re | [RCTF2019]asm
re | [RCTF2019]asm
简单file一下:
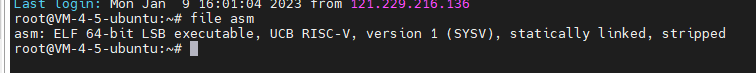
推测是risc-v64位,去网上找逆向脚本:
这个反汇编器是可以用的:
https://github.com/riscv/riscv-gnu-toolchain
或者用下面这个idaproc可以打开,但是效果不太好。
https://github.com/bingseclab/ida_riscv
总之就是装第一个工具然后objdump能够查看反汇编(这里参考了官方wp),exp如下:
data = [0x11,0x76,0xd0,0x1e,0x99,0xb6,0x2c,0x91,0x12,0x45,0xfb,0x2a,0x97,0xc6,0x63,0xb8,0x14,0x7c,0xe1,0x1e,0x83,0xe6,0x45,0xa0,0x19,0x63,0xdd,0x32,0xa4,0xdf,0x71,0x00]
print(len(data))
flag = ""
a = ord('R')
data_len = len(data)
for i in range(data_len):
flag += chr(a)
a = a ^ data[i] ^ ((i * 97) % 256)
print(flag)
本文来自博客园,作者:Mz1,转载请注明原文链接:https://www.cnblogs.com/Mz1-rc/p/17037465.html
如果有问题可以在下方评论或者email:mzi_mzi@163.com






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构
2021-01-09 re | [watevrCTF 2019]Repyc
2021-01-09 web | [Windows][BJDCTF 2nd]EasyAspDotNet