEBASBIQEASFBQEgQEBIETgPZyTnjkiHp5GPkljzGpMlZrYEsvJ2QICAkCAgJAkKCgJAgICQICAkCpztk82nX5Bg3/1n7x7j5DHrJuHPybVyzIkFASBAQEgSEBAEhQUBIEBASBIQEgcsdsrlHz2rvHuPOkhe1ZIx7MDlA/7IiQUJIEBASBIQEASFBQEgQEBIEhASB0w7ZgyVXo04OE98xxWt/1uSQdPIL8IiHtyJBQEgQEBIEhAQBIUFASBAQEgSEBIHRO2SXzE+XXIB7Z8nf6wPZIQtvJyQICAkCQoKAkCAgJAgICQJCgsDlDtm72d+SqevkXtfJE6GX/Mr7T2l+BysSBIQEASFBQEgQEBIEhAQBIUFASBA47ZC9/MQd87j9O2SXzBmXnEt8Z8/uaSsSBIQEASFBQEgQEBIEhAQBIUFASBAY3SG7/0zd/dPJJfPu3OSe63ewIkFASBAQEgSEBAEhQUBIEBASBIQEgdNA9m6kNfm/9szjNrh7G/tf1OR343oib0WCgJAgICQICAkCQoKAkCAgJAgICQKnI4snN7ROfuDkCHLJ/tOD/bf33hl+81YkCAgJAkKCgJAgICQICAkCQoKAkCBweWTxpMljhCdPTl4ynt4/Mp5khyz8JCFBQEgQEBIEhAQBIUFASBAQEgRGB7L57G/JQcd3v9dvnYQu2QY7PJ62IkFASBAQEgSEBAEhQUBIEBASBIQEgdORxb/V/ltT70z+KSe3LU9uJT6wQxbeTkgQEBIEhAQBIUFASBAQEgSEBIHTDtlHDy7zXZCTI8i7x9j/91pySvOBHbLwk4QEASFBQEgQEBIEhAQBIUFASBC4PLJ4yb7a/SPI3JL9p5NnO+fe8RhWJAgICQJCgoCQICAkCAgJAkKCgJAg0N8hmw9JH33z7JKNn5MefYfsNSsSBIQEASFBQEgQEBIEhAQBIUFASBDoB7IfaPIm07sPvDvA+dEXxQ5Prq1IEBASBIQEASFBQEgQEBIEhAQBIUHAQPZf5Uf7Th4IvGTL7d3v9Yi3YUWCgJAgICQICAkCQoKAkCAgJAgICQL9QHb/mbqTT7jkvOX8A5fsxt1zibAVCQJCgoCQICAkCAgJAkKCgJAgICQIvB4x7boweXnro7fBTj7GEu6QhaWEBAEhQUBIEBASBIQEASFBQEgQOA1kgX9kRYKAkCAgJAgICQJCgoCQICAkCAgJAkKCwF9sIhJFGPgGhQAAAABJRU5ErkJggg==
该文件是一个base64编码的图片,链接http://www.vgot.net/test/image2base64.php,扫码即可
6
\x6a\x0b\x58\x99\x52\x66\x68\x2d\x63\x89\xe7\x68\x2f\x73\x68\x00\x68\x2f\x62\x69\x6e\x89\xe3\x52\xe8\x34\x00\x00\x00\x65\x63\x68\x6f\x20\x5a
\x6d\x78\x68\x5a\x33\x74\x54\x53\x45\x56\x73\x62\x47\x4e\x76\x5a\x47\x56\x66\x53\x56\x4e\x66\x63\x32\x39\x66\x51\x32\x39\x76\x62\x48\x30\x4b
\x7c\x62\x61\x73\x65\x36\x34\x20\x2d\x64\x00\x57\x53\x89\xe1\xcd\x80
hex to ascii :ZmxhZ3tTSEVsbGNvZGVfSVNfc29fQ29vbH0K|base64
base64解码即可





