DASCTF X CBCTF 2023 10
能力有限 只能复现能做的一些题 其他的慢慢补
Crypto
rsa
chall.py
from Crypto.Util.number import *
import random
from gmpy2 import *
from libnum import *
from flag import flag
def padding(f):
random_chars = bytes([random.randint(0, 255) for _ in range(32)])
f = f + random_chars
return f
def guess_p(p):
e = 65537
P = p
n1 = getPrime(512)*getPrime(512)
with open('enc.txt', 'w+') as f:
while jacobi(2,n1) == 1:
n1 = getPrime(512)*getPrime(512)
while P:
pad = random.randint(0, 2**2023)**2
message = pad << 1 + P % 2
cipher = pow(message, e, n1)
f.write(str(cipher)+'n')
P //= 2
print("n1 = "+ str(n1) )
def guess_q(q):
def encrypt(q, n):
e = random.randint(1000,2000)
noise = random.randint(0, n - 1)
c = pow(q+noise,e,n)
return e, noise,c
n2 = getPrime(512)*getPrime(512)
e1, noise1, c1 = encrypt(q, n2)
e2, noise2, c2 = encrypt(q, n2)
print("n2 = "+ str(n2) )
print('(e1, noise1, c1) =', (e1,noise1,c1))
print('(e2, noise2, c2) =', (e2,noise2,c2))
p = getPrime(512)
q = getPrime(512)
n = p*q
guess_p(p)
guess_q(q)
e = 0x10001
flag = padding(flag)
m = bytes_to_long(flag)
c = pow(m,e,n)
print("c = " + str(c))
'''
n1 = 65634094430927080732256164808833233563732628654160389042977689628512527168256899310662239009610512772020503283842588142453533499954947692968978190310627721338357432052800695091789711809256924541784954080619073213358228083200846540676931341013554634493581962527475555869292091755676130810562421465063412235309
n2 = 103670293685965841863872863719573676572683187403862749665555450164387906552249974071743238931253290278574192713467491802940810851806104430306195931179902098180199167945649526235613636163362672777298968943319216325949503045377100235181706964846408396946496139224344270391027205106691880999410424150216806861393
(e1, noise1, c1) = (1743, 44560588075773853612820227436439937514195680734214431948441190347878274184937952381785302837541202705212687700521129385632776241537669208088777729355349833215443048466316517110778502508209433792603420158786772339233397583637570006255153020675167597396958251208681121668808253767520416175569161674463861719776, 65643009354198075182587766550521107063140340983433852821580802983736094225036497335607400197479623208915379722646955329855681601551282788854644359967909570360251550766970054185510197999091645907461580987639650262519866292285164258262387411847857812391136042309550813795587776534035784065962779853621152905983)
(e2, noise2, c2) = (1325, 35282006599813744140721262875292395887558561517759721467291789696459426702600397172655624765281531167221787036009507833425145071265739486735993631460189629709591456017092661028839951392247601628468621576100035700437892164435424035004463142959219067199451575338270613300215815894328788753564798153516122567683, 50327632090778183759544755226710110702046850880299488259739672542025916422119065179822210884622225945376465802069464782311211031263046593145733701591371950349735709553105217501410716570601397725812709771348772095131473415552527749452347866778401205442409443726952960806789526845194216490544108773715759733714)
c = 124349762993424531697403299350944207725577290992189948388824124986066269514204313888980321088629462472088631052329128042837153718129149149661961926557818023704330462282009415874674794190206220980118413541269327644472633791532767765585035518183177197863522573410860341245613331398610013697803459403446614221369
'''
这里比赛的时候大概明白这里的Jacobi的玄机 但是只是储备完全不够 瞎猜的几个结论也求不出p
求q的部分当时也以为e不同不能sage跑(虽说写了一个copper但好像写假了。。。 要再认真弄懂copper的原理)
先跑q:
def attack():
PR.<x> = PolynomialRing(Zmod(n2))
g1 = (x+noise1)^e1-c1
g2 = (x+noise2)^e2-c2
def gcd(g1,g2):
while g2:
g1, g2 = g2,g1%g2
return g1.monic()
return -gcd(g1,g2)[0]
# print(attack())
然后求p
首先了解kronecker符号
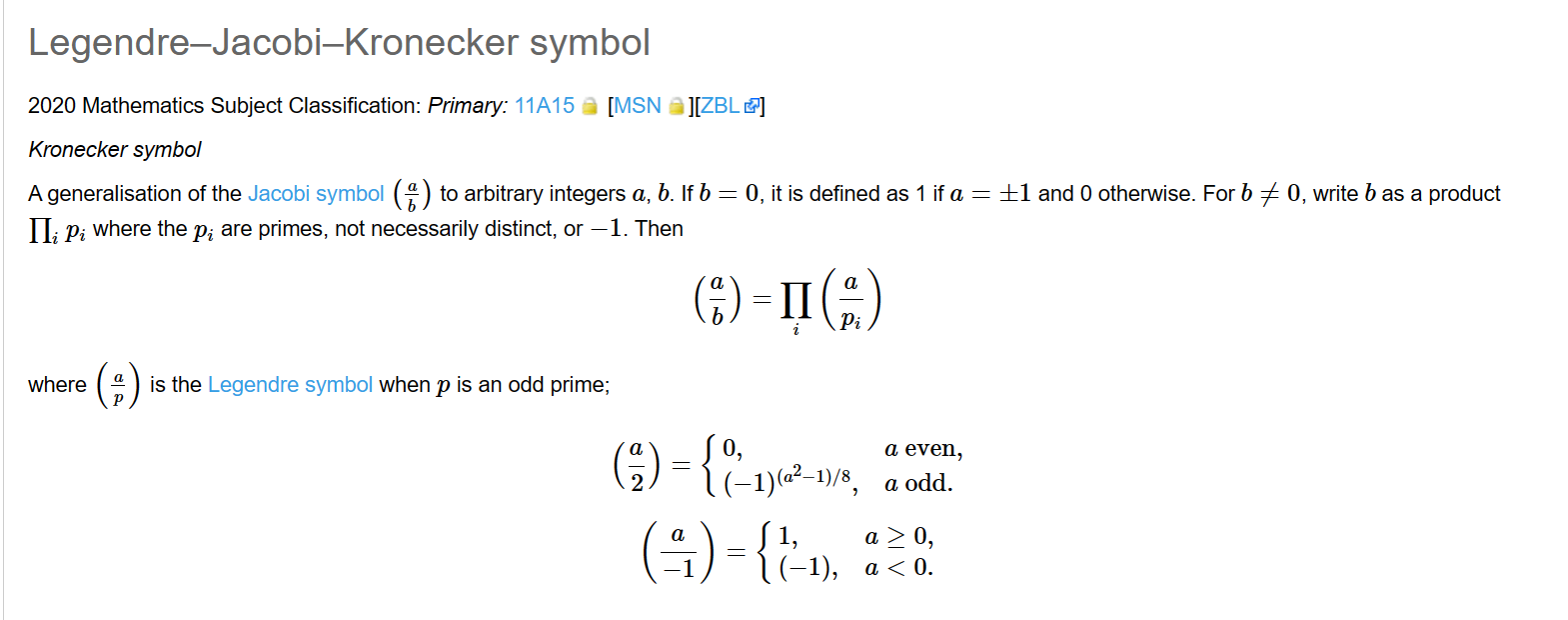
由于Jacobi只是将勒让德的奇素数推广到了奇数
而kronecker符号是推广到了一般的整数 更具普适意义
两种情况
(2x^2)^e(2x^2+1)^e
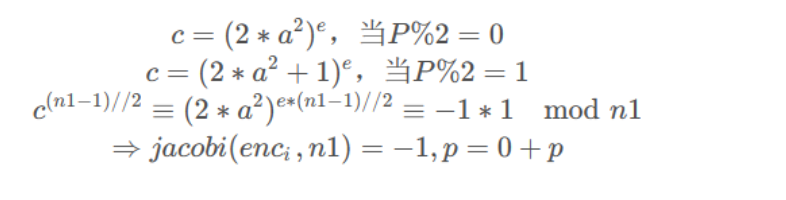
不要忘了欧拉准则!!!二次剩余最初的判断方式!!!
p = ''
for i in enc:
# print(i)
i = int(i)
if(kronecker(i,n1)==1):
p = '1'+p
else:
p = '0'+p
# print(int(p,2))
或者这种
if(kronecker(i,n1)==-1):
p = '0'+p
else:
p = '1'+p
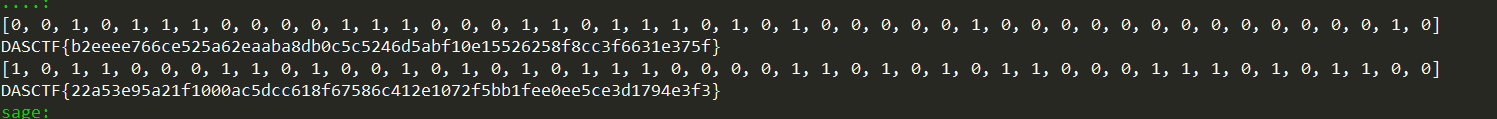
最后的flag
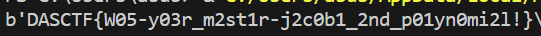
backpack
粗浅学了下格密码 看了看背包密码LLL破解的本质
还是要学会自己造格子
这题跟普通的背包不同在于 每6个中必有3个1
所以要再加上一列的约束 即 Σxi = 24
借大佬的图
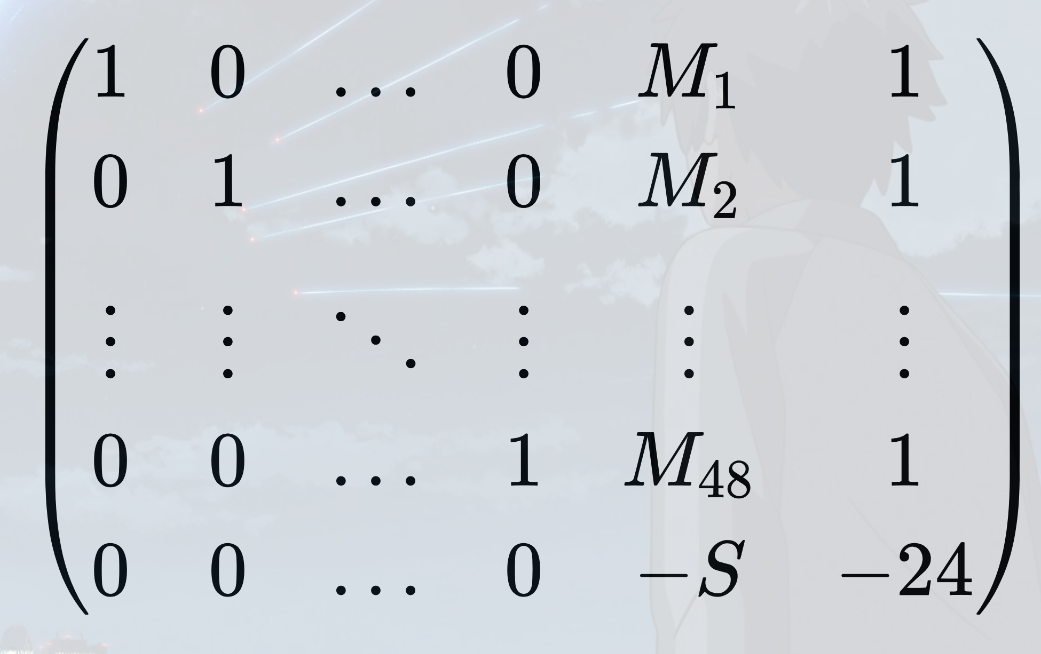
最后判断就是在常规的-S那列为0后加上最后一列为0
solution.py
from sage.all import *
from hashlib import *
a = [65651991706497, 247831871690373, 120247087605020, 236854536567393, 38795708921144, 256334857906663, 120089773523233, 165349388120302, 123968326805899, 79638234559694, 259559389823590, 256776519514651, 107733244474073, 216508566448440, 39327578905012, 118682486932022, 263357223061004, 132872609024098, 44605761726563, 24908360451602, 237906955893793, 204469770496199, 7055254513808, 221802659519968, 169686619990988, 23128789035141, 208847144870760, 272339624469135, 269511404473473, 112830627321371, 73203551744776, 42843503010671, 118193938825623, 49625220390324, 230439888723036, 241486656550572, 107149406378865, 233503862264755, 269502011971514, 181805192674559, 152612003195556, 184127512098087, 165959151027513, 188723045133473, 241615906682300, 216101484550038, 81190147709444, 124498742419309]
re = 4051501228761632
n = len(a)
K = 2^10
M = Matrix(ZZ,n+1,n+2)
for i in range(n):
M[i,i] = 1
M[i,n] = K*a[i]
M[i,n+1] = K*1
M[n,n] = -K*re
M[n,n+1] = -24*K
for line in M.LLL():
if(line[-1]==0 and line[-2]==0):
x = [abs(i) for i in line[:-2]]
if set(x).issubset([0, 1]):
print(x)
flag = 'DASCTF{'+sha256(''.join([str(i) for i in x]).encode()).hexdigest()+'}'
print(flag)
Re
auuuu3
给的是一个autoit格式的exe
如果用IDA查看 基本上是做不出来的
万幸的是有个脚本可以帮我们extract
https://github.com/nazywam/AutoIt-Ripper
然后这么用
from autoit_ripper import extract, AutoItVersion
with open(r"D:\浏览器下载\auuuu3.exe", "rb") as f:
file_content = f.read()
# EA05 for v3.00+, EA06 for v3.26+
# Omitting `version` or passing None will try both versions
content_list = extract(data=file_content, version=AutoItVersion.EA06)
with open(r'D:\浏览器下载\auuuu3.txt','w+') as f:
for content in content_list:
s = str(content)
f.write(s)
WP用的exe我没找到... 但是这样提取出来大致也能看
很容易定位到最后一部分
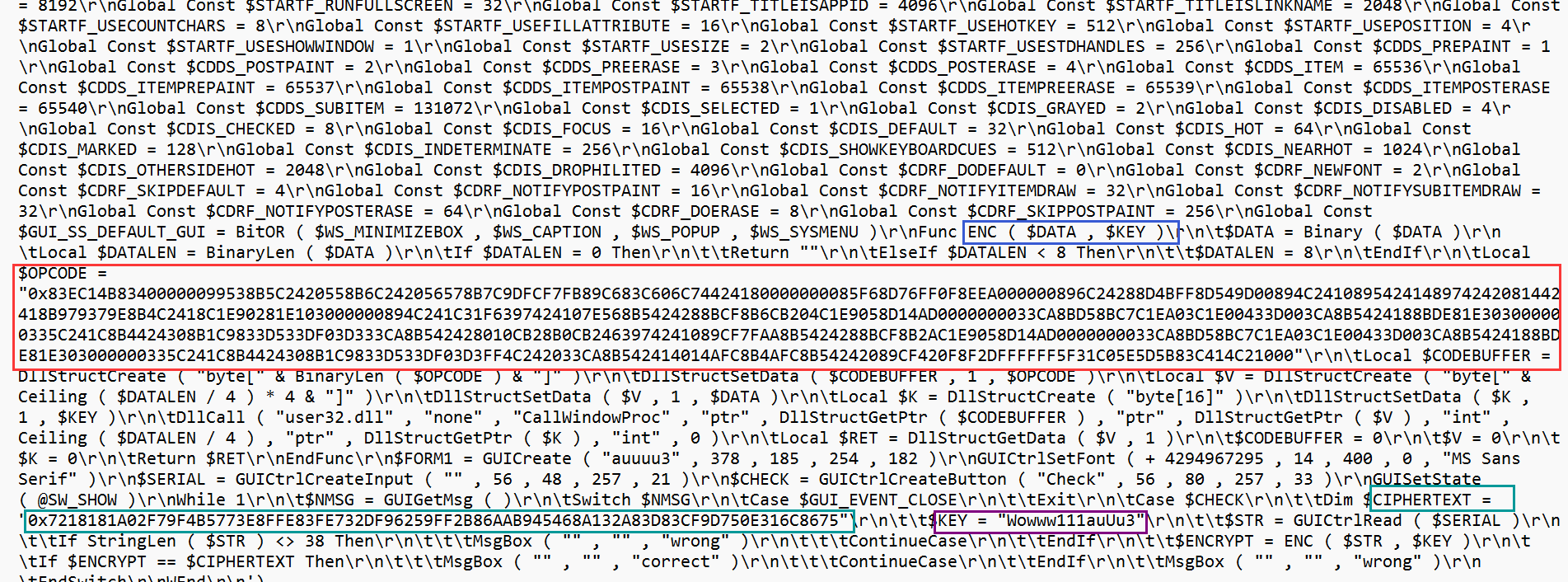
这里相当于load了一个dll 只是是用hex写的 我们将这段opcode导入dll用IDA来分析
import binascii
OPCODE = "83EC14B83400000099538B5C2420558B6C242056578B7C9DFCF7FB89C683C606C74424180000000085F68D76FF0F8EEA000000896C24288D4BFF8D549D00894C2410895424148974242081442418B979379E8B4C2418C1E90281E103000000894C241C31F6397424107E568B5424288BCF8B6CB204C1E9058D14AD0000000033CA8BD58BC7C1EA03C1E00433D003CA8B5424188BDE81E303000000335C241C8B4424308B1C9833D533DF03D333CA8B542428010CB28B0CB2463974241089CF7FAA8B5424288BCF8B2AC1E9058D14AD0000000033CA8BD58BC7C1EA03C1E00433D003CA8B5424188BDE81E303000000335C241C8B4424308B1C9833D533DF03D3FF4C242033CA8B542414014AFC8B4AFC8B54242089CF420F8F2DFFFFFF5F31C05E5D5B83C414C21000"
with open(r"D:\浏览器下载\enc.dll","wb") as f:
f.write(binascii.unhexlify(OPCODE))
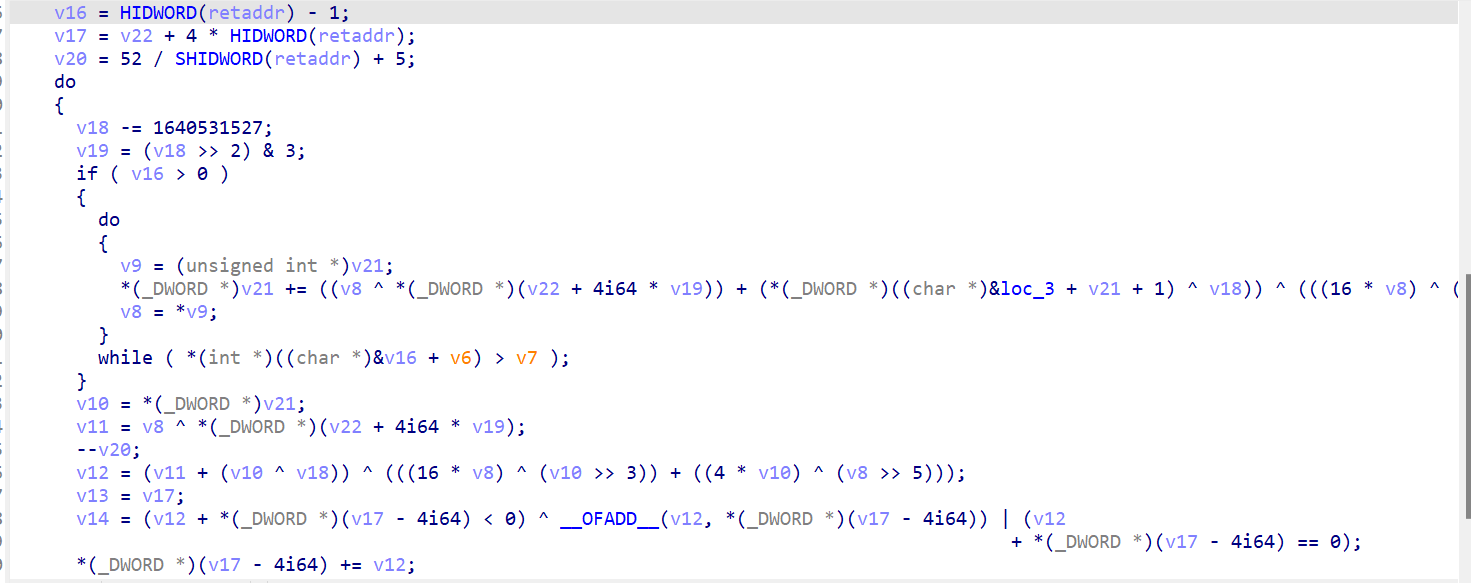
标准的xxtea加密
我们已知 ciphertext7218181A02F79F4B5773E8FFE83FE732DF96259FF2B86AAB945468A132A83D83CF9D750E316C8675
keyWowww111auUu3
小端序转一下 解密
#include <stdio.h>
#include <stdint.h>
#define DELTA 0x9e3779b9
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
void btea(uint32_t *v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n > 1) /* Coding Part */
{
rounds = 6 + 52/n;
sum = 0;
z = v[n-1];
do
{
sum += DELTA;
e = (sum >> 2) & 3;
for (p=0; p<n-1; p++)
{
y = v[p+1];
z = v[p] += MX;
}
y = v[0];
z = v[n-1] += MX;
}
while (--rounds);
}
else if (n < -1) /* Decoding Part */
{
n = -n;
rounds = 6 + 52/n;
sum = rounds*DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p=n-1; p>0; p--)
{
z = v[p-1];
y = v[p] -= MX;
}
z = v[n-1];
y = v[0] -= MX;
sum -= DELTA;
}
while (--rounds);
}
}
int main()
{
uint32_t v[10]= {0x1A181872,0x4B9FF702,0xFFE87357,0x32E73FE8,0x9F2596DF,0xAB6AB8F2,0xA1685494,0x833DA832,0x0E759DCF,0x75866C31};
uint32_t const k[4]= {0x77776f57,0x31313177,0x75557561,0x33};
int n= 10;
btea(v, -n, k);
for(int i=0;i<10;i++)
for(int j=0;j<=3;j++)
printf("%c",(v[i]>>(8*j))&0xff);
return 0;
}
flag : DASCTF{Oh1_autO1t_iS_so_Co0oL_aNd_Fun}
可以看到 这题主要考的其实是合理利用工具进行分析(找到autoit-ripper后的分析其实并不难 但如果只会IDA就G了...)
marshal
题目给的一个嵌套marshal的py
import marshal
code = b'c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00@\x00\x00\x00@\x00\x00\x00s\xe2\x00\x00\x00d\x00d\x01d\x02d\x03d\x04d\x05d\x06d\x07d\x08d\td\nd\x0bd\x0cd\rd\x0ed\x0fg\x10Z\x00d\x10d\x11\x84\x00e\x01d\x12\x83\x01D\x00\x83\x01Z\x02d\x05d\x12d\x13d\x14d\x0ed\x15d\x16d\x17d\x0fd\x18d\x19d\x1ad\x08d\x1bd\x1cd\x1dd\x0cd\x1ed\x1fd d\x01d!d"d#d\x02d$d%d&d\rd\'d(d)d\x0bd*d+d,d\x04d-d.d/d\x06d0d1d2d\x03d3d4d5d\x00d6d7d8d\x07d9d:d;d\td<d=d>d\nd?d@dAg@Z\x03dBd\x11\x84\x00e\x01dC\x83\x01D\x00\x83\x01Z\x04e\x05\xa0\x06dD\xa1\x01Z\x07e\x08e\x07\x83\x01\x01\x00dES\x00)F\xe9\x0c\x00\x00\x00\xe9\x05\x00\x00\x00\xe9\x06\x00\x00\x00\xe9\x0b\x00\x00\x00\xe9\t\x00\x00\x00\xe9\x00\x00\x00\x00\xe9\n\x00\x00\x00\xe9\r\x00\x00\x00\xe9\x03\x00\x00\x00\xe9\x0e\x00\x00\x00\xe9\x0f\x00\x00\x00\xe9\x08\x00\x00\x00\xe9\x04\x00\x00\x00\xe9\x07\x00\x00\x00\xe9\x01\x00\x00\x00\xe9\x02\x00\x00\x00c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x05\x00\x00\x00C\x00\x00\x00s\x16\x00\x00\x00g\x00|\x00]\x0e}\x01t\x00\xa0\x01|\x01\xa1\x01\x91\x02q\x04S\x00\xa9\x00)\x02\xda\x04Sbox\xda\x05index\xa9\x02\xda\x02.0\xda\x01xr\x10\x00\x00\x00r\x10\x00\x00\x00\xda\x00\xda\n<listcomp>\x04\x00\x00\x00s\x04\x00\x00\x00\x06\x00\x02\x00r\x17\x00\x00\x00\xe9\x10\x00\x00\x00\xe9 \x00\x00\x00\xe90\x00\x00\x00\xe9\x11\x00\x00\x00\xe9!\x00\x00\x00\xe91\x00\x00\x00\xe9\x12\x00\x00\x00\xe9"\x00\x00\x00\xe92\x00\x00\x00\xe9\x13\x00\x00\x00\xe9#\x00\x00\x00\xe93\x00\x00\x00\xe9\x14\x00\x00\x00\xe9$\x00\x00\x00\xe94\x00\x00\x00\xe9\x15\x00\x00\x00\xe9%\x00\x00\x00\xe95\x00\x00\x00\xe9\x16\x00\x00\x00\xe9&\x00\x00\x00\xe96\x00\x00\x00\xe9\x17\x00\x00\x00\xe9\'\x00\x00\x00\xe97\x00\x00\x00\xe9\x18\x00\x00\x00\xe9(\x00\x00\x00\xe98\x00\x00\x00\xe9\x19\x00\x00\x00\xe9)\x00\x00\x00\xe99\x00\x00\x00\xe9\x1a\x00\x00\x00\xe9*\x00\x00\x00\xe9:\x00\x00\x00\xe9\x1b\x00\x00\x00\xe9+\x00\x00\x00\xe9;\x00\x00\x00\xe9\x1c\x00\x00\x00\xe9,\x00\x00\x00\xe9<\x00\x00\x00\xe9\x1d\x00\x00\x00\xe9-\x00\x00\x00\xe9=\x00\x00\x00\xe9\x1e\x00\x00\x00\xe9.\x00\x00\x00\xe9>\x00\x00\x00\xe9\x1f\x00\x00\x00\xe9/\x00\x00\x00\xe9?\x00\x00\x00c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x05\x00\x00\x00C\x00\x00\x00s\x16\x00\x00\x00g\x00|\x00]\x0e}\x01t\x00\xa0\x01|\x01\xa1\x01\x91\x02q\x04S\x00r\x10\x00\x00\x00)\x02\xda\x04PBoxr\x12\x00\x00\x00r\x13\x00\x00\x00r\x10\x00\x00\x00r\x10\x00\x00\x00r\x16\x00\x00\x00r\x17\x00\x00\x00\t\x00\x00\x00s\x04\x00\x00\x00\x06\x00\x02\x00\xe9@\x00\x00\x00s#\n\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x02\x00\x00\x00C\x00\x00\x00s\x08\x00\x00\x00|\x00|\x01A\x00S\x00)\x01N\xa9\x00)\x02\xda\x05stateZ\x08roundkeyr\x00\x00\x00\x00r\x00\x00\x00\x00\xda\x00\xda\x0baddRoundKey\x02\x00\x00\x00s\x02\x00\x00\x00\x00\x01r\x03\x00\x00\x00s,\t\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00\x06\x00\x00\x00C\x00\x00\x00s6\x00\x00\x00d\x01}\x01t\x00d\x02\x83\x01D\x00]$}\x02|\x01t\x01|\x00|\x02d\x03\x14\x00?\x00d\x04@\x00\x19\x00|\x02d\x03\x14\x00>\x007\x00}\x01q\x0c|\x01S\x00)\x05N\xe9\x00\x00\x00\x00\xe9\x10\x00\x00\x00\xe9\x04\x00\x00\x00\xe9\x0f\x00\x00\x00)\x02\xda\x05rangeZ\x04Sbox)\x03\xda\x05state\xda\x06output\xda\x01i\xa9\x00r\x08\x00\x00\x00\xda\x00\xda\tsBoxLayer\x02\x00\x00\x00s\x08\x00\x00\x00\x00\x01\x04\x01\x0c\x01"\x01r\n\x00\x00\x00s\xe4\x07\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00\x05\x00\x00\x00C\x00\x00\x00s.\x00\x00\x00d\x01}\x01t\x00d\x02\x83\x01D\x00]\x1c}\x02|\x01|\x00|\x02?\x00d\x03@\x00t\x01|\x02\x19\x00>\x007\x00}\x01q\x0c|\x01S\x00)\x04N\xe9\x00\x00\x00\x00\xe9@\x00\x00\x00\xe9\x01\x00\x00\x00)\x02\xda\x05rangeZ\x04PBox)\x03\xda\x05state\xda\x06output\xda\x01i\xa9\x00r\x07\x00\x00\x00\xda\x00\xda\x06pLayer\x02\x00\x00\x00s\x08\x00\x00\x00\x00\x01\x04\x01\x0c\x01\x1a\x01r\t\x00\x00\x00s\xac\x06\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\x04\x00\x00\x00\x03\x00\x00\x00s\x1a\x00\x00\x00t\x00\x87\x00f\x01d\x01d\x02\x84\x08t\x01d\x03\x83\x01D\x00\x83\x01\x83\x01S\x00)\x04Nc\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x05\x00\x00\x00\x13\x00\x00\x00s \x00\x00\x00g\x00|\x00]\x18}\x01t\x00\x88\x00|\x01\x19\x00\x83\x01d\x00|\x01\x14\x00>\x00\x91\x02q\x04S\x00)\x01\xe9\x08\x00\x00\x00)\x01\xda\x03ord)\x02\xda\x02.0\xda\x01c\xa9\x01\xda\x01i\xa9\x00\xda\x00\xda\n<listcomp>\x03\x00\x00\x00s\x04\x00\x00\x00\x06\x00\x02\x00z!string2number.<locals>.<listcomp>r\x00\x00\x00\x00)\x02\xda\x03sum\xda\x05ranger\x04\x00\x00\x00r\x06\x00\x00\x00r\x04\x00\x00\x00r\x07\x00\x00\x00\xda\rstring2number\x02\x00\x00\x00s\x02\x00\x00\x00\x00\x01r\x0b\x00\x00\x00s\x01\x05\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x04\x00\x00\x00\x05\x00\x00\x00C\x00\x00\x00st\x00\x00\x00g\x00}\x02t\x00d\x01|\x01d\x01\x17\x00d\x01\x83\x03D\x00]Z}\x03|\x02\xa0\x01|\x00d\x02?\x00\xa1\x01\x01\x00|\x00d\x03@\x00d\x04>\x00|\x00d\x05?\x00\x17\x00}\x00t\x02|\x00d\x06?\x00\x19\x00d\x06>\x00|\x00d\x07d\x06\x13\x00d\x01\x18\x00@\x00\x17\x00}\x00|\x00|\x03d\x08>\x00|\x00d\x05?\x00A\x00N\x00}\x00q\x14|\x02S\x00)\tN\xe9\x01\x00\x00\x00\xe9\x10\x00\x00\x00i\xff\xff\x07\x00\xe9=\x00\x00\x00\xe9\x13\x00\x00\x00\xe9L\x00\x00\x00\xe9\x02\x00\x00\x00\xe9\x0f\x00\x00\x00)\x03\xda\x05range\xda\x06appendZ\x04Sbox)\x04\xda\x03key\xda\x06roundsZ\troundkeys\xda\x01i\xa9\x00r\x0c\x00\x00\x00\xda\x00\xda\x13generateRoundkeys80\x02\x00\x00\x00s\x0e\x00\x00\x00\x00\x01\x04\x01\x14\x01\x0e\x01\x14\x01 \x01\x16\x01r\x0e\x00\x00\x00sF\x03\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x06\x00\x00\x00@\x00\x00\x00s\xa6\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01d\x02\x83\x01Z\x02e\x03e\x02\x83\x01d\x03k\x03r,e\x04d\x04\x83\x01\x01\x00e\x05d\x05\x83\x01\x01\x00e\x02d\x06d\x07\x85\x02\x19\x00e\x02d\x07d\x08\x85\x02\x19\x00e\x02d\x08d\t\x85\x02\x19\x00e\x02d\td\x03\x85\x02\x19\x00g\x04Z\x06d\nd\x0bd\x0cd\rg\x04Z\x07e\x00e\x06\x83\x01Z\x08e\td\x0e\x83\x01D\x00]$Z\ne\x07e\n\x19\x00e\x08e\n\x19\x00k\x03rte\x04d\x04\x83\x01\x01\x00e\x05d\x05\x83\x01\x01\x00qte\x04d\x0f\x83\x01\x01\x00d\x06S\x00)\x10c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x08\x00\x00\x00\x06\x00\x00\x00C\x00\x00\x00sp\x00\x00\x00d\x01}\x01t\x00d\x02|\x01\x83\x02}\x02g\x00}\x03|\x00D\x00]T}\x04t\x01|\x04\x83\x01}\x05t\x02|\x01d\x03\x18\x00\x83\x01D\x00]"}\x06t\x03|\x05|\x02|\x06\x19\x00\x83\x02}\x05t\x04|\x05\x83\x01}\x05t\x05|\x05\x83\x01}\x05q.t\x03|\x05|\x02d\x04\x19\x00\x83\x02}\x07|\x03\xa0\x06|\x07\xa1\x01\x01\x00q\x16|\x03S\x00)\x05N\xe9 \x00\x00\x00l\x06\x00\x00\x00! 20\\X\xa8 1!\x02\x00\xe9\x01\x00\x00\x00\xe9\xff\xff\xff\xff)\x07Z\x13generateRoundkeys80Z\rstring2number\xda\x05rangeZ\x0baddRoundKeyZ\tsBoxLayerZ\x06pLayer\xda\x06append)\x08\xda\x06blocks\xda\x06roundsZ\troundkeysZ\x03outZ\x05block\xda\x05state\xda\x01iZ\x06cipher\xa9\x00r\t\x00\x00\x00\xda\x00\xda\x07encrypt\x02\x00\x00\x00s\x18\x00\x00\x00\x00\x01\x04\x01\n\x01\x04\x01\x08\x01\x08\x01\x10\x01\x0e\x01\x08\x01\n\x01\x0e\x01\x0c\x01r\x0b\x00\x00\x00z\x12pls input ur flag:r\x00\x00\x00\x00z\x0bwrong flag!\xe9\x00\x00\x00\x00N\xe9\x08\x00\x00\x00\xe9\x10\x00\x00\x00\xe9\x18\x00\x00\x00l\x04\x00\x00\x00\x9e\x1faH\xc4\x13d\rl\x05\x00\x00\x00b]t:\x94Z\x15\x18\x0e\x00l\x04\x00\x00\x000ek95\x04\xb2"l\x05\x00\x00\x00\x88o\xeddY\x13\xb1L\x01\x00\xe9\x04\x00\x00\x00z\x08Correct!)\x0br\x0b\x00\x00\x00\xda\x05inputZ\x03inp\xda\x03len\xda\x05print\xda\x04exitr\x05\x00\x00\x00Z\x04cmpsZ\nout_blocksr\x03\x00\x00\x00r\x08\x00\x00\x00r\t\x00\x00\x00r\t\x00\x00\x00r\t\x00\x00\x00r\n\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x18\x00\x00\x00\x08\x0e\x08\x01\x0c\x01\x08\x01\x08\x01,\x01\x0c\x01\x08\x01\x0c\x01\x10\x01\x08\x01\n\x01N)\x05r\x0e\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x0c\x00\x00\x00r\x0c\x00\x00\x00r\x0c\x00\x00\x00r\r\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\t\n\x01N)\x05r\x0b\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x06\x00\x00\x00r\x06\x00\x00\x00r\x06\x00\x00\x00r\x07\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\x03\n\x01N)\x05r\t\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x07\x00\x00\x00r\x07\x00\x00\x00r\x07\x00\x00\x00r\x08\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\x06\n\x01N)\x05r\n\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x08\x00\x00\x00r\x08\x00\x00\x00r\x08\x00\x00\x00r\t\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\x06\n\x01N)\x05r\x03\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x00\x00\x00\x00r\x00\x00\x00\x00r\x00\x00\x00\x00r\x02\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\x03\n\x01N)\tr\x11\x00\x00\x00\xda\x05rangeZ\x08Sbox_invrH\x00\x00\x00Z\x08PBox_inv\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x10\x00\x00\x00r\x10\x00\x00\x00r\x10\x00\x00\x00r\x16\x00\x00\x00\xda\x08<module>\x03\x00\x00\x00sl\x00\x00\x00$\x01\x12\x01 \x01\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x01\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x01\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\x00\x02\xfd\x04\x04\x12\x02\n\x01'
l = marshal.loads(code)
exec(l)
直接执行是会报错的 拿到这种还是先用dis.dis查看下字节码(本地跑还一直报错 用在线python跑就行了)
l = marshal.loads(code)
import dis
dis.dis(l)
可以发现里面还嵌了marshal
点击查看代码
3 0 LOAD_CONST 0 (12)
2 LOAD_CONST 1 (5)
4 LOAD_CONST 2 (6)
6 LOAD_CONST 3 (11)
8 LOAD_CONST 4 (9)
10 LOAD_CONST 5 (0)
12 LOAD_CONST 6 (10)
14 LOAD_CONST 7 (13)
16 LOAD_CONST 8 (3)
18 LOAD_CONST 9 (14)
20 LOAD_CONST 10 (15)
22 LOAD_CONST 11 (8)
24 LOAD_CONST 12 (4)
26 LOAD_CONST 13 (7)
28 LOAD_CONST 14 (1)
30 LOAD_CONST 15 (2)
32 BUILD_LIST 16
34 STORE_NAME 0 (Sbox)
4 36 LOAD_CONST 16 (<code object <listcomp> at 0x7fbf6f8f83a0, file "", line 4>)
38 LOAD_CONST 17 ('<listcomp>')
40 MAKE_FUNCTION 0
42 LOAD_NAME 1 (range)
44 LOAD_CONST 18 (16)
46 CALL_FUNCTION 1
48 GET_ITER
50 CALL_FUNCTION 1
52 STORE_NAME 2 (Sbox_inv)
5 54 LOAD_CONST 5 (0)
56 LOAD_CONST 18 (16)
58 LOAD_CONST 19 (32)
60 LOAD_CONST 20 (48)
62 LOAD_CONST 14 (1)
64 LOAD_CONST 21 (17)
66 LOAD_CONST 22 (33)
68 LOAD_CONST 23 (49)
70 LOAD_CONST 15 (2)
72 LOAD_CONST 24 (18)
74 LOAD_CONST 25 (34)
76 LOAD_CONST 26 (50)
78 LOAD_CONST 8 (3)
80 LOAD_CONST 27 (19)
82 LOAD_CONST 28 (35)
84 LOAD_CONST 29 (51)
6 86 LOAD_CONST 12 (4)
88 LOAD_CONST 30 (20)
90 LOAD_CONST 31 (36)
92 LOAD_CONST 32 (52)
94 LOAD_CONST 1 (5)
96 LOAD_CONST 33 (21)
98 LOAD_CONST 34 (37)
100 LOAD_CONST 35 (53)
102 LOAD_CONST 2 (6)
104 LOAD_CONST 36 (22)
106 LOAD_CONST 37 (38)
108 LOAD_CONST 38 (54)
110 LOAD_CONST 13 (7)
112 LOAD_CONST 39 (23)
114 LOAD_CONST 40 (39)
116 LOAD_CONST 41 (55)
7 118 LOAD_CONST 11 (8)
120 LOAD_CONST 42 (24)
122 LOAD_CONST 43 (40)
124 LOAD_CONST 44 (56)
126 LOAD_CONST 4 (9)
128 LOAD_CONST 45 (25)
130 LOAD_CONST 46 (41)
132 LOAD_CONST 47 (57)
134 LOAD_CONST 6 (10)
136 LOAD_CONST 48 (26)
138 LOAD_CONST 49 (42)
140 LOAD_CONST 50 (58)
142 LOAD_CONST 3 (11)
144 LOAD_CONST 51 (27)
146 LOAD_CONST 52 (43)
148 LOAD_CONST 53 (59)
8 150 LOAD_CONST 0 (12)
152 LOAD_CONST 54 (28)
154 LOAD_CONST 55 (44)
156 LOAD_CONST 56 (60)
158 LOAD_CONST 7 (13)
160 LOAD_CONST 57 (29)
162 LOAD_CONST 58 (45)
164 LOAD_CONST 59 (61)
166 LOAD_CONST 9 (14)
168 LOAD_CONST 60 (30)
170 LOAD_CONST 61 (46)
172 LOAD_CONST 62 (62)
174 LOAD_CONST 10 (15)
176 LOAD_CONST 63 (31)
178 LOAD_CONST 64 (47)
180 LOAD_CONST 65 (63)
5 182 BUILD_LIST 64
184 STORE_NAME 3 (PBox)
9 186 LOAD_CONST 66 (<code object <listcomp> at 0x7fbf6f8f8660, file "", line 9>)
188 LOAD_CONST 17 ('<listcomp>')
190 MAKE_FUNCTION 0
192 LOAD_NAME 1 (range)
194 LOAD_CONST 67 (64)
196 CALL_FUNCTION 1
198 GET_ITER
200 CALL_FUNCTION 1
202 STORE_NAME 4 (PBox_inv)
11 204 LOAD_NAME 5 (marshal)
206 LOAD_METHOD 6 (loads)
208 LOAD_CONST 68 (b'c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x02\x00\x00\x00C\x00\x00\x00s\x08\x00\x00\x00|\x00|\x01A\x00S\x00)\x01N\xa9\x00)\x02\xda\x05stateZ\x08roundkeyr\x00\x00\x00\x00r\x00\x00\x00\x00\xda\x00\xda\x0baddRoundKey\x02\x00\x00\x00s\x02\x00\x00\x00\x00\x01r\x03\x00\x00\x00s,\t\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00\x06\x00\x00\x00C\x00\x00\x00s6\x00\x00\x00d\x01}\x01t\x00d\x02\x83\x01D\x00]$}\x02|\x01t\x01|\x00|\x02d\x03\x14\x00?\x00d\x04@\x00\x19\x00|\x02d\x03\x14\x00>\x007\x00}\x01q\x0c|\x01S\x00)\x05N\xe9\x00\x00\x00\x00\xe9\x10\x00\x00\x00\xe9\x04\x00\x00\x00\xe9\x0f\x00\x00\x00)\x02\xda\x05rangeZ\x04Sbox)\x03\xda\x05state\xda\x06output\xda\x01i\xa9\x00r\x08\x00\x00\x00\xda\x00\xda\tsBoxLayer\x02\x00\x00\x00s\x08\x00\x00\x00\x00\x01\x04\x01\x0c\x01"\x01r\n\x00\x00\x00s\xe4\x07\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00\x05\x00\x00\x00C\x00\x00\x00s.\x00\x00\x00d\x01}\x01t\x00d\x02\x83\x01D\x00]\x1c}\x02|\x01|\x00|\x02?\x00d\x03@\x00t\x01|\x02\x19\x00>\x007\x00}\x01q\x0c|\x01S\x00)\x04N\xe9\x00\x00\x00\x00\xe9@\x00\x00\x00\xe9\x01\x00\x00\x00)\x02\xda\x05rangeZ\x04PBox)\x03\xda\x05state\xda\x06output\xda\x01i\xa9\x00r\x07\x00\x00\x00\xda\x00\xda\x06pLayer\x02\x00\x00\x00s\x08\x00\x00\x00\x00\x01\x04\x01\x0c\x01\x1a\x01r\t\x00\x00\x00s\xac\x06\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\x04\x00\x00\x00\x03\x00\x00\x00s\x1a\x00\x00\x00t\x00\x87\x00f\x01d\x01d\x02\x84\x08t\x01d\x03\x83\x01D\x00\x83\x01\x83\x01S\x00)\x04Nc\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x05\x00\x00\x00\x13\x00\x00\x00s \x00\x00\x00g\x00|\x00]\x18}\x01t\x00\x88\x00|\x01\x19\x00\x83\x01d\x00|\x01\x14\x00>\x00\x91\x02q\x04S\x00)\x01\xe9\x08\x00\x00\x00)\x01\xda\x03ord)\x02\xda\x02.0\xda\x01c\xa9\x01\xda\x01i\xa9\x00\xda\x00\xda\n<listcomp>\x03\x00\x00\x00s\x04\x00\x00\x00\x06\x00\x02\x00z!string2number.<locals>.<listcomp>r\x00\x00\x00\x00)\x02\xda\x03sum\xda\x05ranger\x04\x00\x00\x00r\x06\x00\x00\x00r\x04\x00\x00\x00r\x07\x00\x00\x00\xda\rstring2number\x02\x00\x00\x00s\x02\x00\x00\x00\x00\x01r\x0b\x00\x00\x00s\x01\x05\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00@\x00\x00\x00s\x1e\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01\xa0\x02d\x02\xa1\x01Z\x03e\x04e\x03\x83\x01\x01\x00d\x03S\x00)\x04c\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x04\x00\x00\x00\x05\x00\x00\x00C\x00\x00\x00st\x00\x00\x00g\x00}\x02t\x00d\x01|\x01d\x01\x17\x00d\x01\x83\x03D\x00]Z}\x03|\x02\xa0\x01|\x00d\x02?\x00\xa1\x01\x01\x00|\x00d\x03@\x00d\x04>\x00|\x00d\x05?\x00\x17\x00}\x00t\x02|\x00d\x06?\x00\x19\x00d\x06>\x00|\x00d\x07d\x06\x13\x00d\x01\x18\x00@\x00\x17\x00}\x00|\x00|\x03d\x08>\x00|\x00d\x05?\x00A\x00N\x00}\x00q\x14|\x02S\x00)\tN\xe9\x01\x00\x00\x00\xe9\x10\x00\x00\x00i\xff\xff\x07\x00\xe9=\x00\x00\x00\xe9\x13\x00\x00\x00\xe9L\x00\x00\x00\xe9\x02\x00\x00\x00\xe9\x0f\x00\x00\x00)\x03\xda\x05range\xda\x06appendZ\x04Sbox)\x04\xda\x03key\xda\x06roundsZ\troundkeys\xda\x01i\xa9\x00r\x0c\x00\x00\x00\xda\x00\xda\x13generateRoundkeys80\x02\x00\x00\x00s\x0e\x00\x00\x00\x00\x01\x04\x01\x14\x01\x0e\x01\x14\x01 \x01\x16\x01r\x0e\x00\x00\x00sF\x03\x00\x00c\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x06\x00\x00\x00@\x00\x00\x00s\xa6\x00\x00\x00d\x00d\x01\x84\x00Z\x00e\x01d\x02\x83\x01Z\x02e\x03e\x02\x83\x01d\x03k\x03r,e\x04d\x04\x83\x01\x01\x00e\x05d\x05\x83\x01\x01\x00e\x02d\x06d\x07\x85\x02\x19\x00e\x02d\x07d\x08\x85\x02\x19\x00e\x02d\x08d\t\x85\x02\x19\x00e\x02d\td\x03\x85\x02\x19\x00g\x04Z\x06d\nd\x0bd\x0cd\rg\x04Z\x07e\x00e\x06\x83\x01Z\x08e\td\x0e\x83\x01D\x00]$Z\ne\x07e\n\x19\x00e\x08e\n\x19\x00k\x03rte\x04d\x04\x83\x01\x01\x00e\x05d\x05\x83\x01\x01\x00qte\x04d\x0f\x83\x01\x01\x00d\x06S\x00)\x10c\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x08\x00\x00\x00\x06\x00\x00\x00C\x00\x00\x00sp\x00\x00\x00d\x01}\x01t\x00d\x02|\x01\x83\x02}\x02g\x00}\x03|\x00D\x00]T}\x04t\x01|\x04\x83\x01}\x05t\x02|\x01d\x03\x18\x00\x83\x01D\x00]"}\x06t\x03|\x05|\x02|\x06\x19\x00\x83\x02}\x05t\x04|\x05\x83\x01}\x05t\x05|\x05\x83\x01}\x05q.t\x03|\x05|\x02d\x04\x19\x00\x83\x02}\x07|\x03\xa0\x06|\x07\xa1\x01\x01\x00q\x16|\x03S\x00)\x05N\xe9 \x00\x00\x00l\x06\x00\x00\x00! 20\\X\xa8 1!\x02\x00\xe9\x01\x00\x00\x00\xe9\xff\xff\xff\xff)\x07Z\x13generateRoundkeys80Z\rstring2number\xda\x05rangeZ\x0baddRoundKeyZ\tsBoxLayerZ\x06pLayer\xda\x06append)\x08\xda\x06blocks\xda\x06roundsZ\troundkeysZ\x03outZ\x05block\xda\x05state\xda\x01iZ\x06cipher\xa9\x00r\t\x00\x00\x00\xda\x00\xda\x07encrypt\x02\x00\x00\x00s\x18\x00\x00\x00\x00\x01\x04\x01\n\x01\x04\x01\x08\x01\x08\x01\x10\x01\x0e\x01\x08\x01\n\x01\x0e\x01\x0c\x01r\x0b\x00\x00\x00z\x12pls input ur flag:r\x00\x00\x00\x00z\x0bwrong flag!\xe9\x00\x00\x00\x00N\xe9\x08\x00\x00\x00\xe9\x10\x00\x00\x00\xe9\x18\x00\x00\x00l\x04\x00\x00\x00\x9e\x1faH\xc4\x13d\rl\x05\x00\x00\x00b]t:\x94Z\x15\x18\x0e\x00l\x04\x00\x00\x000ek95\x04\xb2"l\x05\x00\x00\x00\x88o\xeddY\x13\xb1L\x01\x00\xe9\x04\x00\x00\x00z\x08Correct!)\x0br\x0b\x00\x00\x00\xda\x05inputZ\x03inp\xda\x03len\xda\x05print\xda\x04exitr\x05\x00\x00\x00Z\x04cmpsZ\nout_blocksr\x03\x00\x00\x00r\x08\x00\x00\x00r\t\x00\x00\x00r\t\x00\x00\x00r\t\x00\x00\x00r\n\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x18\x00\x00\x00\x08\x0e\x08\x01\x0c\x01\x08\x01\x08\x01,\x01\x0c\x01\x08\x01\x0c\x01\x10\x01\x08\x01\n\x01N)\x05r\x0e\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x0c\x00\x00\x00r\x0c\x00\x00\x00r\x0c\x00\x00\x00r\r\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\t\n\x01N)\x05r\x0b\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x06\x00\x00\x00r\x06\x00\x00\x00r\x06\x00\x00\x00r\x07\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\x03\n\x01N)\x05r\t\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x07\x00\x00\x00r\x07\x00\x00\x00r\x07\x00\x00\x00r\x08\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\x06\n\x01N)\x05r\n\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x08\x00\x00\x00r\x08\x00\x00\x00r\x08\x00\x00\x00r\t\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\x06\n\x01N)\x05r\x03\x00\x00\x00\xda\x07marshal\xda\x05loads\xda\x02co\xda\x04execr\x00\x00\x00\x00r\x00\x00\x00\x00r\x00\x00\x00\x00r\x02\x00\x00\x00\xda\x08<module>\x02\x00\x00\x00s\x04\x00\x00\x00\x08\x03\n\x01')
210 CALL_METHOD 1
212 STORE_NAME 7 (co)
12 214 LOAD_NAME 8 (exec)
216 LOAD_NAME 7 (co)
218 CALL_FUNCTION 1
220 POP_TOP
222 LOAD_CONST 69 (None)
224 RETURN_VALUE
Disassembly of <code object <listcomp> at 0x7fbf6f8f83a0, file "", line 4>:
4 0 BUILD_LIST 0
2 LOAD_FAST 0 (.0)
>> 4 FOR_ITER 14 (to 20)
6 STORE_FAST 1 (x)
8 LOAD_GLOBAL 0 (Sbox)
10 LOAD_METHOD 1 (index)
12 LOAD_FAST 1 (x)
14 CALL_METHOD 1
16 LIST_APPEND 2
18 JUMP_ABSOLUTE 4
>> 20 RETURN_VALUE
Disassembly of <code object <listcomp> at 0x7fbf6f8f8660, file "", line 9>:
9 0 BUILD_LIST 0
2 LOAD_FAST 0 (.0)
>> 4 FOR_ITER 14 (to 20)
6 STORE_FAST 1 (x)
8 LOAD_GLOBAL 0 (PBox)
10 LOAD_METHOD 1 (index)
12 LOAD_FAST 1 (x)
14 CALL_METHOD 1
16 LIST_APPEND 2
18 JUMP_ABSOLUTE 4
>> 20 RETURN_VALUE
注意到有几个显眼特征:
- Sbox
- PBox
- generateRoundkeys80
搜索可以得到:
说明是present算法
那我们怎么得到那几个关键变量的值呢?
这里跟着官方WP学习了一手全局hook的思想

但是实际用的时候会发现 在exec后用的话 程序会直接退出(调用了exit())
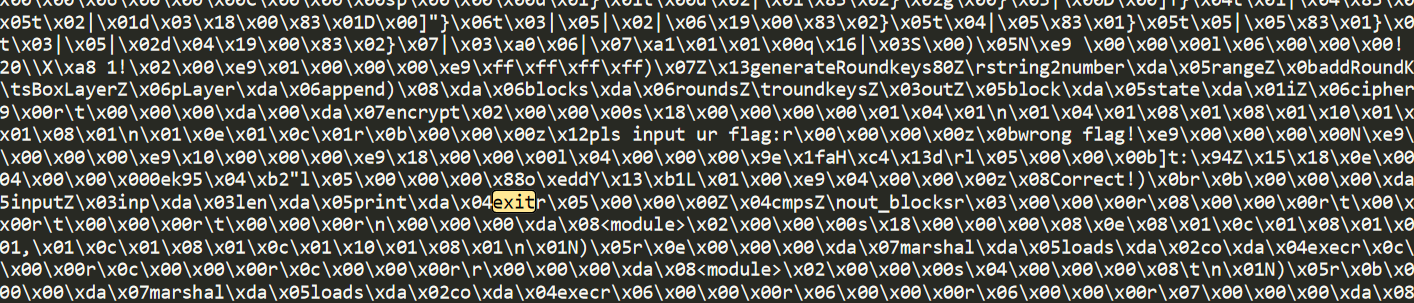
而我们在exec执行前定义一个exit 相当于把系统的exit给覆盖掉 (利用全局特性 类似web get/post修改全局变量)
但是这样运行还是报错 我们再加个try except块来保证能得到globals()
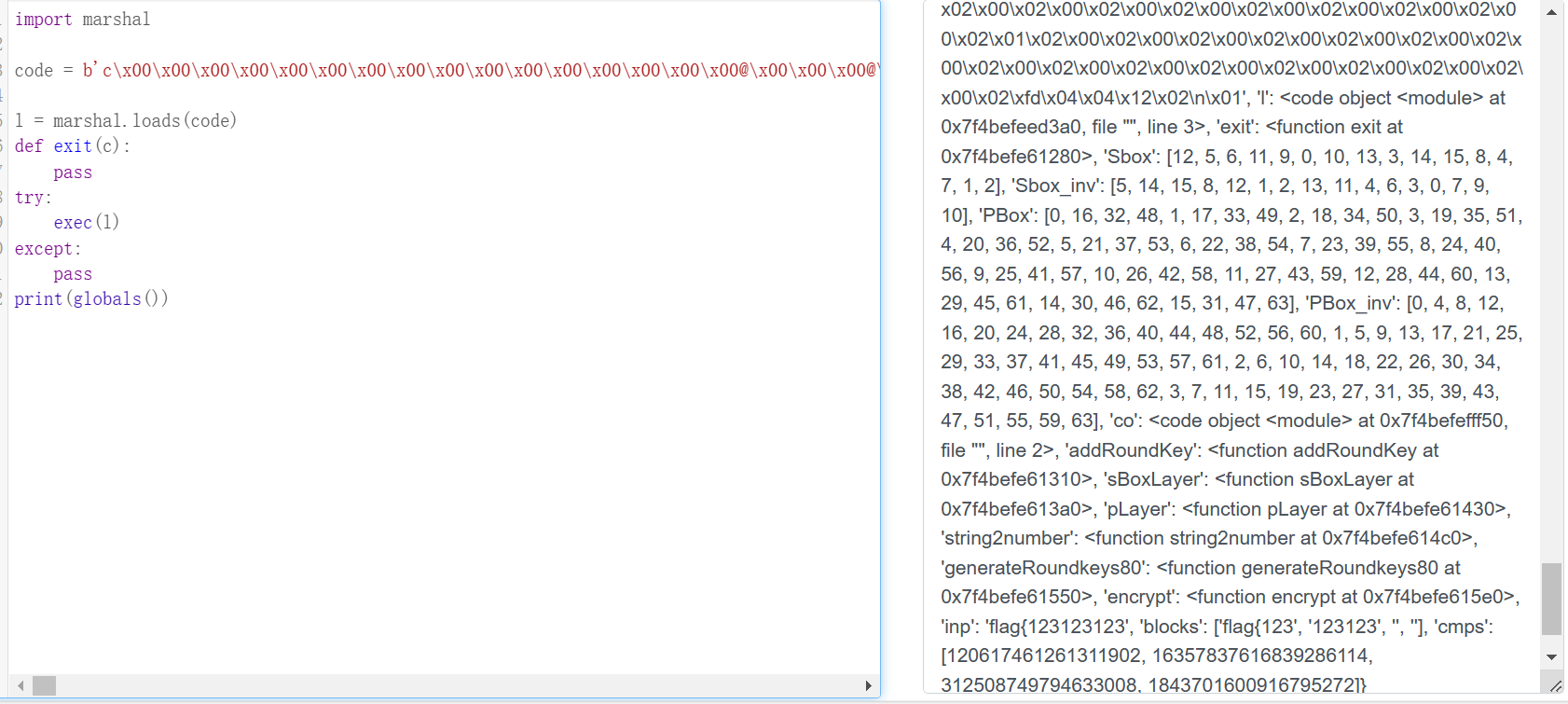
可以看到这时已经能得到一些关键值了
总结一下 : 现在得到了
- sbox
- sbox_inv
- pbox
- pbox_inv
- cmps
发现这里还少了 key的值
说明key不在globals里 这里再次利用全局hook的技巧
key在generateRoundkeys80中被调用
所以我们修改generateRoundkeys80 使它输出传入的两个变量的值即可(使用lambda python高级特征学到了)
generateRoundkeys80 = lambda x1,x2: print(x1,x2)
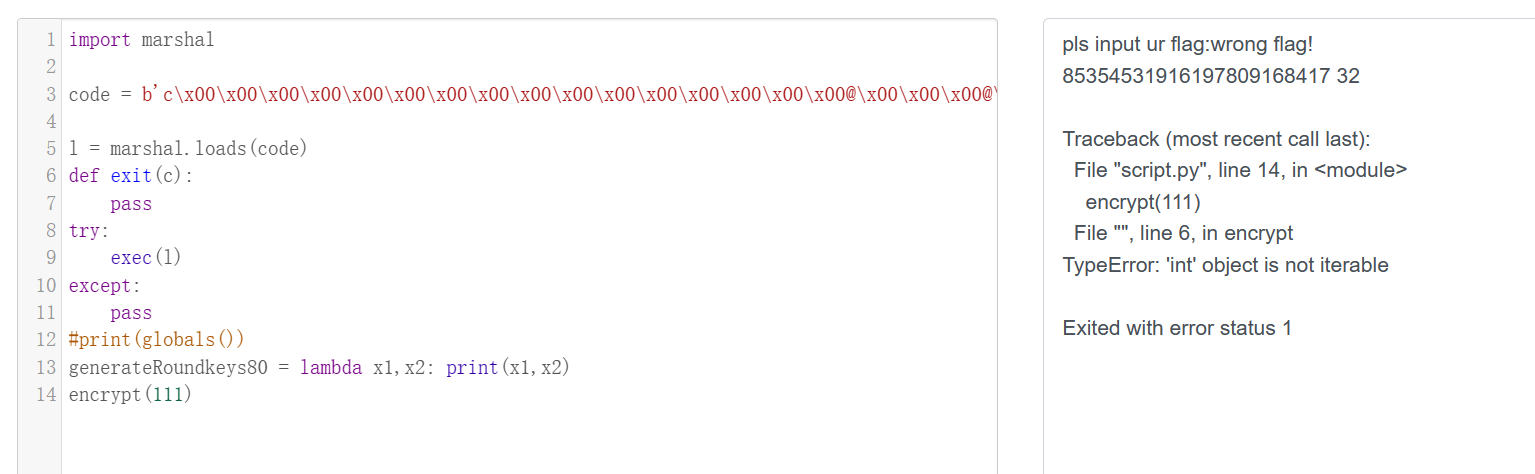
这就得到了key!
但是直接套会发现解出来不对...
那就只能看字节码 手动脱marshal(5,6次吧)
得到关键的generatekey80的字节码(最后一层才脱出来 说明关键应该在这里)
点击查看代码
2 0 LOAD_CONST 0 (<code object generateRoundkeys80 at 0x7fb5577493a0, file "", line 2>)
2 LOAD_CONST 1 ('generateRoundkeys80')
4 MAKE_FUNCTION 0
6 STORE_NAME 0 (generateRoundkeys80)
11 8 LOAD_NAME 1 (marshal)
10 LOAD_METHOD 2 (loads)
12 LOAD_CONST 2 0 LOAD_CONST 0 (<code object encrypt at 0x7f7a22c7c660, file "", line 2>)
2 LOAD_CONST 1 ('encrypt')
4 MAKE_FUNCTION 0
6 STORE_NAME 0 (encrypt)
16 8 LOAD_NAME 1 (input)
10 LOAD_CONST 2 ('pls input ur flag:')
12 CALL_FUNCTION 1
14 STORE_NAME 2 (inp)
17 16 LOAD_NAME 3 (len)
18 LOAD_NAME 2 (inp)
20 CALL_FUNCTION 1
22 LOAD_CONST 3 (32)
24 COMPARE_OP 3 (!=)
26 POP_JUMP_IF_FALSE 44
18 28 LOAD_NAME 4 (print)
30 LOAD_CONST 4 ('wrong flag!')
32 CALL_FUNCTION 1
34 POP_TOP
19 36 LOAD_NAME 5 (exit)
38 LOAD_CONST 5 (0)
40 CALL_FUNCTION 1
42 POP_TOP
20 >> 44 LOAD_NAME 2 (inp)
46 LOAD_CONST 6 (None)
48 LOAD_CONST 7 (8)
50 BUILD_SLICE 2
52 BINARY_SUBSCR
54 LOAD_NAME 2 (inp)
56 LOAD_CONST 7 (8)
58 LOAD_CONST 8 (16)
60 BUILD_SLICE 2
62 BINARY_SUBSCR
64 LOAD_NAME 2 (inp)
66 LOAD_CONST 8 (16)
68 LOAD_CONST 9 (24)
70 BUILD_SLICE 2
72 BINARY_SUBSCR
74 LOAD_NAME 2 (inp)
76 LOAD_CONST 9 (24)
78 LOAD_CONST 3 (32)
80 BUILD_SLICE 2
82 BINARY_SUBSCR
84 BUILD_LIST 4
86 STORE_NAME 6 (blocks)
21 88 LOAD_CONST 10 (120617461261311902)
90 LOAD_CONST 11 (16357837616839286114)
92 LOAD_CONST 12 (312508749794633008)
94 LOAD_CONST 13 (1843701600916795272)
96 BUILD_LIST 4
98 STORE_NAME 7 (cmps)
22 100 LOAD_NAME 0 (encrypt)
102 LOAD_NAME 6 (blocks)
104 CALL_FUNCTION 1
106 STORE_NAME 8 (out_blocks)
23 108 LOAD_NAME 9 (range)
110 LOAD_CONST 14 (4)
112 CALL_FUNCTION 1
114 GET_ITER
>> 116 FOR_ITER 36 (to 154)
118 STORE_NAME 10 (i)
24 120 LOAD_NAME 7 (cmps)
122 LOAD_NAME 10 (i)
124 BINARY_SUBSCR
126 LOAD_NAME 8 (out_blocks)
128 LOAD_NAME 10 (i)
130 BINARY_SUBSCR
132 COMPARE_OP 3 (!=)
134 POP_JUMP_IF_FALSE 116
25 136 LOAD_NAME 4 (print)
138 LOAD_CONST 4 ('wrong flag!')
140 CALL_FUNCTION 1
142 POP_TOP
26 144 LOAD_NAME 5 (exit)
146 LOAD_CONST 5 (0)
148 CALL_FUNCTION 1
150 POP_TOP
152 JUMP_ABSOLUTE 116
27 >> 154 LOAD_NAME 4 (print)
156 LOAD_CONST 15 ('Correct!')
158 CALL_FUNCTION 1
160 POP_TOP
162 LOAD_CONST 6 (None)
164 RETURN_VALUE
Disassembly of <code object encrypt at 0x7f7a22c7c660, file "", line 2>:
3 0 LOAD_CONST 1 (32)
2 STORE_FAST 1 (rounds)
4 4 LOAD_GLOBAL 0 (generateRoundkeys80)
6 LOAD_CONST 2 (85354531916197809168417)
8 LOAD_FAST 1 (rounds)
10 CALL_FUNCTION 2
12 STORE_FAST 2 (roundkeys)
5 14 BUILD_LIST 0
16 STORE_FAST 3 (out)
6 18 LOAD_FAST 0 (blocks)
20 GET_ITER
>> 22 FOR_ITER 84 (to 108)
24 STORE_FAST 4 (block)
7 26 LOAD_GLOBAL 1 (string2number)
28 LOAD_FAST 4 (block)
30 CALL_FUNCTION 1
32 STORE_FAST 5 (state)
8 34 LOAD_GLOBAL 2 (range)
36 LOAD_FAST 1 (rounds)
38 LOAD_CONST 3 (1)
40 BINARY_SUBTRACT
42 CALL_FUNCTION 1
44 GET_ITER
>> 46 FOR_ITER 34 (to 82)
48 STORE_FAST 6 (i)
9 50 LOAD_GLOBAL 3 (addRoundKey)
52 LOAD_FAST 5 (state)
54 LOAD_FAST 2 (roundkeys)
56 LOAD_FAST 6 (i)
58 BINARY_SUBSCR
60 CALL_FUNCTION 2
62 STORE_FAST 5 (state)
10 64 LOAD_GLOBAL 4 (sBoxLayer)
66 LOAD_FAST 5 (state)
68 CALL_FUNCTION 1
70 STORE_FAST 5 (state)
11 72 LOAD_GLOBAL 5 (pLayer)
74 LOAD_FAST 5 (state)
76 CALL_FUNCTION 1
78 STORE_FAST 5 (state)
80 JUMP_ABSOLUTE 46
12 >> 82 LOAD_GLOBAL 3 (addRoundKey)
84 LOAD_FAST 5 (state)
86 LOAD_FAST 2 (roundkeys)
88 LOAD_CONST 4 (-1)
90 BINARY_SUBSCR
92 CALL_FUNCTION 2
94 STORE_FAST 7 (cipher)
13 96 LOAD_FAST 3 (out)
98 LOAD_METHOD 6 (append)
100 LOAD_FAST 7 (cipher)
102 CALL_METHOD 1
104 POP_TOP
106 JUMP_ABSOLUTE 22
14 >> 108 LOAD_FAST 3 (out)
110 RETURN_VALUE
None
14 CALL_METHOD 1
16 STORE_NAME 3 (co)
12 18 LOAD_NAME 4 (exec)
20 LOAD_NAME 3 (co)
22 CALL_FUNCTION 1
24 POP_TOP
26 LOAD_CONST 3 (None)
28 RETURN_VALUE
Disassembly of <code object generateRoundkeys80 at 0x7fb5577493a0, file "", line 2>:
3 0 BUILD_LIST 0
2 STORE_FAST 2 (roundkeys)
4 4 LOAD_GLOBAL 0 (range)
6 LOAD_CONST 1 (1)
8 LOAD_FAST 1 (rounds)
10 LOAD_CONST 1 (1)
12 BINARY_ADD
14 LOAD_CONST 1 (1)
16 CALL_FUNCTION 3
18 GET_ITER
>> 20 FOR_ITER 90 (to 112)
22 STORE_FAST 3 (i)
5 24 LOAD_FAST 2 (roundkeys)
26 LOAD_METHOD 1 (append)
28 LOAD_FAST 0 (key)
30 LOAD_CONST 2 (16)
32 BINARY_RSHIFT
34 CALL_METHOD 1
36 POP_TOP
6 38 LOAD_FAST 0 (key)
40 LOAD_CONST 3 (524287)
42 BINARY_AND
44 LOAD_CONST 4 (61)
46 BINARY_LSHIFT
48 LOAD_FAST 0 (key)
50 LOAD_CONST 5 (19)
52 BINARY_RSHIFT
54 BINARY_ADD
56 STORE_FAST 0 (key)
7 58 LOAD_GLOBAL 2 (Sbox)
60 LOAD_FAST 0 (key)
62 LOAD_CONST 6 (76)
64 BINARY_RSHIFT
66 BINARY_SUBSCR
68 LOAD_CONST 6 (76)
70 BINARY_LSHIFT
72 LOAD_FAST 0 (key)
74 LOAD_CONST 7 (2)
76 LOAD_CONST 6 (76)
78 BINARY_POWER
80 LOAD_CONST 1 (1)
82 BINARY_SUBTRACT
84 BINARY_AND
86 BINARY_ADD
88 STORE_FAST 0 (key)
8 90 LOAD_FAST 0 (key)
92 LOAD_FAST 3 (i)
94 LOAD_CONST 8 (15)
96 BINARY_LSHIFT
98 LOAD_FAST 0 (key)
100 LOAD_CONST 5 (19)
102 BINARY_RSHIFT
104 BINARY_XOR
106 INPLACE_XOR
108 STORE_FAST 0 (key)
110 JUMP_ABSOLUTE 20
9 >> 112 LOAD_FAST 2 (roundkeys)
114 RETURN_VALUE
None
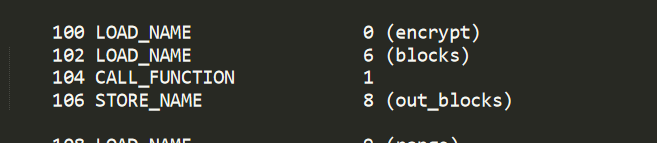
这里也能解释为什么前面全局hook后调用encrypt(xxx)
结合标准roundkeys生成算法
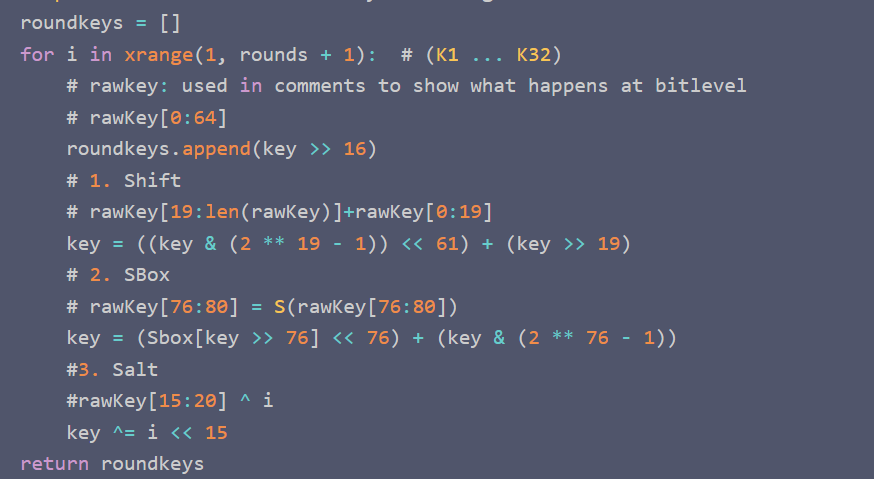
再对比字节码(通过特征参数定位)
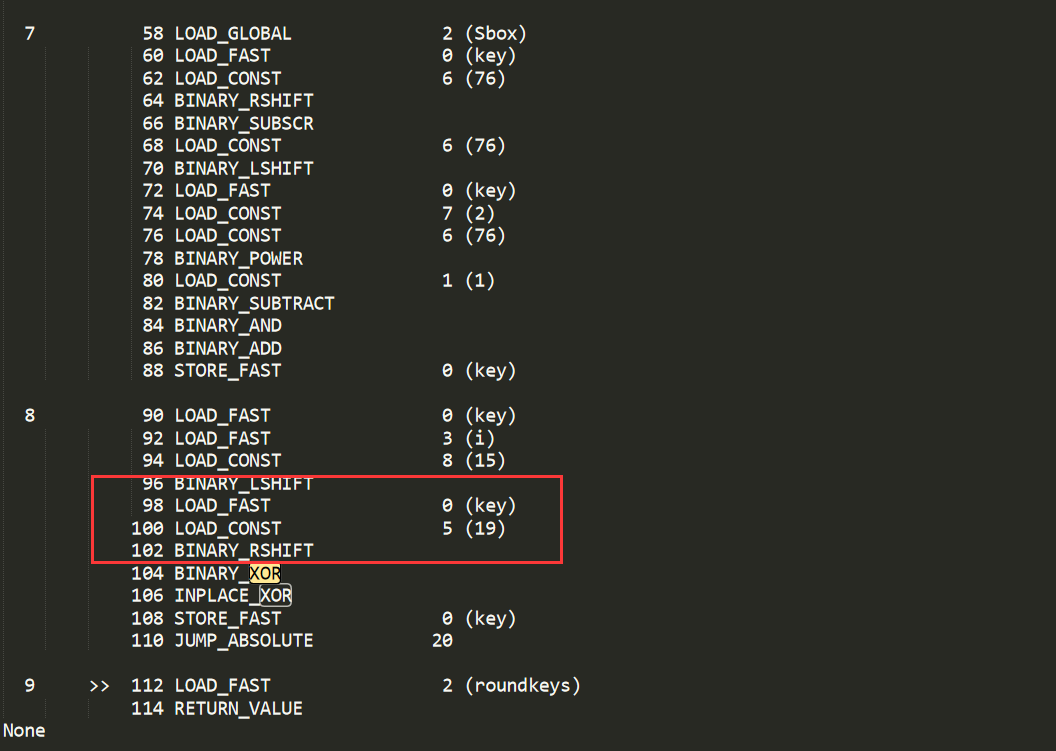
可以发现在 key ^= i << 15 的基础上变成了
key ^= (i<<15) ^ (key >> 19)
所以在标准代码上稍作修改:(直接搬官方的了 应该是对着字节码写的吧 网上找的都不好直接改 还不如自己手搓字节码)
def sBoxLayer_dec(state):
output = 0
for i in range(16):
output += Sbox_inv[( state >> (i*4)) & 0xF] << (i*4)
return output
def pLayer_dec(state):
output = 0
for i in range(64):
output += ((state >> i) & 0x01) << PBox_inv[i]
return output
def generateRoundkeys80(key,rounds):
roundkeys = []
for i in range(1,rounds+1,1):
roundkeys.append(key >>16)
key = ((key & (2**19-1)) << 61) + (key >> 19)
key = (Sbox[key >> 76] << 76)+(key & (2**76-1))
key ^= (i << 15)^(key >> 19)
return roundkeys
def string2number(i):
return sum([ord(i[c])<<(8*c) for c in range(8)])
# 0 1 2 3 4 5 6 7 8 9 a b c d e f
Sbox= [0xc,0x5,0x6,0xb,0x9,0x0,0xa,0xd,0x3,0xe,0xf,0x8,0x4,0x7,0x1,0x2]
Sbox_inv = [Sbox.index(x) for x in range(16)]
PBox = [0,16,32,48,1,17,33,49,2,18,34,50,3,19,35,51,
4,20,36,52,5,21,37,53,6,22,38,54,7,23,39,55,
8,24,40,56,9,25,41,57,10,26,42,58,11,27,43,59,
12,28,44,60,13,29,45,61,14,30,46,62,15,31,47,63]
PBox_inv = [PBox.index(x) for x in range(64)]
def addRoundKey(state,roundkey):
return state ^ roundkey
def decrypt(blocks):
rounds = 32
roundkeys = generateRoundkeys80(85354531916197809168417, rounds)
flag = ''
for block in blocks:
state = block
for i in range(rounds-1):
state = addRoundKey(state, roundkeys[-i-1])
state = pLayer_dec(state)
state = sBoxLayer_dec(state)
decipher = addRoundKey(state, roundkeys[0])
flag += ''.join([chr(decipher>>(c*8) & 0xff) for c in range(8)])
print(flag)
cmps = [120617461261311902, 16357837616839286114, 312508749794633008, 1843701600916795272]
decrypt(cmps)
# 83ab766012aef9934c95ed93e9822a91
想了想还是自己手搓一下(练习下字节码) 把加密代码写了下:
还复习了几个点:
- INPLACE_ADD: output +=
- BINARY_SUBSCR 用来划分块 避免字节码产生歧义
自己写的时候 发现string2number直接看字节码是不太能写出来的 但知道原理自己写一下也差不了多少
def encrypt():
rounds = 32
generateRoundkeys80(85354531916197809168417,rounds)
for block in blocks:
state = string2number(block)
for i in range(rounds-1):
state = addRoundKey(state,roundkeys[i]) # roundkeys是数组
state = sBoxLayer(state)
state = pLayer(state)
cipher = addRoundKey(state,roundkeys[-1])
out.append(cipher)
return out
def addRoundKey(state,roundkey):
return state^roundkey
def string2number(i):
return sum([ord(i[c])<<(8*c) for c in range(8)])
def sBoxLayer(state):
output = 0
for i in range(16):
output += Sbox[(4*i>>15)&15]<<(4*i)
return output
def pLayer(state):
output = 0
for i in range(64):
output += ((state>>i)&1)<<PBox[i]
return output
def generateRoundkeys80(key, rounds):
"""Generate the roundkeys for a 80-bit key
Input:
key: the key as a 80-bit integer
rounds: the number of rounds as an integer
Output: list of 64-bit roundkeys as integers"""
roundkeys = []
for i in xrange(1, rounds + 1): # (K1 ... K32)
# rawkey: used in comments to show what happens at bitlevel
# rawKey[0:64]
roundkeys.append(key >> 16)
# 1. Shift
# rawKey[19:len(rawKey)]+rawKey[0:19]
key = ((key & (2 ** 19 - 1)) << 61) + (key >> 19)
# 2. SBox
# rawKey[76:80] = S(rawKey[76:80])
key = (Sbox[key >> 76] << 76) + (key & (2 ** 76 - 1))
#3. Salt
#rawKey[15:20] ^ i
key ^= (i << 15)^(key>>19)
return roundkeys
最后放一份手脱marshal的大致字节码:
点击查看代码
3 0 LOAD_CONST 0 (12)
2 LOAD_CONST 1 (5)
4 LOAD_CONST 2 (6)
6 LOAD_CONST 3 (11)
8 LOAD_CONST 4 (9)
10 LOAD_CONST 5 (0)
12 LOAD_CONST 6 (10)
14 LOAD_CONST 7 (13)
16 LOAD_CONST 8 (3)
18 LOAD_CONST 9 (14)
20 LOAD_CONST 10 (15)
22 LOAD_CONST 11 (8)
24 LOAD_CONST 12 (4)
26 LOAD_CONST 13 (7)
28 LOAD_CONST 14 (1)
30 LOAD_CONST 15 (2)
32 BUILD_LIST 16
34 STORE_NAME 0 (Sbox)
4 36 LOAD_CONST 16 (<code object <listcomp> at 0x7f7b29b00a80, file "", line 4>)
38 LOAD_CONST 17 ('<listcomp>')
40 MAKE_FUNCTION 0
42 LOAD_NAME 1 (range)
44 LOAD_CONST 18 (16)
46 CALL_FUNCTION 1
48 GET_ITER
50 CALL_FUNCTION 1
52 STORE_NAME 2 (Sbox_inv)
5 54 LOAD_CONST 5 (0)
56 LOAD_CONST 18 (16)
58 LOAD_CONST 19 (32)
60 LOAD_CONST 20 (48)
62 LOAD_CONST 14 (1)
64 LOAD_CONST 21 (17)
66 LOAD_CONST 22 (33)
68 LOAD_CONST 23 (49)
70 LOAD_CONST 15 (2)
72 LOAD_CONST 24 (18)
74 LOAD_CONST 25 (34)
76 LOAD_CONST 26 (50)
78 LOAD_CONST 8 (3)
80 LOAD_CONST 27 (19)
82 LOAD_CONST 28 (35)
84 LOAD_CONST 29 (51)
6 86 LOAD_CONST 12 (4)
88 LOAD_CONST 30 (20)
90 LOAD_CONST 31 (36)
92 LOAD_CONST 32 (52)
94 LOAD_CONST 1 (5)
96 LOAD_CONST 33 (21)
98 LOAD_CONST 34 (37)
100 LOAD_CONST 35 (53)
102 LOAD_CONST 2 (6)
104 LOAD_CONST 36 (22)
106 LOAD_CONST 37 (38)
108 LOAD_CONST 38 (54)
110 LOAD_CONST 13 (7)
112 LOAD_CONST 39 (23)
114 LOAD_CONST 40 (39)
116 LOAD_CONST 41 (55)
7 118 LOAD_CONST 11 (8)
120 LOAD_CONST 42 (24)
122 LOAD_CONST 43 (40)
124 LOAD_CONST 44 (56)
126 LOAD_CONST 4 (9)
128 LOAD_CONST 45 (25)
130 LOAD_CONST 46 (41)
132 LOAD_CONST 47 (57)
134 LOAD_CONST 6 (10)
136 LOAD_CONST 48 (26)
138 LOAD_CONST 49 (42)
140 LOAD_CONST 50 (58)
142 LOAD_CONST 3 (11)
144 LOAD_CONST 51 (27)
146 LOAD_CONST 52 (43)
148 LOAD_CONST 53 (59)
8 150 LOAD_CONST 0 (12)
152 LOAD_CONST 54 (28)
154 LOAD_CONST 55 (44)
156 LOAD_CONST 56 (60)
158 LOAD_CONST 7 (13)
160 LOAD_CONST 57 (29)
162 LOAD_CONST 58 (45)
164 LOAD_CONST 59 (61)
166 LOAD_CONST 9 (14)
168 LOAD_CONST 60 (30)
170 LOAD_CONST 61 (46)
172 LOAD_CONST 62 (62)
174 LOAD_CONST 10 (15)
176 LOAD_CONST 63 (31)
178 LOAD_CONST 64 (47)
180 LOAD_CONST 65 (63)
5 182 BUILD_LIST 64
184 STORE_NAME 3 (PBox)
9 186 LOAD_CONST 66 (<code object <listcomp> at 0x7f7b29a76a80, file "", line 9>)
188 LOAD_CONST 17 ('<listcomp>')
190 MAKE_FUNCTION 0
192 LOAD_NAME 1 (range)
194 LOAD_CONST 67 (64)
196 CALL_FUNCTION 1
198 GET_ITER
200 CALL_FUNCTION 1
202 STORE_NAME 4 (PBox_inv)
11 204 LOAD_NAME 5 (marshal)
206 LOAD_METHOD 6 (loads)
2 0 LOAD_CONST 0 (<code object addRoundKey at 0x7f5223878a80, file "", line 2>)
2 LOAD_CONST 1 ('addRoundKey')
4 MAKE_FUNCTION 0
6 STORE_NAME 0 (addRoundKey)
5 8 LOAD_NAME 1 (marshal)
10 LOAD_METHOD 2 (loads)
2 0 LOAD_CONST 0 (<code object sBoxLayer at 0x7fab1d117a80, file "", line 2>)
2 LOAD_CONST 1 ('sBoxLayer')
4 MAKE_FUNCTION 0
6 STORE_NAME 0 (sBoxLayer)
8 8 LOAD_NAME 1 (marshal)
10 LOAD_METHOD 2 (loads)
2 0 LOAD_CONST 0 (<code object pLayer at 0x7f023882ba80, file "", line 2>)
2 LOAD_CONST 1 ('pLayer')
4 MAKE_FUNCTION 0
6 STORE_NAME 0 (pLayer)
8 8 LOAD_NAME 1 (marshal)
10 LOAD_METHOD 2 (loads)
2 0 LOAD_CONST 0 (<code object string2number at 0x7f7370421a80, file "", line 2>)
2 LOAD_CONST 1 ('string2number')
4 MAKE_FUNCTION 0
6 STORE_NAME 0 (string2number)
5 8 LOAD_NAME 1 (marshal)
10 LOAD_METHOD 2 (loads)
2 0 LOAD_CONST 0 (<code object generateRoundkeys80 at 0x7f133db26a80, file "", line 2>)
2 LOAD_CONST 1 ('generateRoundkeys80')
4 MAKE_FUNCTION 0
6 STORE_NAME 0 (generateRoundkeys80)
11 8 LOAD_NAME 1 (marshal)
10 LOAD_METHOD 2 (loads)
2 0 LOAD_CONST 0 (<code object encrypt at 0x7f57c4c3aa80, file "", line 2>)
2 LOAD_CONST 1 ('encrypt')
4 MAKE_FUNCTION 0
6 STORE_NAME 0 (encrypt)
16 8 LOAD_NAME 1 (input)
10 LOAD_CONST 2 ('pls input ur flag:')
12 CALL_FUNCTION 1
14 STORE_NAME 2 (inp)
17 16 LOAD_NAME 3 (len)
18 LOAD_NAME 2 (inp)
20 CALL_FUNCTION 1
22 LOAD_CONST 3 (32)
24 COMPARE_OP 3 (!=)
26 POP_JUMP_IF_FALSE 44
18 28 LOAD_NAME 4 (print)
30 LOAD_CONST 4 ('wrong flag!')
32 CALL_FUNCTION 1
34 POP_TOP
19 36 LOAD_NAME 5 (exit)
38 LOAD_CONST 5 (0)
40 CALL_FUNCTION 1
42 POP_TOP
20 >> 44 LOAD_NAME 2 (inp)
46 LOAD_CONST 6 (None)
48 LOAD_CONST 7 (8)
50 BUILD_SLICE 2
52 BINARY_SUBSCR
54 LOAD_NAME 2 (inp)
56 LOAD_CONST 7 (8)
58 LOAD_CONST 8 (16)
60 BUILD_SLICE 2
62 BINARY_SUBSCR
64 LOAD_NAME 2 (inp)
66 LOAD_CONST 8 (16)
68 LOAD_CONST 9 (24)
70 BUILD_SLICE 2
72 BINARY_SUBSCR
74 LOAD_NAME 2 (inp)
76 LOAD_CONST 9 (24)
78 LOAD_CONST 3 (32)
80 BUILD_SLICE 2
82 BINARY_SUBSCR
84 BUILD_LIST 4
86 STORE_NAME 6 (blocks)
21 88 LOAD_CONST 10 (120617461261311902)
90 LOAD_CONST 11 (16357837616839286114)
92 LOAD_CONST 12 (312508749794633008)
94 LOAD_CONST 13 (1843701600916795272)
96 BUILD_LIST 4
98 STORE_NAME 7 (cmps)
22 100 LOAD_NAME 0 (encrypt)
102 LOAD_NAME 6 (blocks)
104 CALL_FUNCTION 1
106 STORE_NAME 8 (out_blocks)
23 108 LOAD_NAME 9 (range)
110 LOAD_CONST 14 (4)
112 CALL_FUNCTION 1
114 GET_ITER
>> 116 FOR_ITER 36 (to 154)
118 STORE_NAME 10 (i)
24 120 LOAD_NAME 7 (cmps)
122 LOAD_NAME 10 (i)
124 BINARY_SUBSCR
126 LOAD_NAME 8 (out_blocks)
128 LOAD_NAME 10 (i)
130 BINARY_SUBSCR
132 COMPARE_OP 3 (!=)
134 POP_JUMP_IF_FALSE 116
25 136 LOAD_NAME 4 (print)
138 LOAD_CONST 4 ('wrong flag!')
140 CALL_FUNCTION 1
142 POP_TOP
26 144 LOAD_NAME 5 (exit)
146 LOAD_CONST 5 (0)
148 CALL_FUNCTION 1
150 POP_TOP
152 JUMP_ABSOLUTE 116
27 >> 154 LOAD_NAME 4 (print)
156 LOAD_CONST 15 ('Correct!')
158 CALL_FUNCTION 1
160 POP_TOP
162 LOAD_CONST 6 (None)
164 RETURN_VALUE
Disassembly of <code object encrypt at 0x7f57c4c3aa80, file "", line 2>:
3 0 LOAD_CONST 1 (32)
2 STORE_FAST 1 (rounds)
4 4 LOAD_GLOBAL 0 (generateRoundkeys80)
6 LOAD_CONST 2 (85354531916197809168417)
8 LOAD_FAST 1 (rounds)
10 CALL_FUNCTION 2
12 STORE_FAST 2 (roundkeys)
5 14 BUILD_LIST 0
16 STORE_FAST 3 (out)
6 18 LOAD_FAST 0 (blocks)
20 GET_ITER
>> 22 FOR_ITER 84 (to 108)
24 STORE_FAST 4 (block)
7 26 LOAD_GLOBAL 1 (string2number)
28 LOAD_FAST 4 (block)
30 CALL_FUNCTION 1
32 STORE_FAST 5 (state)
8 34 LOAD_GLOBAL 2 (range)
36 LOAD_FAST 1 (rounds)
38 LOAD_CONST 3 (1)
40 BINARY_SUBTRACT
42 CALL_FUNCTION 1
44 GET_ITER
>> 46 FOR_ITER 34 (to 82)
48 STORE_FAST 6 (i)
9 50 LOAD_GLOBAL 3 (addRoundKey)
52 LOAD_FAST 5 (state)
54 LOAD_FAST 2 (roundkeys)
56 LOAD_FAST 6 (i)
58 BINARY_SUBSCR
60 CALL_FUNCTION 2
62 STORE_FAST 5 (state)
10 64 LOAD_GLOBAL 4 (sBoxLayer)
66 LOAD_FAST 5 (state)
68 CALL_FUNCTION 1
70 STORE_FAST 5 (state)
11 72 LOAD_GLOBAL 5 (pLayer)
74 LOAD_FAST 5 (state)
76 CALL_FUNCTION 1
78 STORE_FAST 5 (state)
80 JUMP_ABSOLUTE 46
12 >> 82 LOAD_GLOBAL 3 (addRoundKey)
84 LOAD_FAST 5 (state)
86 LOAD_FAST 2 (roundkeys)
88 LOAD_CONST 4 (-1)
90 BINARY_SUBSCR
92 CALL_FUNCTION 2
94 STORE_FAST 7 (cipher)
13 96 LOAD_FAST 3 (out)
98 LOAD_METHOD 6 (append)
100 LOAD_FAST 7 (cipher)
102 CALL_METHOD 1
104 POP_TOP
106 JUMP_ABSOLUTE 22
14 >> 108 LOAD_FAST 3 (out)
110 RETURN_VALUE
14 CALL_METHOD 1
16 STORE_NAME 3 (co)
12 18 LOAD_NAME 4 (exec)
20 LOAD_NAME 3 (co)
22 CALL_FUNCTION 1
24 POP_TOP
26 LOAD_CONST 3 (None)
28 RETURN_VALUE
Disassembly of <code object generateRoundkeys80 at 0x7f133db26a80, file "", line 2>:
3 0 BUILD_LIST 0
2 STORE_FAST 2 (roundkeys)
4 4 LOAD_GLOBAL 0 (range)
6 LOAD_CONST 1 (1)
8 LOAD_FAST 1 (rounds)
10 LOAD_CONST 1 (1)
12 BINARY_ADD
14 LOAD_CONST 1 (1)
16 CALL_FUNCTION 3
18 GET_ITER
>> 20 FOR_ITER 90 (to 112)
22 STORE_FAST 3 (i)
5 24 LOAD_FAST 2 (roundkeys)
26 LOAD_METHOD 1 (append)
28 LOAD_FAST 0 (key)
30 LOAD_CONST 2 (16)
32 BINARY_RSHIFT
34 CALL_METHOD 1
36 POP_TOP
6 38 LOAD_FAST 0 (key)
40 LOAD_CONST 3 (524287)
42 BINARY_AND
44 LOAD_CONST 4 (61)
46 BINARY_LSHIFT
48 LOAD_FAST 0 (key)
50 LOAD_CONST 5 (19)
52 BINARY_RSHIFT
54 BINARY_ADD
56 STORE_FAST 0 (key)
7 58 LOAD_GLOBAL 2 (Sbox)
60 LOAD_FAST 0 (key)
62 LOAD_CONST 6 (76)
64 BINARY_RSHIFT
66 BINARY_SUBSCR
68 LOAD_CONST 6 (76)
70 BINARY_LSHIFT
72 LOAD_FAST 0 (key)
74 LOAD_CONST 7 (2)
76 LOAD_CONST 6 (76)
78 BINARY_POWER
80 LOAD_CONST 1 (1)
82 BINARY_SUBTRACT
84 BINARY_AND
86 BINARY_ADD
88 STORE_FAST 0 (key)
8 90 LOAD_FAST 0 (key)
92 LOAD_FAST 3 (i)
94 LOAD_CONST 8 (15)
96 BINARY_LSHIFT
98 LOAD_FAST 0 (key)
100 LOAD_CONST 5 (19)
102 BINARY_RSHIFT
104 BINARY_XOR
106 INPLACE_XOR
108 STORE_FAST 0 (key)
110 JUMP_ABSOLUTE 20
9 >> 112 LOAD_FAST 2 (roundkeys)
114 RETURN_VALUE
14 CALL_METHOD 1
16 STORE_NAME 3 (co)
6 18 LOAD_NAME 4 (exec)
20 LOAD_NAME 3 (co)
22 CALL_FUNCTION 1
24 POP_TOP
26 LOAD_CONST 3 (None)
28 RETURN_VALUE
Disassembly of <code object string2number at 0x7f7370421a80, file "", line 2>:
3 0 LOAD_GLOBAL 0 (sum)
2 LOAD_CLOSURE 0 (i)
4 BUILD_TUPLE 1
6 LOAD_CONST 1 (<code object <listcomp> at 0x7f73704aba80, file "", line 3>)
8 LOAD_CONST 2 ('string2number.<locals>.<listcomp>')
10 MAKE_FUNCTION 8 (closure)
12 LOAD_GLOBAL 1 (range)
14 LOAD_CONST 3 (8)
16 CALL_FUNCTION 1
18 GET_ITER
20 CALL_FUNCTION 1
22 CALL_FUNCTION 1
24 RETURN_VALUE
Disassembly of <code object <listcomp> at 0x7f73704aba80, file "", line 3>:
3 0 BUILD_LIST 0
2 LOAD_FAST 0 (.0)
>> 4 FOR_ITER 24 (to 30)
6 STORE_FAST 1 (c)
8 LOAD_GLOBAL 0 (ord)
10 LOAD_DEREF 0 (i)
12 LOAD_FAST 1 (c)
14 BINARY_SUBSCR
16 CALL_FUNCTION 1
18 LOAD_CONST 0 (8)
20 LOAD_FAST 1 (c)
22 BINARY_MULTIPLY
24 BINARY_LSHIFT
26 LIST_APPEND 2
28 JUMP_ABSOLUTE 4
>> 30 RETURN_VALUE
14 CALL_METHOD 1
16 STORE_NAME 3 (co)
9 18 LOAD_NAME 4 (exec)
20 LOAD_NAME 3 (co)
22 CALL_FUNCTION 1
24 POP_TOP
26 LOAD_CONST 3 (None)
28 RETURN_VALUE
Disassembly of <code object pLayer at 0x7f023882ba80, file "", line 2>:
3 0 LOAD_CONST 1 (0)
2 STORE_FAST 1 (output)
4 4 LOAD_GLOBAL 0 (range)
6 LOAD_CONST 2 (64)
8 CALL_FUNCTION 1
10 GET_ITER
>> 12 FOR_ITER 28 (to 42)
14 STORE_FAST 2 (i)
5 16 LOAD_FAST 1 (output)
18 LOAD_FAST 0 (state)
20 LOAD_FAST 2 (i)
22 BINARY_RSHIFT
24 LOAD_CONST 3 (1)
26 BINARY_AND
28 LOAD_GLOBAL 1 (PBox)
30 LOAD_FAST 2 (i)
32 BINARY_SUBSCR
34 BINARY_LSHIFT
36 INPLACE_ADD
38 STORE_FAST 1 (output)
40 JUMP_ABSOLUTE 12
6 >> 42 LOAD_FAST 1 (output)
44 RETURN_VALUE
14 CALL_METHOD 1
16 STORE_NAME 3 (co)
9 18 LOAD_NAME 4 (exec)
20 LOAD_NAME 3 (co)
22 CALL_FUNCTION 1
24 POP_TOP
26 LOAD_CONST 3 (None)
28 RETURN_VALUE
Disassembly of <code object sBoxLayer at 0x7fab1d117a80, file "", line 2>:
3 0 LOAD_CONST 1 (0)
2 STORE_FAST 1 (output)
4 4 LOAD_GLOBAL 0 (range)
6 LOAD_CONST 2 (16)
8 CALL_FUNCTION 1
10 GET_ITER
>> 12 FOR_ITER 36 (to 50)
14 STORE_FAST 2 (i)
5 16 LOAD_FAST 1 (output)
18 LOAD_GLOBAL 1 (Sbox)
20 LOAD_FAST 0 (state)
22 LOAD_FAST 2 (i)
24 LOAD_CONST 3 (4)
26 BINARY_MULTIPLY
28 BINARY_RSHIFT
30 LOAD_CONST 4 (15)
32 BINARY_AND
34 BINARY_SUBSCR
36 LOAD_FAST 2 (i)
38 LOAD_CONST 3 (4)
40 BINARY_MULTIPLY
42 BINARY_LSHIFT
44 INPLACE_ADD
46 STORE_FAST 1 (output)
48 JUMP_ABSOLUTE 12
6 >> 50 LOAD_FAST 1 (output)
52 RETURN_VALUE
14 CALL_METHOD 1
16 STORE_NAME 3 (co)
6 18 LOAD_NAME 4 (exec)
20 LOAD_NAME 3 (co)
22 CALL_FUNCTION 1
24 POP_TOP
26 LOAD_CONST 3 (None)
28 RETURN_VALUE
Disassembly of <code object addRoundKey at 0x7f5223878a80, file "", line 2>:
3 0 LOAD_FAST 0 (state)
2 LOAD_FAST 1 (roundkey)
4 BINARY_XOR
6 RETURN_VALUE
210 CALL_METHOD 1
212 STORE_NAME 7 (co)
12 214 LOAD_NAME 8 (exec)
216 LOAD_NAME 7 (co)
218 CALL_FUNCTION 1
220 POP_TOP
222 LOAD_CONST 69 (None)
224 RETURN_VALUE
Disassembly of <code object <listcomp> at 0x7f7b29b00a80, file "", line 4>:
4 0 BUILD_LIST 0
2 LOAD_FAST 0 (.0)
>> 4 FOR_ITER 14 (to 20)
6 STORE_FAST 1 (x)
8 LOAD_GLOBAL 0 (Sbox)
10 LOAD_METHOD 1 (index)
12 LOAD_FAST 1 (x)
14 CALL_METHOD 1
16 LIST_APPEND 2
18 JUMP_ABSOLUTE 4
>> 20 RETURN_VALUE
Disassembly of <code object <listcomp> at 0x7f7b29a76a80, file "", line 9>:
9 0 BUILD_LIST 0
2 LOAD_FAST 0 (.0)
>> 4 FOR_ITER 14 (to 20)
6 STORE_FAST 1 (x)
8 LOAD_GLOBAL 0 (PBox)
10 LOAD_METHOD 1 (index)
12 LOAD_FAST 1 (x)
14 CALL_METHOD 1
16 LIST_APPEND 2
18 JUMP_ABSOLUTE 4
>> 20 RETURN_VALUE


 浙公网安备 33010602011771号
浙公网安备 33010602011771号