BUUCTF [NCTF2019]Sore
很有意思的一道题
题目源码:
from string import ascii_letters
from flag import flag
ctoi = lambda x: ascii_letters.index(x)
itoc = lambda x: ascii_letters[x]
key = flag.strip('NCTF{}')
len_key = len(key)
plaintext = open('plaintext.txt', 'r').read()
plain = ''.join(p for p in plaintext if p in ascii_letters)
cipher = ''.join( itoc( ( ctoi(p) + ctoi( key[i % len_key] ) ) % 52 ) \
for i,p in enumerate(plain) )
open('ciphertext.txt', 'w').write(cipher)
我们得到的只有ciphertext的信息 然而想要获得作为key的flag肯定是需要plaintext
这里可以采用 词频分析 其实也就是类似维吉尼亚加密的方法
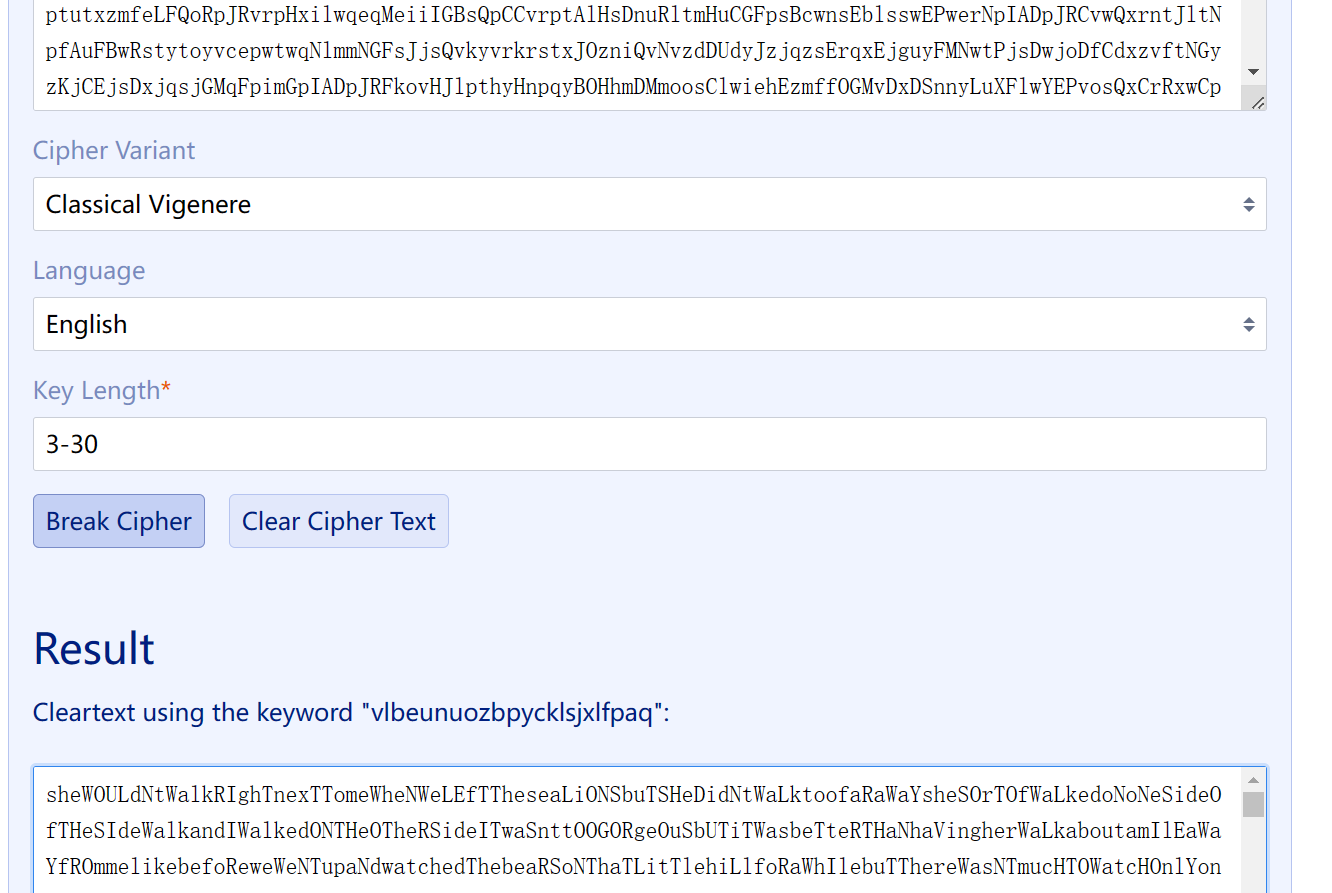
这里还顺带给了我们key
只是要注意 这里大小写是不符合实际的
应该改为
Shewouldntwalkrightnext
所以重新计算key:
from string import ascii_letters
ctoi = lambda x: ascii_letters.index(x)
itoc = lambda x: ascii_letters[x]
with open(r'\ciphertext.txt','r+') as f:
cipher = f.read()
with open(r'\plaintext.txt','r+') as f:
plaintext = f.read()
plaintext = "Shewouldntwalkrightnext"
cipher = "nsfAIHFrMuLynuCApeEstxJ"
plain = ''.join(p for p in plaintext if p in ascii_letters)
flag = ""
for i in range(len(cipher)):
c = cipher[i]
p = plaintext[i]
for key in ascii_letters:
cc = itoc( ( ctoi(p) + ctoi(key) ) % 52 )
if(cc == c):
flag += key
break
print(flag)
# VlbEUNUoZbPyckLSjXLfpaQ
最终flag:vlbeunuozbpycklsjXlfpaq

