re | [GKCTF2020]WannaReverse
四个文件:
勒索的程序
被加密的flag
dll
启动器
勒索的程序主要流程就是这样:
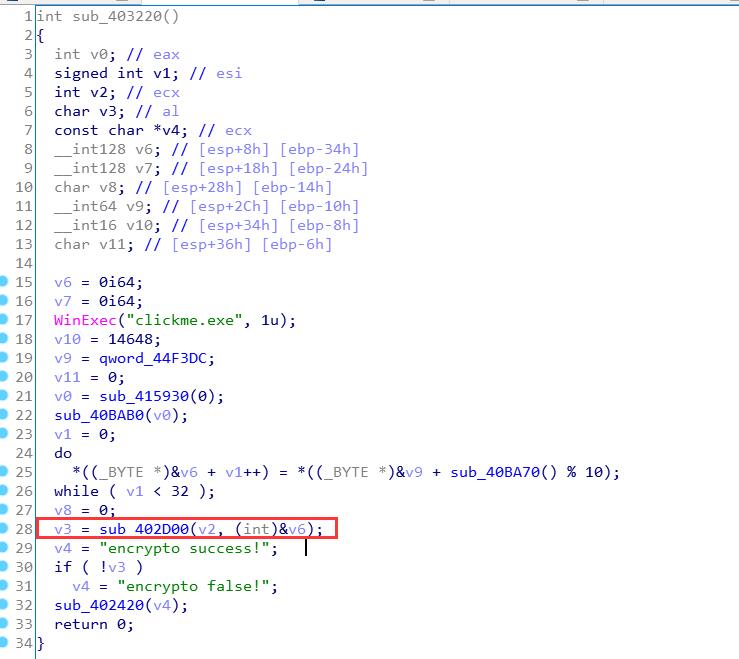
框出来的是具体的加密操作
程序给出了RSA的私钥,直接使用工具对密文进行解密,得到AES的密钥,然后解密在最后的密文就可以得到flag。
具体参考文章:https://bbs.pediy.com/thread-260358-1.htm
但是那个里面的代码会报错,我改的脚本如下:
1 from Crypto.Cipher import AES 2 from hashlib import md5 3 ciper =[0x5C, 0xBC, 0xEA, 4 0x89, 0xBA, 0x2B, 0x18, 0x27, 0x79, 0x3F, 0x13, 0x0A, 0x8A, 5 0x97, 0xB4, 0x9B, 0xCD, 0x78, 0x9B, 0xD8, 0x35, 0x92, 0x05, 6 0x45, 0x4C, 0x22, 0xA5, 0x69, 0x37, 0xEB, 0x6E, 0x2B, 0x0E, 7 0xBD, 0x84, 0x0F, 0x91, 0x61, 0x38, 0xF6, 0xF1, 0xBA, 0x99, 8 0x19, 0x41, 0x72, 0x07, 0x91, 0xF0, 0x26, 0x68, 0x06, 0x61, 9 0x26, 0x5C, 0x20, 0x35, 0xDD, 0xCF, 0xFC, 0x77, 0x57, 0x54, 10 0x81, 0xF2, 0xF2, 0xE4, 0xAF, 0xBF, 0xA2, 0x1D, 0x29, 0xAE, 11 0x6C, 0x08, 0x3B, 0x76, 0x1B, 0x66, 0xB8, 0xFE, 0x72, 0xCB, 12 0xD6, 0x94, 0xC3, 0xD5, 0x6A, 0xE7, 0x0C, 0x7A, 0x28, 0xDC, 13 0xBC, 0xAC, 0x80] 14 key = b"30776159143604297789676442413079" 15 aes = AES.new(key, AES.MODE_ECB) 16 text = b'' 17 for i in ciper: 18 text += bytes(chr(i),encoding="latin1") 19 print(text) 20 c = aes.decrypt(text) 21 print(c.decode("utf-16"))
主要是程序给的提示太多,连蒙带猜就能弄出来了。
本文来自博客园,作者:Mz1,转载请注明原文链接:https://www.cnblogs.com/Mz1-rc/p/14145491.html
如果有问题可以在下方评论或者email:mzi_mzi@163.com



