BUUCTF-RE-[SUCTF2019]SignIn
分析
__int64 __fastcall main(__int64 a1, char **a2, char **a3)
{
char v4; // [rsp+0h] [rbp-4A0h]
char v5; // [rsp+10h] [rbp-490h]
char v6; // [rsp+20h] [rbp-480h]
char v7; // [rsp+30h] [rbp-470h]
char v8; // [rsp+40h] [rbp-460h]
char v9; // [rsp+B0h] [rbp-3F0h]
unsigned __int64 v10; // [rsp+498h] [rbp-8h]
v10 = __readfsqword(0x28u);
puts("[sign in]");
printf("[input your flag]: ", a2);
__isoc99_scanf((__int64)"%99s", (__int64)&v8);
sub_96A(&v8, (__int64)&v9);
__gmpz_init_set_str((__int64)&v7, (__int64)"ad939ff59f6e70bcbfad406f2494993757eee98b91bc244184a377520d06fc35", 16LL);
__gmpz_init_set_str((__int64)&v6, (__int64)&v9, 16LL);
__gmpz_init_set_str(
(__int64)&v4,
(__int64)"103461035900816914121390101299049044413950405173712170434161686539878160984549",
10LL);
__gmpz_init_set_str((__int64)&v5, (__int64)"65537", 10LL);
__gmpz_powm(&v6, &v6, &v5, &v4);//rop = base^exp取余mod v6=v6^v5 mod v4
if ( (unsigned int)__gmpz_cmp((__int64)&v6, (__int64)&v7) ) //这里是v6和v7对比
puts("GG!");
else
puts("TTTTTTTTTTql!");
return 0LL;
}
没有更多信息了。iui
这里程序用了 __gmpz_init_set_str 函数,查一查知道这是一个 GNU 高精度算法库官方文档
程序中有用到的两个:
int mpz_init_set_str (mpz_t rop, const char *str, int base) [Function]
Initialize rop and set its value like mpz_set_str
mpz_t rop:多精度整数变量
char *str: 字符串
int base: 进制
将str按照base进制转换为rop
void mpz_powm (mpz_t rop, const mpz_t base, const mpz_t exp, const mpz_t mod) [Function]
Set rop to base^exp mod mod.
rop = base^exp取余mod
看到这个 过程rop = base^exp取余mod 就很容易联想到RSA RSA相关知识补充
对应的就是c=m^e(mod n) v6=v6^v5 mod v4
v7=c=ad939ff59f6e70bcbfad406f2494993757eee98b91bc244184a377520d06fc35
v4=n=103461035900816914121390101299049044413950405173712170434161686539878160984549
v5=e=65537
有n先求p、q
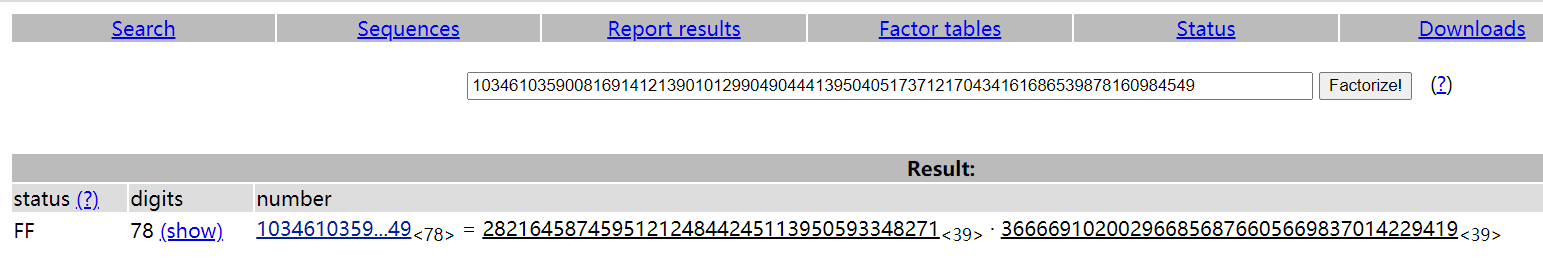
工具
p:282164587459512124844245113950593348271
q:366669102002966856876605669837014229419
e:65537
n:103461035900816914121390101299049044413950405173712170434161686539878160984549
这样子就齐活了能求了=v=
解题脚本
import gmpy2
import binascii
n = int("103461035900816914121390101299049044413950405173712170434161686539878160984549")
# p 和 q通过在线网站http://factordb.com/index.php分解
p = gmpy2.mpz(282164587459512124844245113950593348271)
q = gmpy2.mpz(366669102002966856876605669837014229419)
e = gmpy2.mpz(65537)
phi_n = (p-1)*(q-1)
d = gmpy2.invert(e, phi_n)
c = gmpy2.mpz(0xad939ff59f6e70bcbfad406f2494993757eee98b91bc244184a377520d06fc35)
m = gmpy2.powmod(c, d, n)
print("十进制:\n%s"%m)
m_hex = hex(m)[2:]
print("十六进制:\n%s"%(m_hex,))
print("ascii:\n%s"%(binascii.a2b_hex(m_hex).decode(encoding="utf8")))
suctf


