NewStarCTF2022 E4sy_Mix
main这里有个SMC自修改
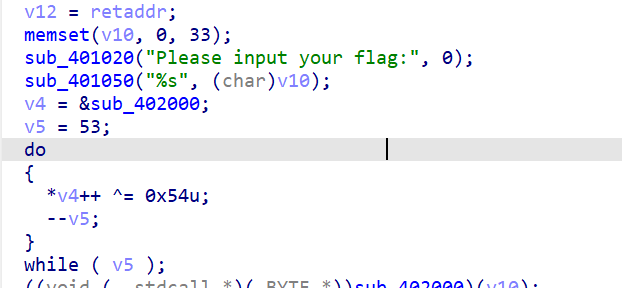
idc脚本patch后
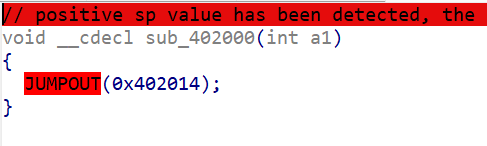
点击跳转
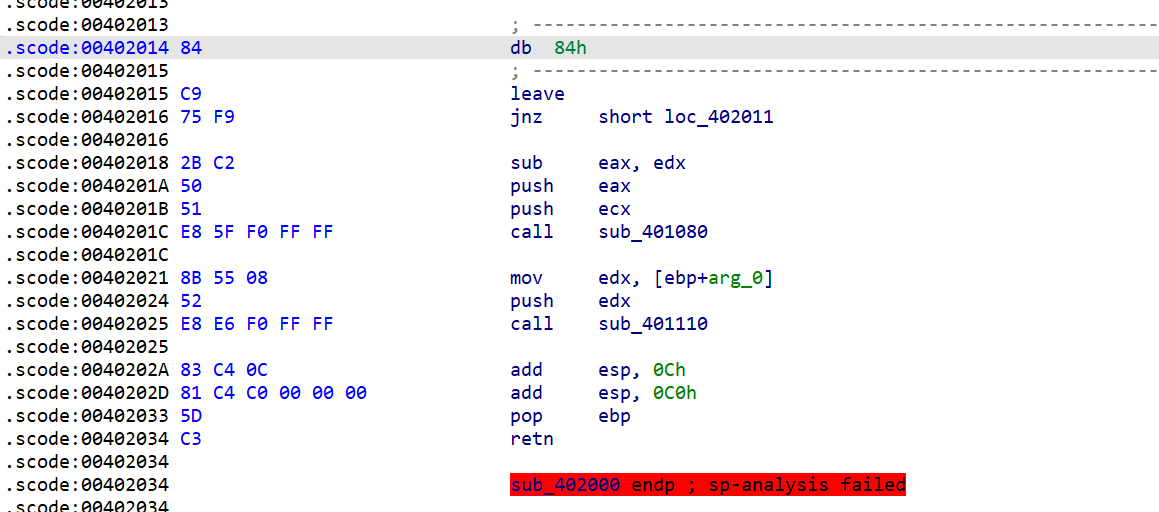
这里虽然不能F5 但是可以看出先后调用了两个函数
点击查看两个函数
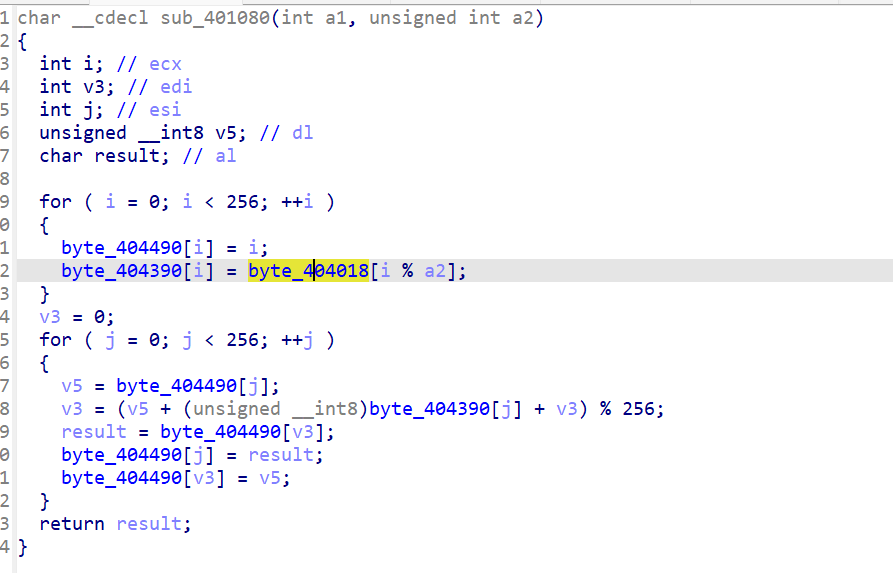
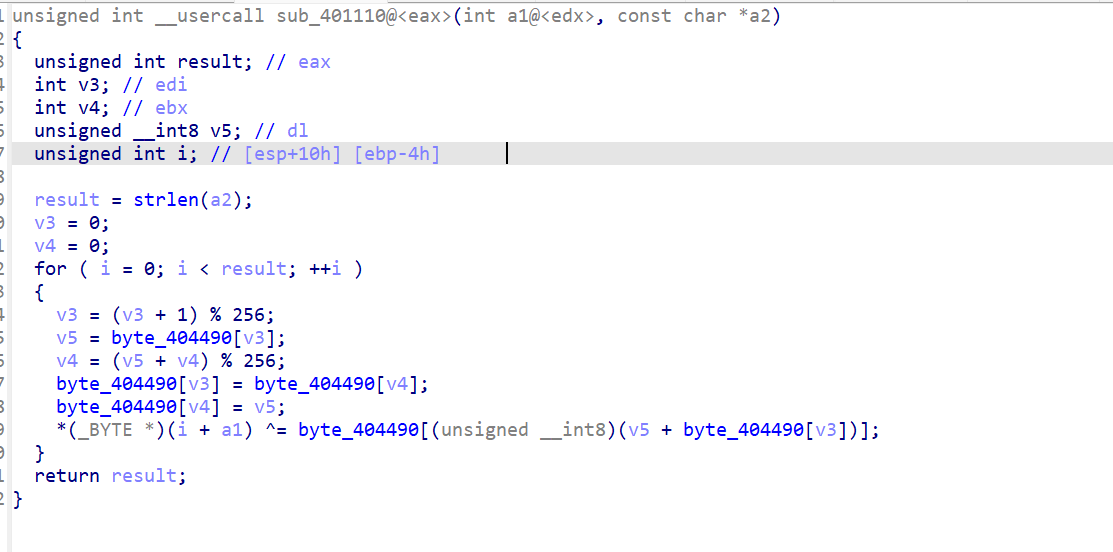
RC4加密
找到对应key
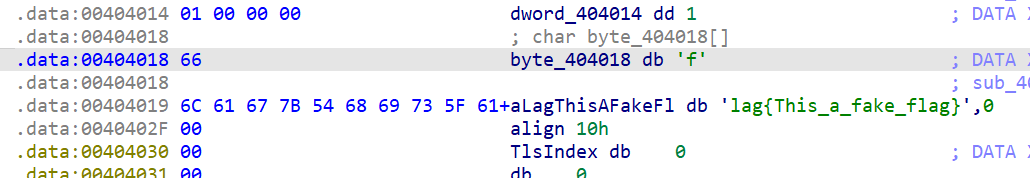
且已知最后enc的结果
从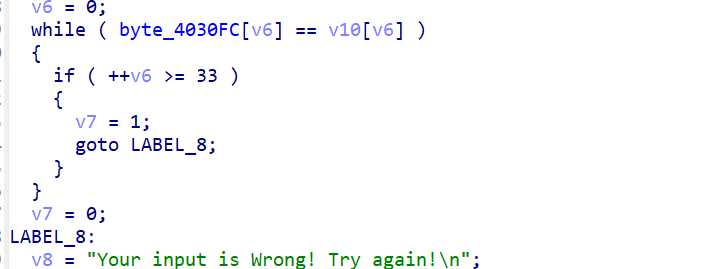
可以推出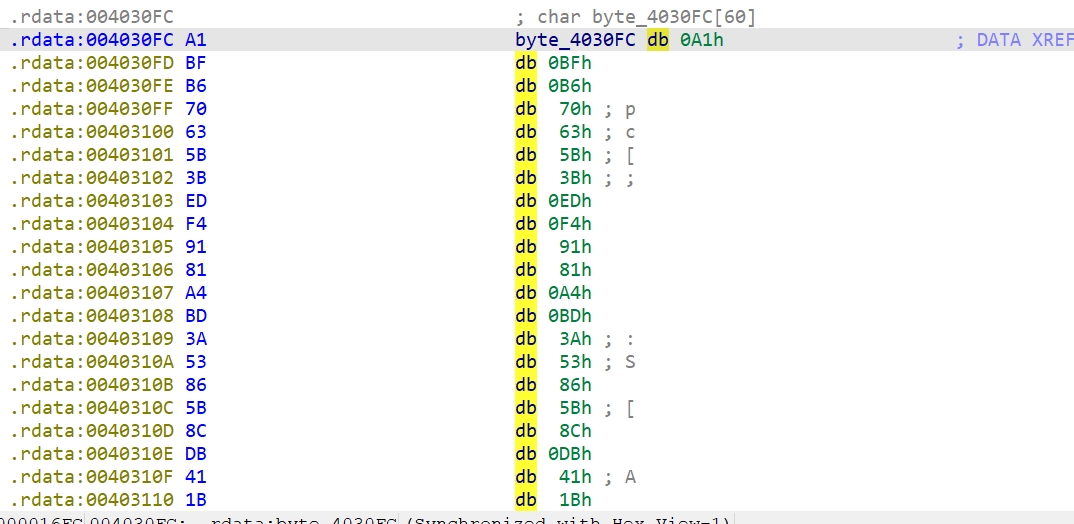
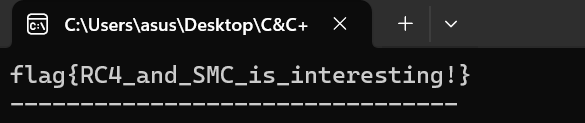
RC4逆向decrypt即可
solution.c
/*
unsigned char byte_4030FC[33] = {
0xA1, 0xBF, 0xB6, 0x70, 0x63, 0x5B, 0x3B, 0xED, 0xF4, 0x91, 0x81, 0xA4, 0xBD, 0x3A, 0x53, 0x86,
0x5B, 0x8C, 0xDB, 0x41, 0x1B, 0x73, 0xE1, 0xD1, 0xF2, 0xB2, 0xDF, 0x6E, 0x16, 0x56, 0x22, 0x42,
0xFC
};
*/
//RC4
#include<bits/stdc++.h>
using namespace std;
signed main(){
int base64_table[] ={
0xA1, 0xBF, 0xB6, 0x70, 0x63, 0x5B, 0x3B, 0xED, 0xF4, 0x91, 0x81, 0xA4, 0xBD, 0x3A, 0x53, 0x86,
0x5B, 0x8C, 0xDB, 0x41, 0x1B, 0x73, 0xE1, 0xD1, 0xF2, 0xB2, 0xDF, 0x6E, 0x16, 0x56, 0x22, 0x42,
0xFC};
string key = "flag{This_a_fake_flag}";
int s[256],k[256];
int j=0;
for (int i = 0; i < 256; i++) {
s[i] = i;
k[i] = key[i % key.length()];
}
for (int i2 = 0; i2 < 256; i2++) {
j = (s[i2] + j + k[i2]) & 255;
int temp = s[i2];
s[i2] = s[j];
s[j] = temp;
}
int j2 = 0;
int i3 = 0;
for (int i4 : base64_table) {
i3 = (i3 + 1) & 255;
j2 = (s[i3] + j2) & 255;
int temp2 = s[i3];
s[i3] = s[j2];
s[j2] = temp2;
int rnd = s[(s[i3] + s[j2]) & 255];
cout<<((char) (i4 ^ rnd));
}
}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号