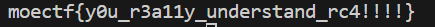
MoeCTF2023 RRRRRc4
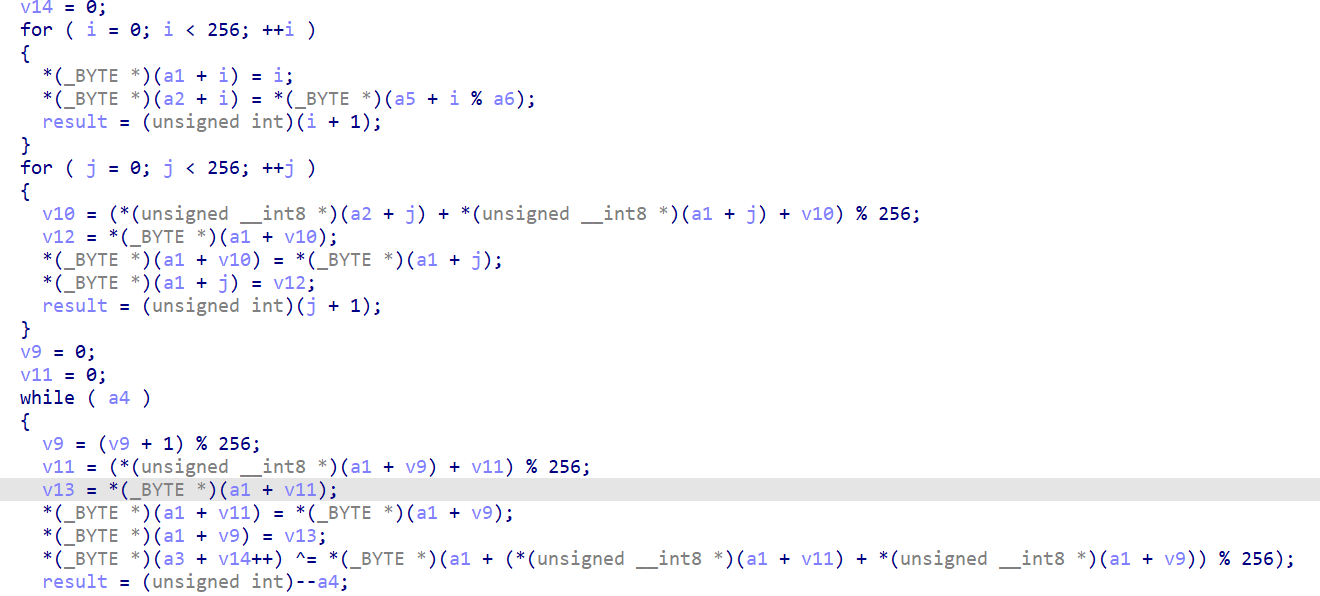
关键加密代码
由于只有最后一个循环的最后一步涉及到a3(也就是flag)的变换 所以直接逆即可
exp:
byte_6000 = [0x1B, 0x9B, 0xFB, 0x19, 0x06, 0x6A, 0xB5, 0x3B, 0x7C, 0xBA, 0x03, 0xF3, 0x91, 0xB8, 0xB6, 0x3D, 0x8A, 0xC1, 0x48, 0x2E, 0x50, 0x11, 0xE7, 0xC7, 0x4F, 0xB1, 0x27, 0xCF, 0xF3, 0xAE, 0x03, 0x09, 0xB2, 0x08, 0xFB, 0xDC, 0x22, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00]
a5 = "moectf2023"
a6 = 10
a1 = []
a2 = []
for i in range(256):
a1.append(i)
a2.append(ord(a5[i%a6]))
v10 = 0
v14 = 0
for j in range(256):
v10 = (a2[j]+a1[j]+v10)%256
v12 = a1[v10]
a1[v10] = a1[j]
a1[j] = v12
v9 = 0
v11 = 0
a4 = 38
flag = ""
while(a4>0):
v9 = (v9+1)%256
v11 = (a1[v9]+v11)%256
v13 = a1[v11]
a1[v11] = a1[v9]
a1[v9] = v13
n = byte_6000[v14]^(a1[(a1[v11]+a1[v9])%256])
flag += chr(n)
v14 += 1
a4 -= 1
print(flag)