[SCTF2019]Who is he
利用 dnspy 查看 Assembly-CSharp.dll,定位到关键部分

注意到 Decrypt 函数所在地方将输入数据与解密内容对比,查看一下这个函数
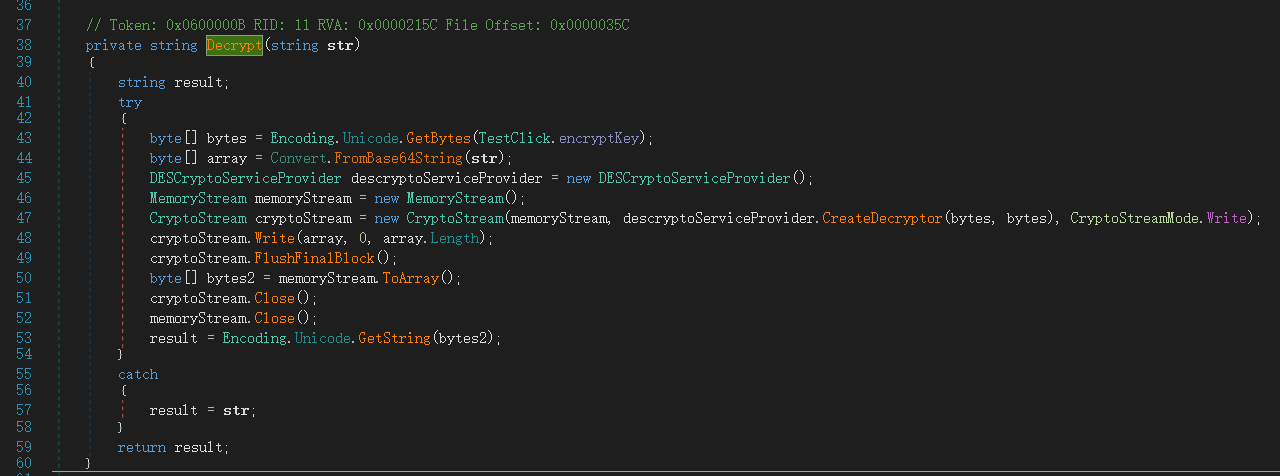
对传入的字符串先 base64 解密再 des 解密,查看传入字符串
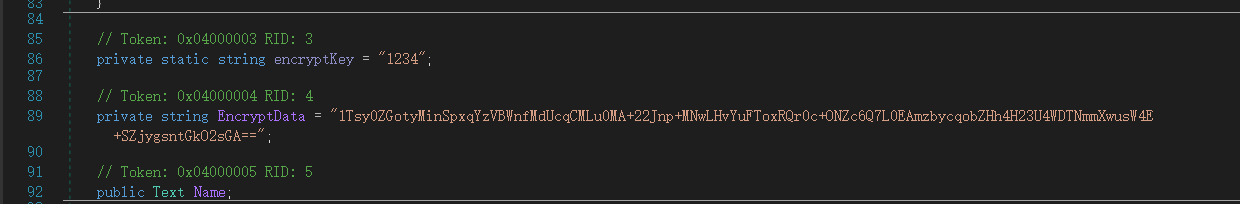
得到密文以及密钥
因为 C# 里面字符串默认是 Unicode,密钥是 1234,转成字节数组每个字符后面都要加 \x00
import base64
from Crypto.Cipher import DES
key = b"1\x002\x003\x004\x00"
des = DES.new(key, mode = DES.MODE_CBC, iv = key)
cipher = b"1Tsy0ZGotyMinSpxqYzVBWnfMdUcqCMLu0MA+22Jnp+MNwLHvYuFToxRQr0c+ONZc6Q7L0EAmzbycqobZHh4H23U4WDTNmmXwusW4E+SZjygsntGkO2sGA=="
cipher = base64.b64decode(cipher)
plain = des.decrypt(cipher)[0:-8].decode("utf-16")
print(plain)
运行得到:He_P1ay_Basketball_Very_We11!Hahahahaha!,但是不对
其他师傅的 wp 说后面要用 ce,直接搜索 Emmmmm
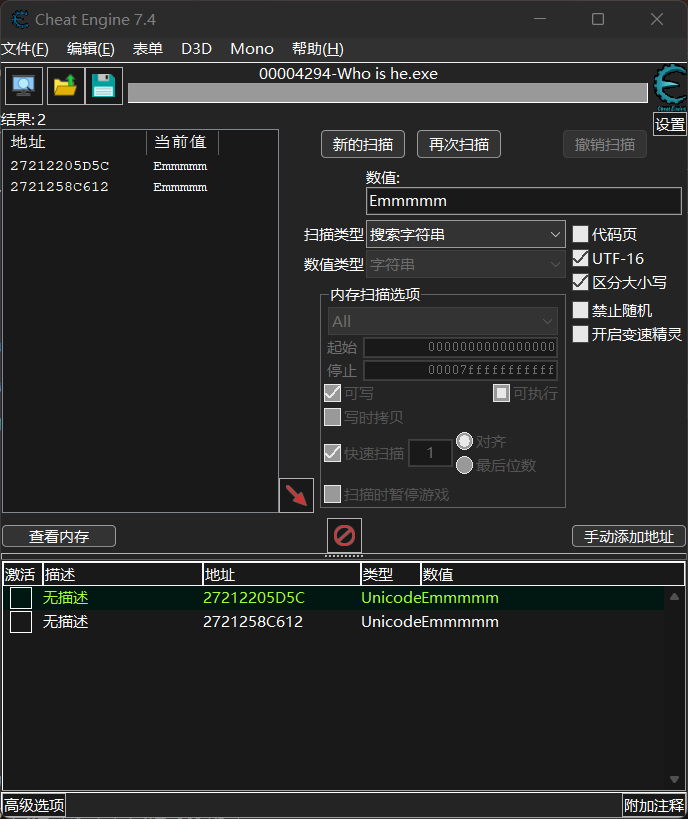
分别定位内存中的位置,得到两个新的密文和密钥
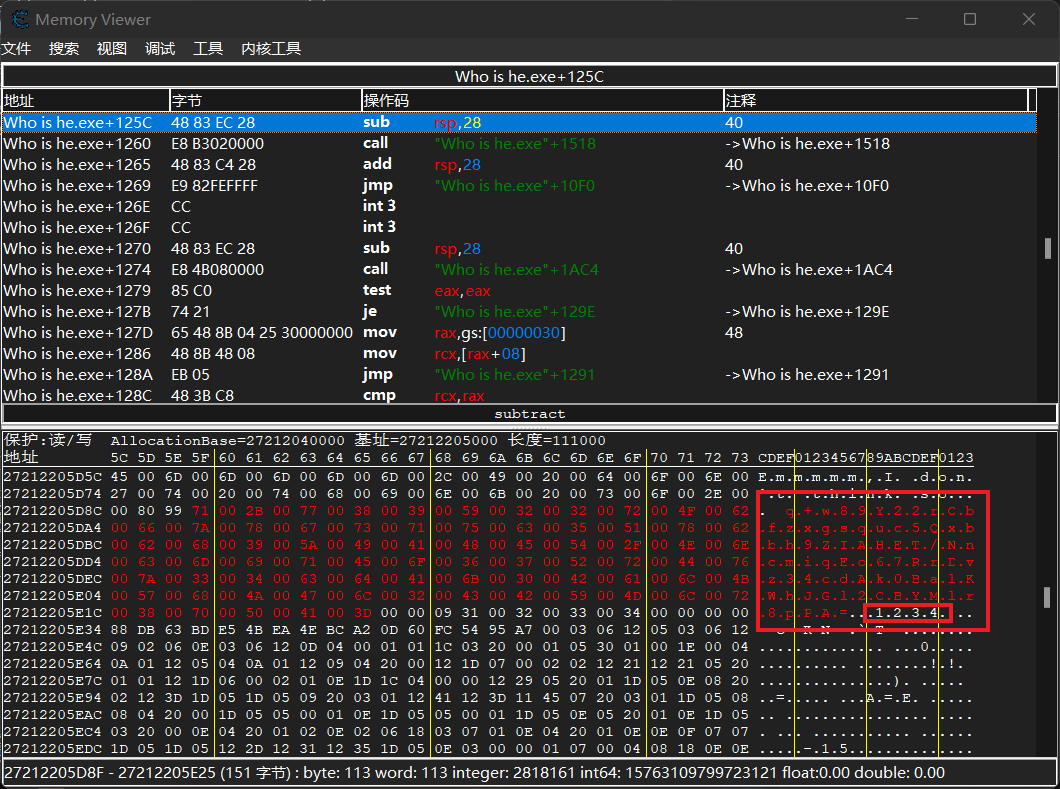

再利用脚本解密一下
import base64
from Crypto.Cipher import DES
key = b"1\x002\x003\x004\x00"
des = DES.new(key, mode = DES.MODE_CBC, iv = key)
cipher = b"1Tsy0ZGotyMinSpxqYzVBWnfMdUcqCMLu0MA+22Jnp+MNwLHvYuFToxRQr0c+ONZc6Q7L0EAmzbycqobZHh4H23U4WDTNmmXwusW4E+SZjygsntGkO2sGA=="
cipher = base64.b64decode(cipher)
plain = des.decrypt(cipher)[0:-8].decode("utf-16")
print(plain)
key = b"1\x002\x003\x004\x00"
des = DES.new(key, mode = DES.MODE_CBC, iv = key)
cipher = b"q+w89Y22rObfzxgsquc5Qxbbh9ZIAHET/NncmiqEo67RrDvz34cdAk0BalKWhJGl2CBYMlr8pPA="
cipher = base64.b64decode(cipher)
plain = des.decrypt(cipher)[0:-8].decode("utf-16")
print(plain)
key = b"t\x00e\x00s\x00t\x00"
des = DES.new(key, mode = DES.MODE_CBC, iv = key)
cipher = b"xZWDZaKEhWNMCbiGYPBIlY3+arozO9zonwrYLiVL4njSez2RYM2WwsGnsnjCDnHs7N43aFvNE54noSadP9F8eEpvTs5QPG+KL0TDE/40nbU="
cipher = base64.b64decode(cipher)
plain = des.decrypt(cipher)[0:-8].decode("utf-16")
print(plain)
又得到两个字符串
Oh no!This is a trick!!!
She_P1ay_Black_Hole_Very_Wel1!LOL!XD
最后一个 "She_P1ay_Black_Hole_Very_Wel1!LOL!XD!" 为正确 flag
flag{She_P1ay_Black_Hole_Very_Wel1!LOL!XD!}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号