GXYCTF2019 simple CPP
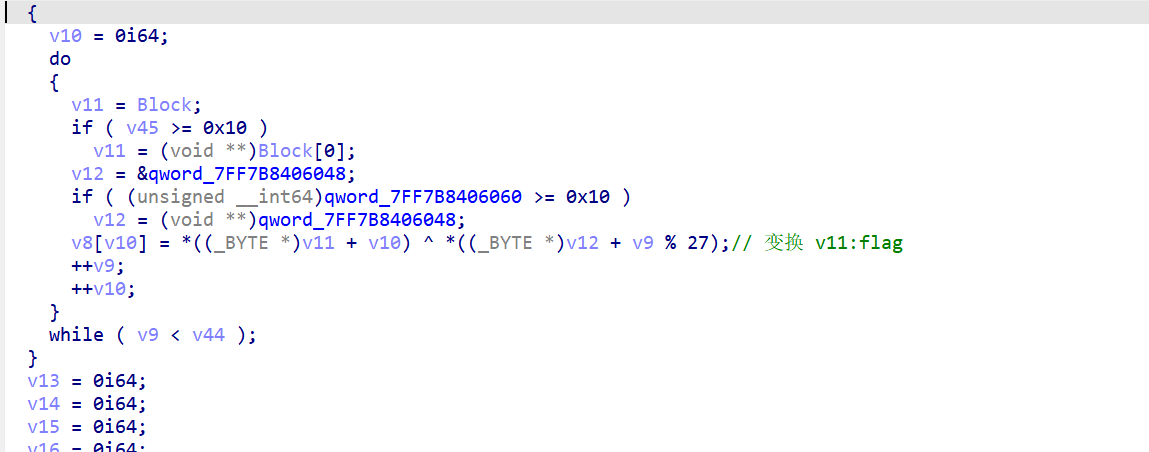
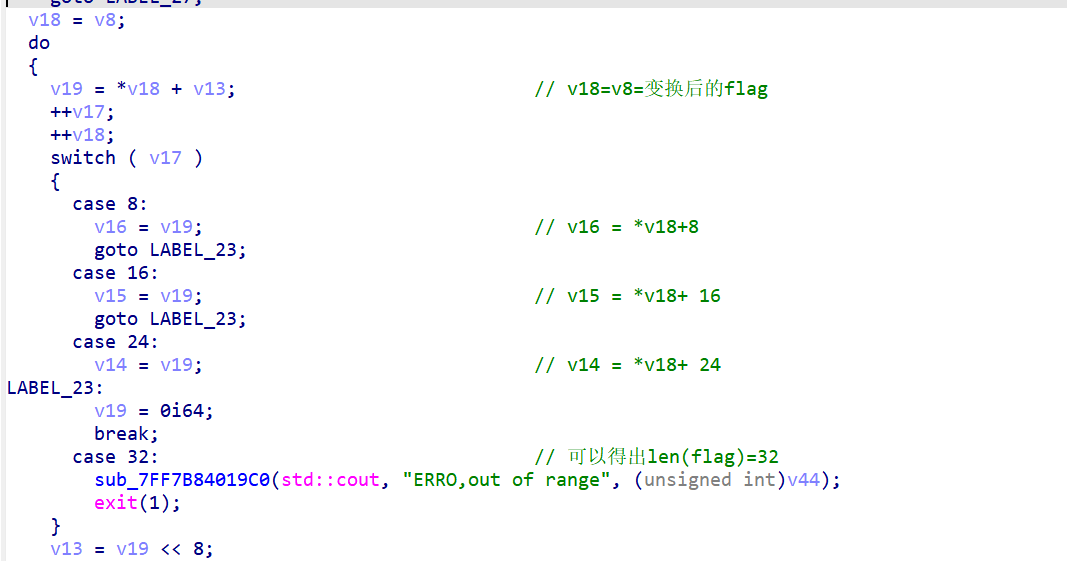
开始对输入进行了xor操作 key要动调才能拿到
然后对32个分成了4个__int64
后面进行了一堆check 看着很复杂 这种都要动笔写一写
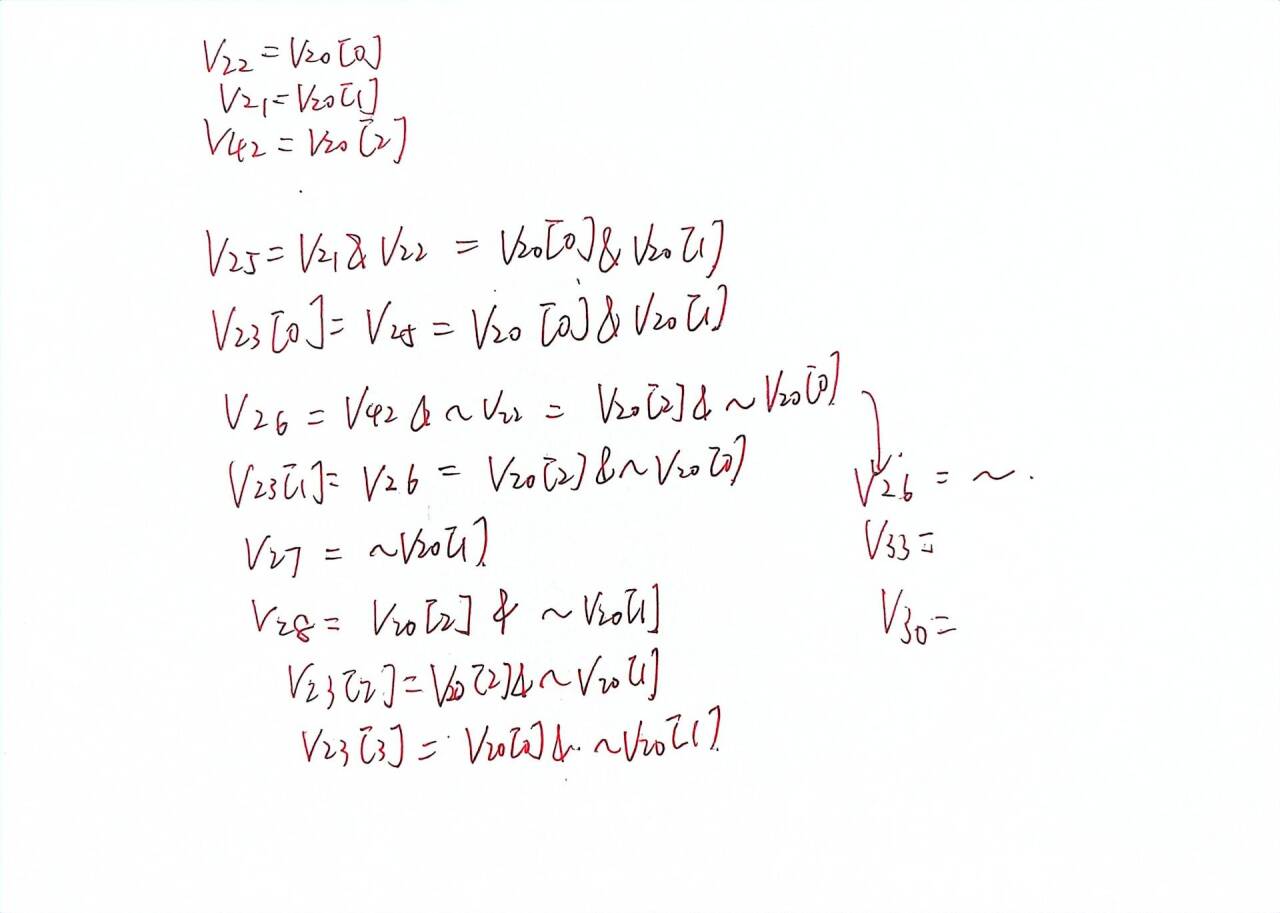
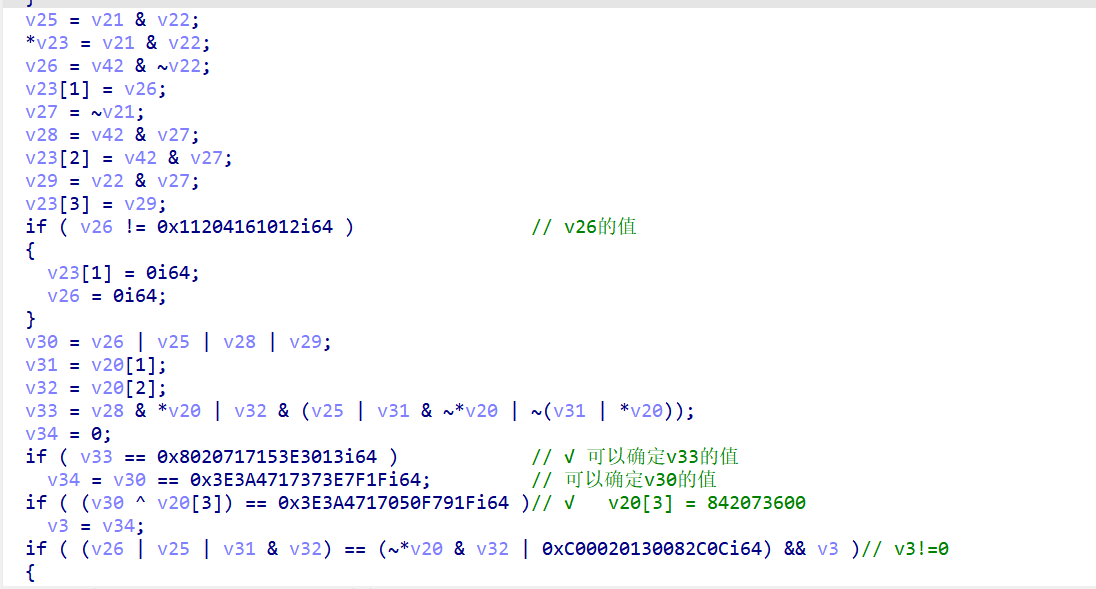
开始就是没动笔写 关系看不明白 还有最关键的一个点
刚开始眼瞎 直接v23[3]=0了...
z3解一解(注意先check才有model)
from z3 import *
from libnum import *
v0,v1,v2 = BitVecs('v0 v1 v2',64)
s = Solver()
s.add(v2&~v0==0x11204161012)
s.add(((v2&~v1) & v0 | v2 & ((v0&v1) | v1 & ~v0 | ~(v1 | v0)))==0x8020717153E3013)
s.add((0x11204161012 | (v0&v1) | (v2&~v1) | (v0&~v1))==0x3E3A4717373E7F1F)
s.add(((v2&~v0) | (v0&v1) | v1 & v2) == (~v0 & v2 | 0xC00020130082C0C))
print(s.check())
print(s.model())
v0 = 4483973367147818765
v1 = 864693332579200012
v2 = 577031497978884115
v3 = 842073600
print(hex(v0),hex(v1),hex(v2),hex(v3))
然后对应32个char xor一下 中间乱码是因为题目当时给了Hint所以无妨
v12 = [0x69, 0x5F, 0x77, 0x69, 0x6C, 0x6C, 0x5F, 0x63, 0x68, 0x65, 0x63, 0x6B, 0x5F, 0x69, 0x73, 0x5F, 0x64, 0x65, 0x62, 0x75, 0x67, 0x5F, 0x6F, 0x72, 0x5F, 0x6E, 0x6F, 0x74]
enc = [0x3e,0x3a,0x46,0x05,0x33,0x28,0x6f,0x0d,0xc0,0x00,0x02,0x01,0x30,0x08,0x2c,0x0c,0x08,
0x02,0x07,0x17,0x15,0x3e,0x30,0x13,0x32,0x31,0x06]
for i in range(len(enc)):
print(chr(enc[i]^v12[i]),end='')

