ctf-show-萌新_杂项
杂项1
这题由题目可知直接用md5进行解码即可得到答案
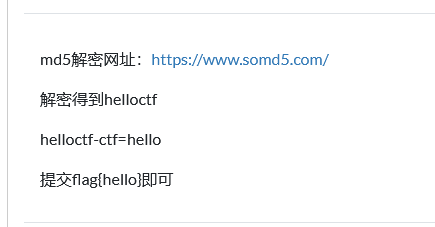
杂项2
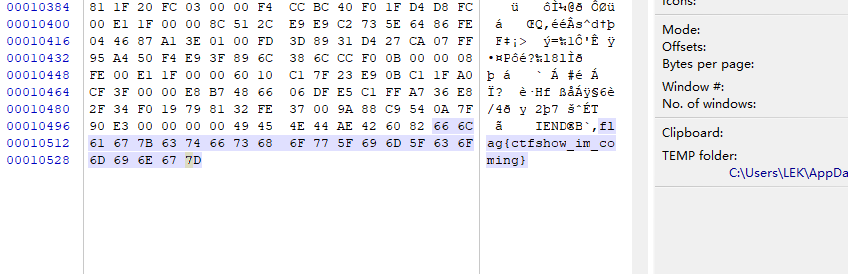
文件末尾有答案
杂项3
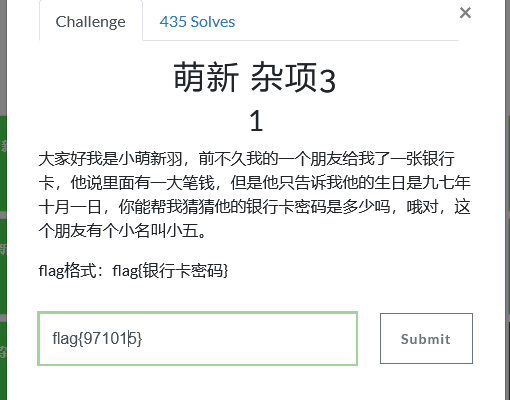
杂项4
直接将压缩包拖进ARCHPR进行解密,根据题目可知为9位数字
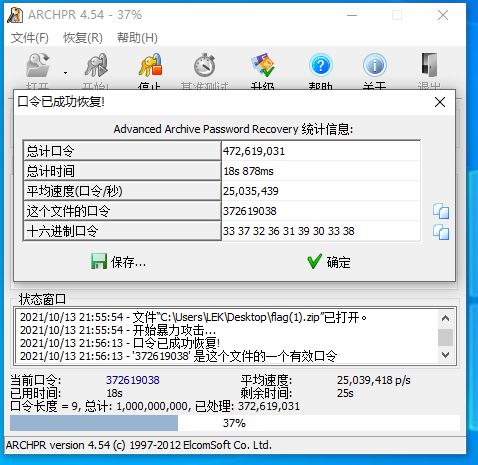
杂项5
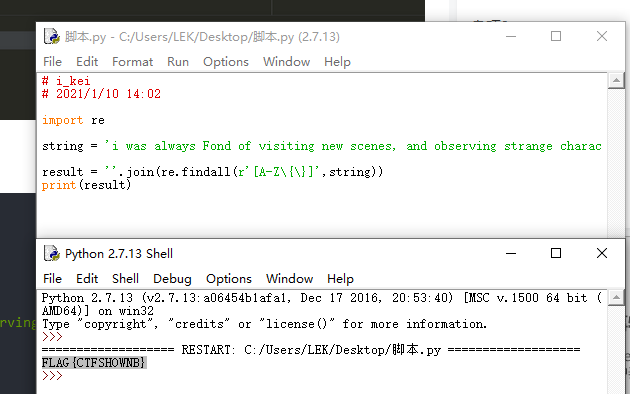
文档中所有大写字母连起来就是flag,所以需要使用脚本来将里面的大写和{}提取出来,这就是答案
# i_kei
# 2021/1/10 14:02
import re
string = 'i was always Fond of visiting new scenes, and observing strange characters and manners. even when a mere chiLd i began my travels, and made mAny tours of discovery into foreiGn {parts and unknown regions of my native City, to the frequent alarm of my parents, and The emolument of the town-crier. as i grew into boyhood, i extended the range oF my obServations. my holiday afternoons were spent in rambles about tHe surrounding cOuntry. i made myself familiar With all its places famous in history or fable. i kNew every spot where a murder or robbery had been committed, or a ghost seen. i visited the neighboring villages, and added greatly to my stock of knowledge,By noting their habits and customs, and conversing with their sages and great men.}'
result = ''.join(re.findall(r'[A-Z\{\}]',string))
print(result)
/*findall查找全部r标识代表后面是正则的语句
Python 正则表达式 re findall 方法能够以列表的形式返回能匹配的子串*/
杂项6
点开压缩包,里面文本要密码,然后将压缩包放到Ziperello中进行解密,发现加密的文件数为0,可以初步判断为伪加密,需要把压缩包放到WinHex中查看。
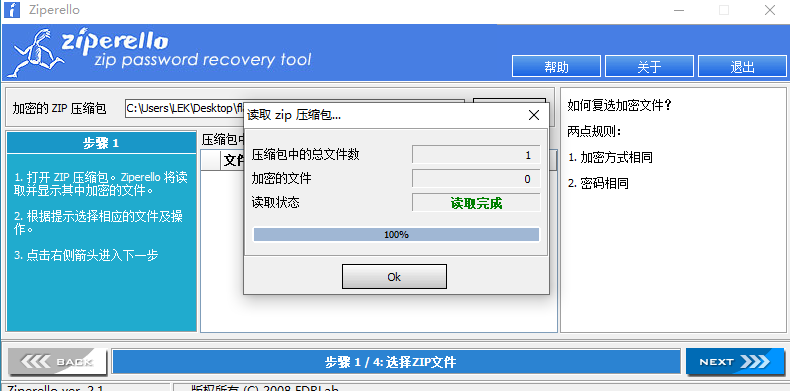
将09改为00,就可以使文本的伪加密解除,从而得到flag
杂项7
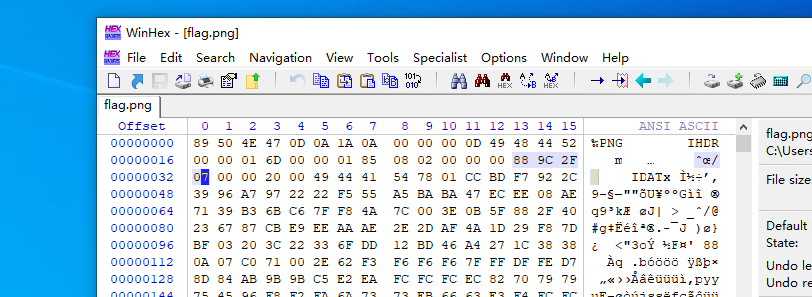
打开题目,可以从题中初步了解,这是一个被修改的图片
有于图片有点那个啥,就不上来了
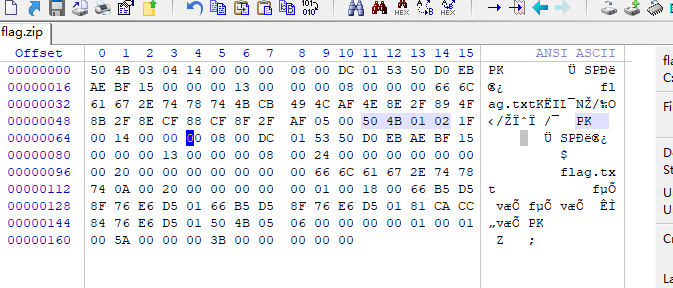
对于这张图片,先用WinHex找到图片中的src,然后用脚本进行爆破
脚本代码:
import struct
import binascii
import os
m = open("flag.png","rb").read()
k=0
for i in range(5000):
if k==1:
break
for j in range(5000):
c = m[12:16] + struct.pack('>i', i) + struct.pack('>i', j)+m[24:29]
crc = binascii.crc32(c) & 0xffffffff
if crc == 0x889C2F07:
k = 1
print(hex(i),hex(j))
break
用Python进行脚本爆破时,需要将脚本和图放在同一目录下,我比较喜欢放桌面,用完就可以删除,如果想保存下来可以放到特定的文件夹,方便下次拿来用。
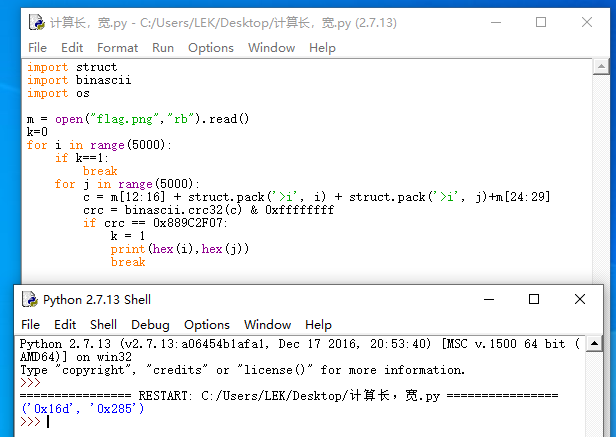
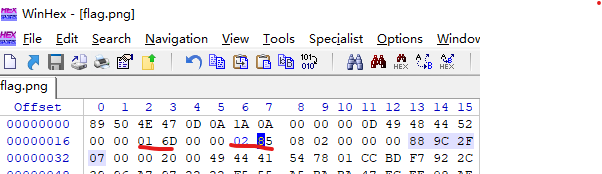
算出得到0285,将原来位置上的长宽修改为与之对应的,然后保存打开图片即可得到flag。

杂项8
本题和杂项7基本步骤一致
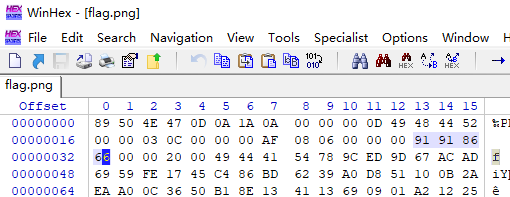
都是运用以上的脚本,但是要将crc的值改一下。
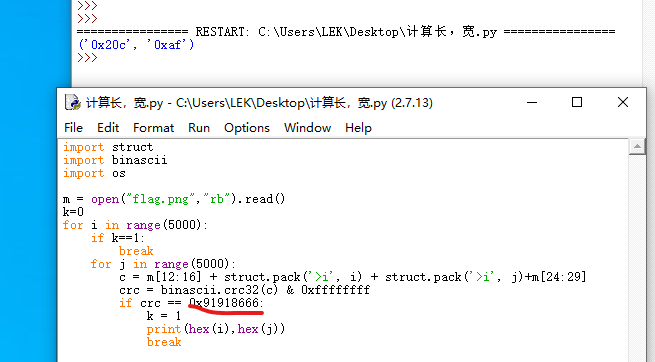
得到正确的长宽时,去修改WinHex中修改,然后图片得到恢复,图片就是flag。
杂项9
该题下架了!!!

杂项10
这题把眼睛摘了,答案就出来了。 内容:我好喜欢你
杂项11
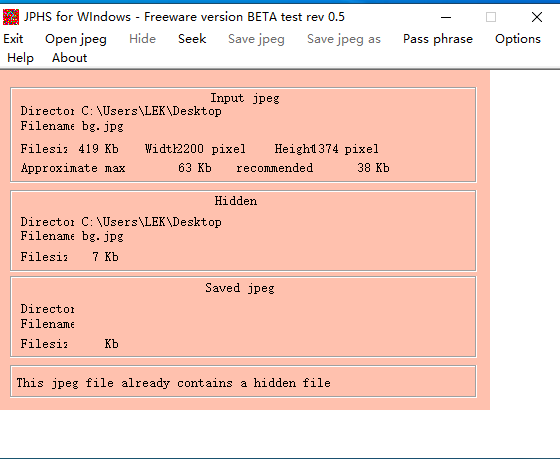
本题打开题目,已经给出要下载的工具Jphswin,进去只需要打开图片,然后Seek,然后看见是空密码,直接点击ok,然后再保存下来即可得到一个二维码。
然后用CQR工具扫描该二维码,可以得到内容:
https://ctf.show/?ZmxhZ3vmiJjnpZ7lvZLmnaXlj5HnjrDoh6rlt7HlhL/lrZDlnKjliLfpopjvvIzkuIDmgJLkuYvkuIvlj6zllKQxMOS4h+WwhuWjq+adpeaKpeS7h30=
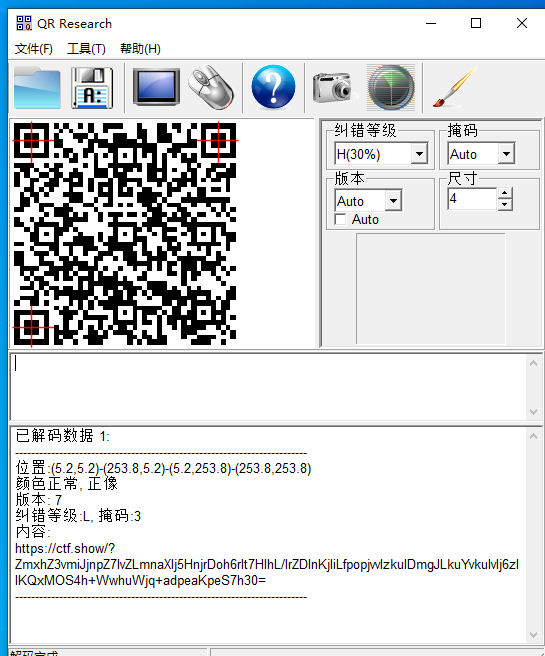
这里主要是看链接后的base64编码,拿它们去解码就可以得到flag。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号