re | [SUCTF2018]HelloPython
re | [SUCTF2018]HelloPython
pyc逆向,解出来一坨翔:
出题人所说应该是使用onelinerizer进行加密的。
(lambda __operator, __print, __g, __contextlib, __y: [ (lambda __mod: [ [ [ (lambda __items, __after, __sentinel: __y(lambda __this: lambda : (lambda __i: [ (lambda __out: (lambda __ctx: [__ctx.__enter__(), __ctx.__exit__(None, None, None), __out[0](lambda : __this())][2])(__contextlib.nested(type('except', (), {'__enter__': lambda self: None, '__exit__': lambda __self, __exctype, __value, __traceback: __exctype is not None and [ True for __out[0] in [(sys.exit(0), lambda after: after())[1]] ][0]})(), type('try', (), {'__enter__': lambda self: None, '__exit__': lambda __self, __exctype, __value, __traceback: [ False for __out[0] in [(v.append(int(word, 16)), lambda __after: __after())[1]] ][0]})())))([None]) for __g['word'] in [__i] ][0] if __i is not __sentinel else __after())(next(__items, __sentinel)))())(iter(p_text.split('_')), lambda : [ [ [ [ [ [ [ (lambda __after: __y(lambda __this: lambda : (lambda __target: [ (lambda __target: [ (lambda __target: [ [ __this() for __g['n'] in [__operator.isub(__g['n'], 1)] ][0] for __target.value in [__operator.iadd(__target.value, (y.value << 4) + k[2] ^ y.value + x.value ^ (y.value >> 5) + k[3])] ][0])(z) for __target.value in [__operator.iadd(__target.value, (z.value << 4) + k[0] ^ z.value + x.value ^ (z.value >> 5) + k[1])] ][0])(y) for __target.value in [__operator.iadd(__target.value, u)] ][0])(x) if n > 0 else __after())())(lambda : [ [ (__print(('').join(map(hex, w)).replace('0x', '').replace('L', '')), None)[1] for w[1] in [z.value] ][0] for w[0] in [y.value] ][0]) for __g['w'] in [[0, 0]] ][0] for __g['n'] in [32] ][0] for __g['u'] in [2654435769] ][0] for __g['x'] in [c_uint32(0)] ][0] for __g['z'] in [c_uint32(v[1])] ][0] for __g['y'] in [c_uint32(v[0])] ][0] for __g['k'] in [[3735928559, 590558003, 19088743, 4275878552]] ][0], [])
for __g['v'] in [[]] ][0]
for __g['p_text'] in [raw_input('plain text:\n> ')] ][0]
for __g['c_uint32'] in [__mod.c_uint32] ][0])(__import__('ctypes', __g, __g, ('c_uint32', ), 0))
for __g['sys'] in [__import__('sys', __g, __g)] ][0])(__import__('operator', level=0), __import__('__builtin__', level=0).__dict__['print'], globals(), __import__('contextlib', level=0), lambda f: (lambda x: x(x))(lambda y: f(lambda : y(y)())))
环境是python2.7
尝试整理失败,直接抓关键数字和位运算特征,一眼tea:
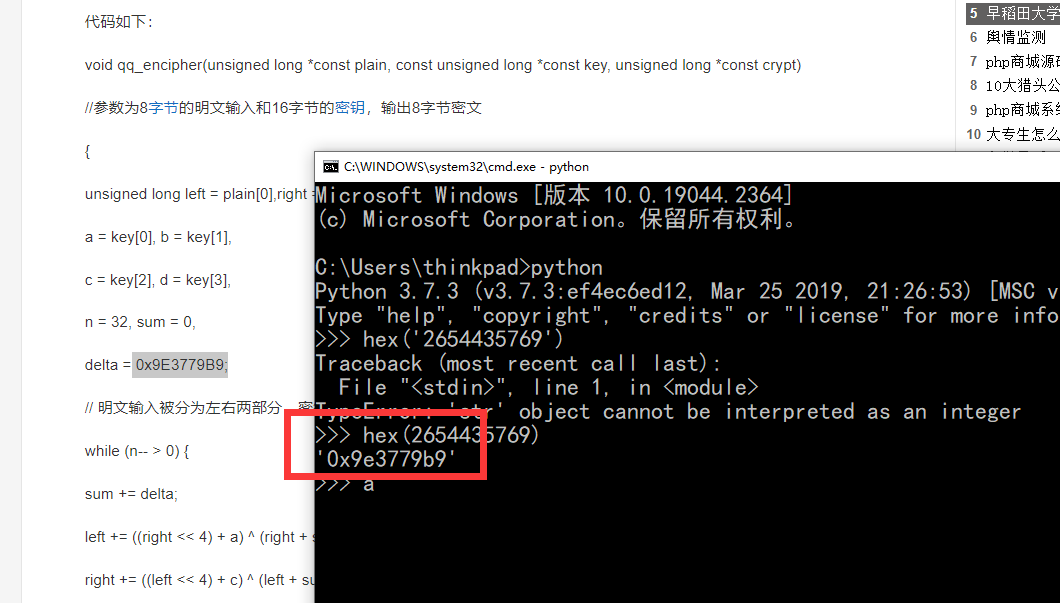
那很明显剩下的4个就是key,因为变量名是k,那我们的输入应该就是v。
密文呢?
去翻了一下才发现:
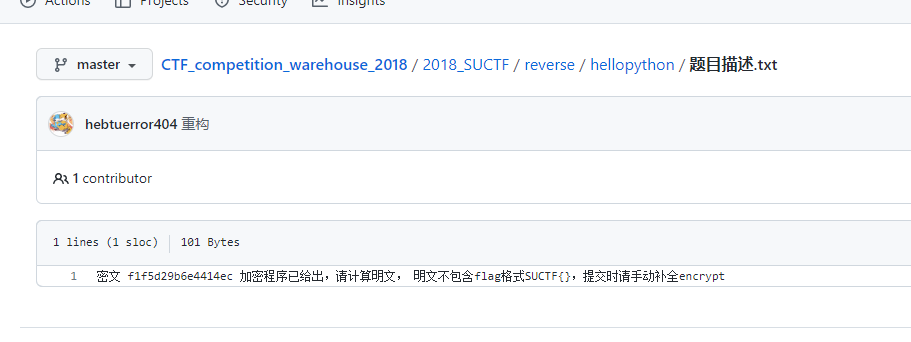
反正就是解密,程序中间还能看出来加了下划线,最后结果中间加个下划线就好了:
#include <iostream>
/* run this program using the console pauser or add your own getch, system("pause") or input loop */
void decry_tea(unsigned int* text, unsigned int* key){
unsigned int delta = 0x9e3779b9; // -delta
unsigned int sum = 0xC6EF3720; // v16
unsigned int v1 = text[1];
unsigned int v0 = text[0];
for (int i = 0; i < 32; i ++){
v1-=((v0<<4)+key[2])^(v0+sum)^((v0>>5)+key[3]);
v0-=((v1<<4)+key[0])^(v1+sum)^((v1>>5)+key[1]);
sum -= delta;
//printf("%d\n",sum);
}
text[1] = v1;
text[0] = v0;
}
void encrypt(unsigned int* v,unsigned int* k){
unsigned int v0=v[0],v1=v[1],sum=0,i;
unsigned int delta=0x9e3779b9;
unsigned int k0=k[0],k1=k[1],k2=k[2],k3=k[3];
for(i = 0; i < 32; i++){
sum += delta;
v0 += ((v1<<4)+k0)^(v1+sum)^((v1>>5)+k1);
v1 += ((v0<<4)+k2)^(v0+sum)^((v0>>5)+k3);
}
v[0]=v0;
v[1]=v1;
}
int main(int argc, char** argv) {
unsigned int key[] = {3735928559u, 590558003u, 19088743u, 4275878552u};
unsigned int text1[] = {0xf1f5d29b ,0x6e4414ec};
//unsigned int* text1 = (unsigned int*)a;
decry_tea(text1, key);
//encrypt(text0, key);
printf("%x %x", text1[0], text1[1]);
printf("\n\n");
for (int i = 0 ; i < 8; i ++){
printf("%c", *((char*)text1 + i));
}
return 0;
}
本文来自博客园,作者:Mz1,转载请注明原文链接:https://www.cnblogs.com/Mz1-rc/p/17037068.html
如果有问题可以在下方评论或者email:mzi_mzi@163.com





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律
2021-01-09 re | [watevrCTF 2019]Repyc
2021-01-09 web | [Windows][BJDCTF 2nd]EasyAspDotNet