[GUET-CTF2019]encrypt
因为新电脑一直没法动调 elf 又懒得找原因,所以用静态分析的办法解这个题,载入 IDA
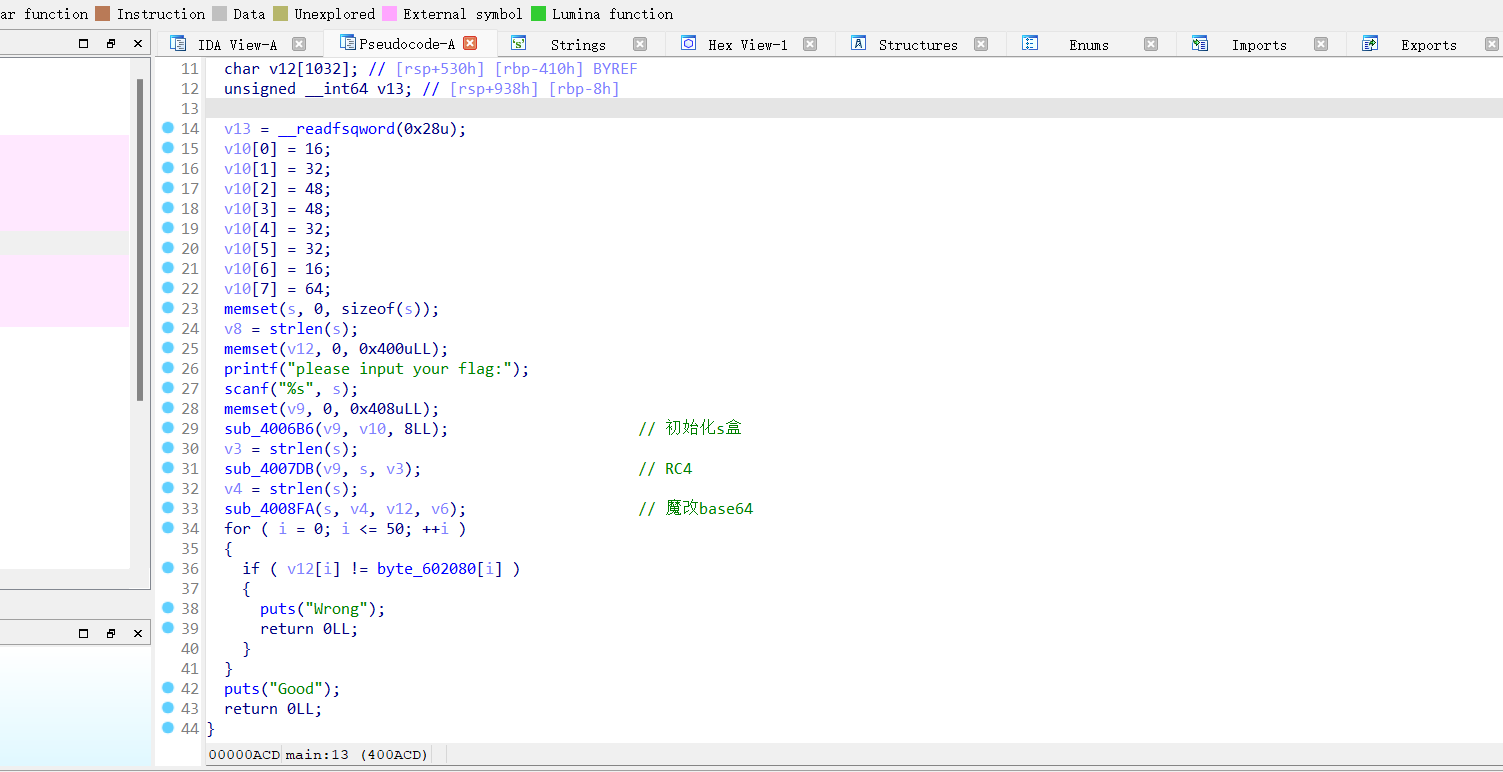
看到 sub_4006B6 很明显是 rc4 的 s 盒的初始化,传入的 v10 应该就是 key
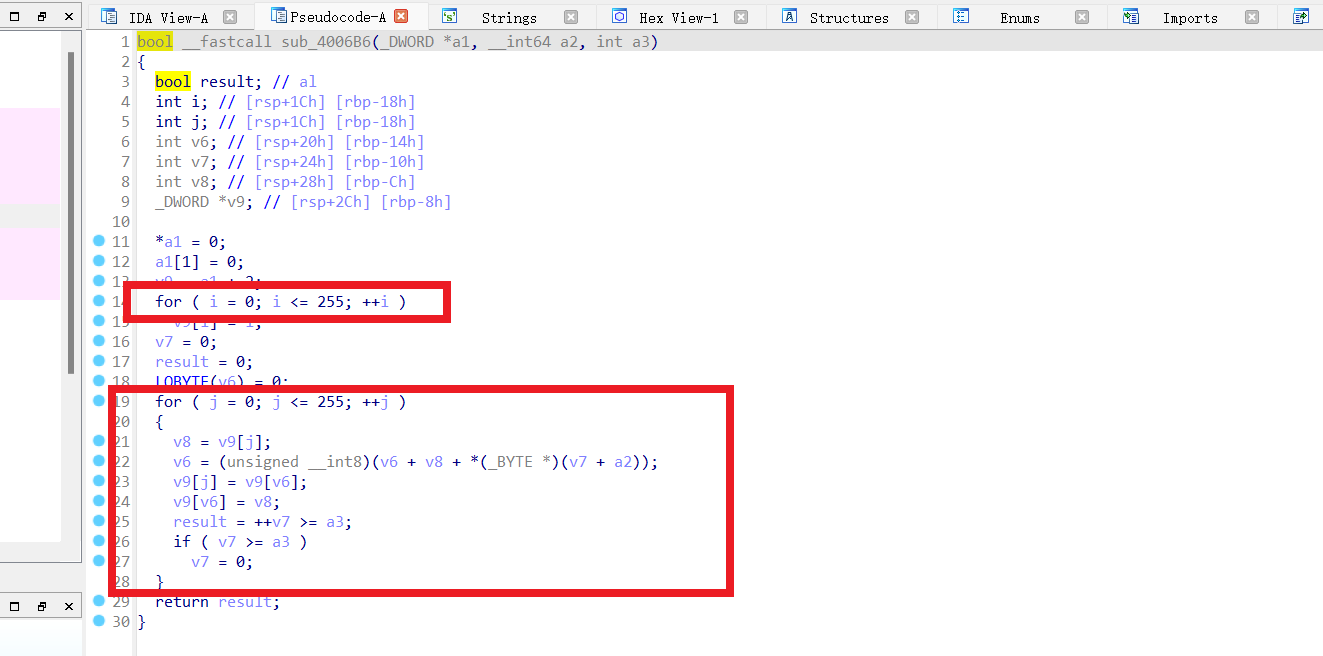
然后看 sub_4007DB
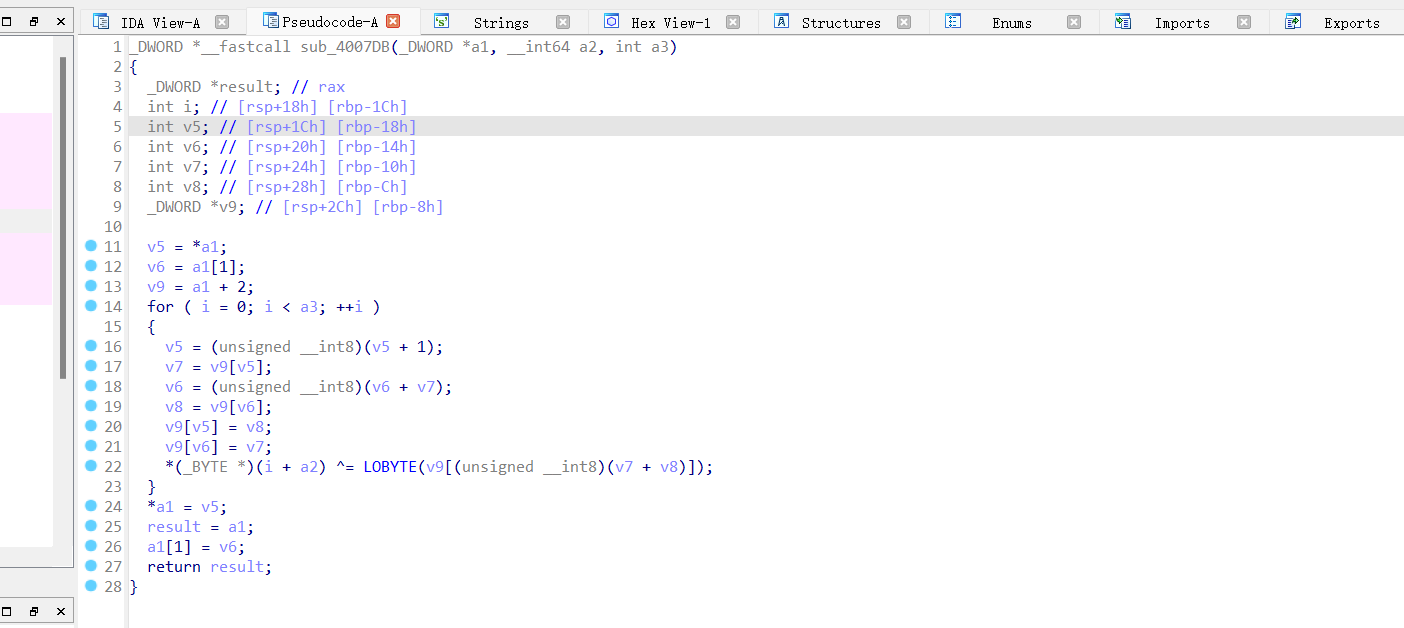
很明显是 RC4 的加密函数,再看 sub_4008FA
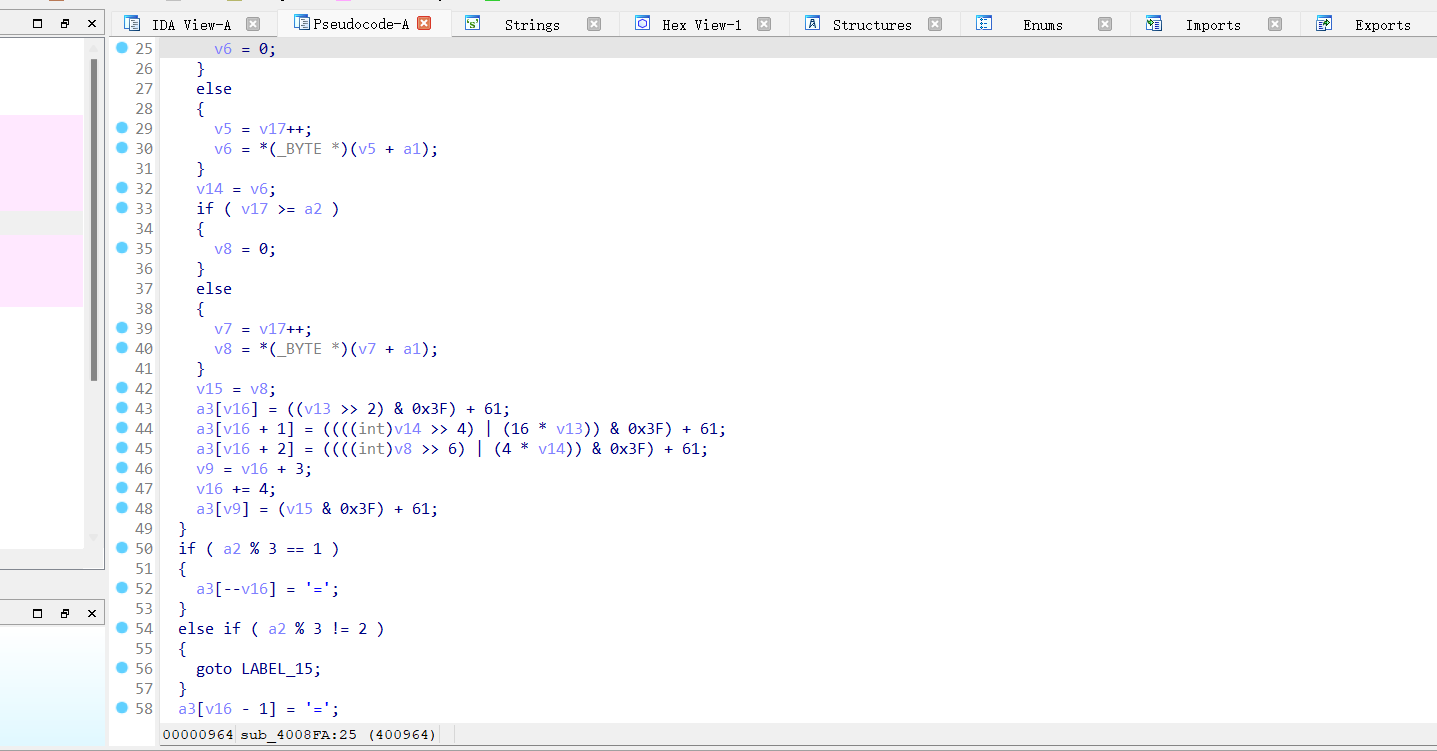
看到了一些 base64 加密的特点,但是并没有码表的参与,函数逻辑主要如下:
- 把 rc4 加密过的内容三个字节一组,变成四个六位的数(这里和 base64 原理一样)
- 把四个数每个加上 61,存入输出的数组之中
然后就知道了程序的总体逻辑:将输入 rc4 加密 ——> 魔改base64加密 ——> 和密文进行对比
写脚本逆向即可:
from base64 import *
import binascii
from Crypto.Util.number import *
duibi="Z`TzzTrD|fQP[_VVL|yneURyUmFklVJgLasJroZpHRxIUlH\\vZE="
# for i in range(len(duibi)-1):
# print(hex(ord(duibi[i])-61),end=",")#得到shuru
shuru=[0x1d,0x23,0x17,0x3d,0x3d,0x17,0x35,0x7,0x3f,0x29,0x14,0x13,0x1e,0x22,0x19,0x19,0xf,0x3f,0x3c,0x31,0x28,0x18,0x15,0x3c,0x18,0x30,0x9,0x2e,0x2f,0x19,0xd,0x2a,0xf,0x24,0x36,0xd,0x35,0x32,0x1d,0x33,0xb,0x15,0x3b,0xc,0x18,0x2f,0xb,0x1f,0x39,0x1d,0x8,0]
def four_to_three(a1,a2,a3,a4):
return (a1<<18)|(a2<<12)|(a3<<6)|a4
for i in range(0,len(shuru),4):
temp=four_to_three(shuru[i],shuru[i+1],shuru[i+2],shuru[i+3])
a1=temp>>16
a2=(temp>>8)&0xff
a3=(temp)&0xff
print(hex(a1)[2:].rjust(2,'0'),end="")
print(hex(a2)[2:].rjust(2,'0'), end="")
print(hex(a3)[2:].rjust(2,'0'), end="")
data1="7635fdf57d47fe95137a26593fff31a1857c63026ebd936a3e4d8dd727732d5ecc62f2dfe5d2"
def rc4_crypt(text,key):
textlen=len(text)
keylen=len(key)
ciper=[]
count=0
s=list(range(256))
for i in range(256):
count=(count+s[i]+key[i%keylen])%256
s[i],s[count]=s[count],s[i]
i=0
j=0
for m in range(textlen):
i=(i+1)%256
j=(j+s[i])%256
s[i],s[j]=s[j],s[i]
k=s[(s[i]+s[j])%256]
ciper.append(k^text[m])
ciper_text=''.join("%02x"%i for i in ciper)
return ciper_text.upper()
if __name__ == "__main__":
data = '7635fdf57d47fe95137a26593fff31a1857c63026ebd936a3e4d8dd727732d5ecc62f2dfe5d2'
key = '1020303020201040'
print()
print("rc4 result:", rc4_crypt(binascii.a2b_hex(data), binascii.a2b_hex(key.upper())))
print(long_to_bytes(0x666C61677B65313061646333393439626135396162626535366530353766323066383833657D))
#7635fdf57d47fe95137a26593fff31a1857c63026ebd936a3e4d8dd727732d5ecc62f2dfe5d200
#rc4 result: 666C61677B65313061646333393439626135396162626535366530353766323066383833657D
#b'flag{e10adc3949ba59abbe56e057f20f883e}'
参考博客:https://blog.csdn.net/weixin_51373492/article/details/121791616


 浙公网安备 33010602011771号
浙公网安备 33010602011771号