NewStarCTF2023 AndroGenshin
卧槽 打开真原神...
直接jadx打开
找到关键代码
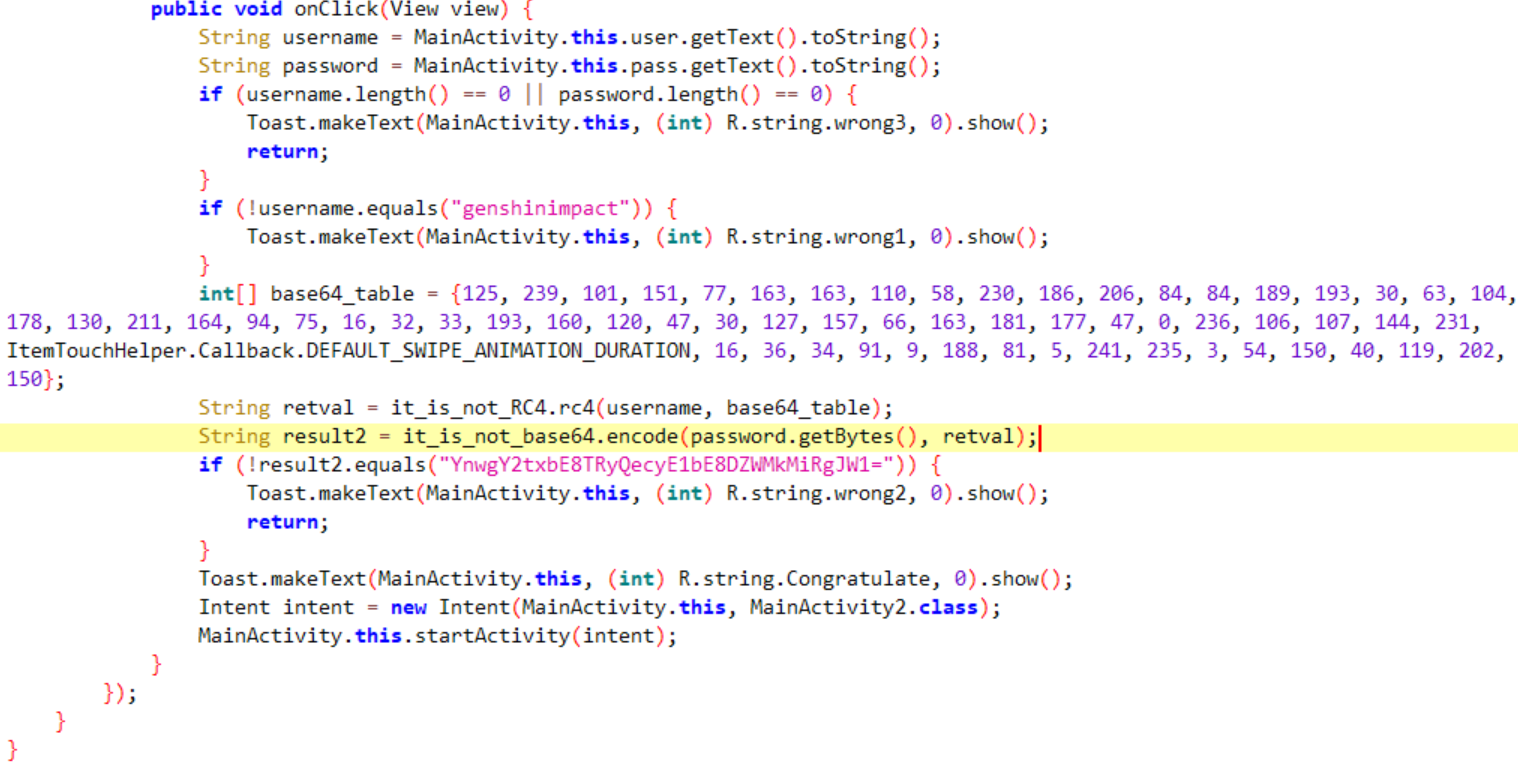
一个RC4 一个base64
先看base64
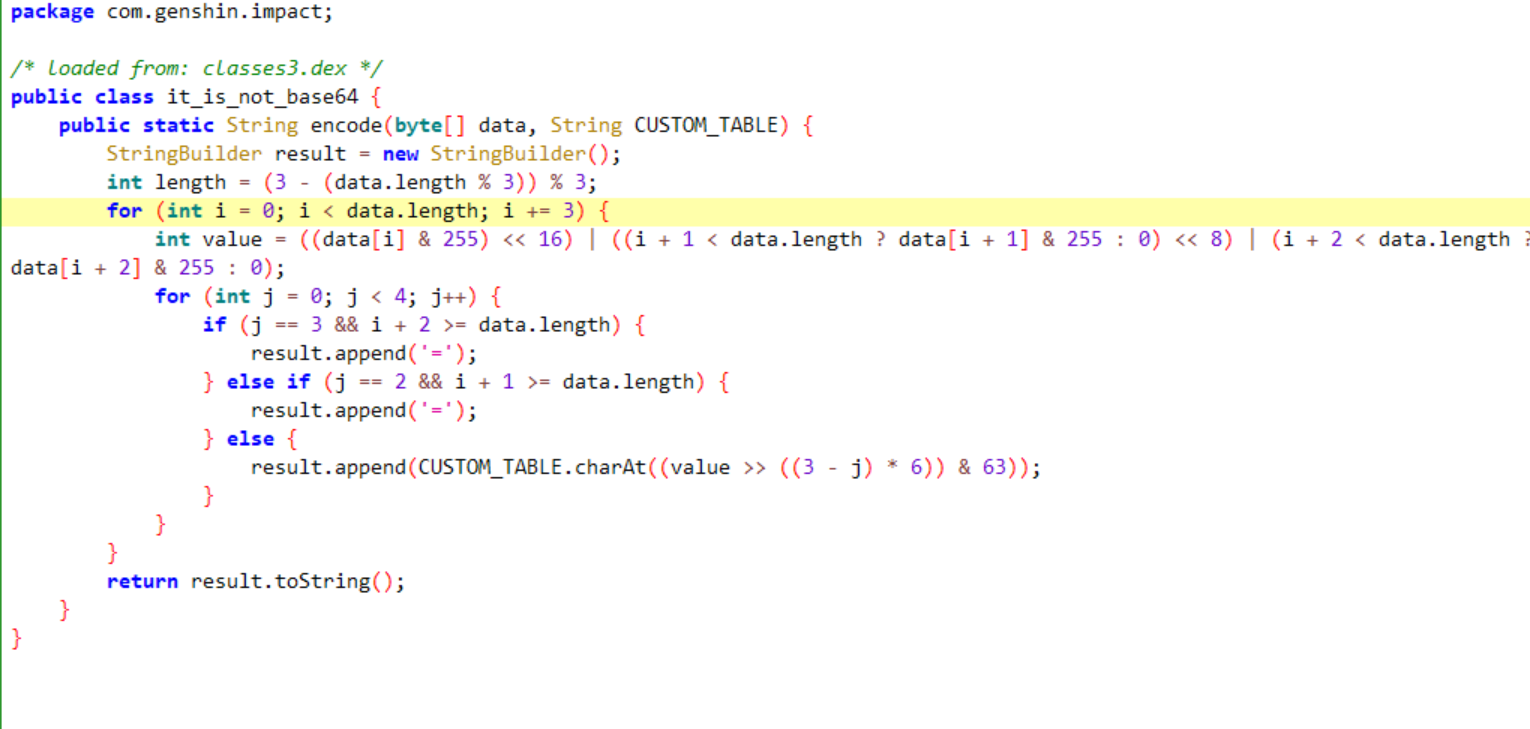
没有对base64进行除了table表以外算法的变化
再看RC4
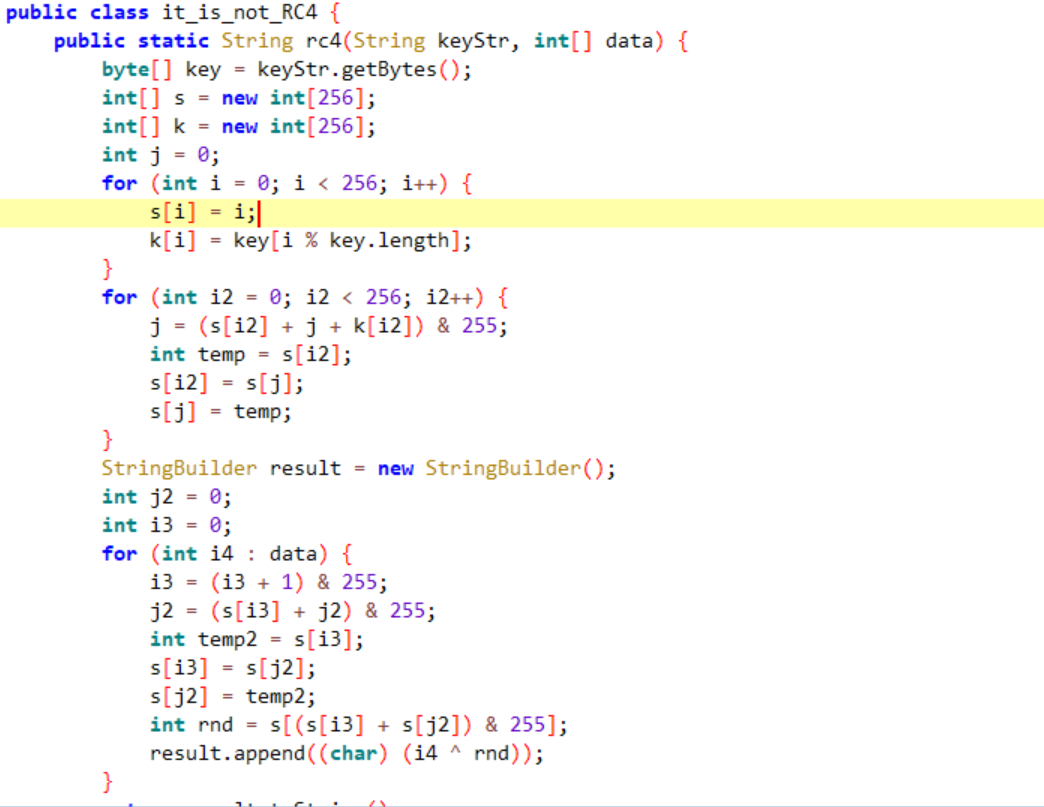
这里直接模拟它对table的变化 得到变化后的table表
再利用变种base64脚本解密即可
exp: 得到table
#include<bits/stdc++.h>
using namespace std;
signed main(){
int base64_table[] = {125, 239, 101, 151, 77, 163, 163, 110, 58, 230, 186, 206, 84, 84, 189, 193, 30, 63, 104, 178, 130, 211, 164, 94, 75, 16, 32, 33, 193, 160, 120, 47, 30, 127, 157, 66, 163, 181, 177, 47, 0, 236, 106, 107, 144, 231, 111, 16, 36, 34, 91, 9, 188, 81, 5, 241, 235, 3, 54, 150, 40, 119, 202, 150};
string key = "genshinimpact";
int s[256],k[256];
int j=0;
for (int i = 0; i < 256; i++) {
s[i] = i;
k[i] = key[i % key.length()];
}
for (int i2 = 0; i2 < 256; i2++) {
j = (s[i2] + j + k[i2]) & 255;
int temp = s[i2];
s[i2] = s[j];
s[j] = temp;
}
int j2 = 0;
int i3 = 0;
for (int i4 : base64_table) {
i3 = (i3 + 1) & 255;
j2 = (s[i3] + j2) & 255;
int temp2 = s[i3];
s[i3] = s[j2];
s[j2] = temp2;
int rnd = s[(s[i3] + s[j2]) & 255];
cout<<((char) (i4 ^ rnd));
}
}
变形base64:
# base64_table = [125, 239, 101, 151, 77, 163, 163, 110, 58, 230, 186, 206, 84, 84, 189, 193, 30, 63, 104, 178, 130, 211, 164, 94, 75, 16, 32, 33, 193, 160, 120, 47, 30, 127, 157, 66, 163, 181, 177, 47, 0, 236, 106, 107, 144, 231, 16, 36, 34, 91, 9, 188, 81, 5, 241, 235, 3, 54, 150, 40, 119, 202, 150]
# changed = "BADCFEHGJILKNMPORQTSVUXWZYbadcfehgjilknmporqtsvuxwzy1032547698/+"
import base64
cipher = 'YnwgY2txbE8TRyQecyE1bE8DZWMkMiRgJW1='
ori = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
changed = 'BADCFEHGJILKNMPORQTSVUXWZYbadcfehgjilknmporqtsvuxwzy1032547698/+'
print(base64.b64decode(cipher.translate(str.maketrans(changed,ori))))
最后用 genshinimpact作为用户名 flag{0h_RC4_w1th_Base64!!}作为密码登陆还有彩蛋



