buuctf rsa类题目(3)
1.BJDCTF rsa1
这道题目比较简单,将变换一下形式就可以解出p和q,脚本如下:
from Crypto.Util.number import long_to_bytes
import gmpy2
#p^2+q^2=324165746902526920084266080643535531095342165893754249955327749284343430505131137318727194237730915112241659680996360273629602852798886167984866252622658437476390502794861249897576814459139456187904850264853138741078482299545600219026031228426085461300900808170874235156093775709506607765428057400359074631130
#p-q=1377302432671735175954874705344520379247613943454281179464329633344438795182276365055921423486736168264010753131757524214443052220424865653259095899130388
c=102818088025122338257223173767486260149578370669223365305620974270883934505747308380040547156190451087129750571842952229355962294694776757401855654341762701403146510450351485088434280631026356430067334739732050618225414211704430904343389973317344858845952239658597751145825213909570583001908561258377437895868
e=10376939
p_q=1377302432671735175954874705344520379247613943454281179464329633344438795182276365055921423486736168264010753131757524214443052220424865653259095899130388
a=324165746902526920084266080643535531095342165893754249955327749284343430505131137318727194237730915112241659680996360273629602852798886167984866252622658437476390502794861249897576814459139456187904850264853138741078482299545600219026031228426085461300900808170874235156093775709506607765428057400359074631130
n=(a-pow(p_q,2))//2
a1=gmpy2.iroot(2*n+a,2)[0]
p=(a1+p_q)//2
q=a1-p
phi=(p-1)*(q-1)
d=gmpy2.invert(e,phi)
m=pow(c,d,n)
print(long_to_bytes(m))
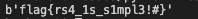
2.HDCTF2019 bbbbbbrsa
首先看一下encode.py文件
from base64 import b64encode as b32encode
from gmpy2 import invert,gcd,iroot
from Crypto.Util.number import *
from binascii import a2b_hex,b2a_hex
import random
flag = "******************************"
nbit = 128
p = getPrime(nbit)
q = getPrime(nbit)
n = p*q
print p
print n
phi = (p-1)*(q-1)
e = random.randint(50000,70000)
while True:
if gcd(e,phi) == 1:
break;
else:
e -= 1;
c = pow(int(b2a_hex(flag),16),e,n)
print b32encode(str(c))[::-1]
这里是将c倒置后用base64进行编码,这个直接倒置解码就可以了,对于e,我们可以采用遍历的方法求出50000到70000内符合条件的e,注意为了保证包含全部的e,在小于50000的范围里还有一个e,然后用这些e来解密找出flag{****}形式的明文即可,脚本如下:
import gmpy2
from Crypto.Util.number import long_to_bytes
p = 177077389675257695042507998165006460849
n = 37421829509887796274897162249367329400988647145613325367337968063341372726061
#c = ==gMzYDNzIjMxUTNyIzNzIjMyYTM4MDM0gTMwEjNzgTM2UTN4cjNwIjN2QzM5ADMwIDNyMTO4UzM2cTM5kDN2MTOyUTO5YDM0czM3MjM
c=2373740699529364991763589324200093466206785561836101840381622237225512234632
q=n//p
phi=(p-1)*(q-1)
a=[]
d1=[]
for e in range(50000,70000):
if(gmpy2.gcd(e,phi)==1):
a.append(e)
e=49999
while True:
if gmpy2.gcd(e,phi) == 1:
a.append(e)
break
else:
e -= 1
for i in a:
if(gmpy2.invert(i,phi)):
d=gmpy2.invert(i,phi)
d1.append(d)
for i in d1:
m=pow(c,i,n)
if "flag" in str(long_to_bytes(m)):
print(long_to_bytes(m))